Multi-factor file watermark generation and extraction method and system
An extraction method and multi-factor technology, applied in the field of multi-factor file watermark generation and extraction, can solve the problems of lack of efficiency and security of mobile terminals, poor application of mobile terminals, and many algorithm steps, etc., to achieve rapid decryption and acquisition of content, Easy to obtain and guarantee the effect of safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
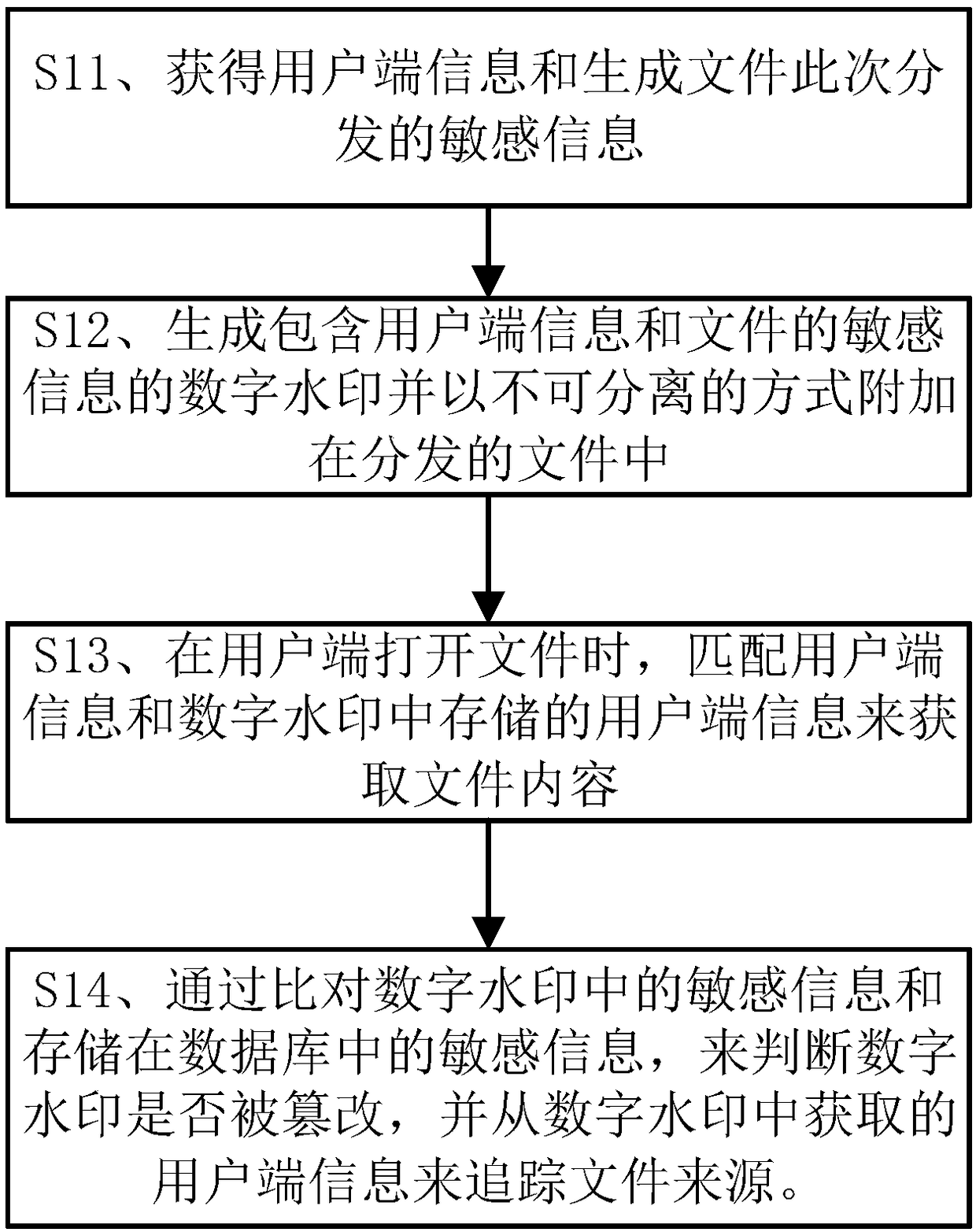
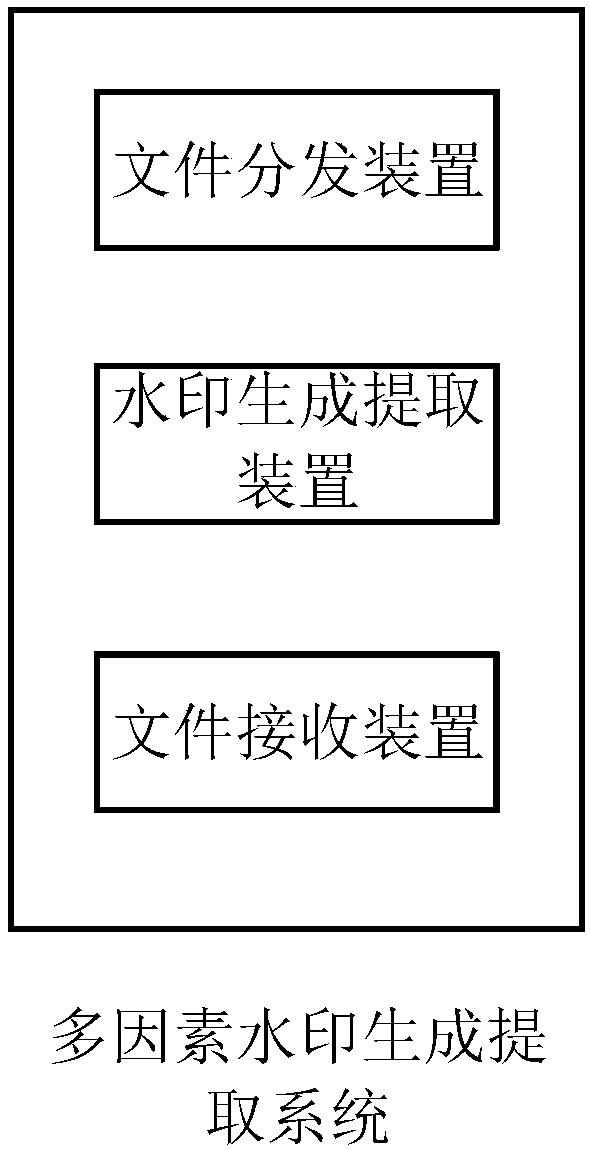
[0038] figure 1 It is a step diagram of the multi-factor file watermark generation and extraction method described in the first embodiment of the present invention. This embodiment can be applied to a file distribution management system with a file distribution device, a database, a watermark generation device, and a file receiving device. The method of the present invention It can be executed by the above-mentioned file distribution management system, such as figure 1 As shown, the multi-factor file watermark generation and extraction method described in this embodiment can be executed by the above-mentioned file distribution management system.
[0039] S11. Obtaining client information and generating sensitive information for file distribution this time;
[0040] Before distributing files, the file management system obtains the information of all the file receiving devices to be distributed, that is, the client. The client is a specific application program on a specific ter...
Embodiment 2
[0051] This embodiment is a description of a further optimized embodiment on the basis of Embodiment 1. For a more preferred implementation scheme, this embodiment uses the Android system as the operating system platform carried by the mobile terminal device, and calls the Android system. A program to complete the generation and extraction of digital watermarks.
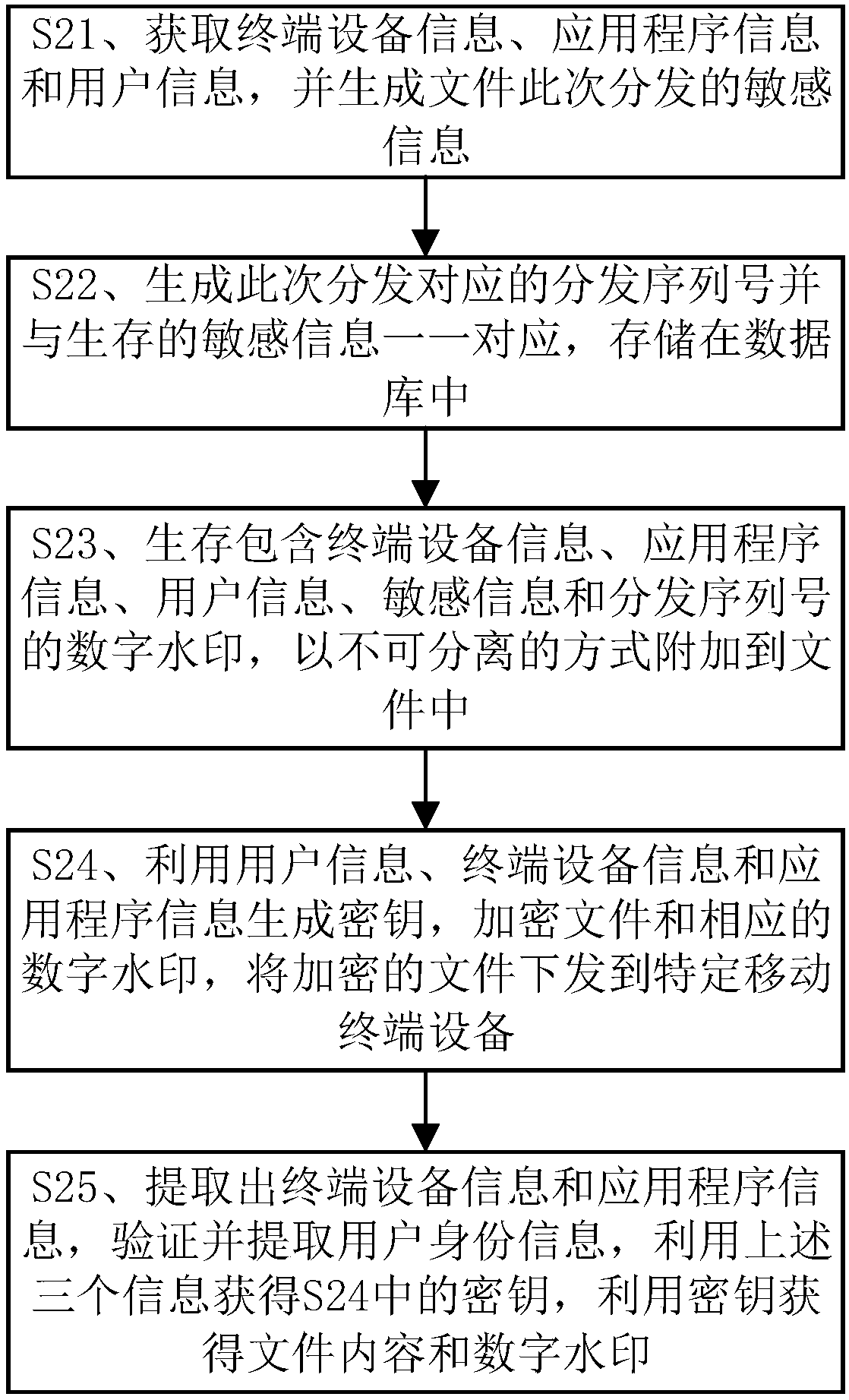
[0052] figure 2 The step diagram of the method for generating and extracting multi-factor file watermarks in this embodiment, as shown in figure 2 The method for generating and extracting the multi-factor file watermark comprises:
[0053] S21. Obtain terminal device information, application program information, and user information, and generate sensitive information for file distribution this time;
[0054] The file distribution management system extracts the unique identifier of the user (such as the user name of a specific application), the unique identifier of the terminal device (such as IMEI number, MAC ad...
Embodiment 3
[0070] The difference between this embodiment and the second embodiment is that when the system finds a leaked file, it extracts the digital watermark, and obtains the embedded user information, terminal device information, application program information, distribution serial number and sensitive information through a reversible algorithm.
[0071] The sensitive information stored in the database is retrieved by using the distribution serial number, and the sensitive information in the digital watermark is compared with the sensitive information stored in the database. If the two are consistent, the tracking result is reliable.
[0072] Specifically, when the file distribution management system finds that the file is leaked, it extracts the inseparable digital watermark attached to the file, calls the reversible algorithm SymFunc for transformation, and obtains user information, mobile terminal device information, application program information, distribution serial number and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com