Method for marking marketing calls by means of semantic mining algorithm and system for governing marketing calls
A semantic mining and telephony technology, applied in the field of telecommunications, can solve the problem of not being able to identify the type of the phone and achieve the effect of accurate interception
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
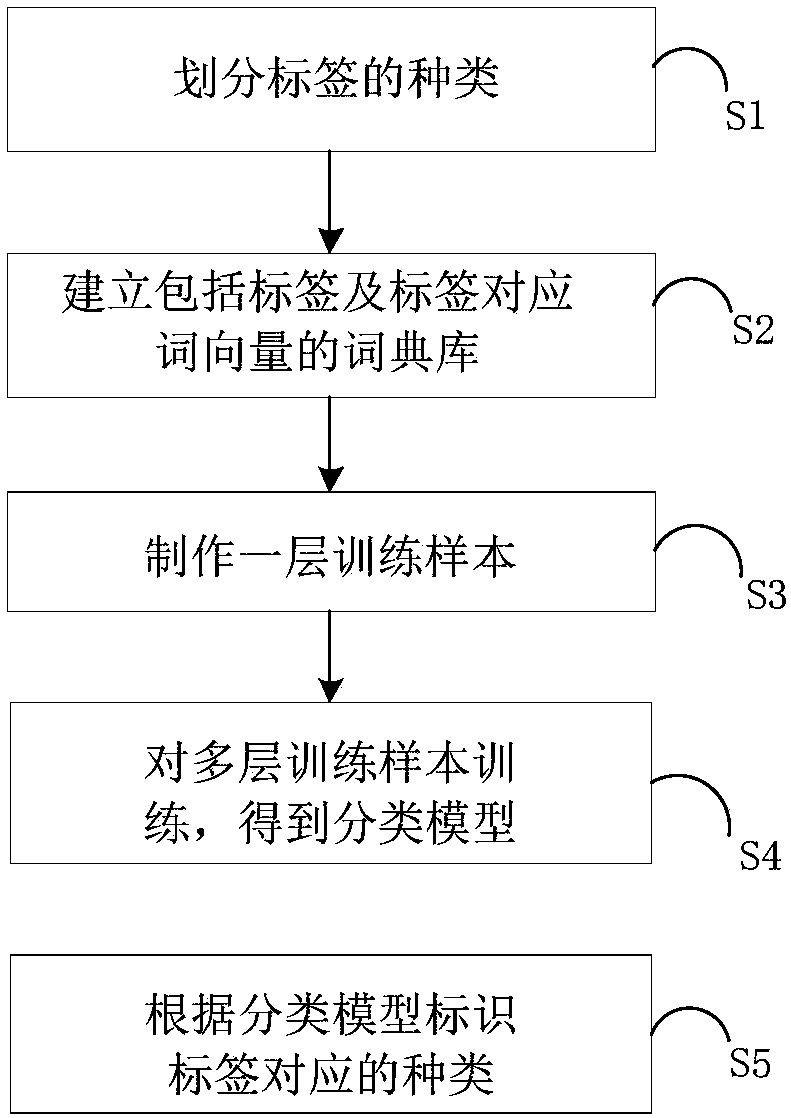
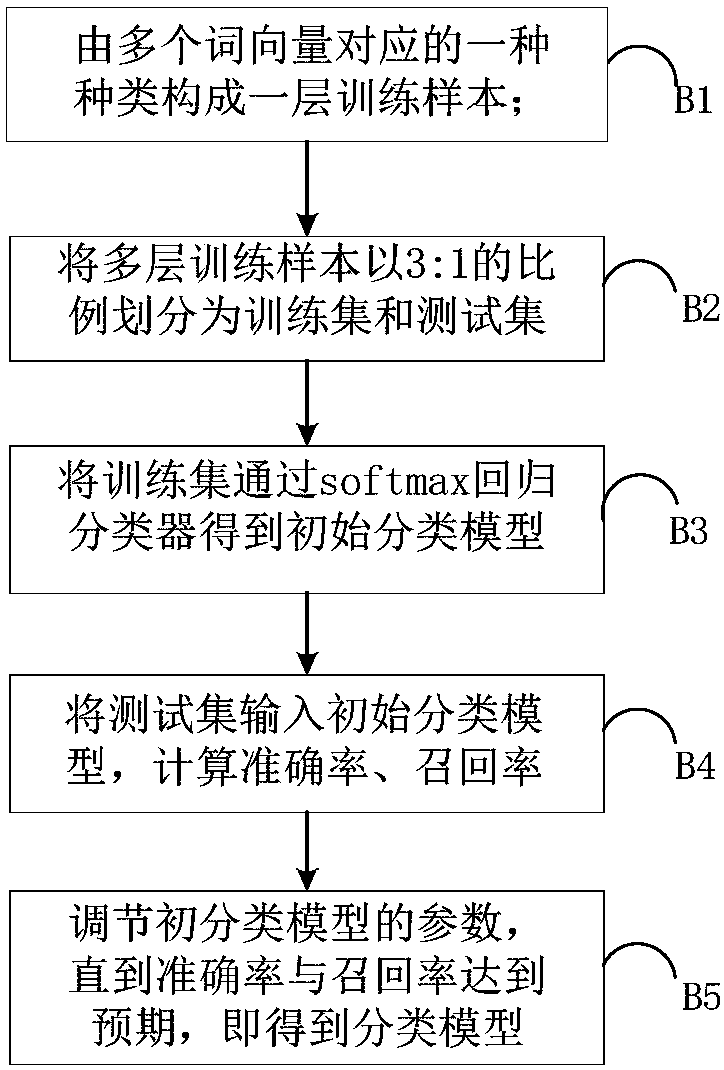
[0044] This example figure 1 , figure 2 , image 3 , Figure 4 , Figure 7 As shown, this embodiment describes a method for identifying marketing calls using a semantic mining algorithm, and the specific operation process is as follows:
[0045] S1. Divide the labels of the phones into different types;
[0046] According to the business and daily life habits, the labels of the phone are divided into N types, such as taxi, fraud, financial, sales, etc., and labels with different writing or pronunciation or pronunciation but the same meaning are classified into the same category. Labels with different writing or pronunciation or pronunciation and meaning are classified into other categories.
[0047] The sources of label classification are divided into the following three categories:
[0048] ① The existing classification of marketing calls comes from the classification of Internet software and mobile terminals.
[0049] For example: 360 Mobile Guardian divides the types of marketing ca...
Embodiment 2
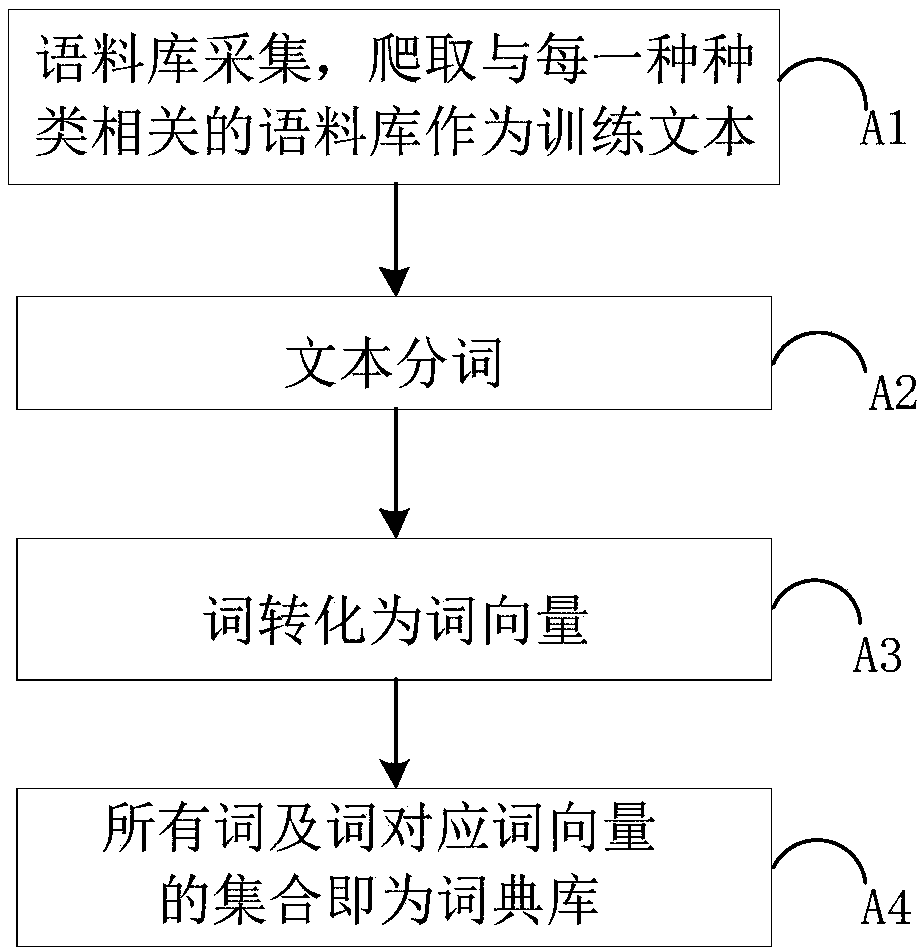
[0096] Such as Figure 5 , Image 6 As shown, this embodiment also includes a scheme for creating a new category category on the basis of the foregoing embodiment 1. This embodiment describes the use of a semantic mining algorithm to establish a new category for tags belonging to an unknown category library. The specific scheme is as follows Show:
[0097] Such as Figure 5 As shown, C5. According to the classification model obtained in Example 1, if the probability value of the output tag of the classification model belonging to each existing category is less than or equal to the threshold, the tag is added to the unknown classification database.
[0098] Such as Image 6 What is described is specifically the processing of tags in the unknown classification library.
[0099] D1. Sorting out the labels of the unknown category library and the corresponding word vectors;
[0100] D2. Perform similarity analysis on the word vectors of all tags in the library;
[0101] D3. Extracting the s...
Embodiment 3
[0111] Such as Figure 8 , Picture 9 , Picture 10 As shown, this embodiment is based on the method of using semantic mining algorithm to identify marketing calls. According to the above embodiment, the category to which each tag belongs is obtained. This embodiment selects to block certain types of calls, and provides a method for using semantic mining Algorithmic management system of marketing calls.
[0112] This embodiment requires the user to register on the marketing call classification interception platform and set the type of calls that need to be intercepted, see Figure 8 . The scope of business acceptance includes all telecommunications, China Unicom and mobile phones. For specific business acceptance procedures, see Picture 9 . The communication network intercepts certain types of marketing calls. The specific scheme is as follows:
[0113] Setting module to set the type of intercepted calls;
[0114] 101: The called user registers on the marketing call classification...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com