Information hiding methods and systems and extraction methods and systems based on big data and neural network
A neural network and information hiding technology, applied in neural learning methods, biological neural network models, digital data protection, etc., can solve the problem of limited complexity and difficulty of secret information, limited data volume, limited data volume of carrier objects and camouflaged objects, etc. problems, to achieve the effect of ensuring high concealment and ensuring safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
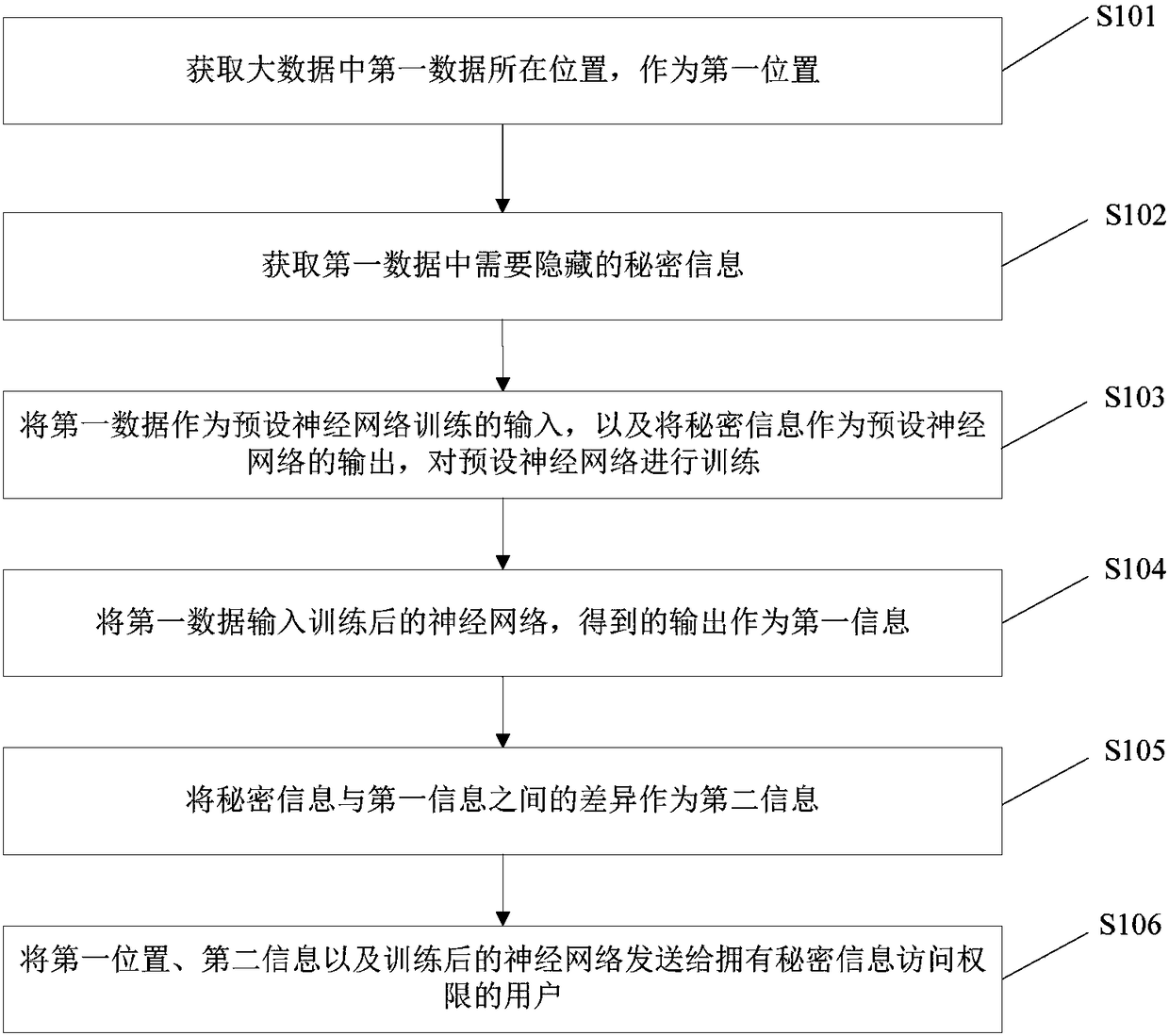
[0096] Such as figure 1 As shown, this embodiment provides an information hiding method, which includes the following steps:
[0097] S101. Obtain the location of the first data in the big data as the first location.
[0098] This embodiment is an information hiding technology based on big data search. Due to the huge amount of data of the carrier object and the disguised object, the complexity and difficulty of analyzing and digging out the secret information from the carrier object and the disguised object with a huge amount of data are very high. , like "finding a needle in a haystack", which makes it extremely impossible for secret information to be cracked, resulting in extremely high security for information hiding. At the same time, due to the large amount of data of the carrier object and the disguised object, a large amount of secret information can be hidden.
[0099] For example, the first data in the big data is an image file P, and the location of the image file...
Embodiment 2
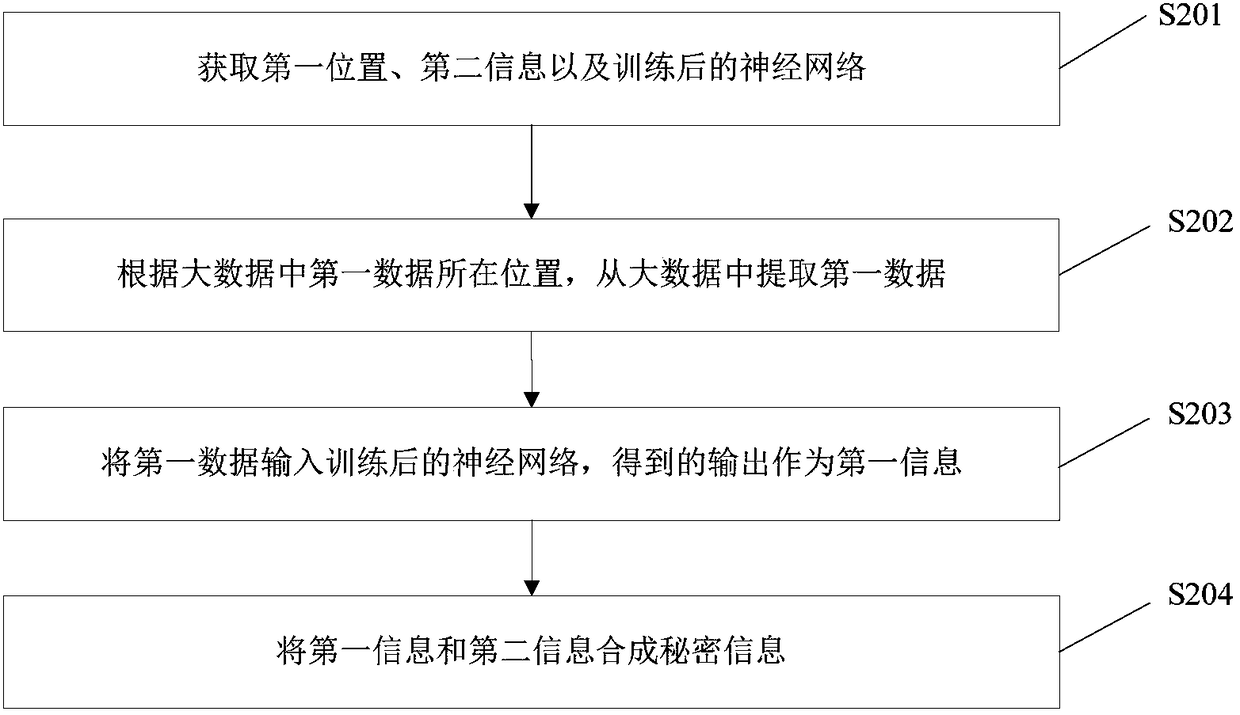
[0110] Such as figure 2 As shown, this embodiment provides an information extraction method, which corresponds to the information hiding method in Embodiment 1, and includes the following steps:
[0111] S201. Acquire a first location, second information, and a trained neural network.
[0112] Since users who have access to big data but do not have access to secret information do not know the first location, second information, and trained neural network, they cannot extract secret information through big data, ensuring the security of secret information .
[0113] Since the first information is the actual output of the neural network whose expected output is the secret information, the difference between the first information and the secret information is very small, that is, the data volume of the second information is very small; and the neural network is based on the network weight Expressed in the form of , the amount of data is also very small; so as long as the first...
Embodiment 3
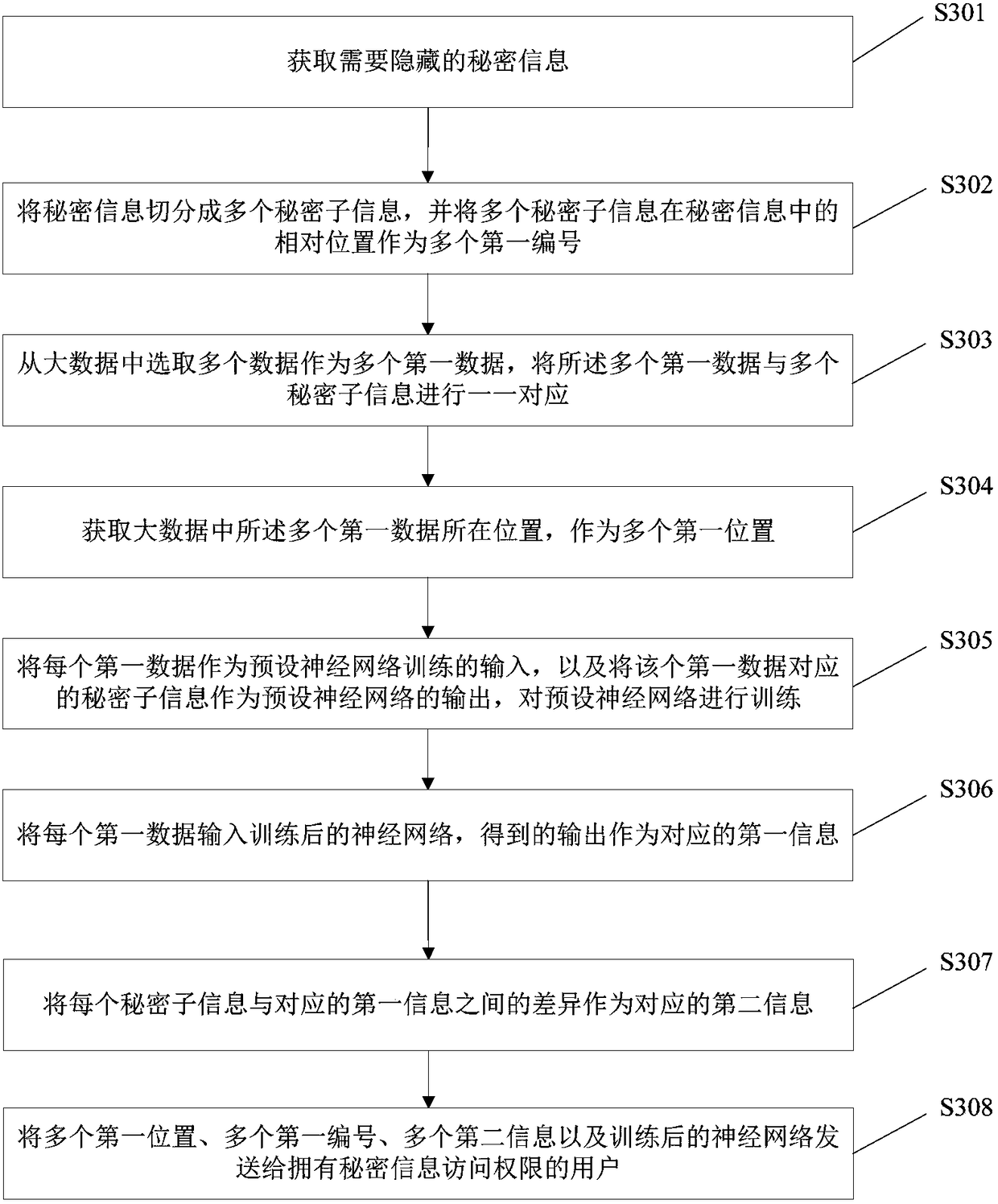
[0121] Such as image 3 As shown, this embodiment provides an information hiding method, which includes the following steps:
[0122] S301. Obtain secret information that needs to be hidden.
[0123] In this embodiment, some secret information is hidden. Therefore, the secret information to be hidden is obtained first, which is denoted as S. For example, the secret information to be hidden is 100 paragraphs.
[0124] S302. Divide the secret information into multiple secret sub-information, and use the relative positions of the multiple secret sub-information in the secret information as multiple first numbers.
[0125] In this embodiment, the secret information S is divided into p pieces of S1, S2, ..., Sp, and the relative positions of the p secret subinformation in the secret information S are used as the numbers W1, W2, ..., Wp, as p first numbers; where p≧2;
[0126] Taking the secret information that needs to be hidden as 100 paragraphs as an example, divide each parag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com