Non-aware authentication method and apparatus
A technology of non-perceptual authentication and authentication request, applied in the field of communication, can solve the problems affecting the normal use of legitimate users, instability, billing disputes, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
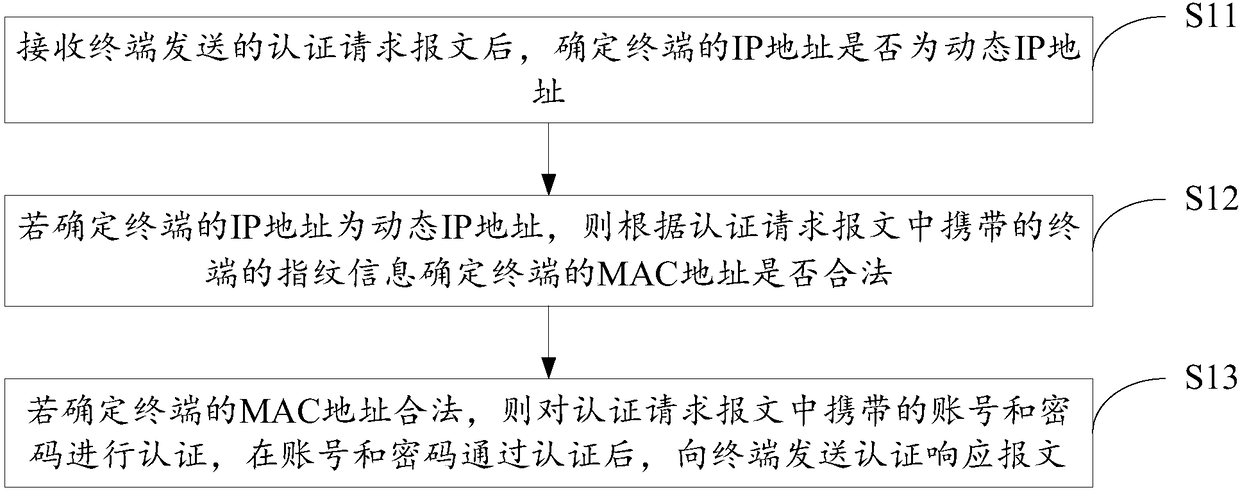
[0051] Aiming at the problems existing in the prior art that not only affect the normal use of legal users, but also lead to billing disputes due to disconnection or network instability, the embodiment of the present invention provides a non-perceptual authentication method, which is applied to the authentication server In , the flow of the method is as follows figure 1 As shown, the execution steps are as follows:
[0052] S11: After receiving the authentication request message sent by the terminal, determine whether the IP address of the terminal is a dynamic IP address.
[0053] At present, the IP address of the terminal includes static IP address and dynamic IP address. The above method is only applicable to the dynamic IP address, that is, the situation of the dynamic area. Therefore, after receiving the authentication request message sent by the terminal, it is necessary to determine the Whether the IP address is a dynamic IP address.
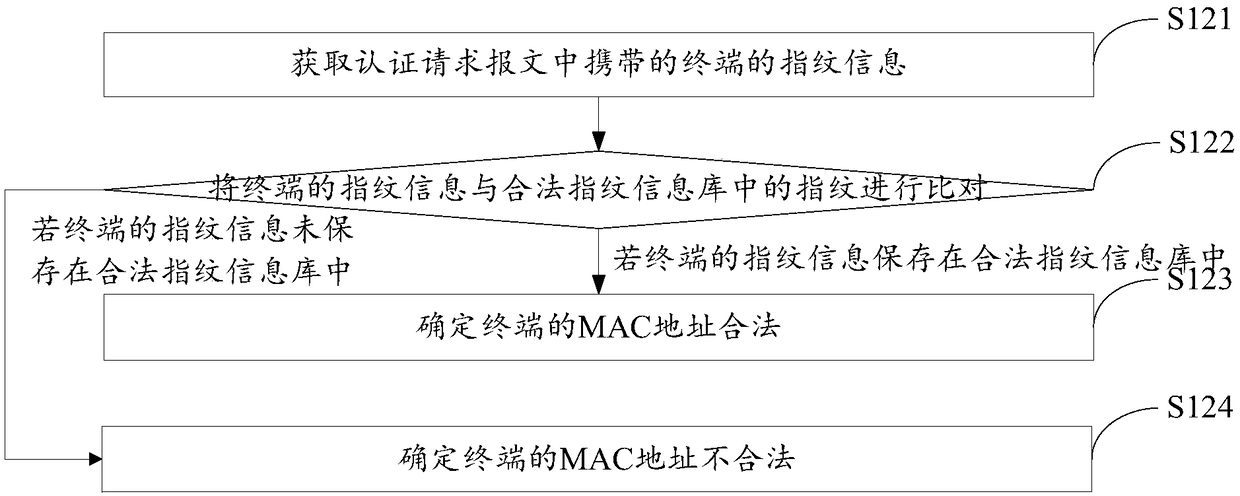
[0054] S12: If it is determined ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com