Software encryption terminal, payment terminal, software package encryption and decryption method and system
A payment terminal and encryption method technology, which is applied in transmission systems, digital transmission systems, encryption devices with shift registers/memory, etc., can solve problems such as keys not complying with key security management regulations, key leakage, etc., to achieve Less vulnerable to attacks and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
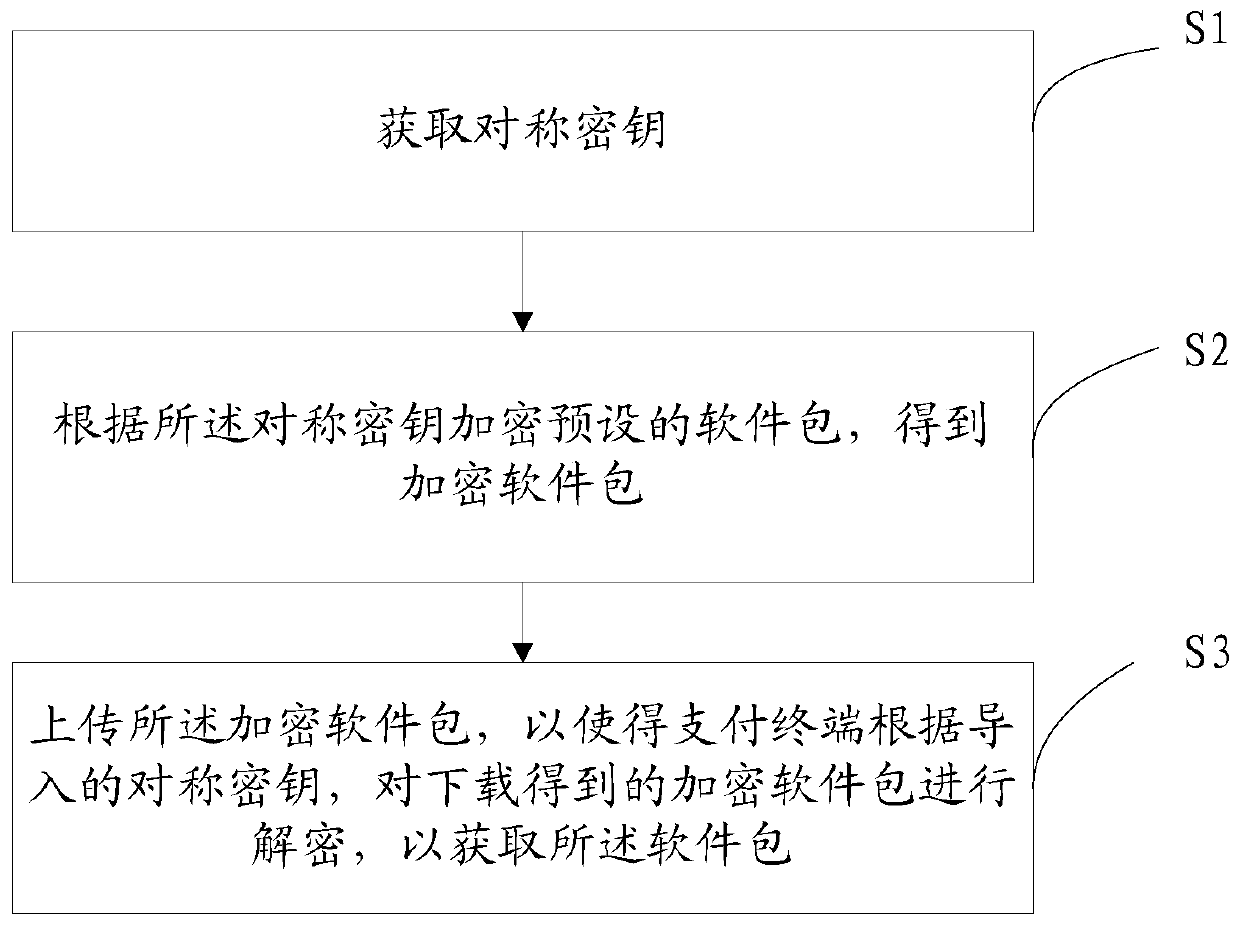
[0185] Please refer to figure 1 , Embodiment 1 of the present invention is:
[0186] A method for encrypting a software package provided by the invention comprises the following steps:
[0187] S1: Obtain a symmetric key;
[0188] Wherein, the S1 can be realized by any of the following methods:
[0189] 1. Complete the import of the symmetric key into the software encryption terminal by manually inputting the components of the symmetric key. If you use this method, you need to build a safe room and complete this operation in the safe room;
[0190] 2. Through the key generation algorithm, the symmetric key is randomly generated;
[0191] 3. Obtain the symmetric key through the key download method (need to use the key download device).
[0192] S2: Encrypt a preset software package according to the symmetric key to obtain an encrypted software package;
[0193] The S2 is specifically:
[0194] S21: Obtain the software package transmitted by the external storage device; ...
Embodiment 2
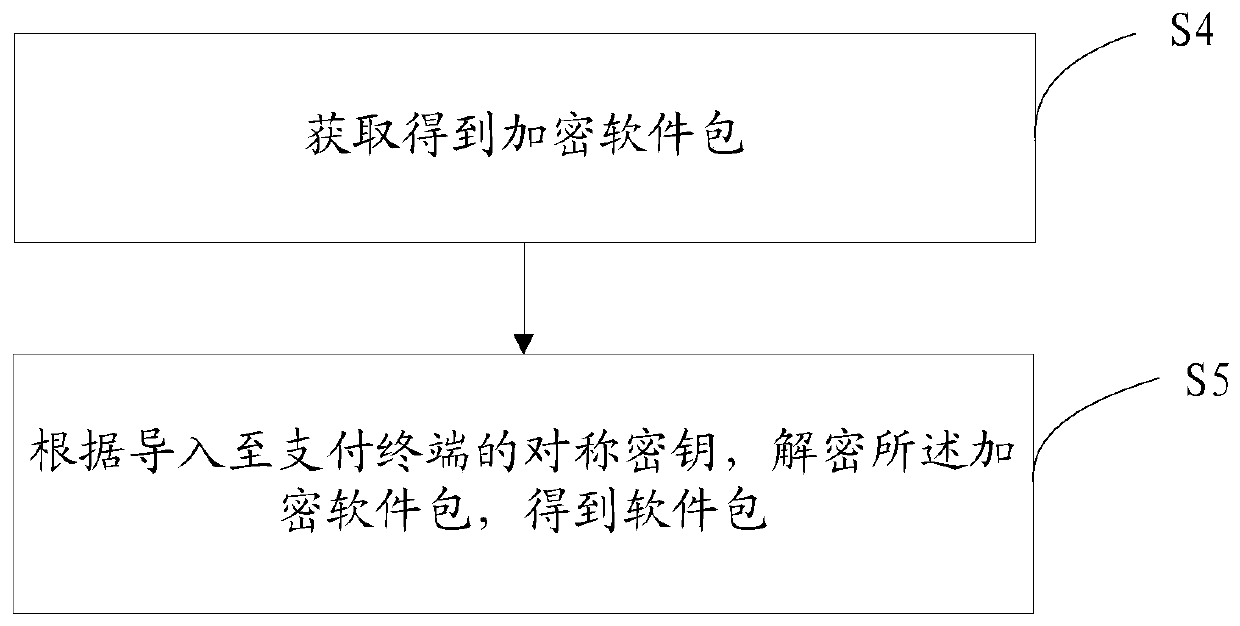
[0211] Please refer to figure 2 , the second embodiment of the present invention is:
[0212] A software package decryption method provided by the present invention comprises the following steps:
[0213] S4: obtain the encrypted software package;
[0214] The S4 is specifically:
[0215] Download the encrypted software package uploaded by the software encryption terminal from the server, and obtain the encrypted software package.
[0216] S5: According to the symmetric key imported to the payment terminal, decrypt the encrypted software package to obtain the software package;
[0217] The S5 is specifically:
[0218] Obtaining the second computer file and the second software ciphertext data according to the encryption software package;
[0219] calculating a hash value of the second software ciphertext data through a hash algorithm to obtain a second hash value;
[0220] extracting the information of the first field and the second field in the second computer file, to ob...
Embodiment 3
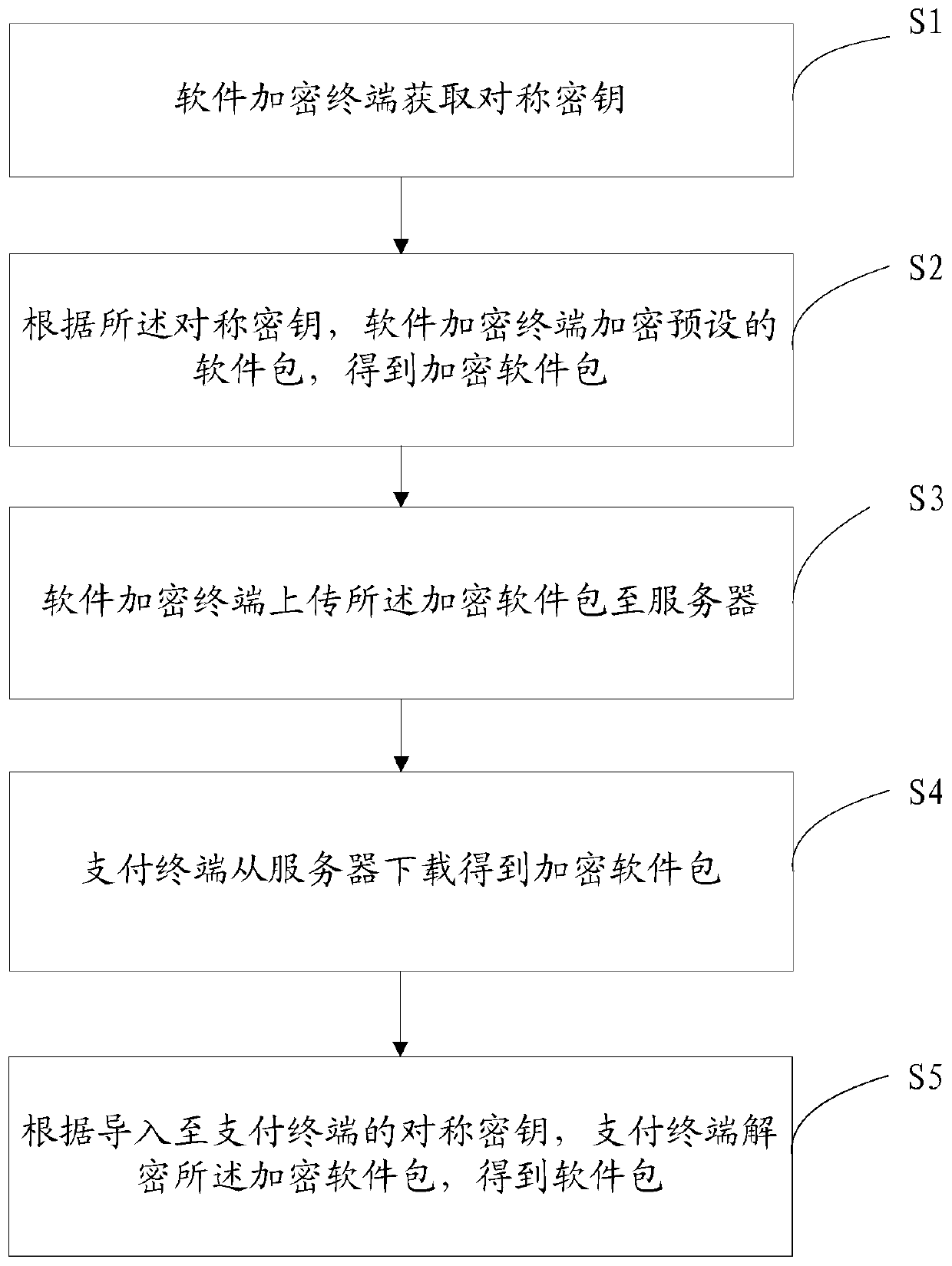
[0226] Please refer to image 3 , Embodiment three of the present invention is:
[0227] A software package encryption and decryption method provided by the present invention comprises the following steps:
[0228] S1: The software encryption terminal obtains the symmetric key;
[0229] S2: According to the symmetric key, the software encryption terminal encrypts a preset software package to obtain an encrypted software package;
[0230] The S2 is specifically:
[0231] The software encryption terminal obtains the software package transmitted by the external storage device;
[0232] preset description information, where the description information includes a first domain and a second domain;
[0233] Generate key serial number;
[0234] Write the key serial number into the first field of the description information;
[0235] Generate a first encryption key through the DUKPT algorithm according to the symmetric key and the key serial number; the first encryption key inclu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com