Power information network security policy learning device and method based on attack and defence
A network security and policy learning technology, applied in the field of power information system security, can solve problems such as inapplicability of security policies, aggravating the complexity of problems, and dynamic changes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0142] Below in conjunction with principle of the present invention, accompanying drawing and embodiment the present invention is further described
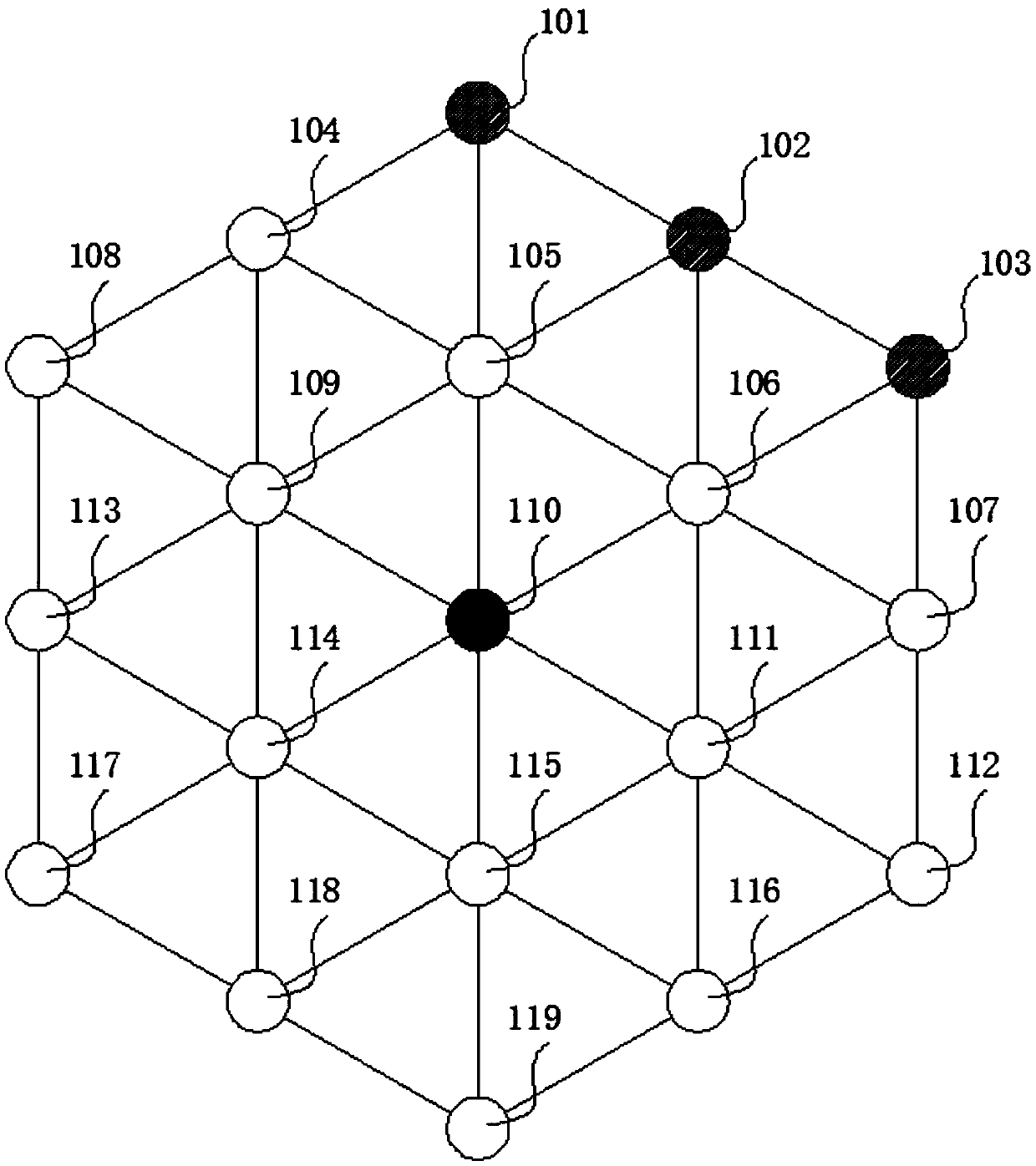
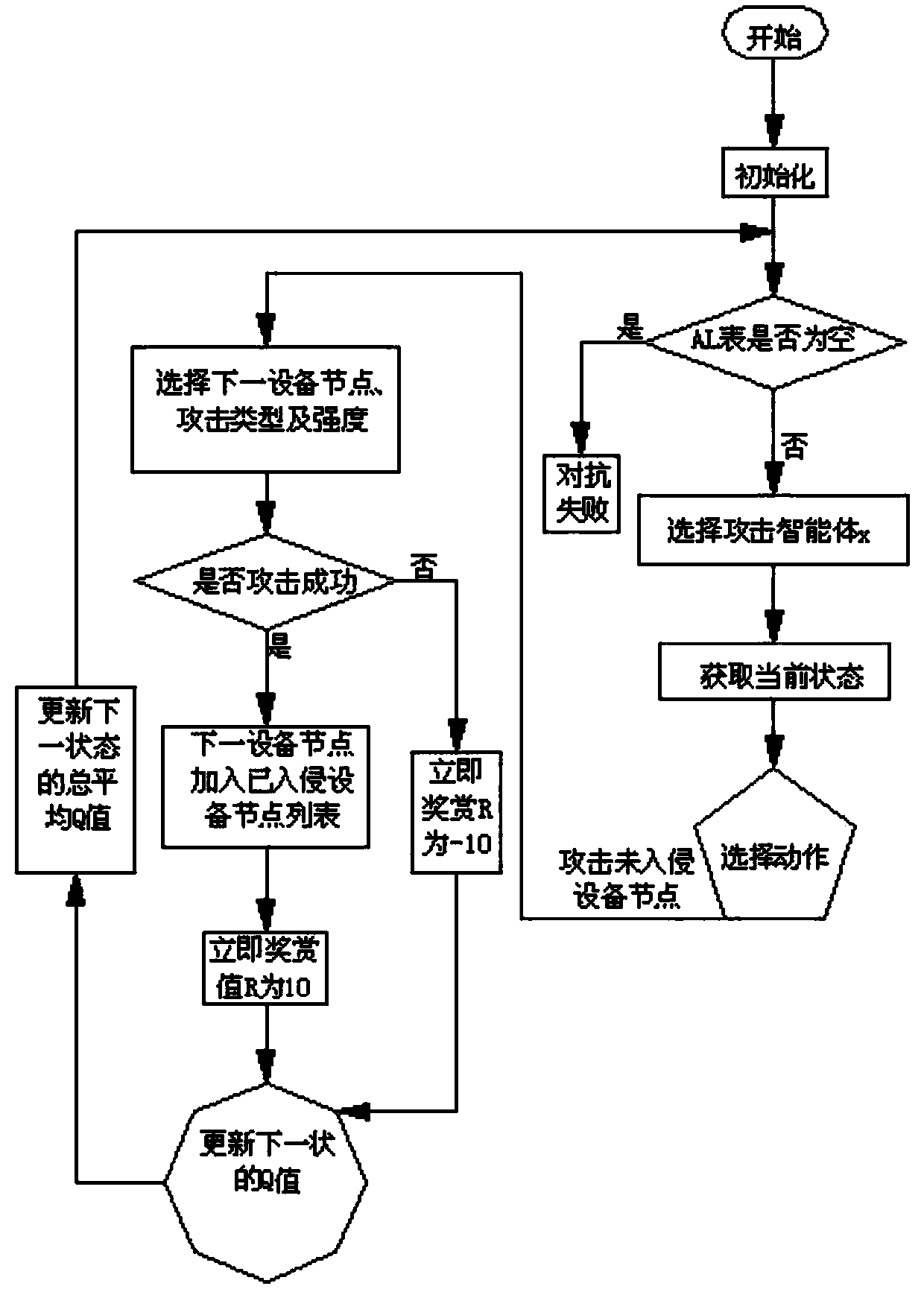
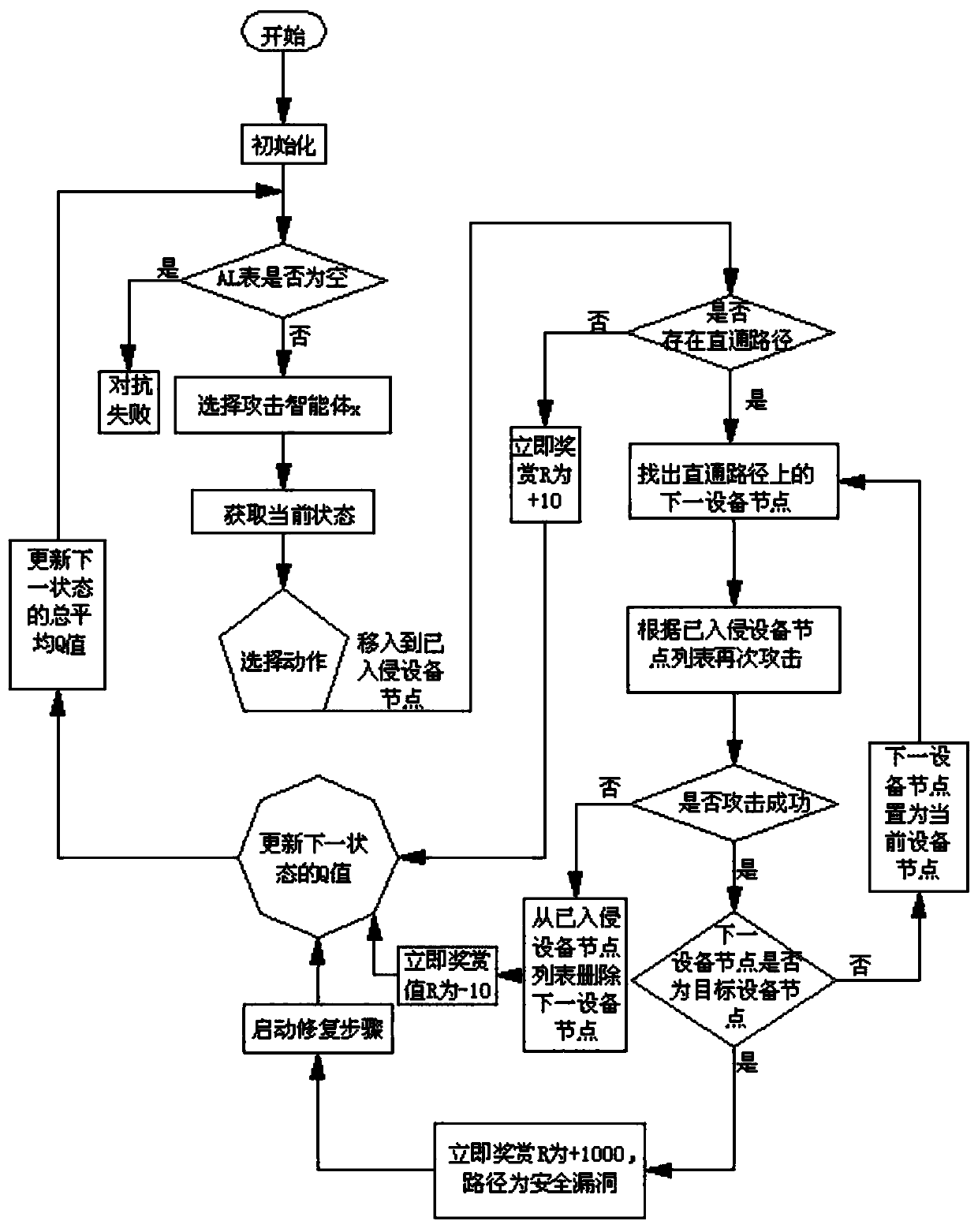
[0143] see figure 1 As shown, a power information network security policy learning device based on reinforcement learning agent attack and defense confrontation, including equipment network, several attack agents and several defense agents,
[0144] The device network is formed by connecting several device nodes 101-119 and lines according to the topology.
[0145] Several attacking agents attack the above-mentioned device network at the same time, and several defensive agents defend the above-mentioned several attacking agents at the same time. The above-mentioned several device nodes include general device nodes 101-109, 111-119 with relatively small losses after being invaded, and nodes with relatively large losses after being invaded. Important device node 110, the goal of the attacking agent is to invade an important device...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com