Risk monitoring method and device, storage medium and terminal
A risk and algorithm technology, applied in the field of communication, can solve the problems of poor timeliness, poor efficiency, and lack of scientific basis for risk monitoring business rules, and achieve the effect of solving poor efficiency and poor timeliness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0094] Figure 5 A structural diagram of the risk monitoring device provided by the embodiment of the present invention is shown, and for convenience of description, only parts related to the embodiment of the present invention are shown.
[0095] In the embodiment of the present invention, the risk monitoring device is used to realize the above figure 1 , figure 2 , image 3 ,or Figure 4 The risk monitoring method described in the embodiments may be a software unit, a hardware unit or a combination of software and hardware built into the terminal.
[0096] refer to Figure 5 , the risk monitoring device includes:
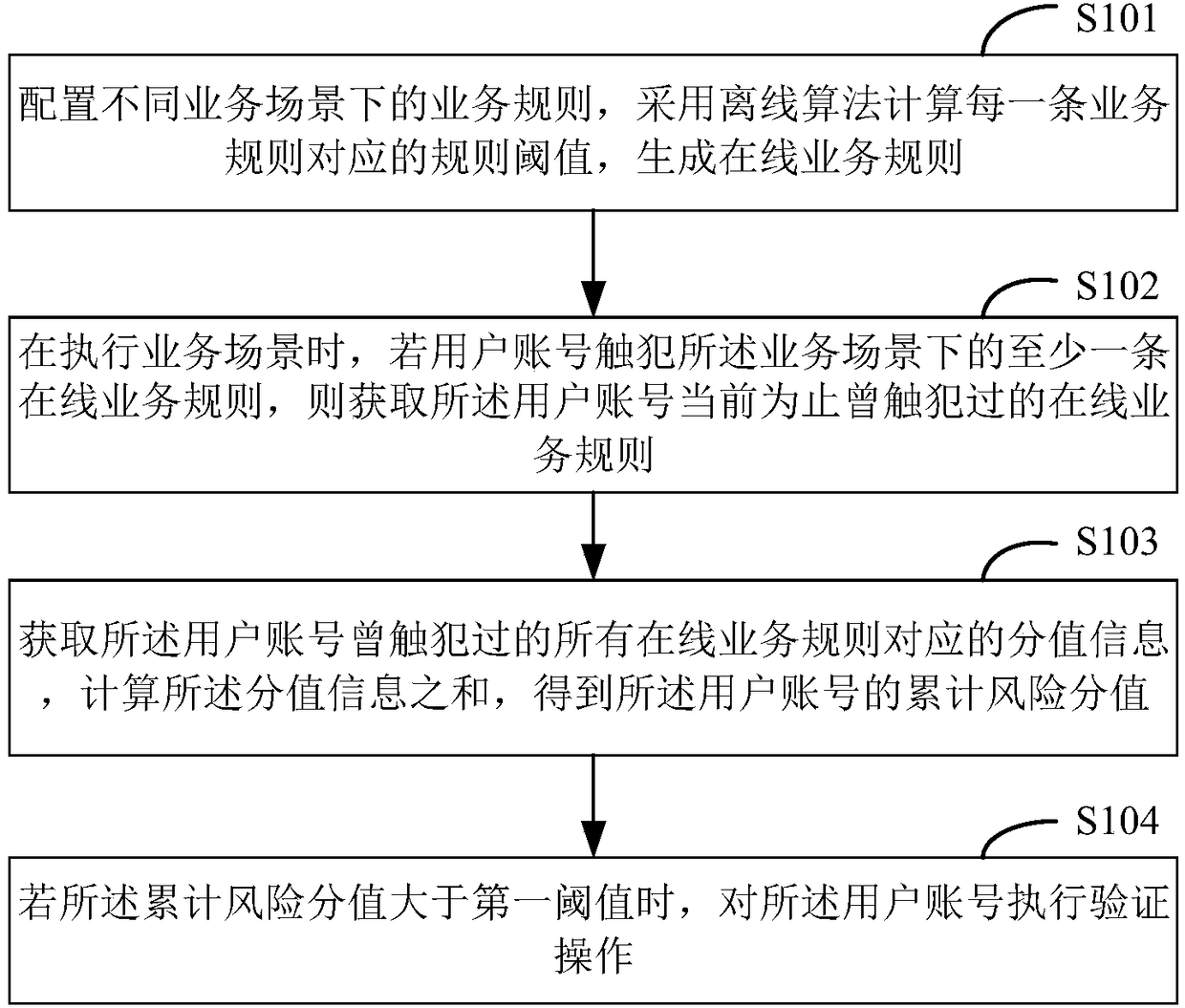
[0097] The configuration module 51 is used to configure business rules under different business scenarios, and adopts an offline algorithm to calculate a rule threshold corresponding to each business rule to generate an online business rule;
[0098] The acquiring module 52 is configured to acquire the online business rules that the user account has violate...
Embodiment 3
[0119] This embodiment provides a computer-readable storage medium, on which a computer program is stored. When the computer program is executed by a processor, the risk monitoring method in Embodiment 1 is implemented. To avoid repetition, details are not repeated here. Alternatively, when the computer program is executed by the processor, the functions of each module / unit in the risk monitoring device in Embodiment 2 are realized, and to avoid repetition, details are not repeated here.
Embodiment 4
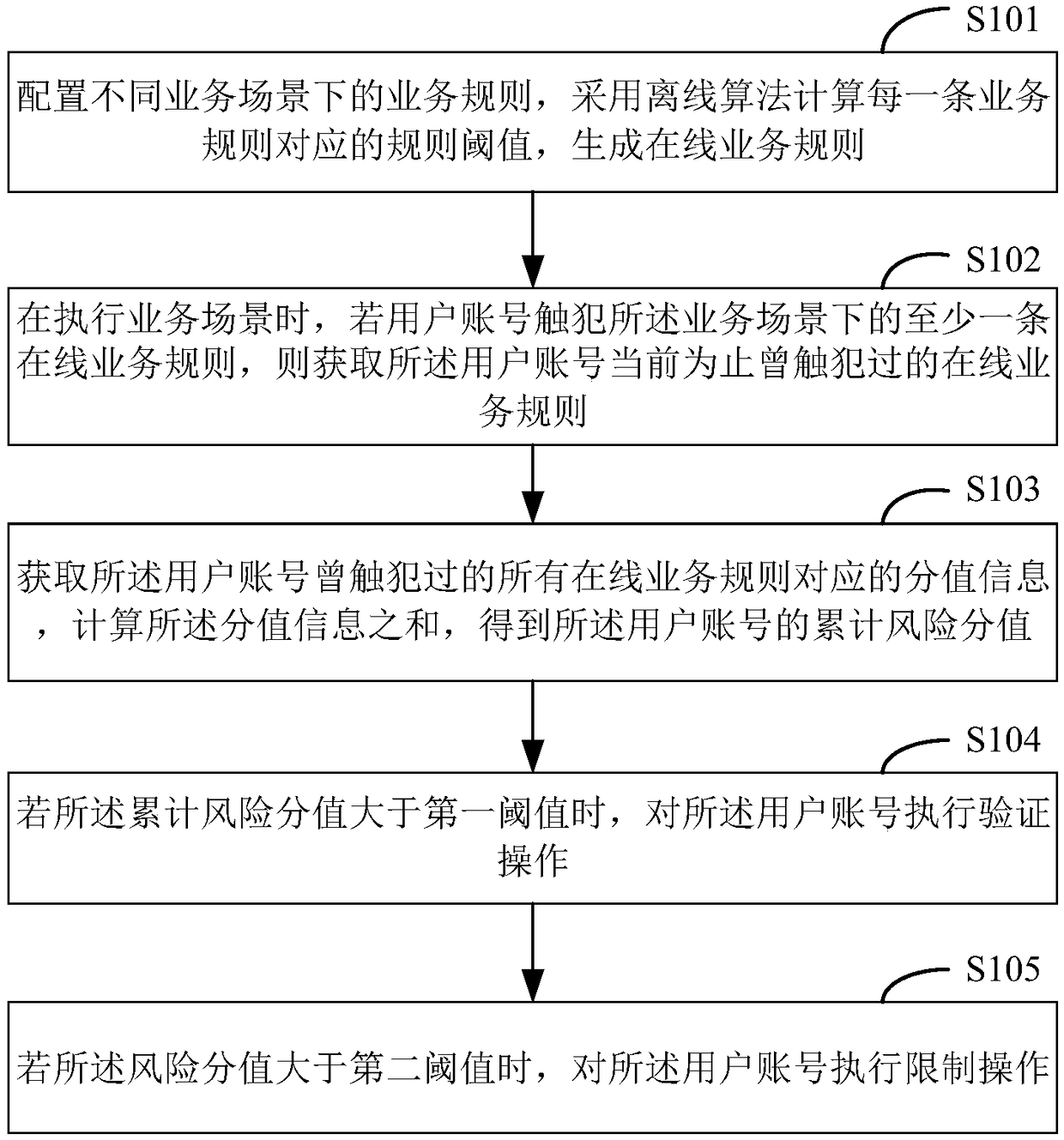
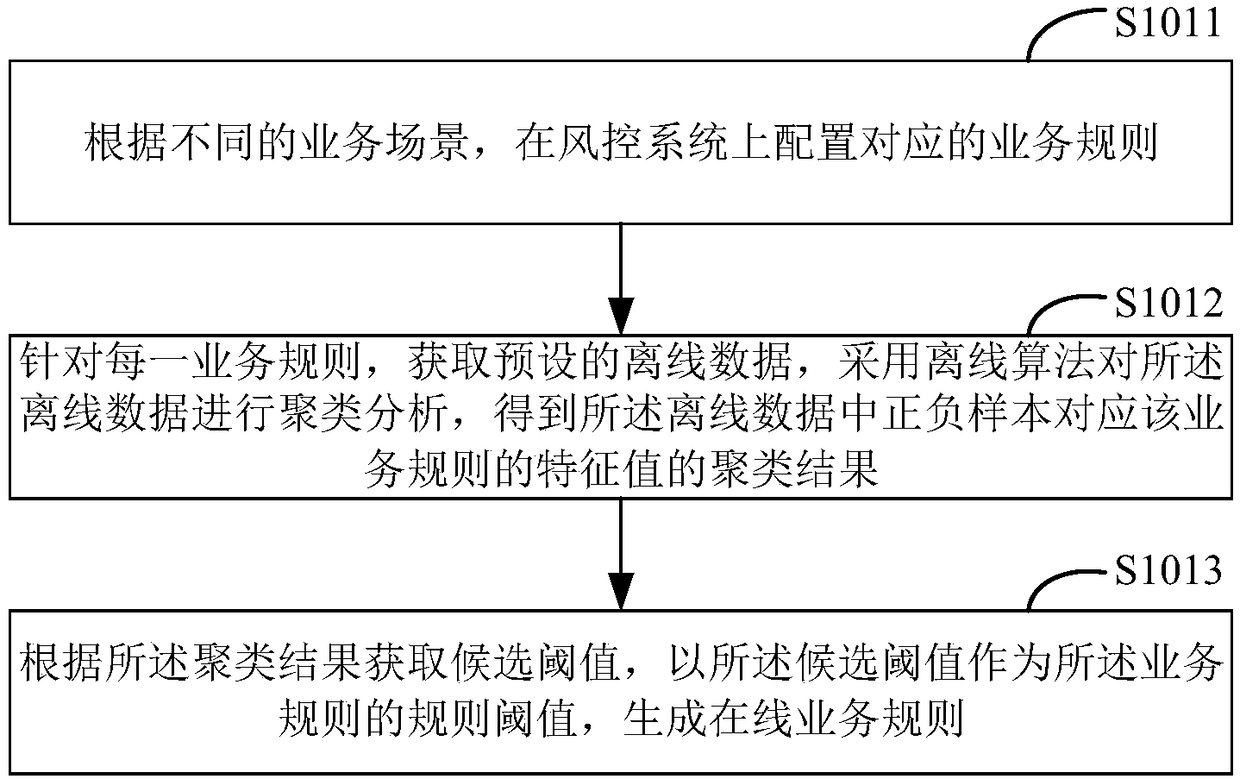
[0121] Figure 6 It is a schematic diagram of a terminal provided by an embodiment of the present invention, and the terminal includes but is not limited to a server and a mobile terminal. Such as Figure 6 As shown, the terminal 6 of this embodiment includes: a processor 60 , a memory 61 and a computer program 62 stored in the memory 61 and operable on the processor 60 . When the processor 60 executes the computer program 62, the steps in the above risk monitoring method embodiment are realized, for example figure 1 shown in steps S101 to S104, figure 2 Step S105 described in the embodiment, image 3 Steps S1011 to S1013 described in the embodiment and Figure 4 Steps S1021 to S1023 described in the embodiment, or, when the processor 60 executes the computer program 62, realizes the functions of the various modules / units in the above risk monitoring device embodiment, for example Figure 5 The functions of modules 51 to 54 are shown.
[0122] Exemplarily, the computer ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com