Safe Code Jumps and Execution Strobes
A security and software code technology, applied in the field of security code jump and execution gating, can solve problems such as vulnerability to attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
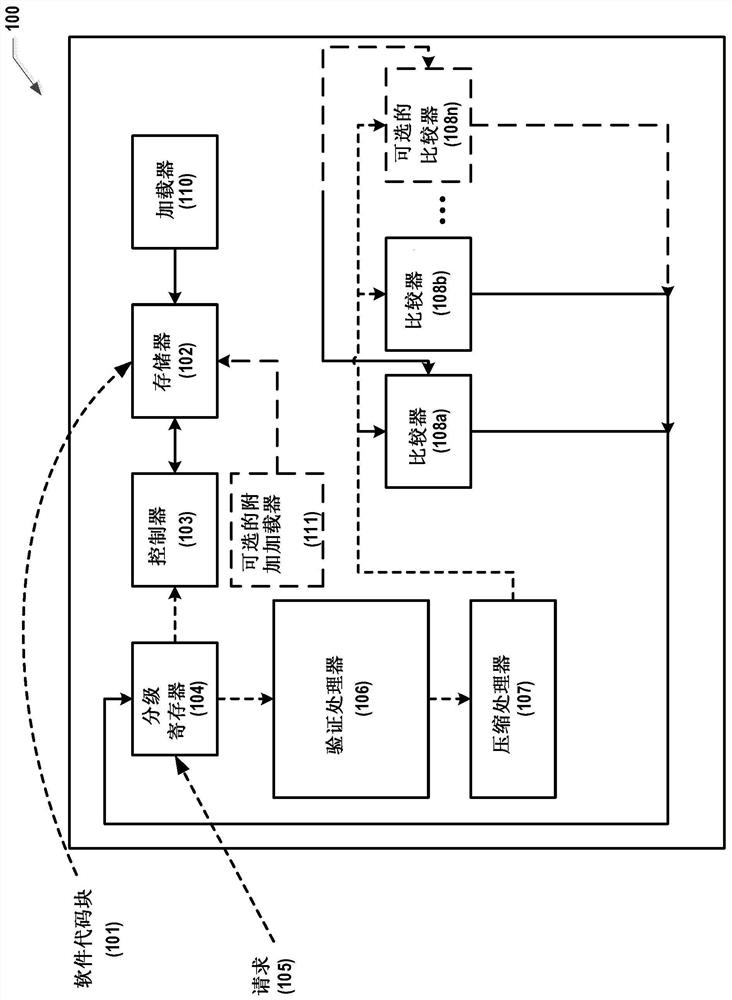
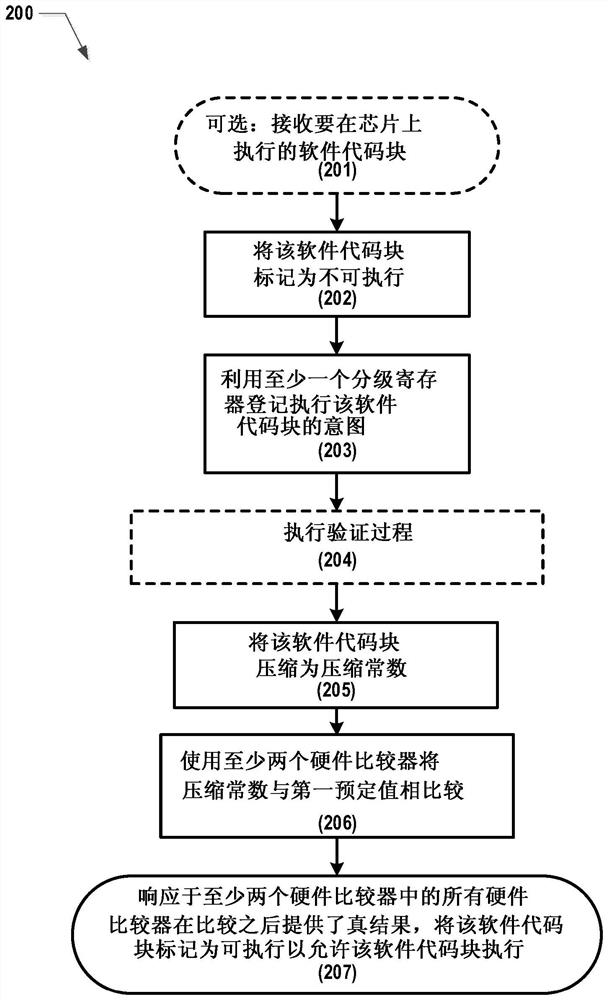
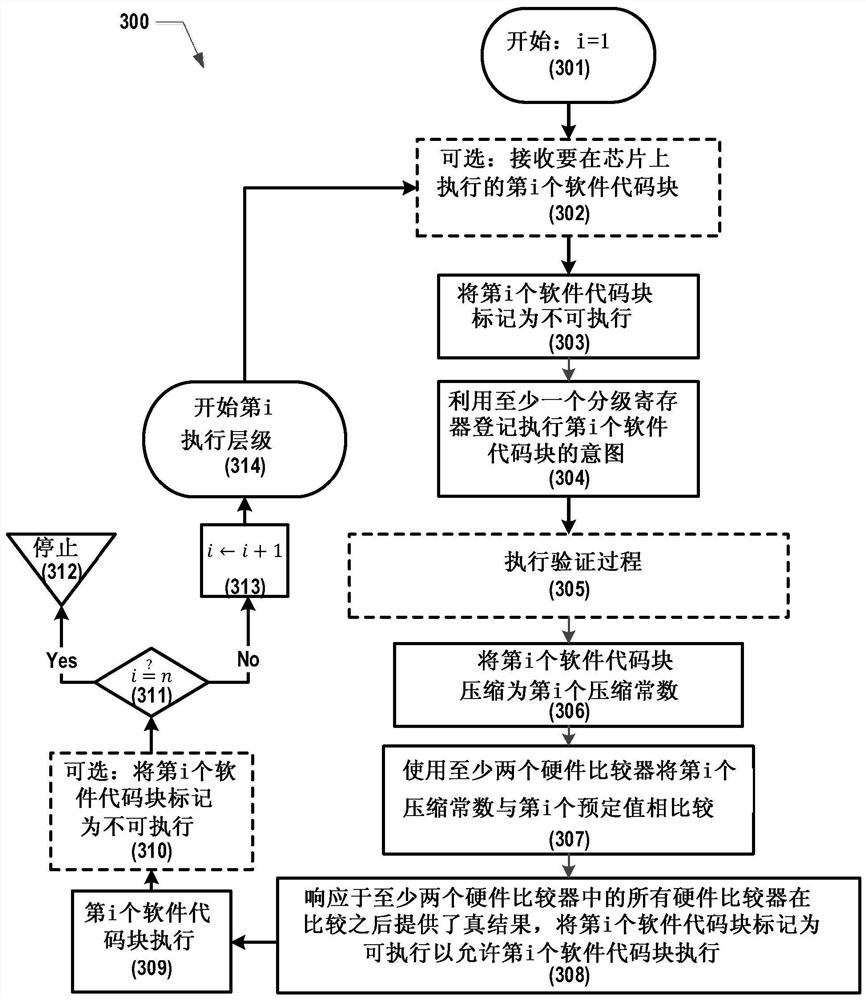
[0011] To prevent an attacker from being able to glitch IF / THEN conditional check operations, secure silicon-based systems benefit from glitch-resistant methods for jumping to verification code. A mechanism is needed to prevent glitches in IF / THEN conditional checks and prevent glitches from causing the system to jump to bad locations.
[0012] Even if conditional statements like IF statements are evaluated correctly, JUMP statements can be disturbed by glitches causing the system to jump to undesirable locations. Also, the JUMP statement may not be enclosed within a conditional block, which means it will be executed when execution reaches the point in the code where the JUMP statement appears. It may be possible to glitch on a JUMP statement that is not contained within a conditional block.
[0013] Therefore, in addition to preventing glitches that cause incorrect evaluation of conditional statements, it is also desirable to prevent execution of malicious code due to glitch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com