An intelligent authentication device and its working method
A technology of intelligent authentication and authentication methods, applied in data processing applications, finance, instruments, etc., can solve problems such as insecurity and fixed authentication methods, and achieve the effect of improving security and flexible authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
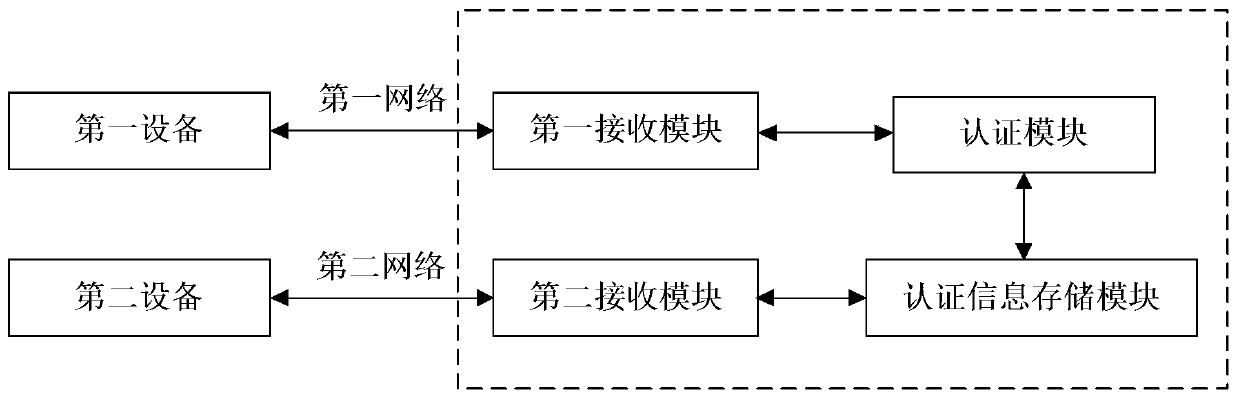
[0019] Such as figure 1 Shown, the structural block diagram of the preferred embodiment of the present invention.
[0020] In order to realize the authentication of the user, it is first necessary to establish the binding relationship between the user equipment, as well as the various authentication methods supported by the user equipment and the information corresponding to the above authentication methods; then when the first device conducts a transaction, from the above transaction information extract the user information, then determine the authentication mode according to the information provided by the second device, obtain corresponding information, and then authenticate the user information. In the above-mentioned authentication process, it is realized by the intelligent authentication device provided by the present invention; wherein, the intelligent authentication device includes:
[0021] The first receiving module: receiving transaction information from the first ...
Embodiment 2
[0036]On the basis of Embodiment 1, Embodiment 2 provides a working method of an intelligent authentication device, including a first receiving module that receives transaction information from the first device, obtains user information according to the transaction information, and sends it to the authentication device. module; the second receiving module receives the user input information from the second device, determines the mode of authenticating the user according to the user input information, and submits it to the authentication information storage module; the authentication information storage module determines the authentication information according to the second receiving module method, and send the authentication policy corresponding to the above authentication method and relevant information required for authentication to the authentication module; the relevant information includes not only the information necessary for the above authentication method, but also inf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com