Data processing methods and data processing devices
A technology of data and equipment, applied in the field of data processing and data processing equipment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
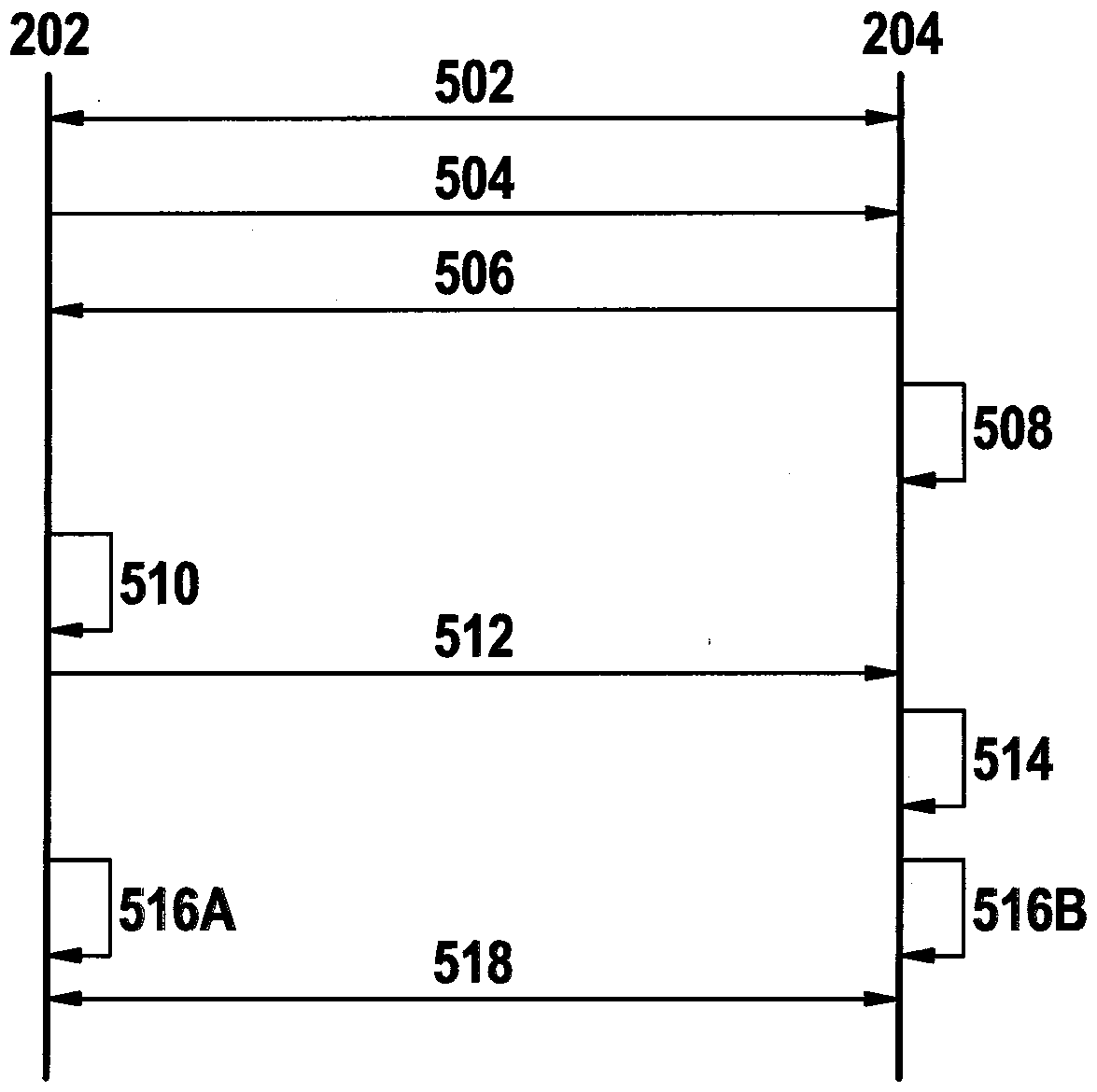
[0034] The devices and methods described below are especially suitable for protocols that conceptually include two phases: the first phase, in which a session key (Session Key) is negotiated via an asymmetric encryption method; the second phase phase, in this second phase, the session key is used in order to transmit the real valid data in an encrypted manner.
[0035] For encrypted transmission, eg Transport Layer Security (TLS) is used on the connection according to the Transmission Control Protocol. For User Datagram Protocol UDP connections, use Datagram Transport Layer Security DTLS or Quick UDP Internet Connection QUIC (QuickUDP Internet Connection).
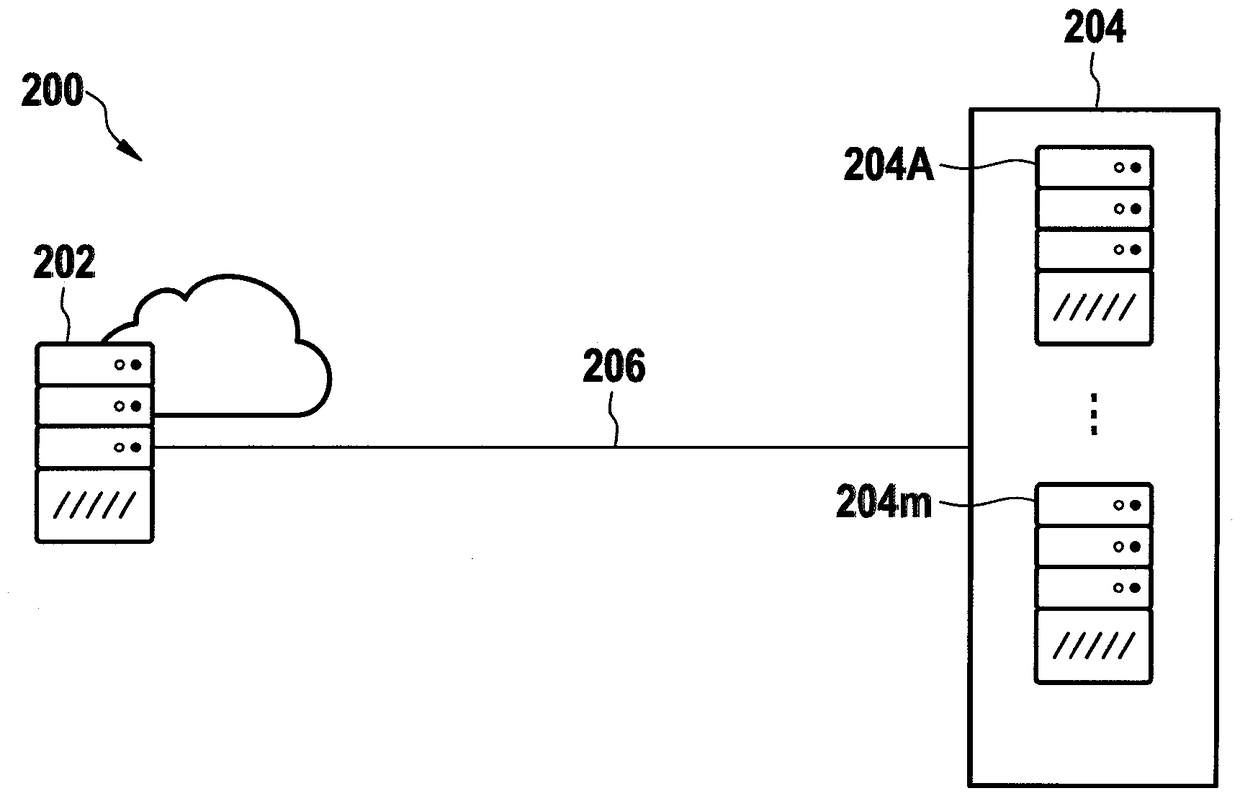
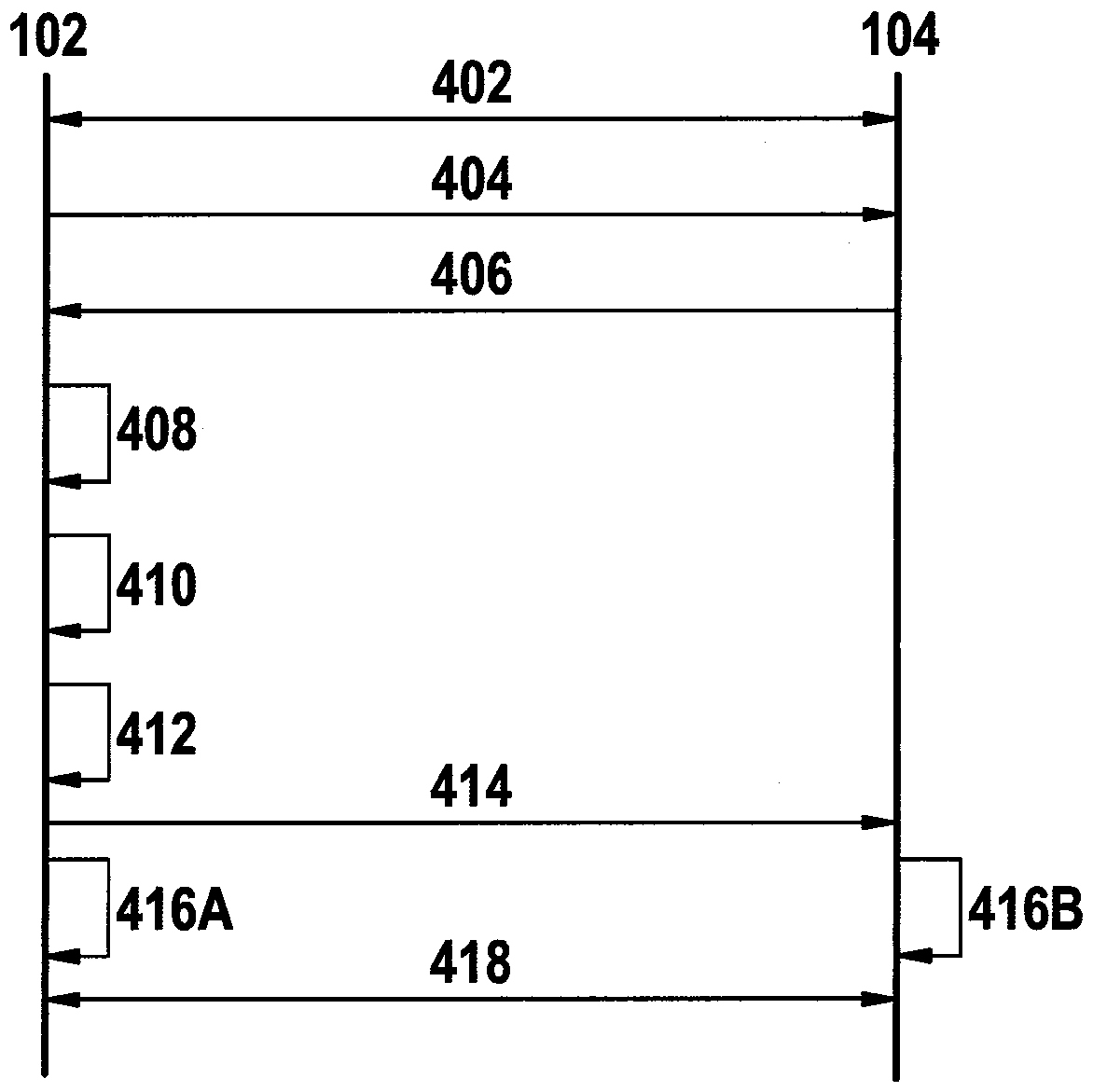
[0036] figure 1 Schematically shows part of a first computer network 100 in which a first terminal 102 and a second terminal 104 can be connected via a first Transmission Control Protocol connection 106 with Transport Layer Security (TLS).
[0037] The first terminal 102 includes a receiver which is designed to receive enc...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap