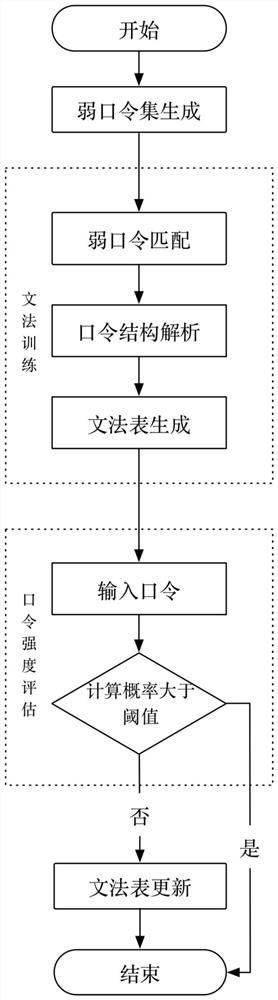
A password strength assessment method based on weak password derivation
A weak password and password technology, applied in the field of information security, can solve problems such as inability to judge, and achieve the effect of improving accuracy and enhancing capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
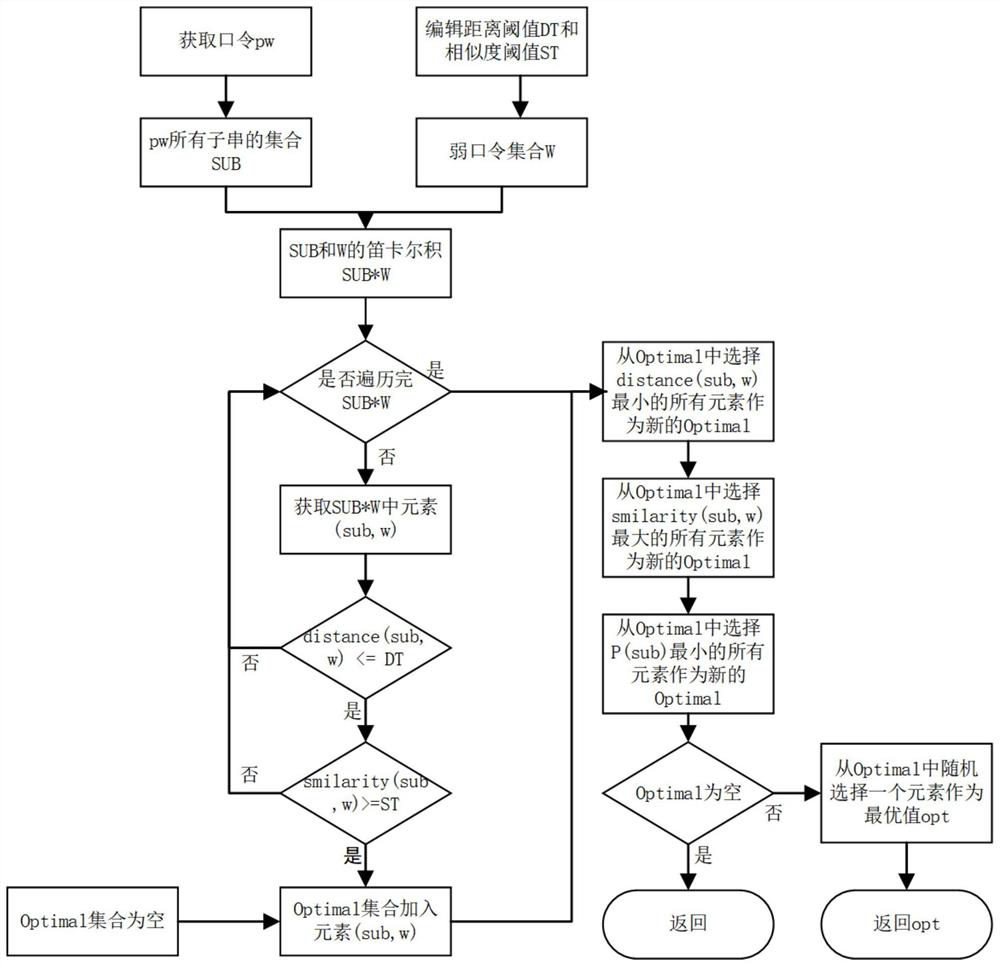
[0047] The meanings of relevant technical terms in this embodiment are as follows:
[0048] PCFG: Probabilistic Context Free Grammar
[0049] W: weak password set
[0050] w: element in W
[0051] Wn: passwords of length n in the weak password set (Lmin≤n≤Lmax)
[0052] Lmax: The maximum length of the password string that the target system allows to receive
[0053] Lmin: The minimum length of the password string that the target system allows to receive
[0054] T: training set
[0055] OLCS (Optimal Longest Common Subsequence): Optimal Longest Common Subsequence Algorithm
[0056] pw: the password to be parsed
[0057] SUB: the set of all substrings of pw
[0058] SUB×W: Cartesian product of SUB and W
[0059] sub: element in SUB
[0060] DT: edit distance threshold
[0061] ST: similarity threshold
[0062] V={Start,A,L,U,D,S,K,insert,delete,replace,no,W1,W2,...Wn}, is a set of non-terminal symbols, and its elements are called non-terminal symbols
[0063] ∑={95 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com