Login verification method and device, terminal device and storage medium
A technology of login verification and verification method, which is applied in the field of login verification methods, terminal equipment and storage media, and devices, and can solve the problems of reducing login security and low verification efficiency, so as to ensure login security, reduce verification operations, and improve verification The effect of efficiency and login efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
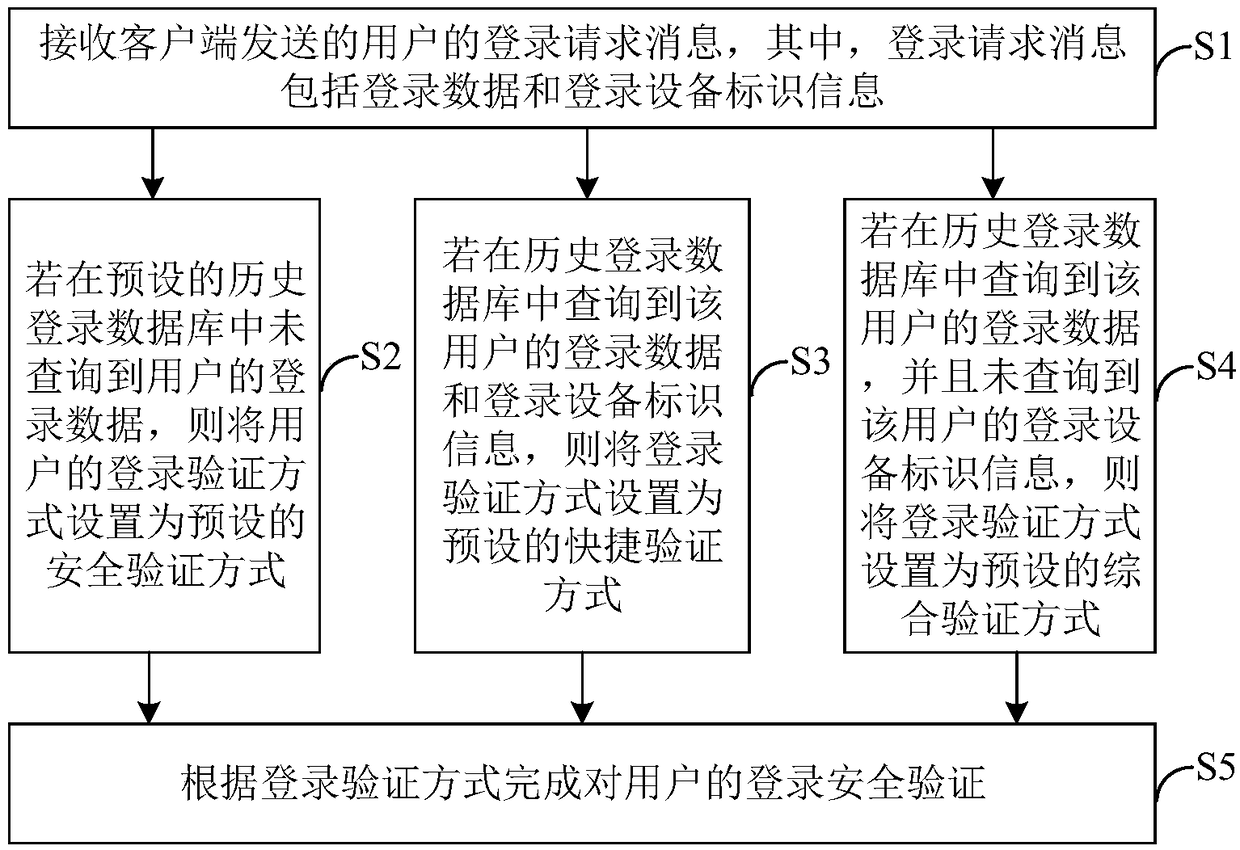
[0029] see figure 1 , figure 1 The implementation process of the login verification method provided by this embodiment is shown, and the details are as follows:
[0030] S1: Receive the user's login request message sent by the client, where the login request message includes login data and login device identification information.
[0031] Specifically, once the client detects that the login control is triggered, that is, after the user enters relevant and valid login data such as user name and password in the target application and clicks to log in, the client sends a login request message to the server. Wherein, the target application includes the management system of the mobile phone software or the webpage that the user is visiting.
[0032] In the embodiment of the present invention, the server receives the login request message sent by the client, and the login request message includes login data and login device identification information of the login device used by th...
Embodiment 2
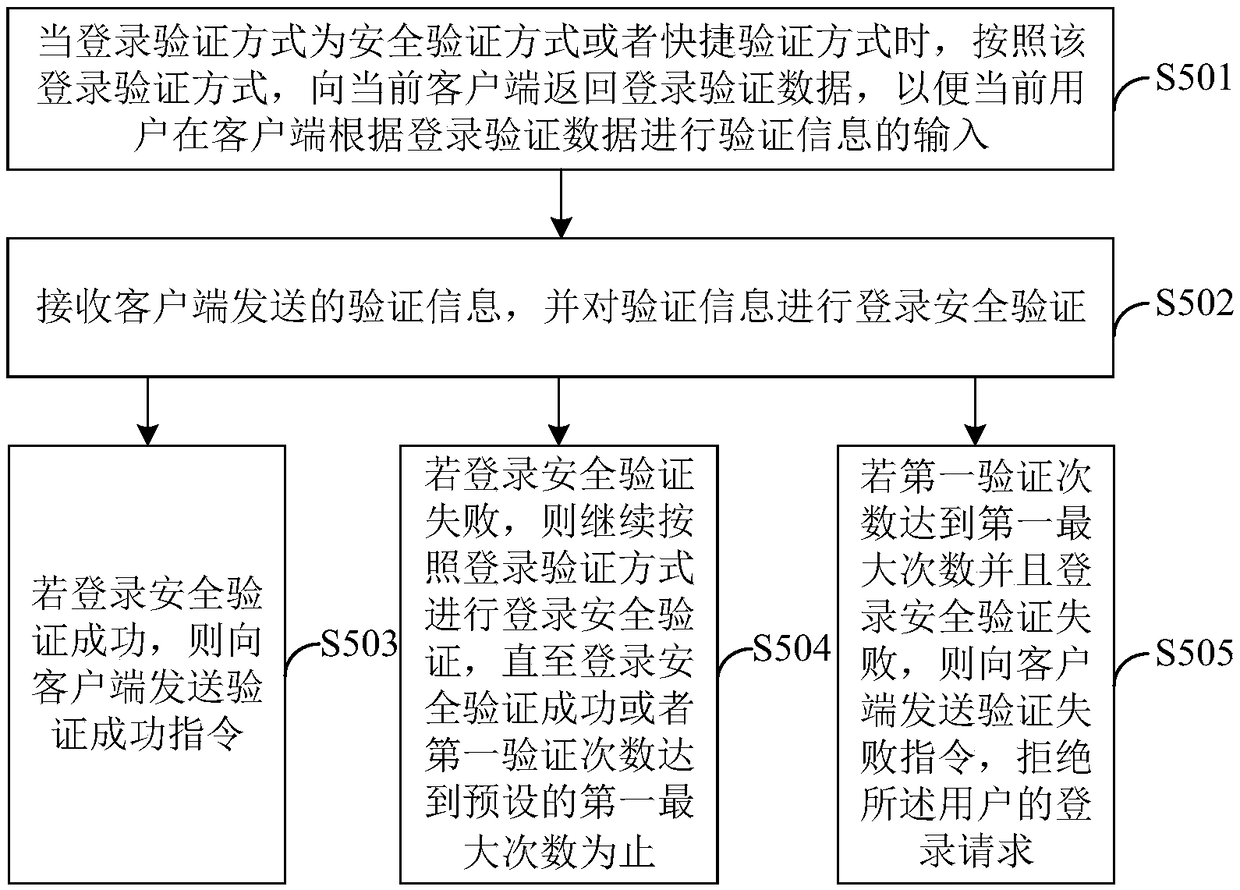
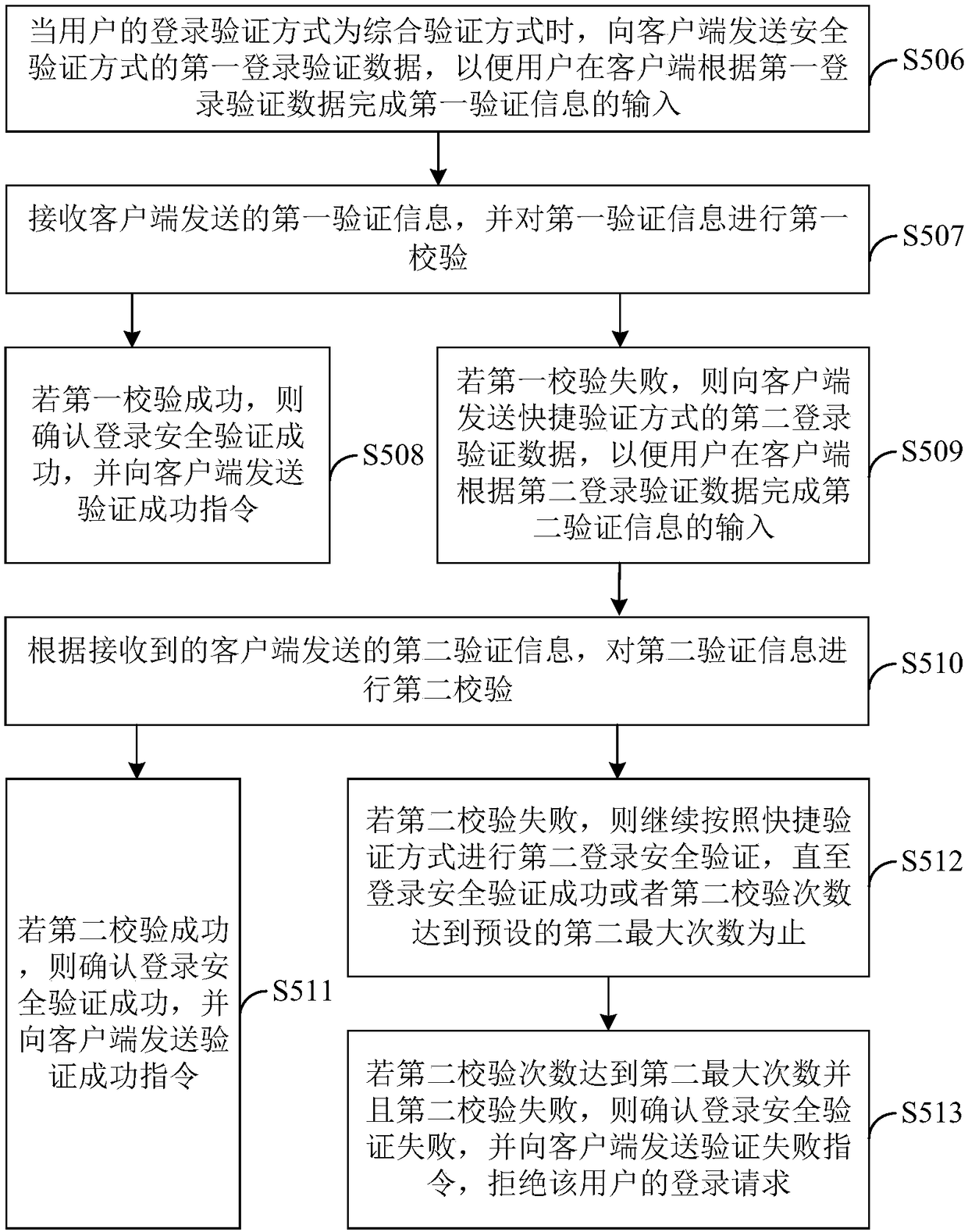
[0124] Corresponding to the login method in Example 1, Figure 5 The login verification device corresponding to the login verification method provided in Embodiment 1 is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown.
[0125] Such as Figure 5 As shown, the login verification device includes: a receiving module 51 , a security verification module 52 , a quick verification module 53 , a comprehensive verification module 54 , and a completion verification module 55 . The detailed description of each functional module is as follows:
[0126] The receiving module 51 is configured to receive a user's login request message sent by the client, wherein the login request message includes login data and login device identification information;
[0127] The security verification module 52 is used to set the user's login verification method to a preset security verification method if the user's login data is no...
Embodiment 3
[0159] This embodiment provides a computer-readable storage medium, and a computer program is stored on the computer-readable storage medium. When the computer program is executed by the processor, the login verification method in Embodiment 1 is implemented, or, when the computer program is executed by the processor Realize the functions of each module / unit in the login verification device in Embodiment 2. To avoid repetition, details are not repeated here.
[0160] It can be understood that the computer-readable storage medium may include: any entity or device capable of carrying the computer program code, recording medium, U disk, mobile hard disk, magnetic disk, optical disk, computer memory, read-only memory (Read- Only Memory, ROM), random access memory (Random Access Memory, RAM), electric carrier signal and telecommunication signal, etc.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com