Malicious-code family determination method and device
A malicious code and judgment method technology, applied in the field of information security, can solve the problems of inaccurate classification, incomplete triggering, and few behavior scalars, and achieve the effect of simplifying calculation and improving processing speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0028] Although the steps in the present invention are arranged with labels, they are not used to limit the order of the steps. Unless the order of the steps is clearly stated or the execution of a step requires other steps as a basis, the relative order of the steps can be adjusted.
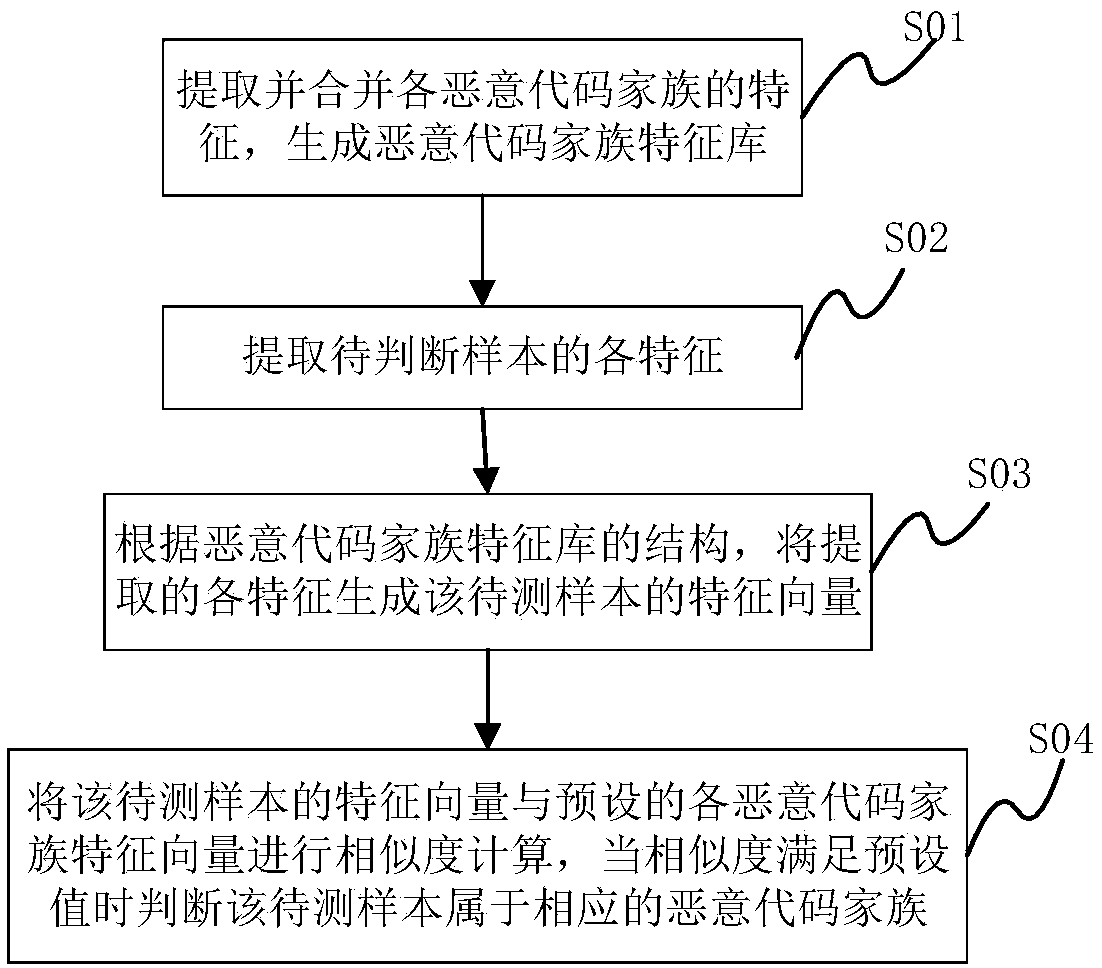
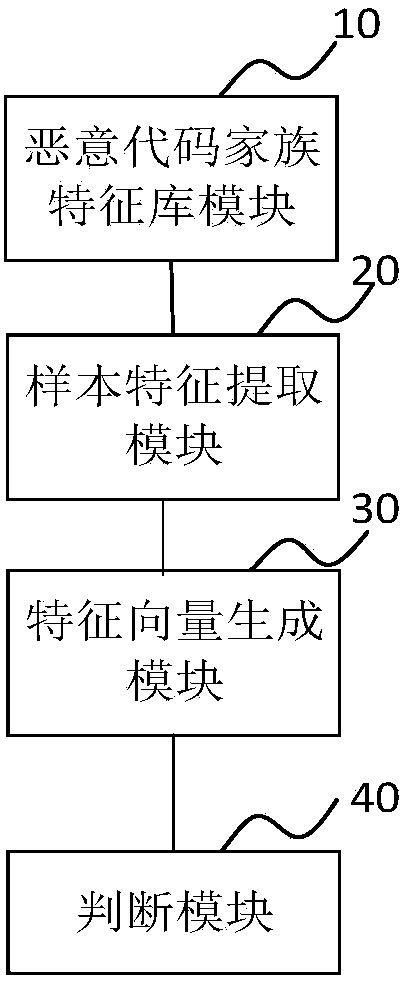
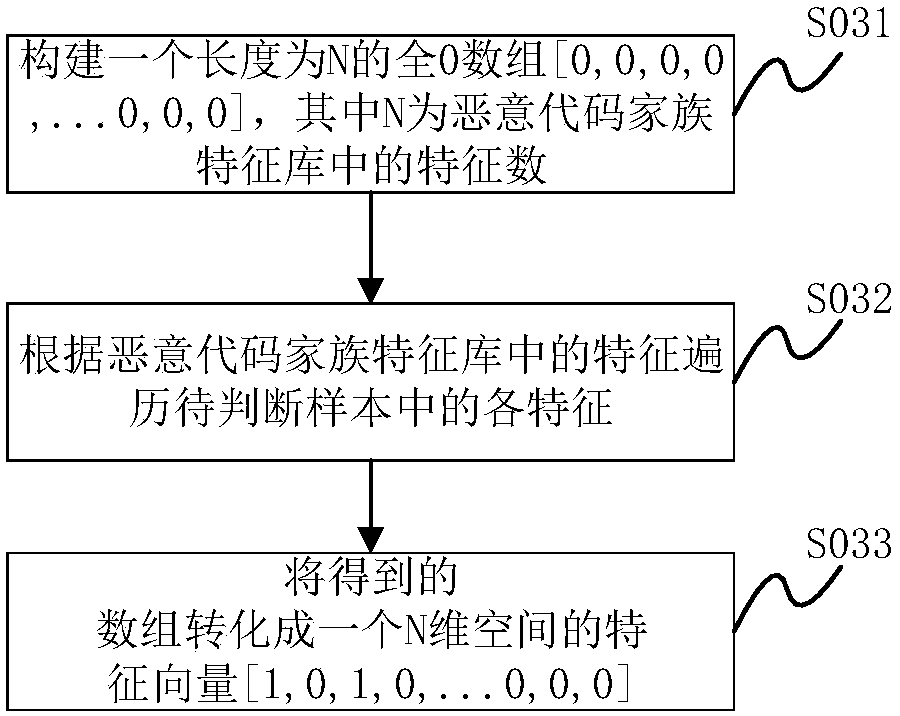
[0029] In some embodiments, such as figure 1 As shown, the method for judging malicious code family includes the following steps:
[0030] S01: Extract and merge the characteristics of each malicious code family to generate a malicious code family feature database.
[0031] Malicious code wants to complete its malicious behavior, and has obvious appearance characteristics in code writing, behavior, etc.; and malicious code of the same family (that is, the same behavior pattern or the sa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com