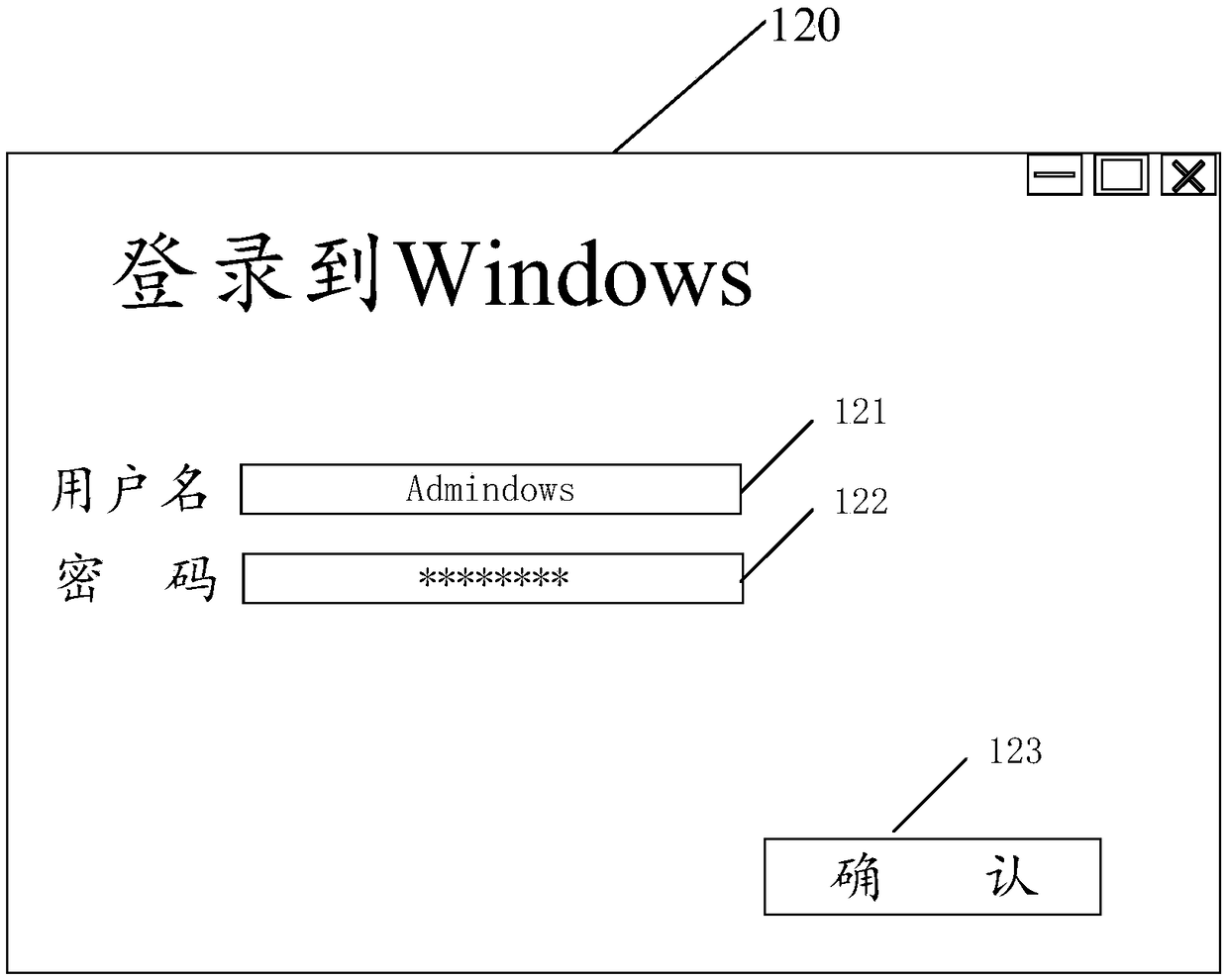
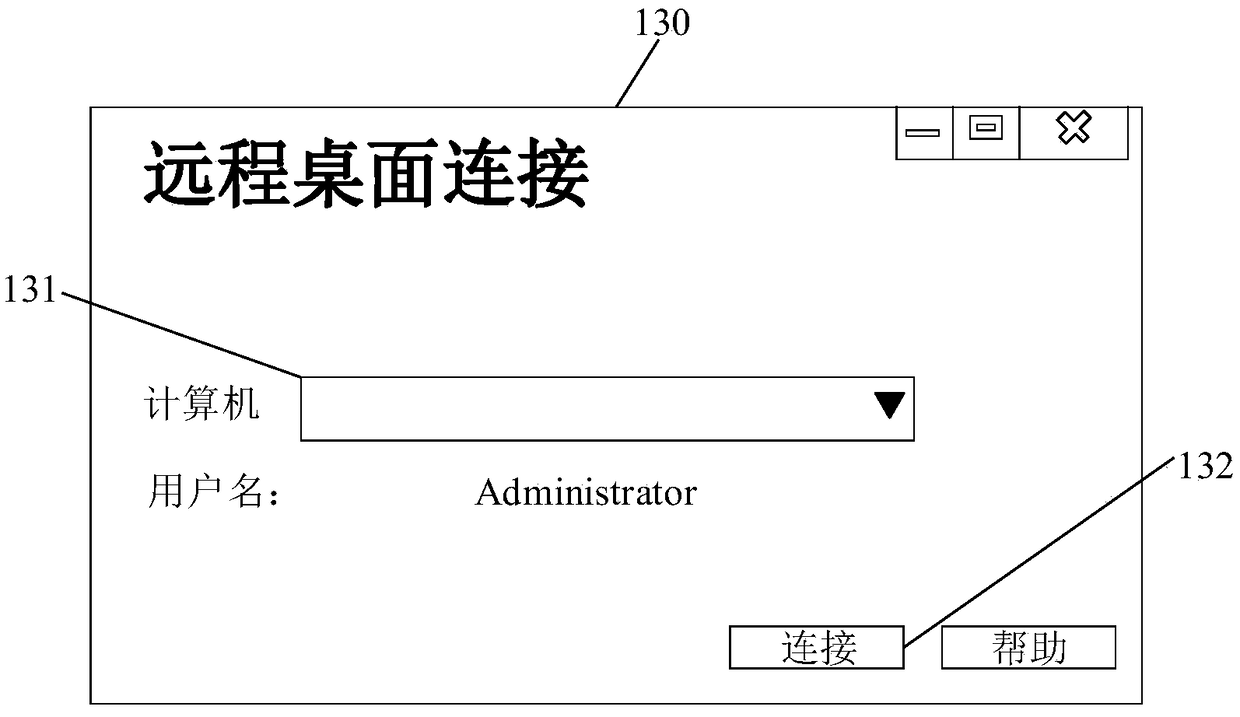
Verification method and device used for server log-in
A verification method and server technology, applied in the verification method and device field of server login, can solve the problems of being unable to block weak password attacks of hackers and low security of Windows servers, so as to increase the complexity of verification and reduce the possibility of brute force cracking, The effect of reducing the waste of network resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
[0100]Embodiment 1: The user terminal that initiates the server login request and intercepts the server login request by the same device. Specifically, an interception application plug-in for intercepting the login request of the server is installed on the user terminal, and the interception application plug-in runs on the user terminal. When the user terminal initiates a server login request, the server login request is intercepted by an interception application plug-in running on the user terminal.
Embodiment approach 2
[0101] Embodiment 2: The user terminal that initiates the server login request and the device that intercepts the server login request do not belong to the same device. Specifically, the device that intercepts the server login request is an intermediate device between the target server and the user terminal that initiates the server login request. The user terminal initiates a server login request to the target server through the intermediate device, and the intermediate device intercepts the user terminal.
Embodiment approach 3
[0102] Embodiment 3: An interception application plug-in for intercepting server login requests is installed on the device where the target server is located. When the user terminal initiates a server login request, the server login request is intercepted by the interception application plug-in running on the device where the target server is located.
[0103] In the specific implementation process, the server login request initiated by each user terminal can be intercepted, and then steps S102 to S103 are executed to verify whether each server login request initiated by each user terminal needs to be sent to the target server . This implementation can absolutely ensure the security of the target server.
[0104] In the specific implementation process, in order to improve the timeliness of server login. It is also possible to set the interception conditions for intercepting the server login request. When the current situation meets the set interception conditions, the server ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com