A method, system, device and storage medium for discovering potential threats in a network
A potential and network technology, applied in the field of discovering potential threats in the network, can solve problems such as poor flexibility, difficulty in changing camouflage methods and specific parameters, and poor integration, so as to achieve better use effect, flexible camouflage deployment and change, and good camouflage effect of effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
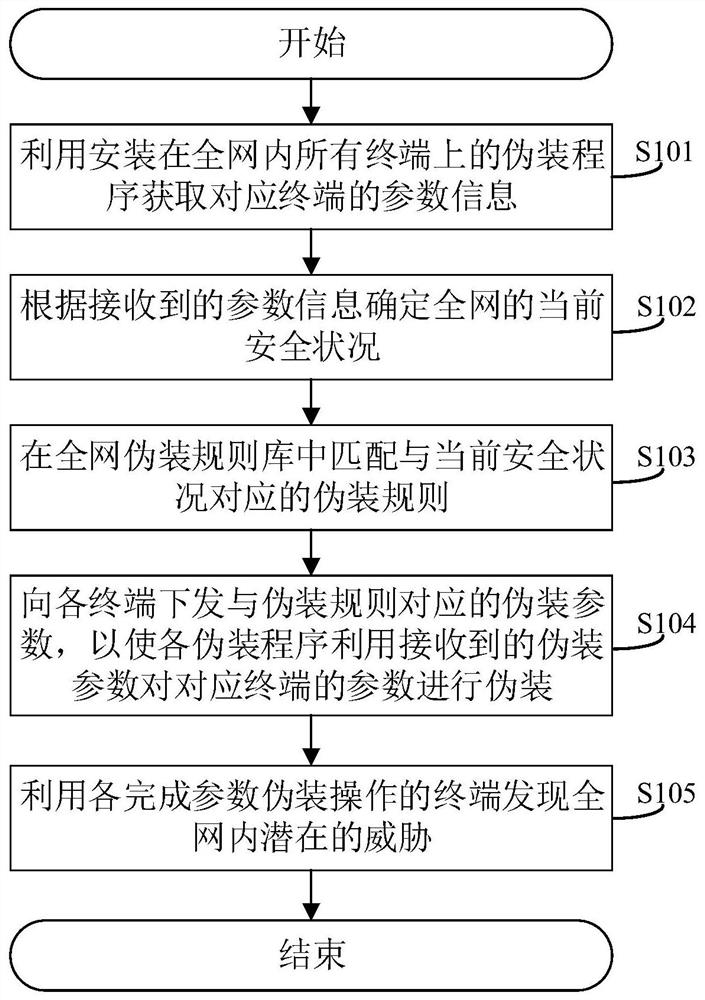
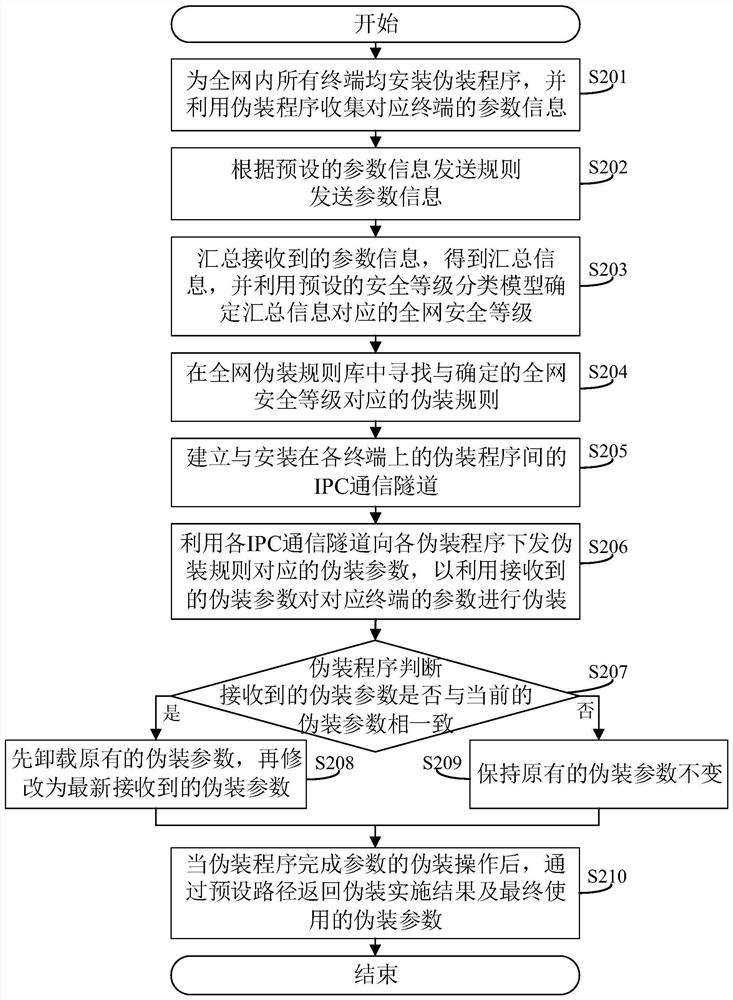
[0067] The core of this application is to provide a method, system, device and computer-readable storage medium for discovering potential threats in the network, directly install the camouflage program on each terminal, and directly modify the external information without affecting the normal use of each terminal. Some parameters are used to lure malicious attackers to take the bait. Since the parameters for camouflage are usually limited to common parameters such as IP, port, and service, and only create a false impression for the outside world, the computing resources occupied are negligible. At the same time, the upper-level centralized management platform is used Combined with the current security status of the entire network, comprehensively plan how each terminal needs to camouflage to achieve a better camouflage effect as a whole. Since each camouflage program only needs to camouflage the parameters of the terminal where it is located, camouflage deployment and changes ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com