Water-cooling 5G computer host system based on information security and water-cooling self-destruction method
An information security, computer host technology, applied in the direction of data processing power supply, electrical digital data processing, internal/peripheral computer component protection, etc., can solve the problem that technology has no way to protect information, achieve good camouflage, good cloud communication mode Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
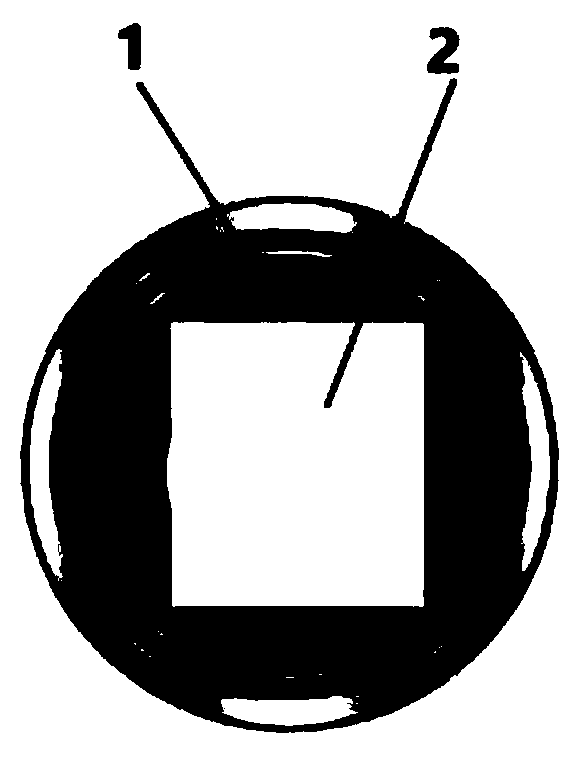
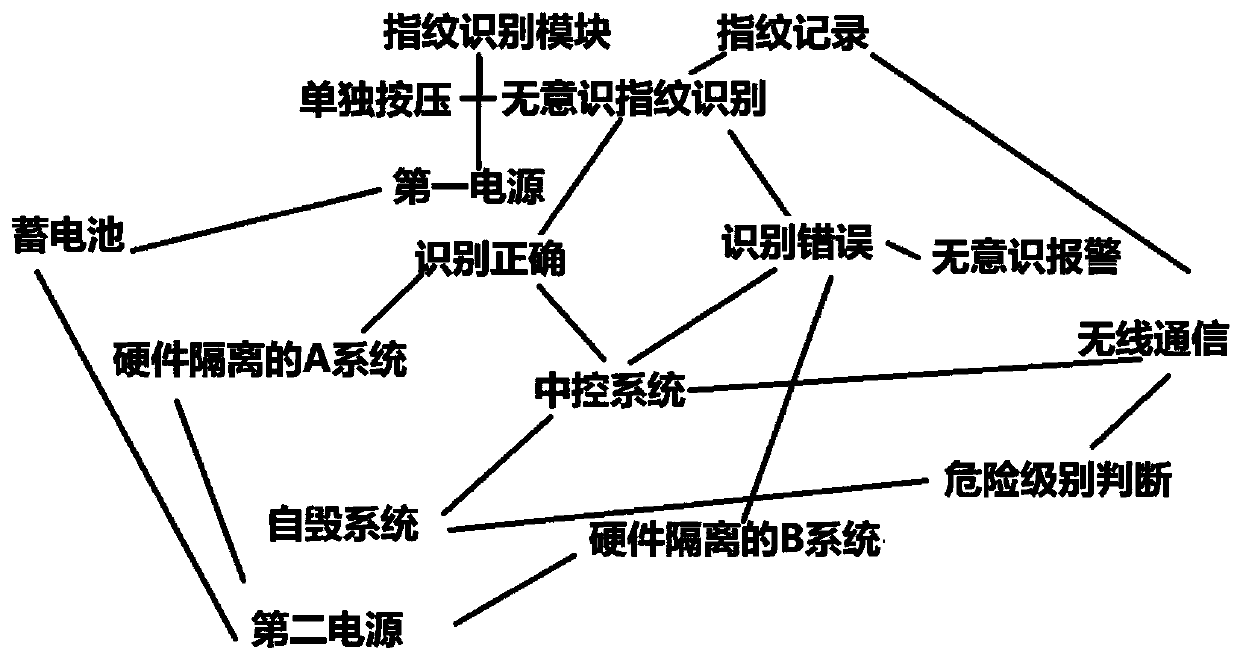
[0062] Embodiment 1: Combining all the accompanying drawings; an unconscious security computer system with 5G dual hardware isolation in the anti-theft tomb, characterized in that the unconscious security computer system includes button 1, which is the start button of the computer, and the extrusion head of the button Hollow, on which the identification area 2 is arranged, and the fingerprint identification system 10 is arranged in the middle of the extrusion head, and also includes a button battery 11 or a mains power system that can supply power to the fingerprint identification system 10; the fingerprint identification system 10 is connected to the boot control part in communication The computer includes two sets of systems, the systems are hardware systems, and the two sets of hardware systems each include a storage battery, which are respectively A system storage battery 20 and B system storage battery 21, and the A system storage battery 20 and the B system storage battery...
Embodiment 2
[0067] Embodiment 2: As a further improved solution or a side-by-side solution or an optional independent solution, the power-on control part is a separate chip, which can collect and judge the recognition effect of the fingerprint recognition system; Communication, at the same time communicate with the remote security host; the person with the correct fingerprint needs to stay on the power button for a while to allow the fingerprint recognition to be successfully turned on. The substantive technical effect and its realization process that the technical scheme of this place plays are as follows: that is to say, in case time stays not enough, proves that the person who starts the machine is not familiar with this main frame, so just proves that there is no power-on authority. That is to say, there is also the requirement to start the action, which is a groundbreaking improvement.
Embodiment 3
[0068] Embodiment 3: As a further improved solution or a side-by-side solution or an optional independent solution, the fingerprint recognition is an unaffected silent recognition, no matter which system is turned on, the external display during the boot process is consistent. The substantive technical effect and the realization process of the technical solution here are as follows: do not startle the snake, and facilitate safety management.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com