Service processing method and apparatus based on identity information
A technology for identity information and business processing, applied in the field of information management, can solve the problems of non-recovery of arrears, harassment, non-real-name mobile number telecommunication fraud, etc., and achieve the effect of reducing telecommunication fraud
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0026] This embodiment provides a business processing method based on identity information, which is used to clean abnormal numbers based on the total data of user identity information of registered mobile numbers nationwide, avoid the existence of unlicensed numbers, and effectively reduce telecommunications fraud. The execution subject of this embodiment is a service processing device based on identity information (hereinafter referred to as the device), which can be installed in the operator's user management system or in a terminal, such as a server, desktop computer, notebook computer, etc.
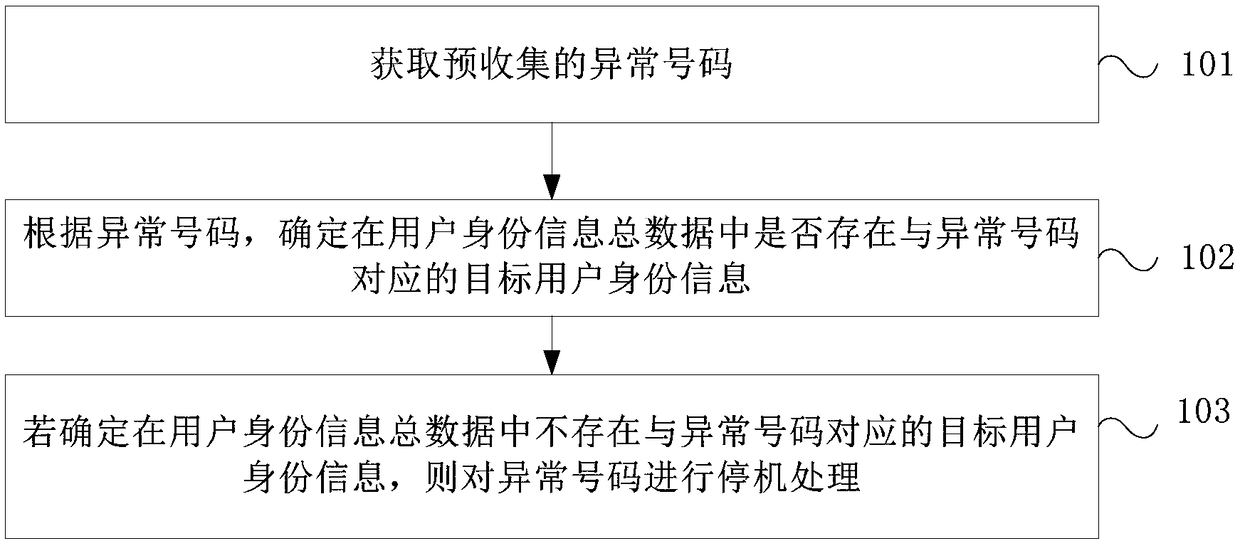
[0027] Such as figure 1 As shown, it is a schematic flowchart of the identity information-based business processing method provided in this embodiment, the method includes:
[0028] Step 101, obtain pre-collected exception numbers.
[0029] Specifically, all known abnormal numbers such as fraud phone numbers and malicious blacklist numbers can be collected, and a blacklist database ...
Embodiment 2
[0039] This embodiment provides a further supplementary description of the service processing method based on identity information provided in the first embodiment.
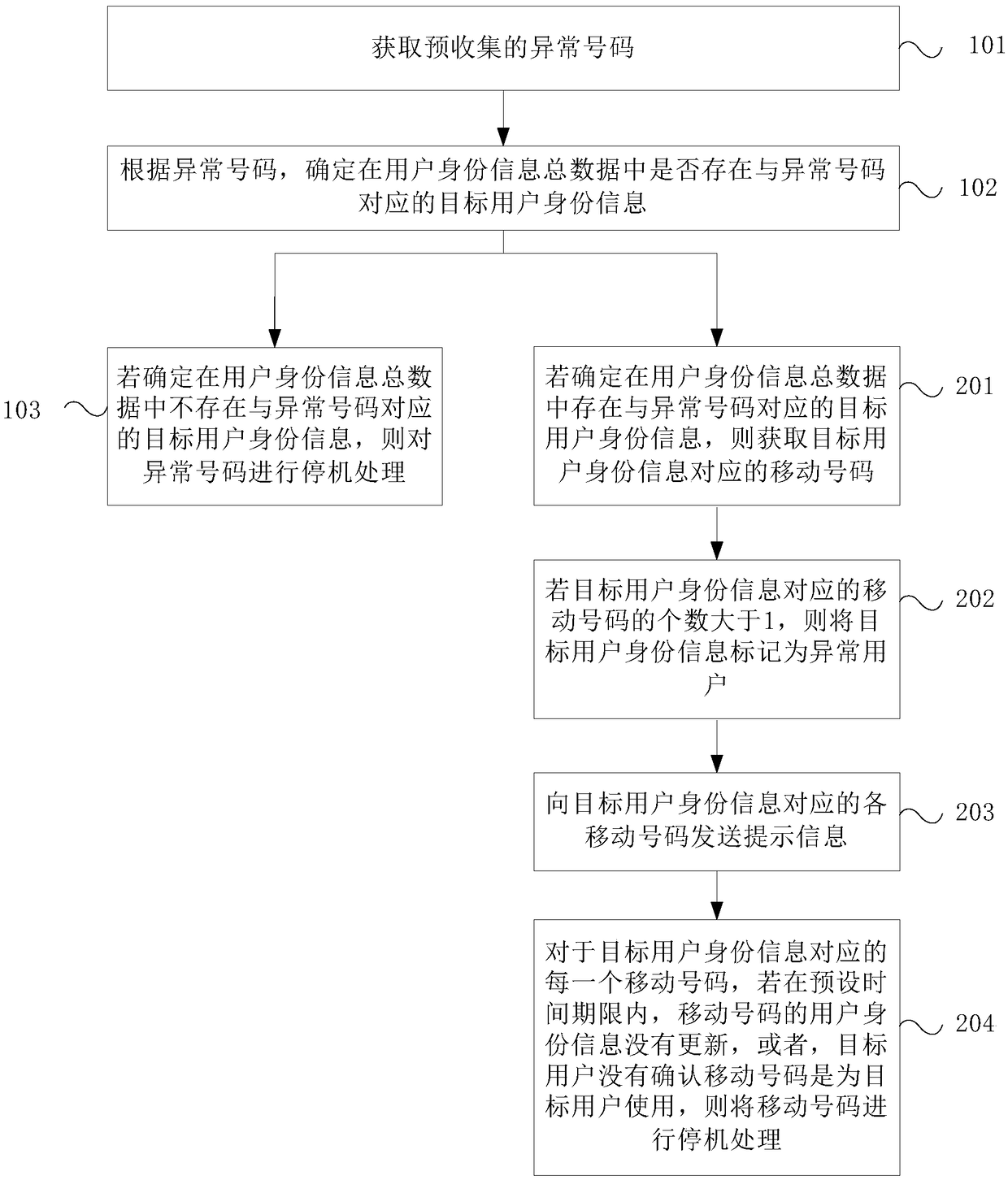
[0040] Such as figure 2 As shown in , it is a schematic flowchart of the service processing method based on identity information provided in this embodiment. On the basis of the first embodiment above, optionally, the method further includes:
[0041] Step 201, if it is determined that the target user identity information corresponding to the abnormal number exists in the total user identity information data, then acquire the mobile number corresponding to the target user identity information.
[0042] Specifically, if it is determined that there is target user identity information corresponding to the abnormal number in the total user identity information data, it means that the abnormal number is a real-name number, but the possibility of identity information theft cannot be ruled out. Therefore, the target u...
Embodiment 3
[0059] This embodiment provides an identity information-based service processing device, which is used to execute the identity information-based service processing method in the first embodiment above.
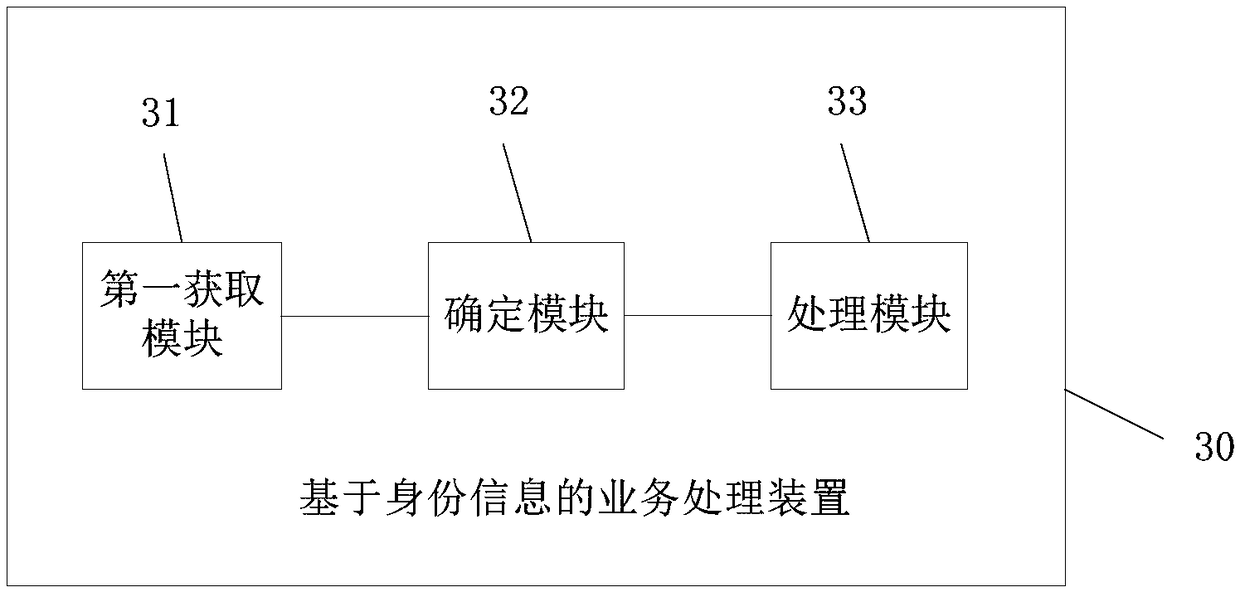
[0060] Such as image 3 As shown in , it is a schematic structural diagram of an identity information-based service processing device provided in this embodiment. The identity information-based business processing device 30 includes a first acquisition module 31 , a determination module 32 and a processing module 33 .
[0061] Wherein, the first acquisition module 31 is used to obtain the pre-collected abnormal number; the determination module 32 is used to determine whether there is target user identity information corresponding to the abnormal number in the total data of user identity information according to the abnormal number, and the total data of user identity information Including the user identity information of registered mobile numbers within the preset geographica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com