Method and system for quickly sensing, locating and verifying vulnerability
A vulnerability and fast technology, applied in the field of information asset security, can solve the problems of general crawler technology search scale, update speed and personalization can not meet the needs of users, and achieve the effect of reasonable structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] Embodiments of the present invention will be described in detail below. It should be emphasized that the following description is only exemplary and not intended to limit the scope of the invention and its application.
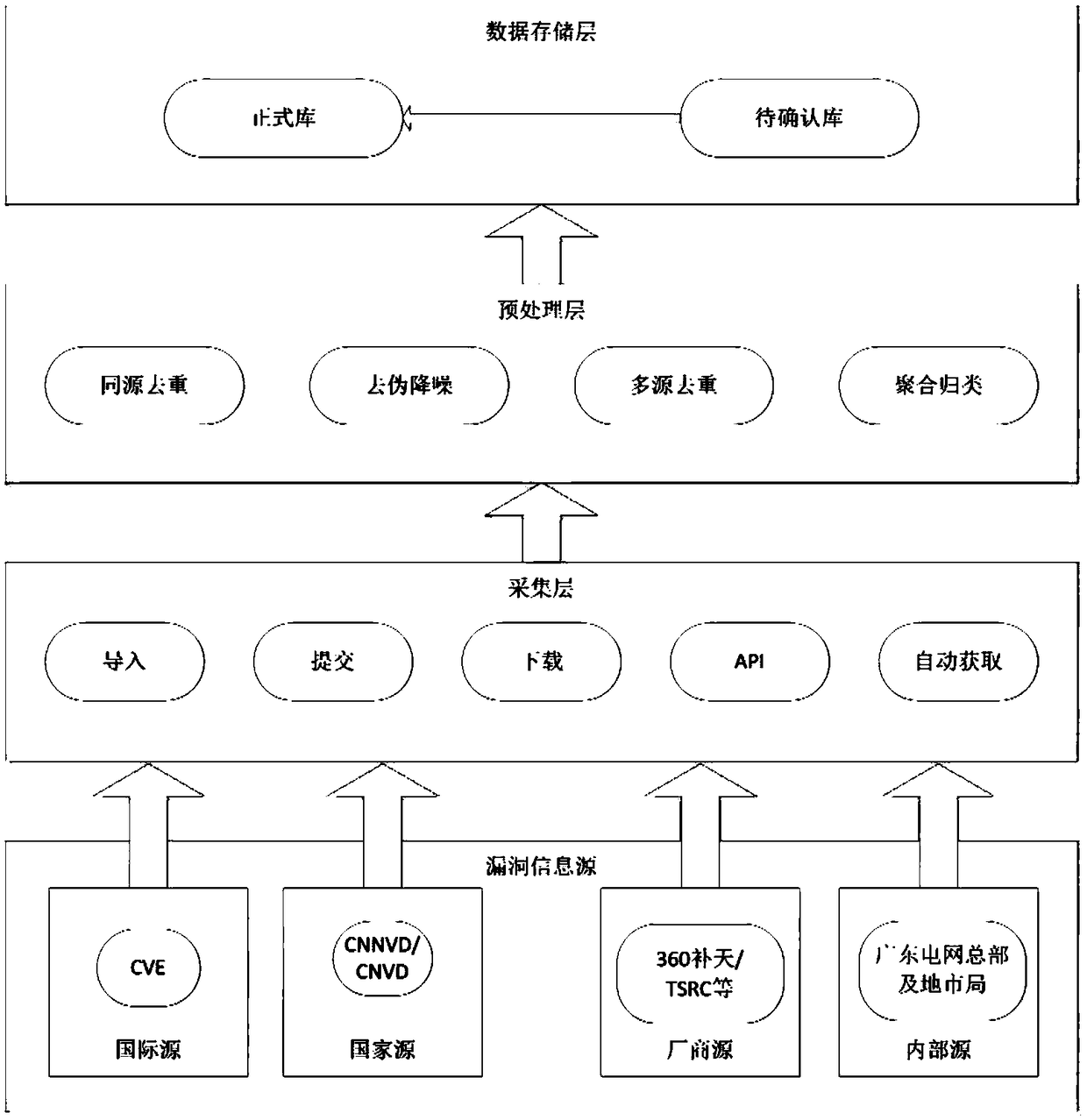
[0046] refer to figure 1 , in one embodiment, a system for realizing fast perception, location and verification of vulnerabilities, characterized in that it includes a vulnerability awareness module, and the vulnerability awareness module includes:
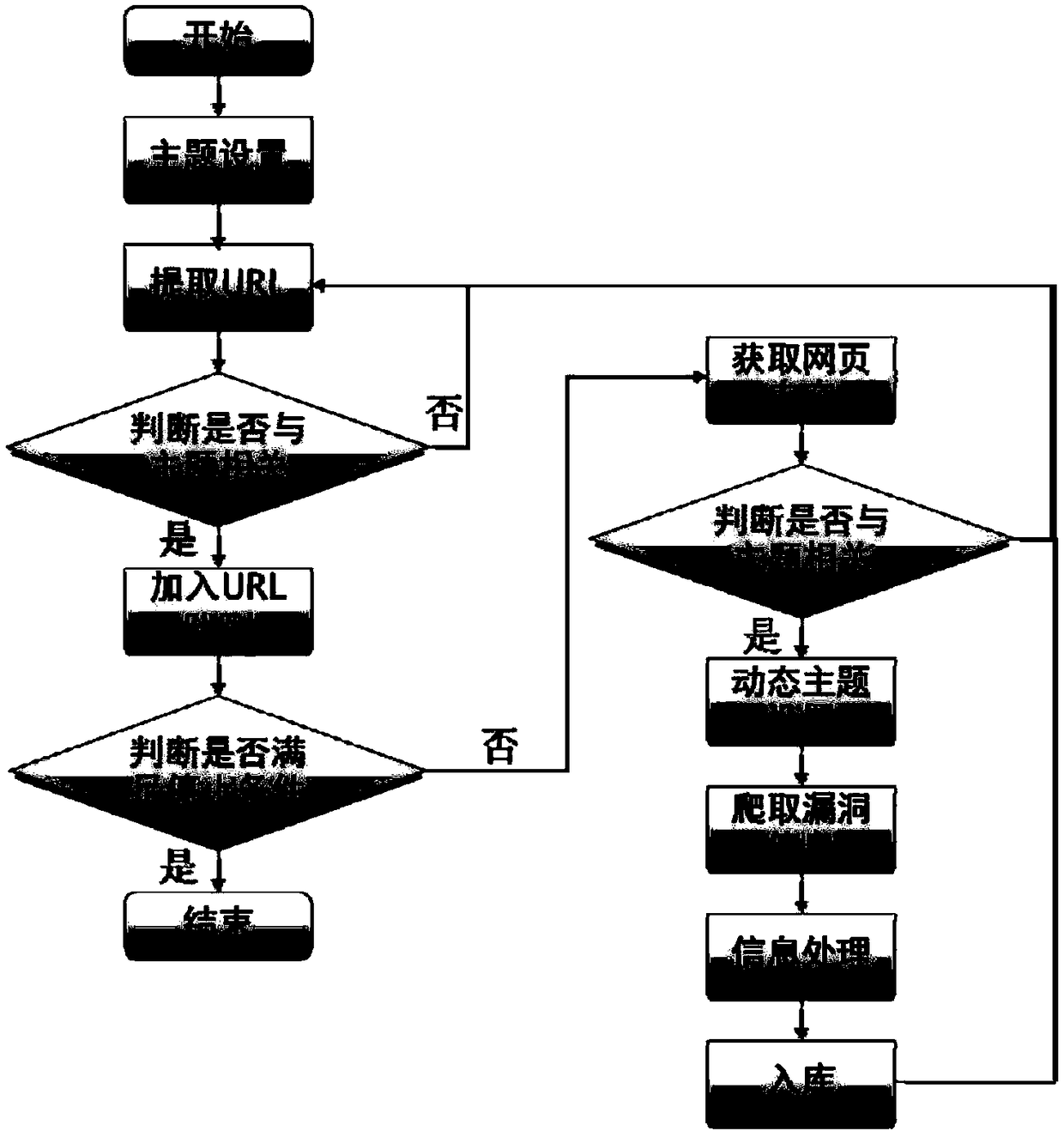
[0047] The vulnerability information collection layer obtains the vulnerability information from the vulnerability information source through the vulnerability information collection technology;
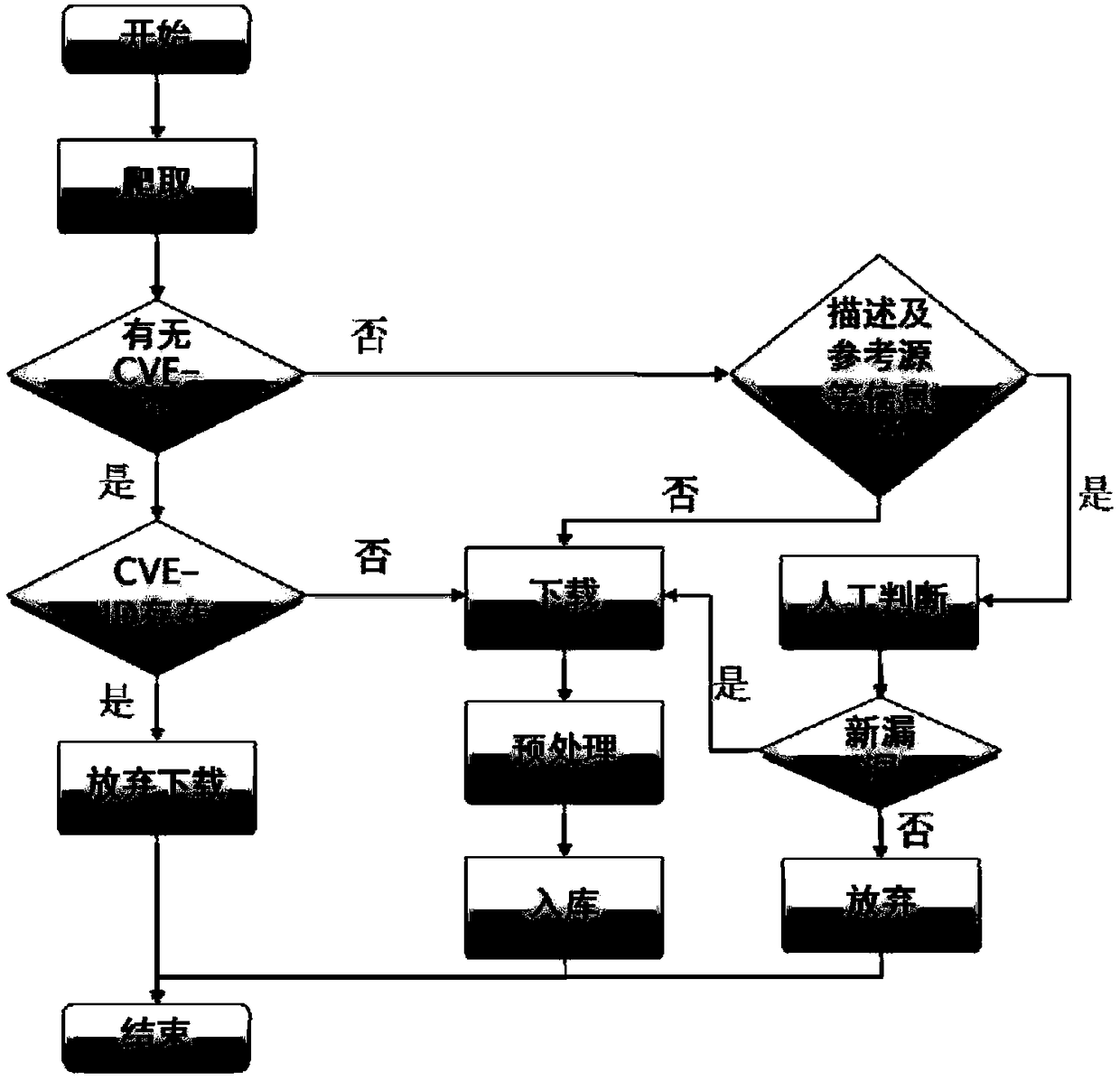
[0048] The vulnerability information preprocessing layer preprocesses the vulnerability information obtained by the vulnerability information collection layer, and sends the vulnerability information to the vulnerability data storage layer according to the processing result;
[0049] The vulnerability data stora...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com