Login authentication method, automatic login authentication method, server and client
A login verification and automatic login technology, which is applied in the Internet field, can solve the problem of low security and achieve the effect of improving security and protecting information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] Multiple embodiments disclosed in this specification will be described below in conjunction with the accompanying drawings.
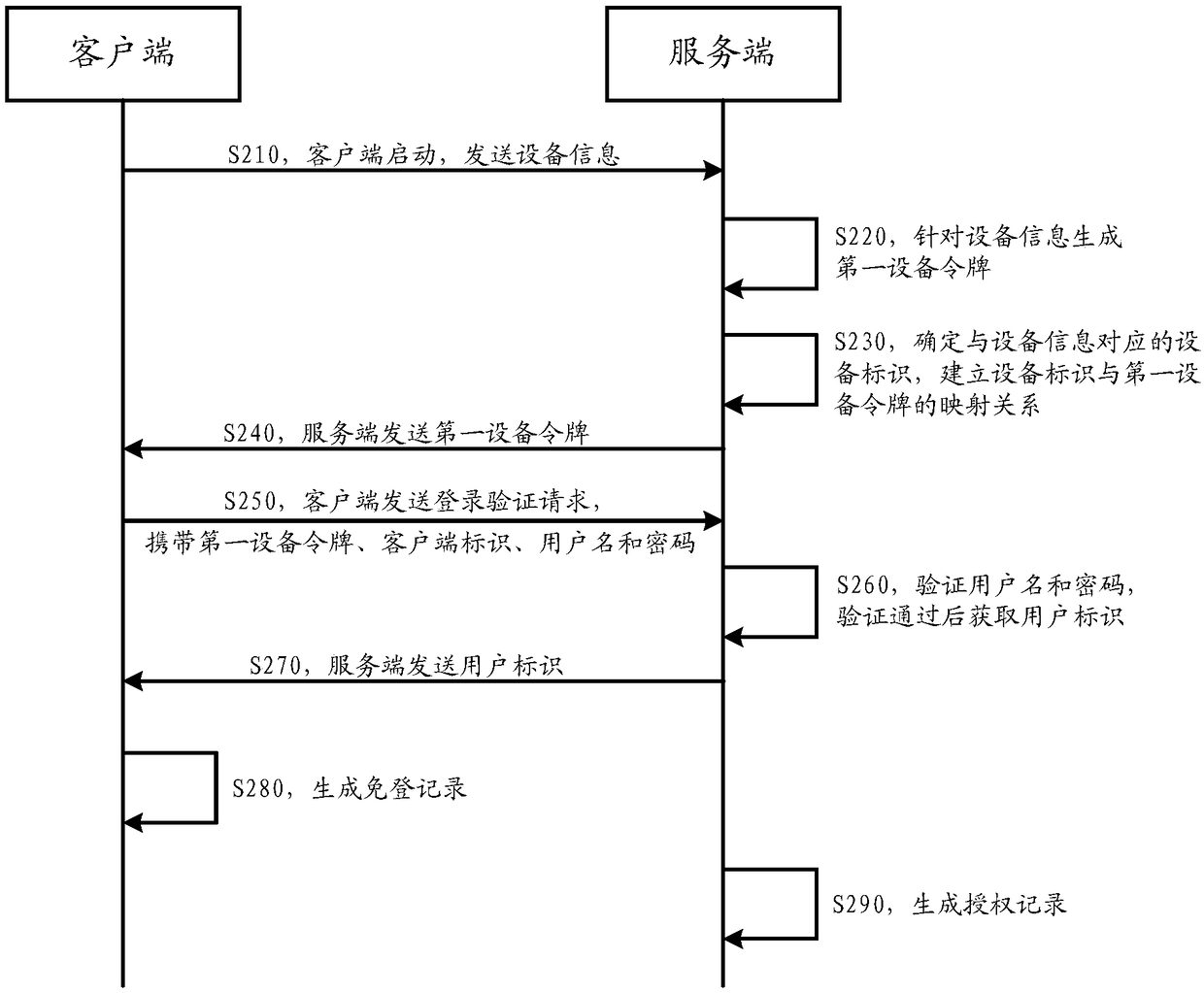
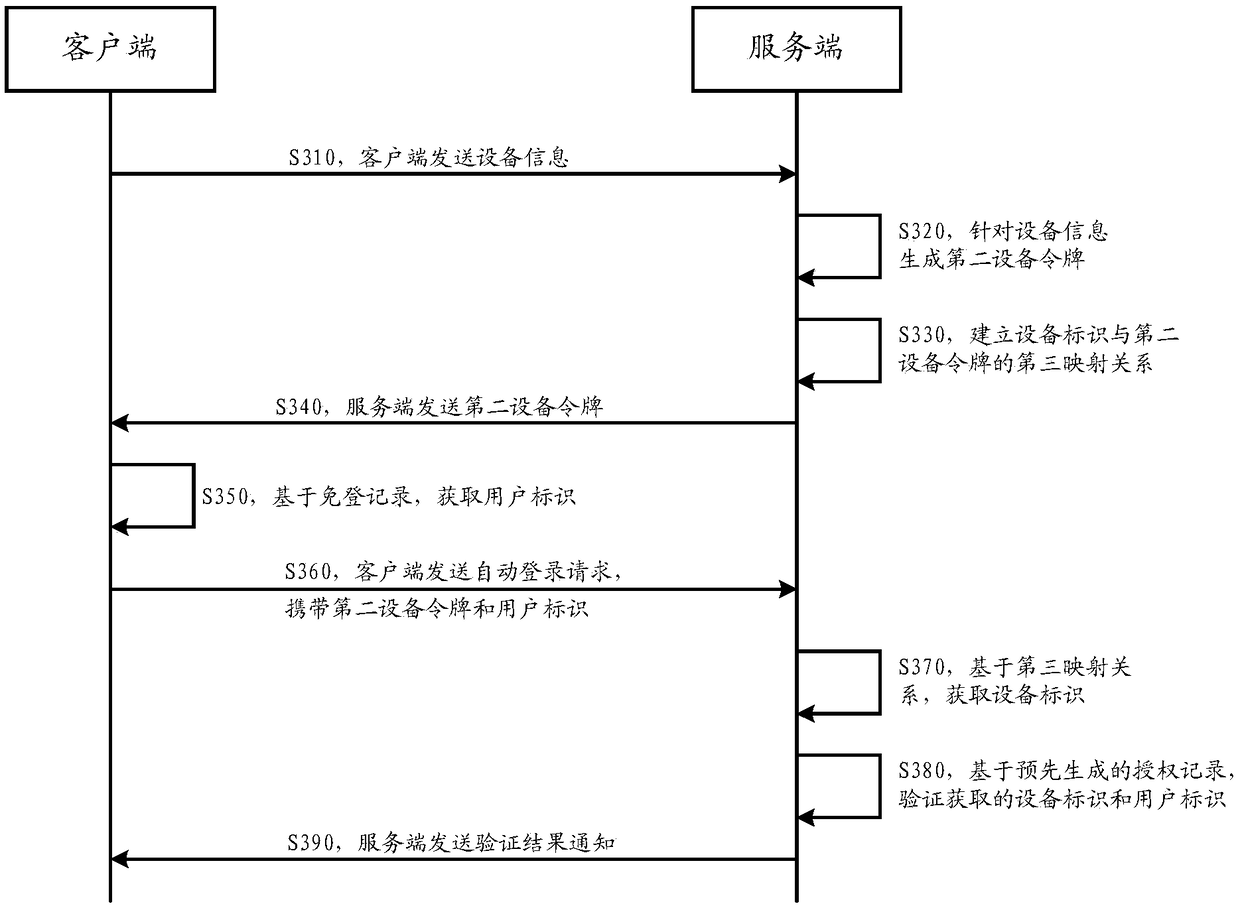
[0033] First, the inventive concept and application scenarios of the automatic login verification method provided by the embodiment of this specification are introduced. The method described is mainly based on the following observations and statistics:
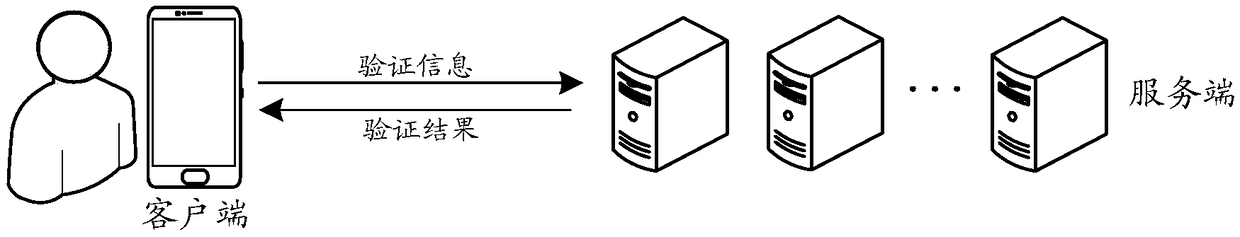
[0034] At present, most mobile clients (hereinafter referred to as clients), that is, applications running on mobile terminals, provide an automatic login mechanism in order to improve user experience, that is, when a user enters authentication information, such as a user name and password , if the login is successful, when the user needs to log in again, he only needs to open the client without entering the authentication information again to complete the login. However, in traditional automatic login mechanisms, see figure 1 In the application scenario shown, the client needs to submit, and a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com