Network security blog classification method and system based on feature extraction
A technology of network security and feature extraction, which is applied in the field of blog classification, can solve the problems of low semantic discrimination and unrecognition, and achieve reliable classification results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0075] The present invention will be further described below in conjunction with examples.
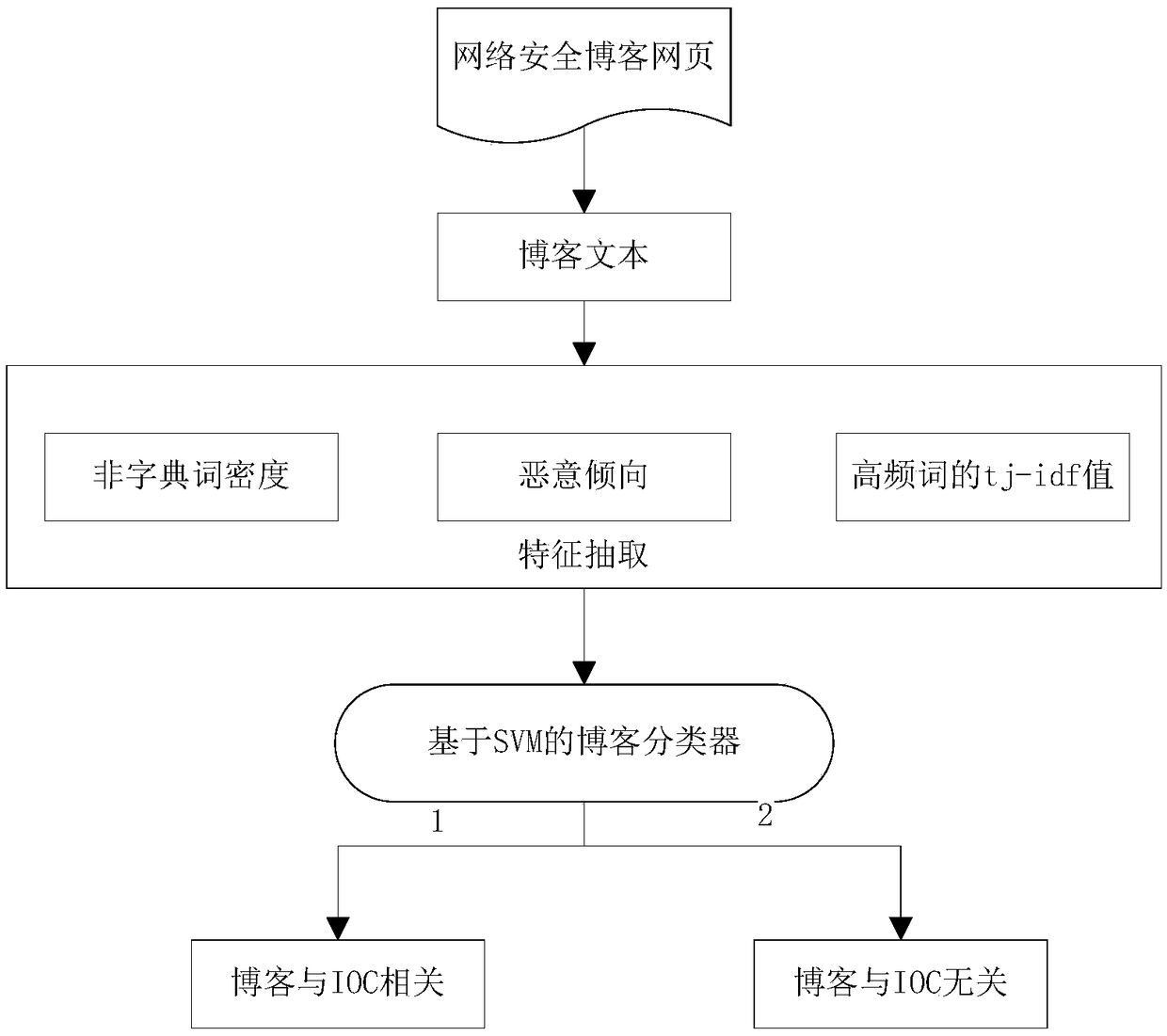
[0076] Such as figure 1 As shown, the present invention discloses a method for classifying network security blogs based on feature extraction, which specifically includes the following steps:
[0077] Step 1: For network security blogs, use web crawler technology to crawl network security blogs from secure websites.
[0078] For example, in this embodiment, taking the security blog website malwarebytes as an example, its corresponding blog list page is https: / / blog.malwarebytes.com / page / 1, where the last 1 indicates the blog list page number. We traverse from the first blog list page until the page is empty, and use XPath to anchor all blog links on each list page. Then visit each blog link, and anchor the title, release time, and text of the blog with XPath. Finally, {link, title, release time, text} is stored in the database as a blog entry. It should be understood that the crawl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com