A fingerprint identification method of industrial control scanner based on honeynet data
A fingerprint recognition and scanner technology, applied in the field of network security, can solve the problem of not being able to effectively identify new types of scanning activities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments, but not as a limitation to the technical solution of the present invention.
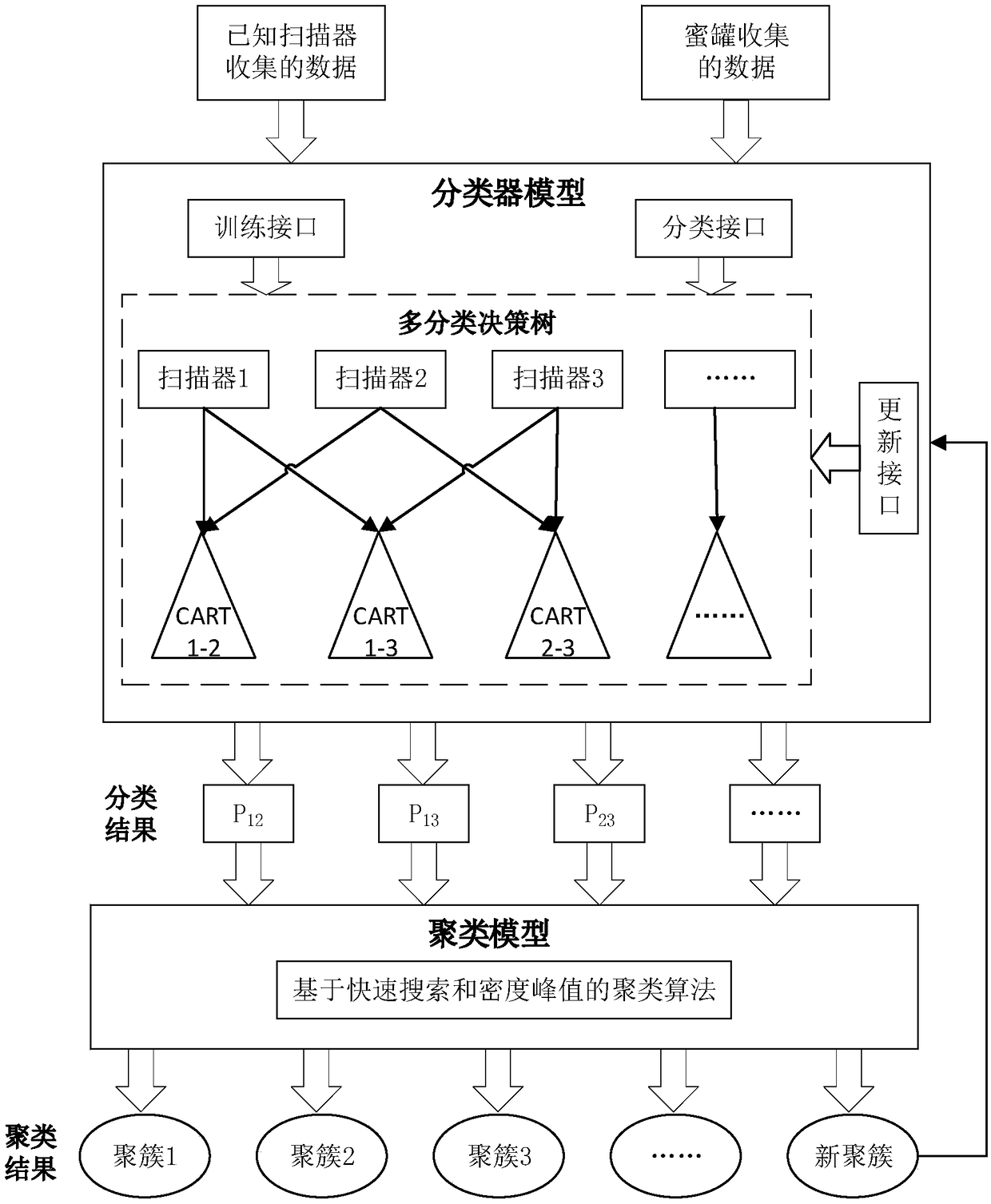
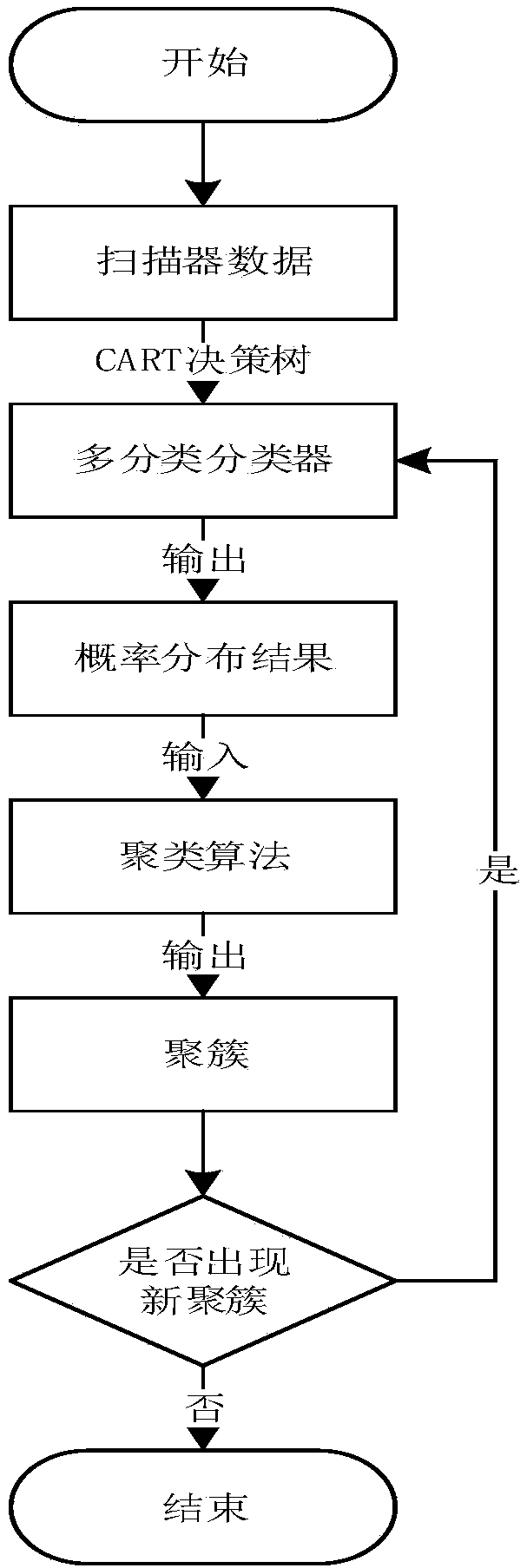
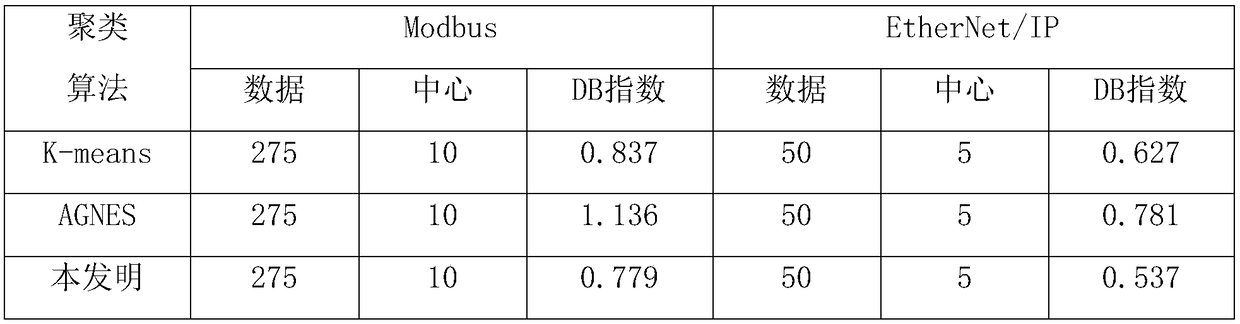
[0026] In recent years, tremendous changes have taken place in the field of cyberspace security. With the deepening of the integration of industrialization and industrialization, industrial control systems have become inseparable from the Internet. After the integration of industrialization and industrialization, the information security of IT systems has also been integrated into the security of industrial control systems. At present, the industrial control scanner fingerprint recognition system can analyze and classify traffic, which plays a vital role in the intrusion of network attackers. The industrial control scanner fingerprint recognition system can classify the known traffic of the system, and can also Unknown traffic is marked, and then judged accord...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com