Web anomaly detection system based on user behaviors
An anomaly detection and behavior technology, applied in the field of information security, can solve problems such as undetectable attacks, and achieve the effect of preventing system crashes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
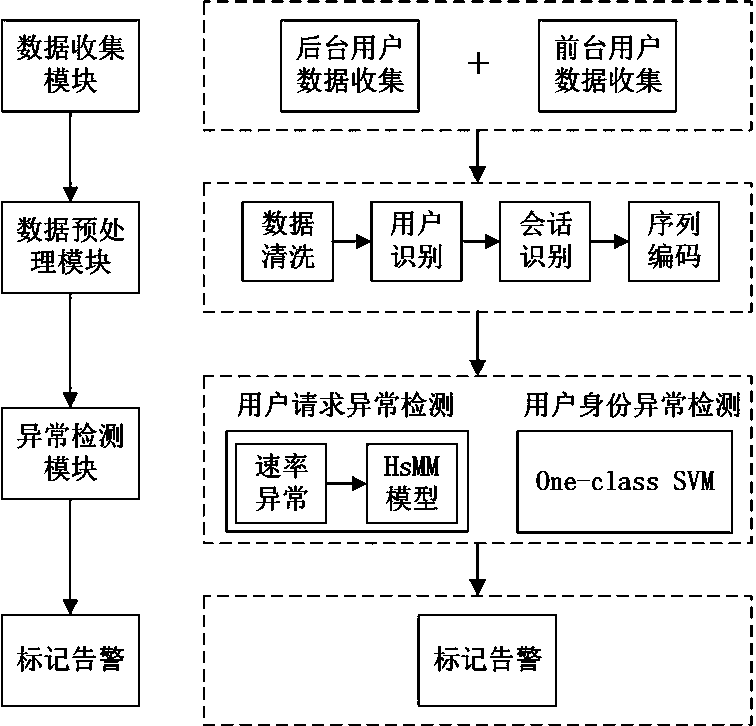
[0029] The web anomaly detection system based on user behavior is mainly composed of user behavior data collection module, data preprocessing module, user request anomaly detection module, user identity anomaly detection module and label alarm module.
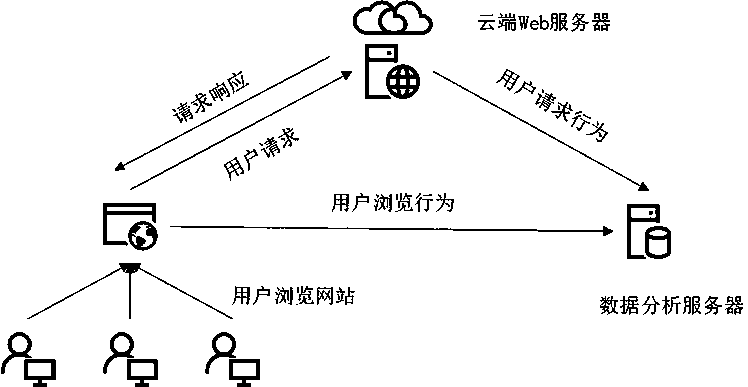
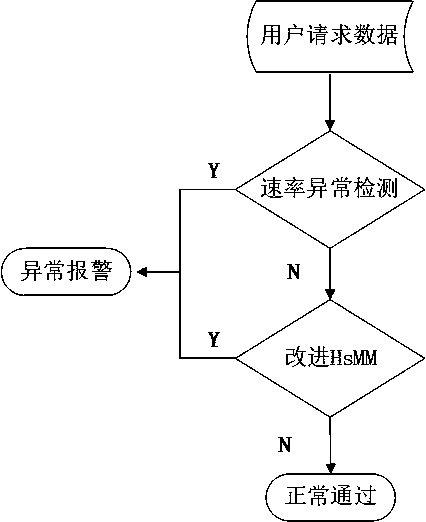
[0030] figure 1 The overall architecture diagram of the system is shown, which introduces the relevant design of the above five modules in detail, and explains the workflow and main functions of the relevant modules. The functions of the data collection module include the collection of user access data and the collection of user browsing behavior data. The collection of user access data is mainly to extract web application logs on the server side, which is called background user behavior data collection. The collection of user browsing behavior data is mainly on the client side, such as the browser, using the JavaScript scripting language to collect user behavior data when browsing the website, which is called front-end user d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com