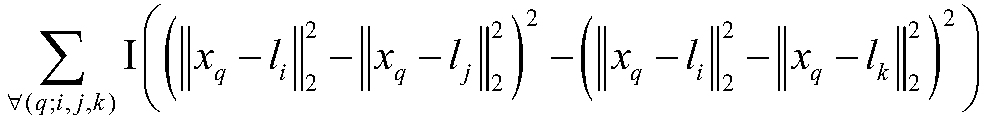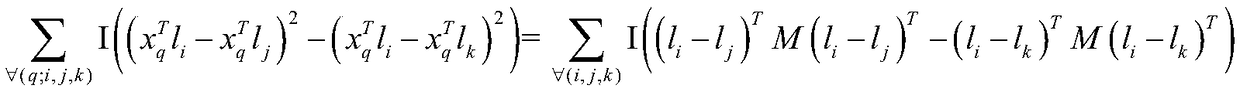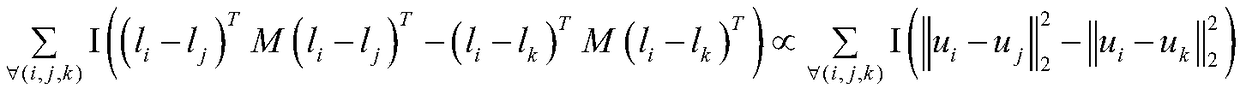Sequence constrained hashing algorithm in image retrieval
A technology of image retrieval and hash algorithm, applied in the direction of still image data retrieval, metadata still image retrieval, calculation, etc., to achieve the effect of improving stream distribution, efficient hash coding mechanism, and reducing precision loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The following examples will further illustrate the present invention.
[0053] The present invention aims to propose a sequence-constrained hashing method, the ultimate goal of which is to obtain the function (hash function) of the hash code:
[0054] H(x)={h 1 (x), h 2 (x),...,h r (x)}.
[0055] The hash function can map the original real feature matrix to the corresponding binary encoding matrix B={b 1 ,b 2 ,...,b n}∈{0,1} r×n , where r is the length of the hash code. The formal description of the proposed detailed scheme is as follows: the formal description of the GIST feature extraction of the query image and the image database to be retrieved is as follows: extract the d-dimensional GIST feature for each image in the training set, and obtain a d×n The original visual feature matrix X={x 1 ,x 2 ,...,x n}∈R d×n , where n represents the number of training samples in the training set, x i The i-th column of the matrix X represents the GIST feature vector ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com