Identity authentication method
A technology for identity authentication and verification failure, applied in the field of identity authentication, it can solve problems such as hidden dangers of information system security, and achieve the effect of improving security and accurate verification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
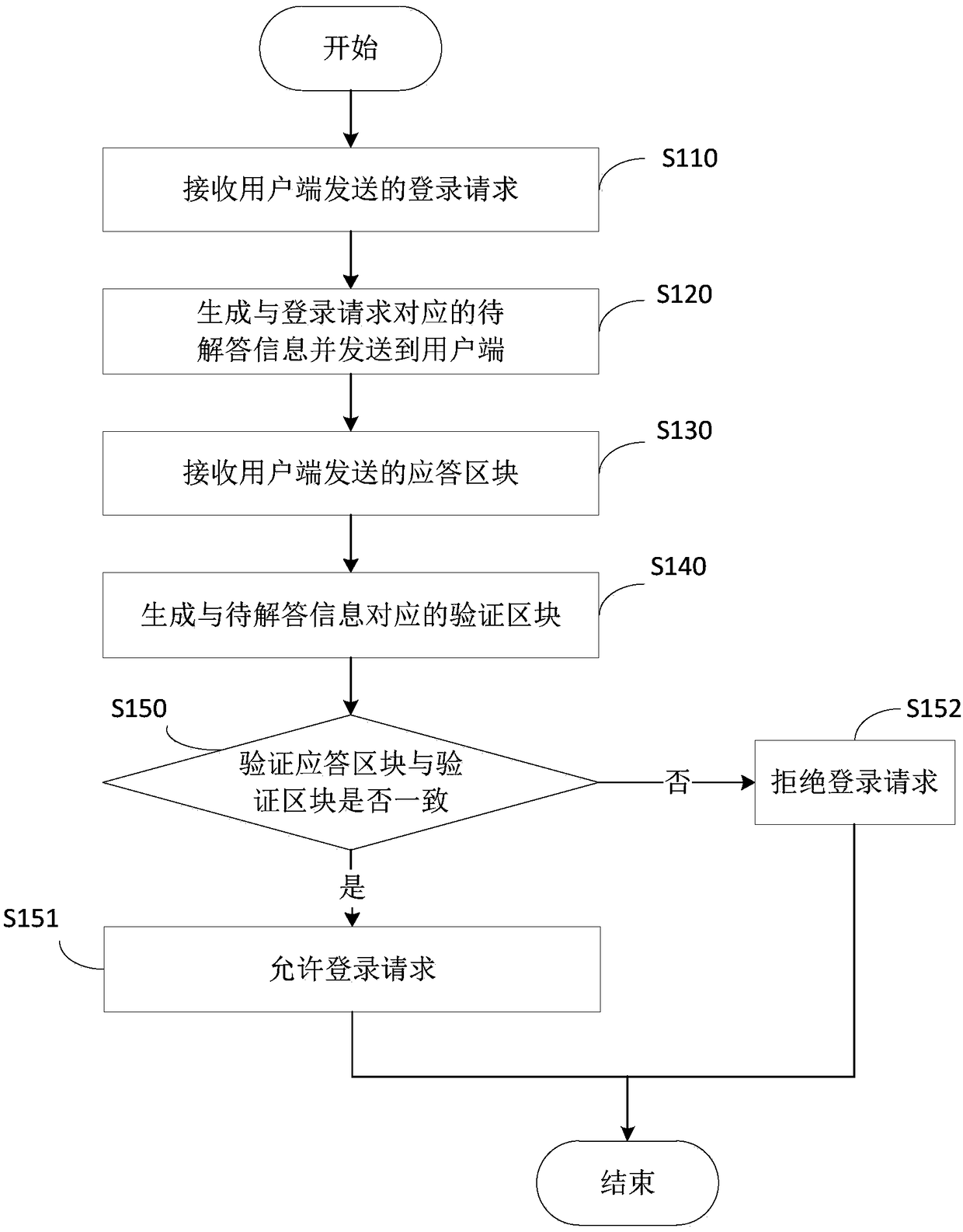
[0053] Identity authentication technology is a technology that can identify the real identity of the information sender and receiver. It is the first door to protect the security of network information resources. Its task is to identify and verify the legitimacy and authenticity of user identities in network information systems. Access system resources and keep illegal visitors out. With the continuous popularization of today's network, network security has become more and more important in information systems. How to ensure the operator who operates with a digital identity is one of the important factors for the legal owner of this digital identity to ensure the reliability of authentication. However, the existing identity authentication methods cannot accurately guarantee that the physical identity of the operator corresponds to the digital identity. In addition, it is difficult to track information about illegal logins that have occurred, which makes the information system ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com