An Android malware detection method and technology based on a behavior graph
A malware and detection method technology, applied in the field of computer security, can solve the problems of imperfect feature extraction in detection methods, detection methods cannot be effectively adapted, low accuracy rate, etc., to achieve a good recognition rate, improve reliability, and improve accuracy sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be further described below in conjunction with accompanying drawings and examples. The invention aims to provide a method and a model for detecting Android malicious software, accurately identify and detect malicious behaviors of application programs, and protect the security of system and user data.
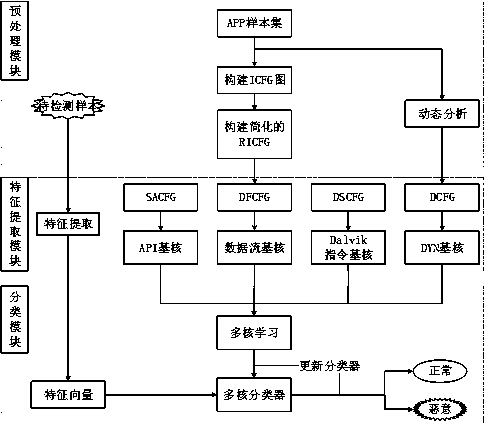
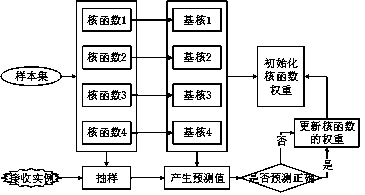
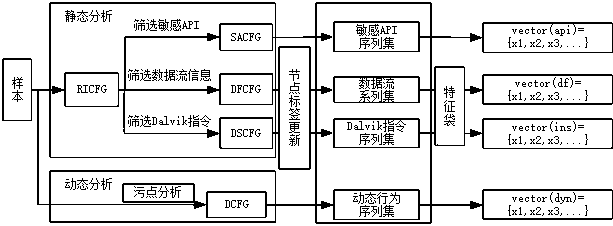
[0018] The present invention provides a novel detection idea, which is different from the mainstream technology for analyzing signatures and behaviors of malicious codes. This is a detection method based on image kernels, and its main advantage lies in the The information is more complete. According to this idea, a behavior graph-based Android malware detection model is designed. The overall structure of the model is as follows: figure 1 As shown, it is mainly divided into preprocessing module, feature extraction module and classification module. Among them, the preprocessing module completes the preprocessing of the application program samples...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com