A method for validate and identifying unsafe sensitive input in Android system
An input verification and Android system technology, applied in machine learning technology and static information flow analysis, natural language processing, identifying unsafe input verification and identification fields in Android systems, can solve unclear definition, ignore input verification, and unclear input Verification and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
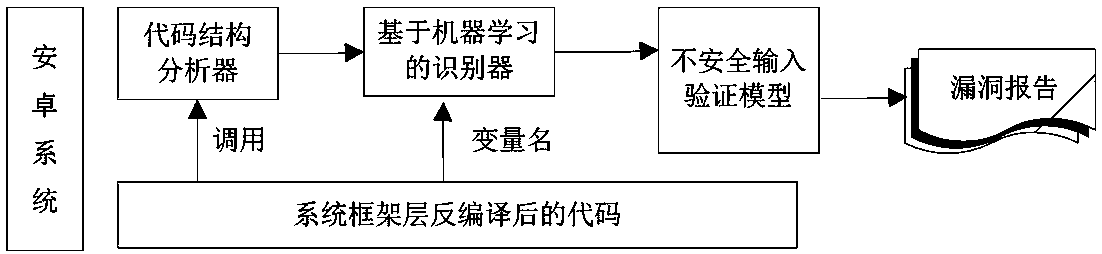
[0031] The present invention designs and implements the above-mentioned brand-new unsafe input verification identification method based on the combination of natural language processing and machine learning. This section introduces the specific implementation of the framework in detail.
[0032] Input Validation Recognition Based on Code Structure Analysis
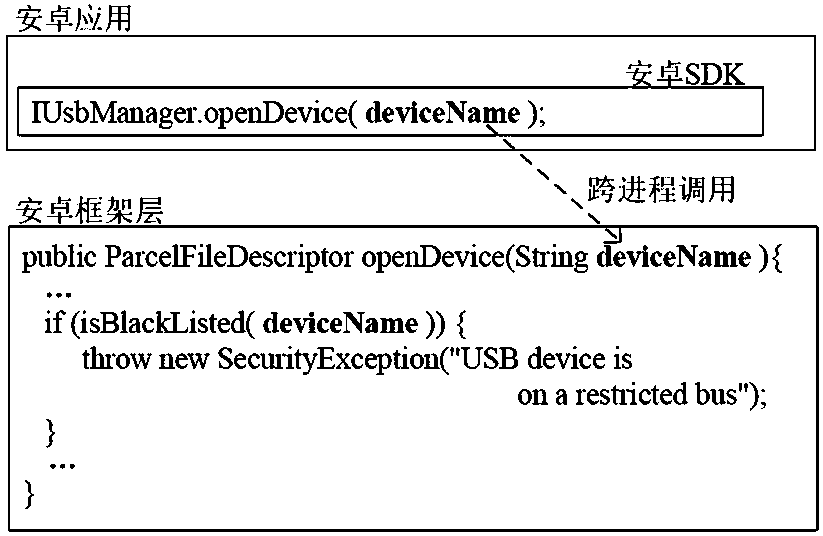
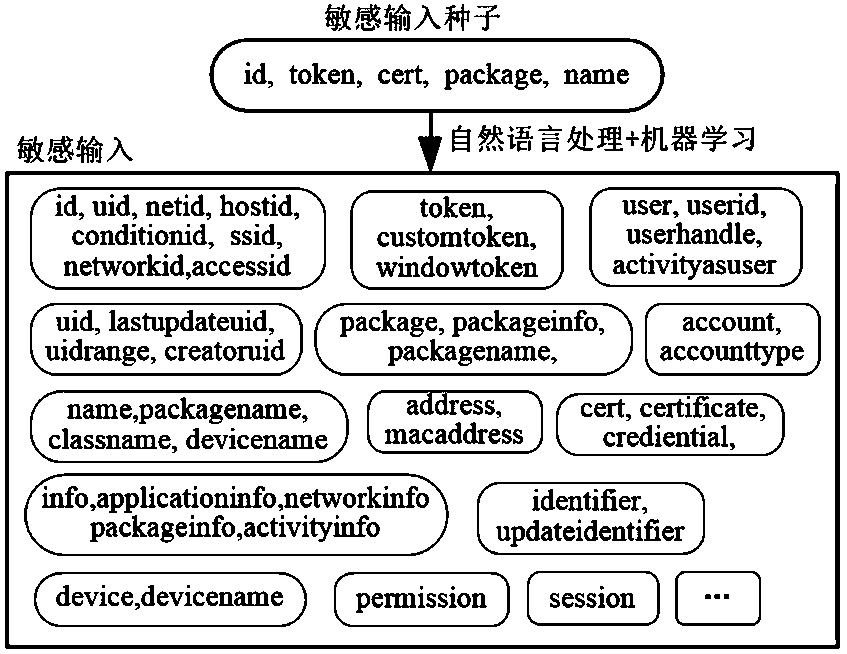
[0033] The present invention analyzes the Android system on the basis of the Soot framework tool. The Soot framework is a mature Java program decompilation tool. First, the present invention decompresses the Android system image, and extracts all Java class files therefrom, then uses Soot to decompile, and obtains the intermediate representation (Jimple format file) of the system code. Afterwards, the present invention extracts all Android system services, methods and input variables in the system services from the decompiled Jimple code as the source of code information to be analyzed. When extracting system services, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com