Patents
Literature
35 results about "Standalone program" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A stand-alone program, also known as a freestanding program, is a computer program that does not load any external module, library function or program and that is designed to boot with the bootstrap procedure of the target processor – it runs on bare metal. In early computers like the ENIAC without the concept of an operating system, standalone programs were the only way to run a computer. Standalone programs are usually written in or compiled to the assembly language for the specific hardware.
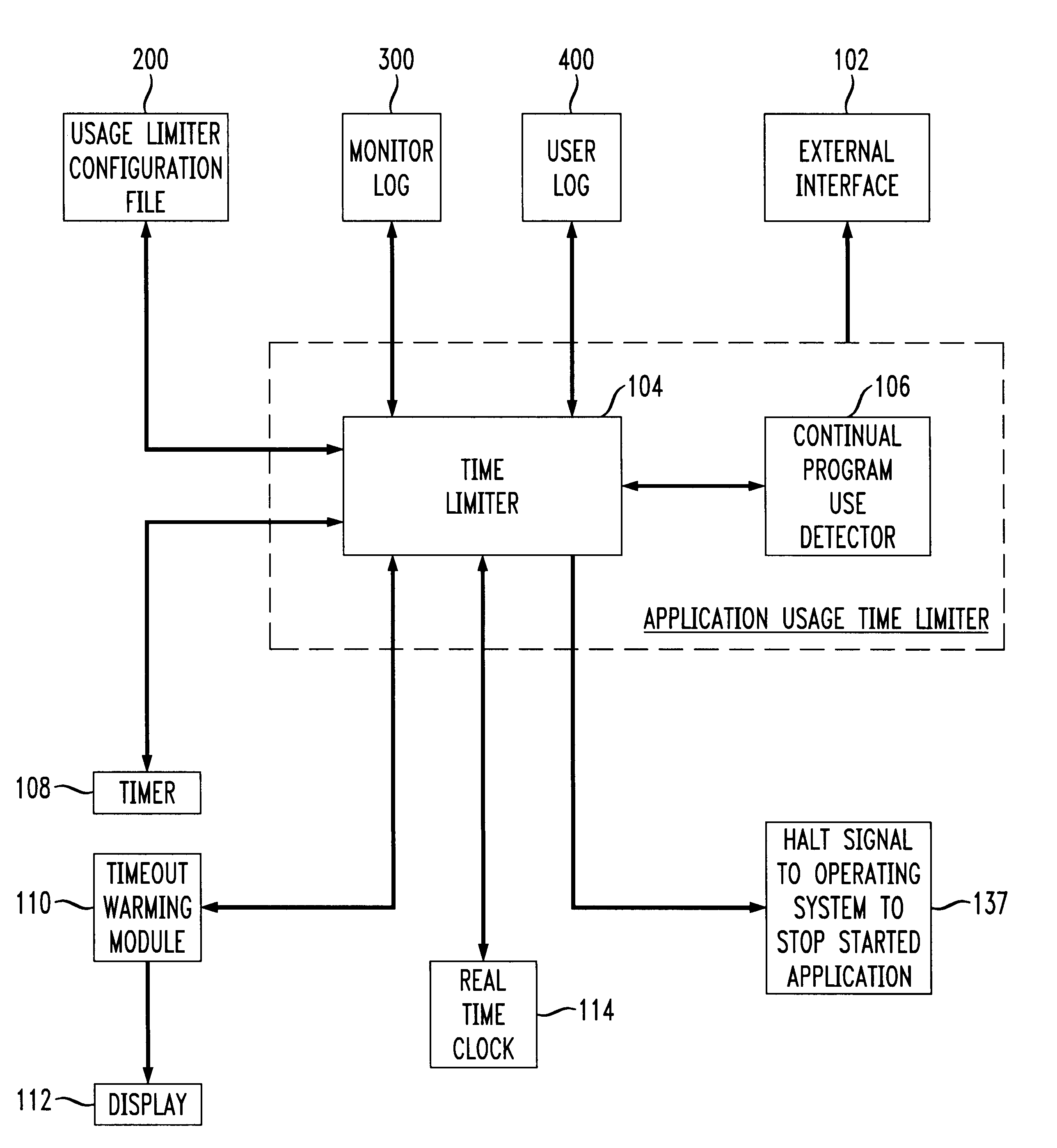
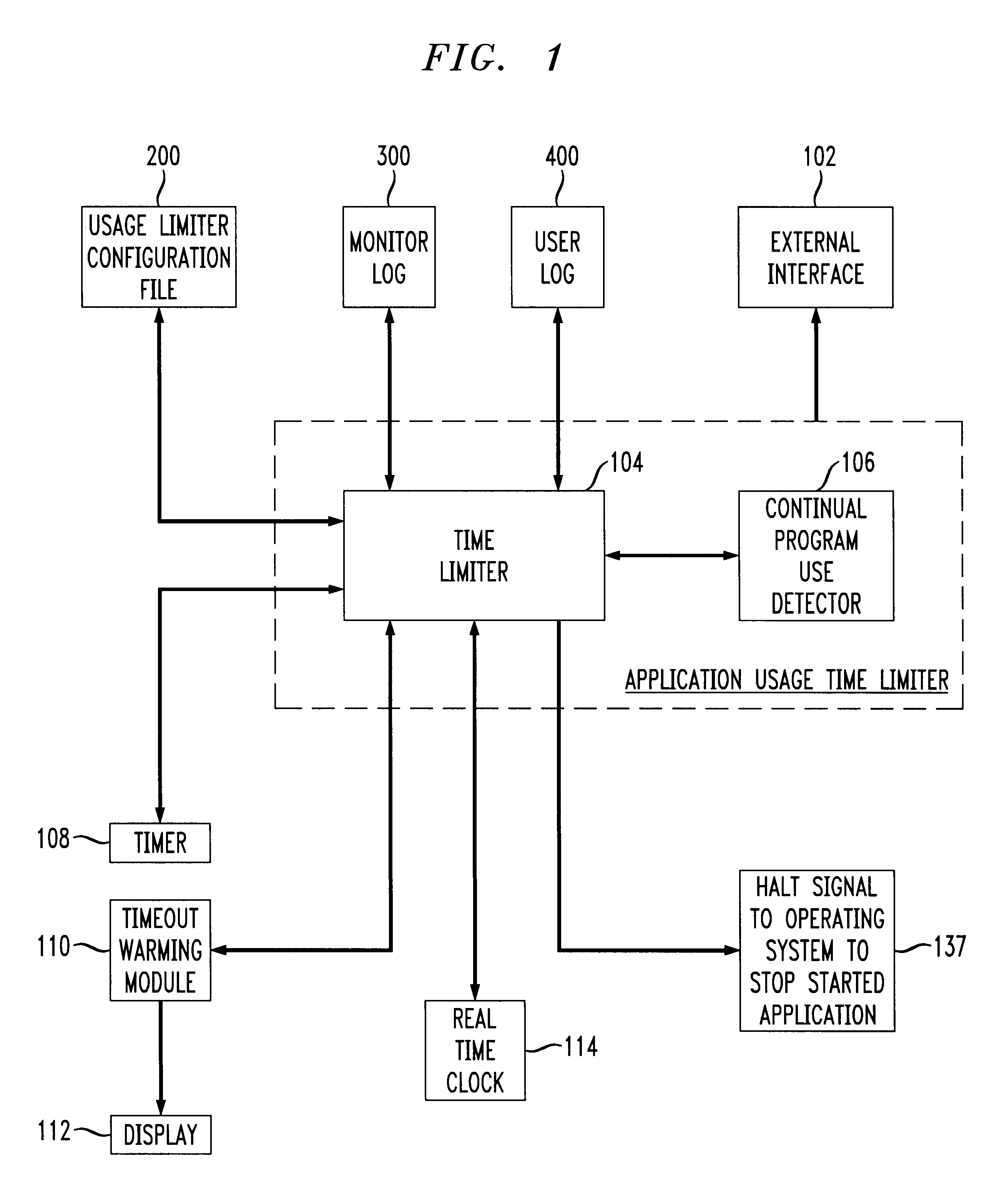
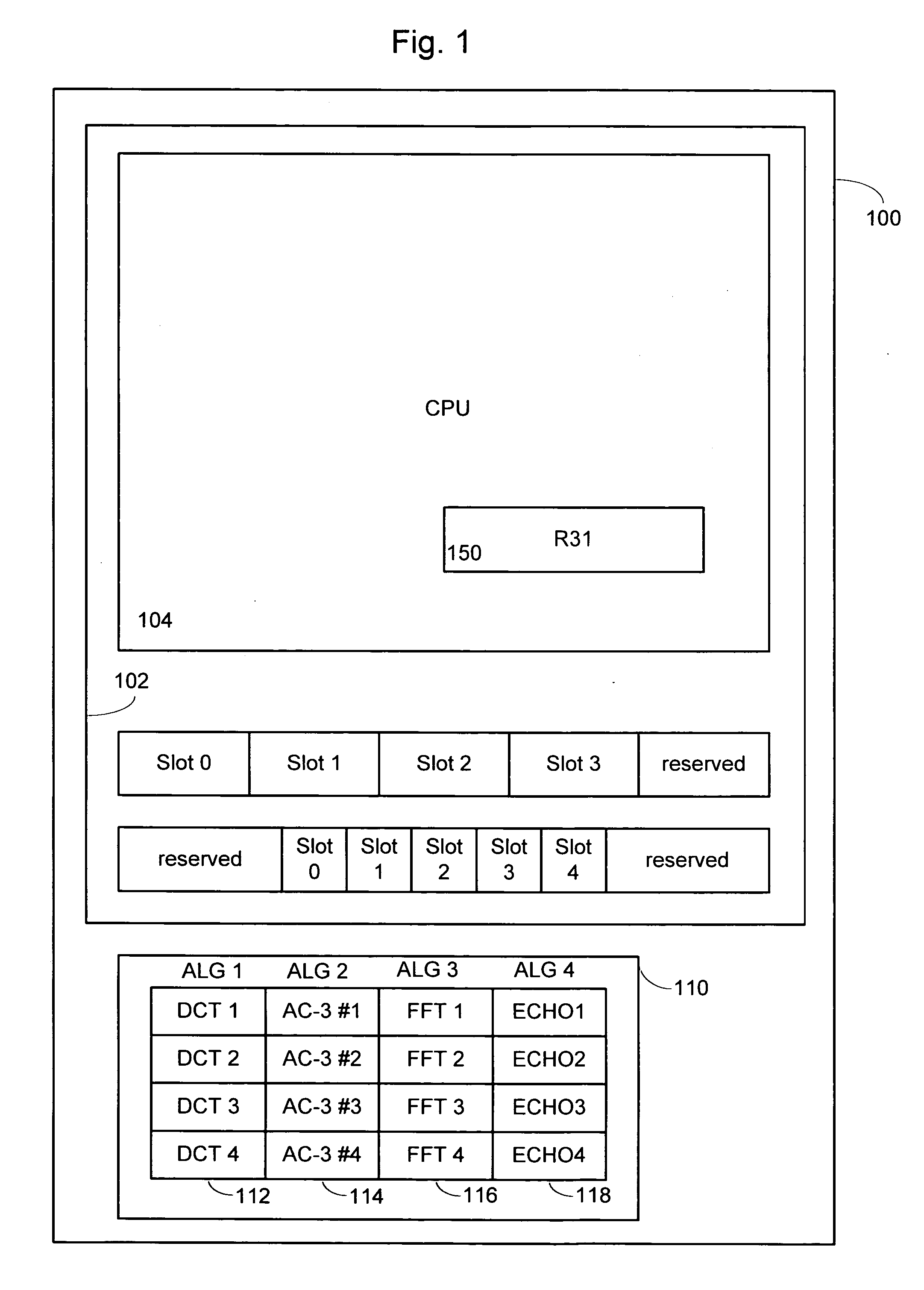
Application usage time limiter
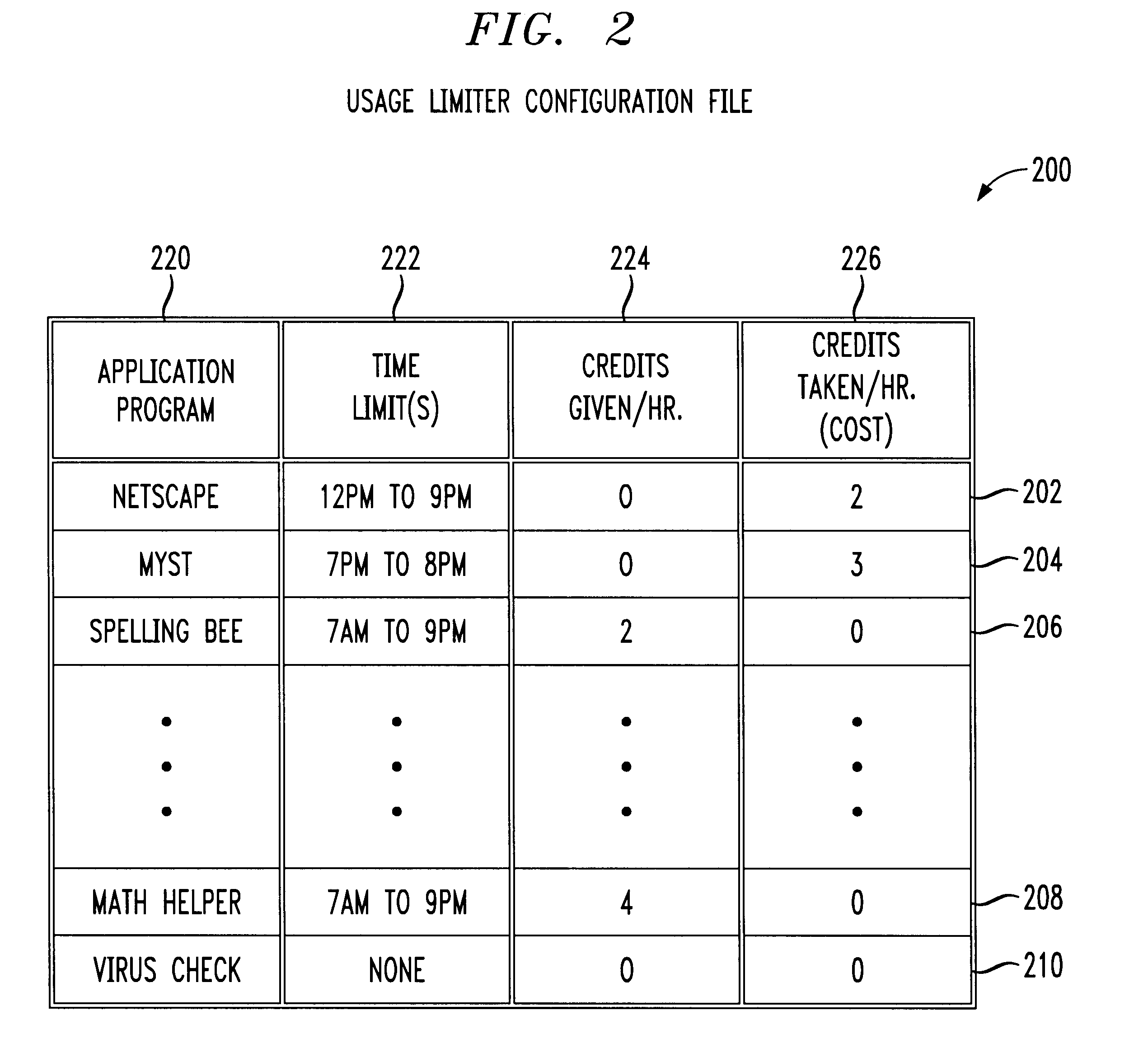
An application usage time limiter monitors certain pre-configured application programs when opened or otherwise executed on a computer (e.g. a PC). The application usage time limiter is itself a program running either as a front end to various selected programs for monitoring, or as a separate program running in a time-sharing operating system environment. Pre-configurable options in a usage limiter configuration file or other memory area are set to limit real time ranges that particular application programs on a particular computer can be started and run, and a limit to a length of time that a specific program (or category of programs-an be operated given a number of available credits for a current user. The user is given credits at a pre-configured rate per hour of usage of an application program designated in the usage limiter configuration file as being beneficial, and the user gives back (or looses) credits at a pre-configured rate per hour of usage for use of programs designated as non-beneficial. Preferably, continued usage of beneficial programs is detected, e.g., by keystrokes. Application programs selected for monitoring in the usage limiter configuration file can be identified on an application by application basis, as a specific category of applications identifiable when the particular application is started, or as being stored in a specific directory (e.g., folder in a Windows(TM) operating system). A credit-giving (i.e., beneficial program) must be run by a particular user to earn credits before a credit-taking (i.e., non-beneficial program) can be run by that user. Up front credits may be provided to a particular user in a user log.
Owner:LUCENT TECH INC
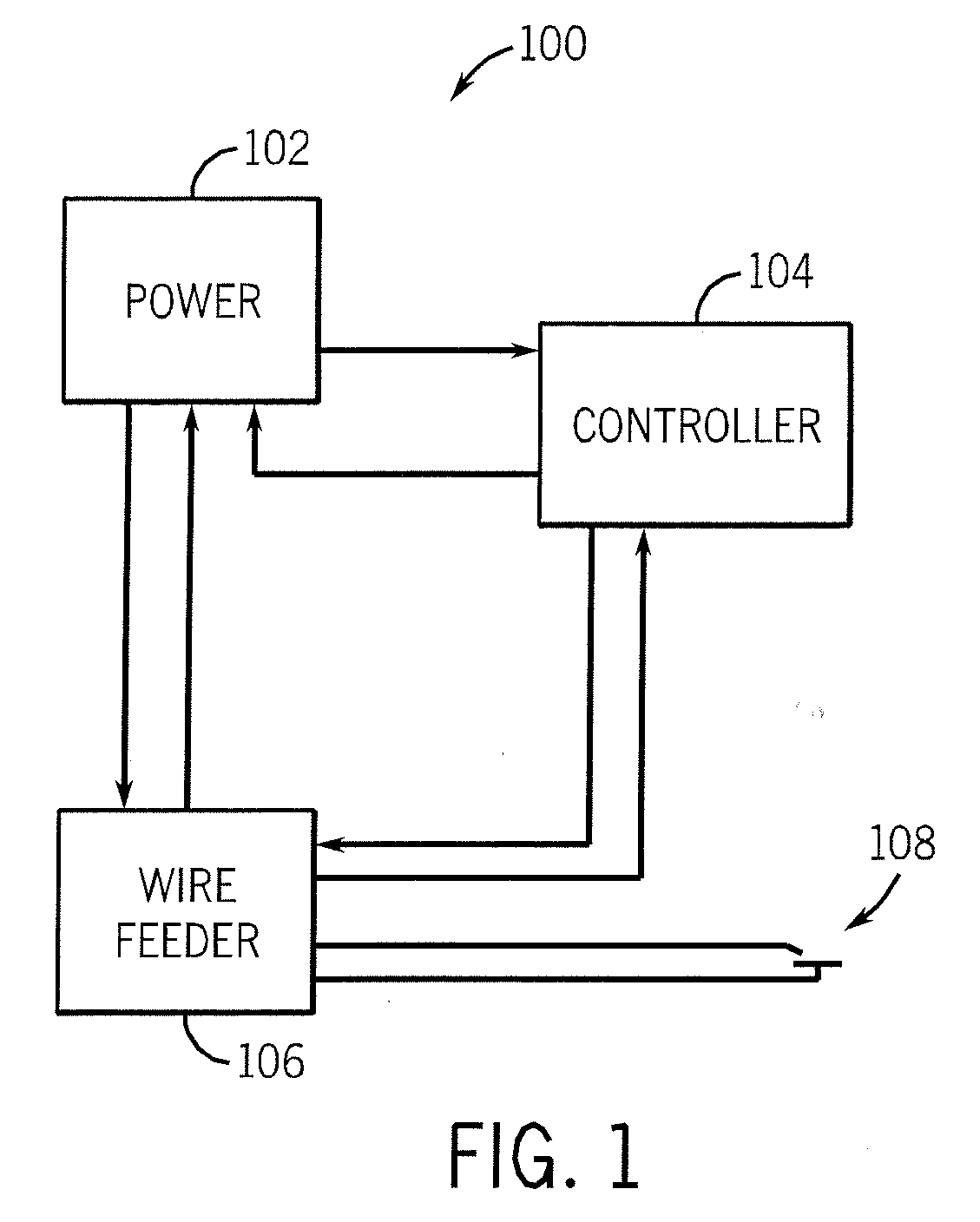
Method and Apparatus For Welding With Limited Term Software
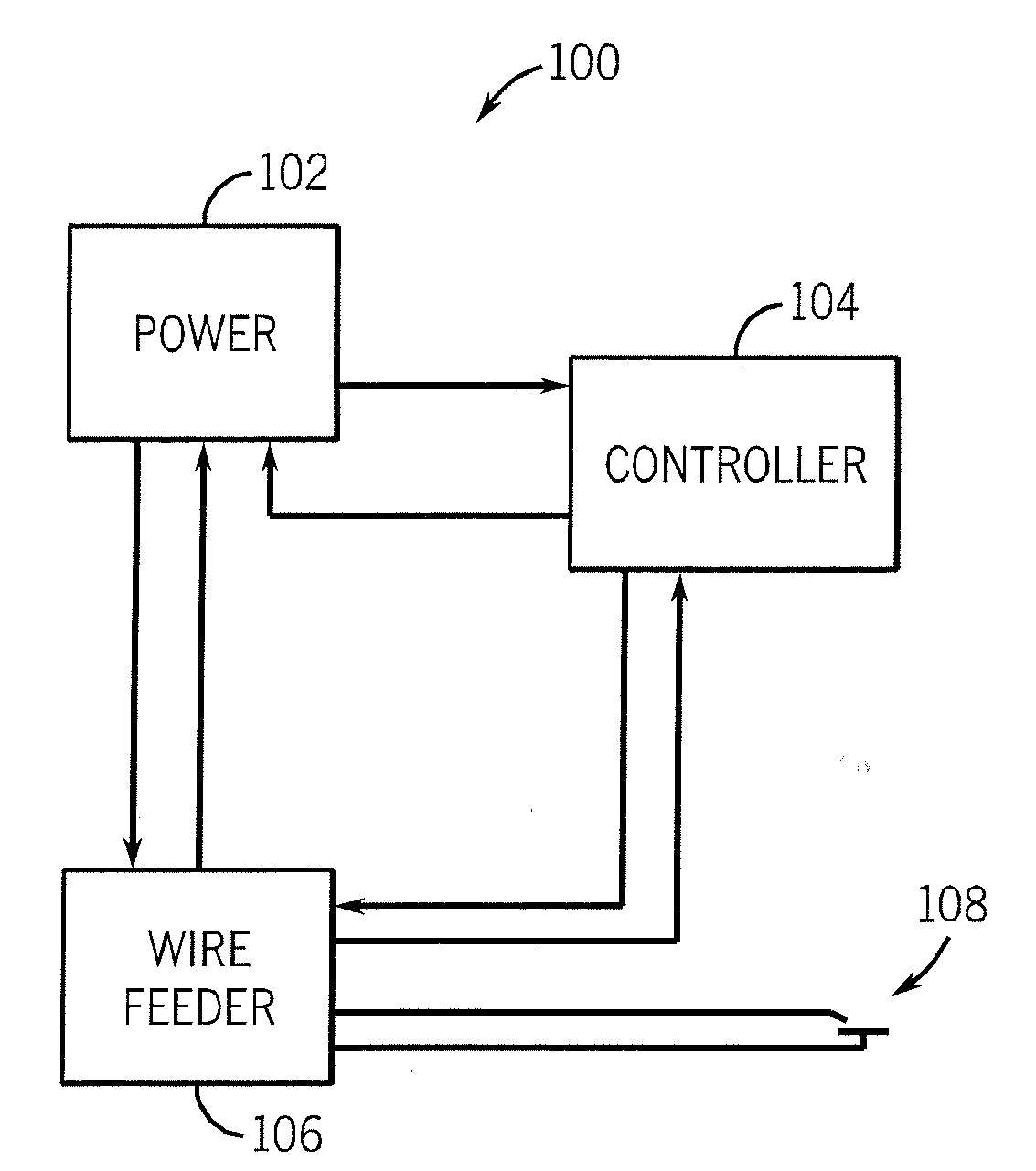
A method and apparatus for welding uses a power circuit and a controller connected to the power circuit. The controller included a welding program having a limited term. The program may be part of a system, or a stand alone program. The controller has a data port and the welding program and / or an authorization is received by the controller on the data port in one embodiment. The welding program includes a limited time module, a limited time in use module, a limited arc start module, a controlled short circuit program, and / or a pulse program in various embodiments. A second welding program, without a limited term module, may be provided.
Owner:ILLINOIS TOOL WORKS INC
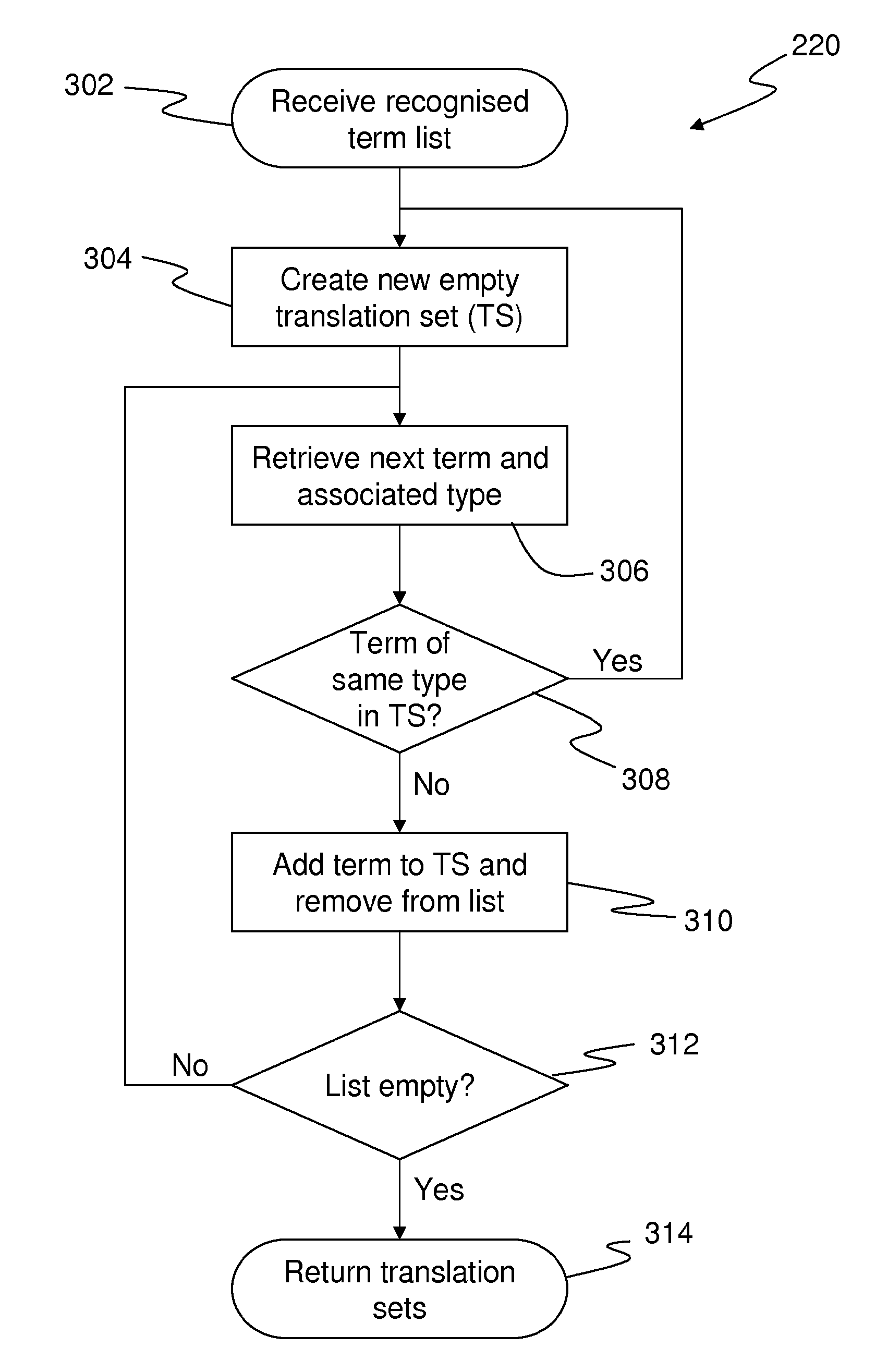
Method and System for Classification of Clinical Information
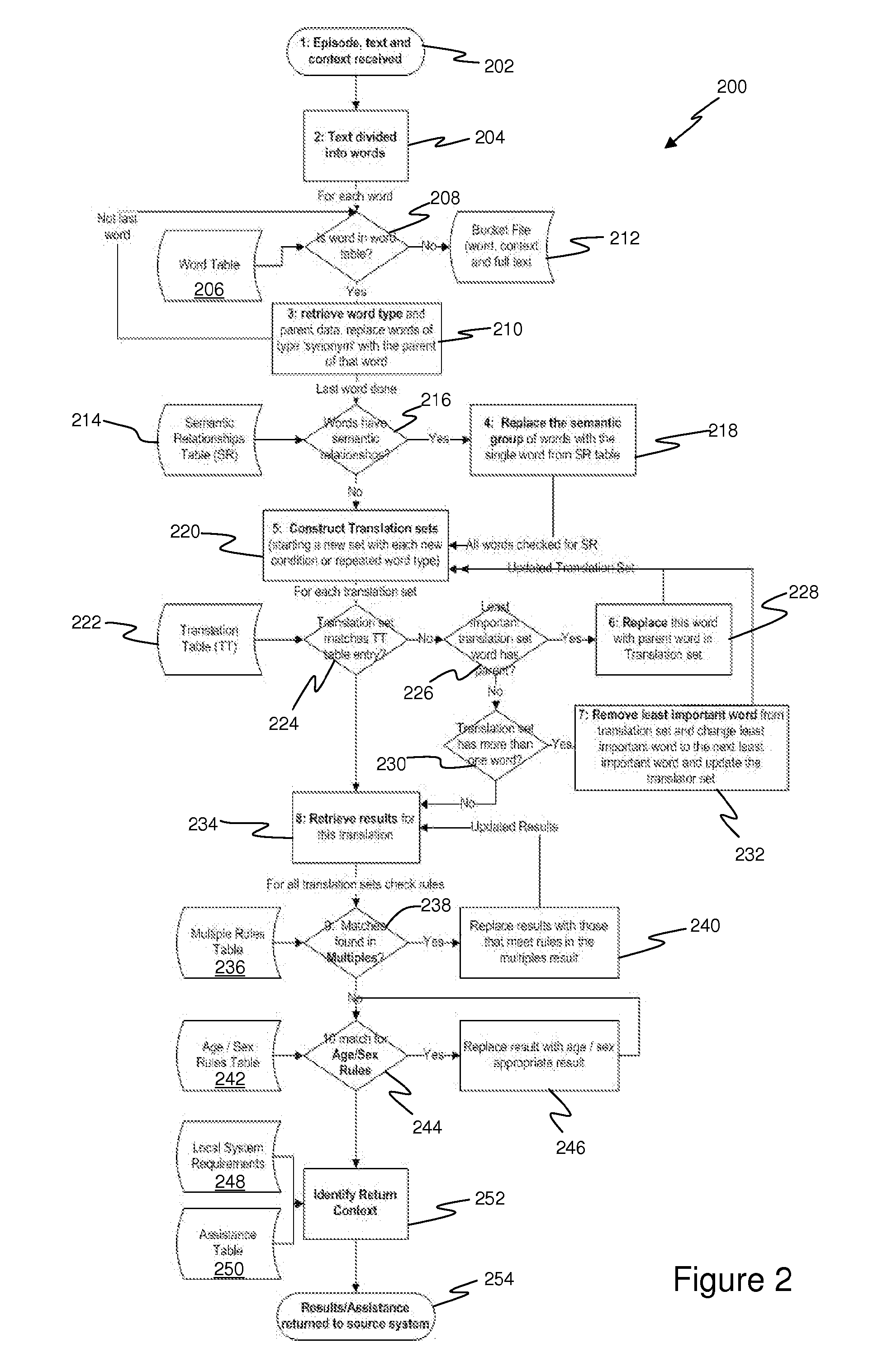
InactiveUS20130046529A1Maximize likelihoodFacilitates effective translation of input textNatural language translationOffice automationClinical informationStandalone program
A method of translating clinical information into one or more standardised systems of coding or nomenclature processes received clinical information (202) relating to a patient, which includes at least one free text description of a clinical status of the patient. The free text description is analysed (208-218) to identify one or more terms relevant to the clinical status of the patient. One or more translation sets are constructed (220), each of which includes one or more sequential identified terms. Each translation set is translated (234-252) into one or more standardised health codes or terms selected from a predetermined system of classification and / or nomenclature, and the selected standardised health codes or terms are output (254). The method may be computer-implemented, either as a standalone program, or in a networked configuration supporting access from remote terminals.
Owner:HEALTH EWORDS
Capturing a user's design intent with resolvable objects
Owner:ARMSTRONG WORLD IND INC
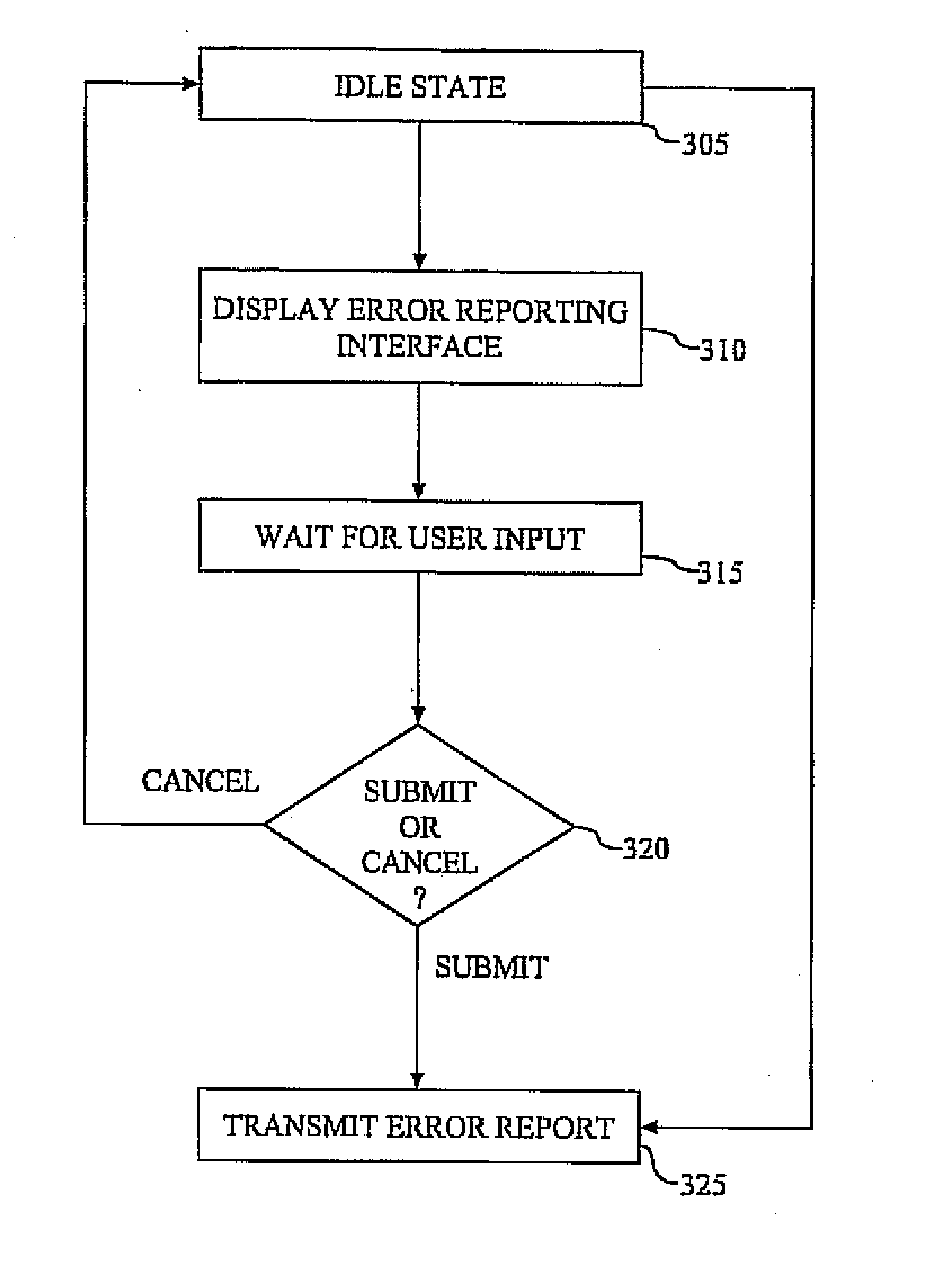
Method and system for site configurable error reporting
Embodiments of the present invention relate generally to error reporting methods and systems. An error reporting application may be configured to be a stand-alone program, embedded within another application, or added as a plug-in application. The error reporting application may also be configured to provide a mechanism for a user to describe a problem with another application and send the problem description to a configurable, user defined location. The error report from the error reporting application may then be processed by an error processing system at the user-defined location.
Owner:RED HAT
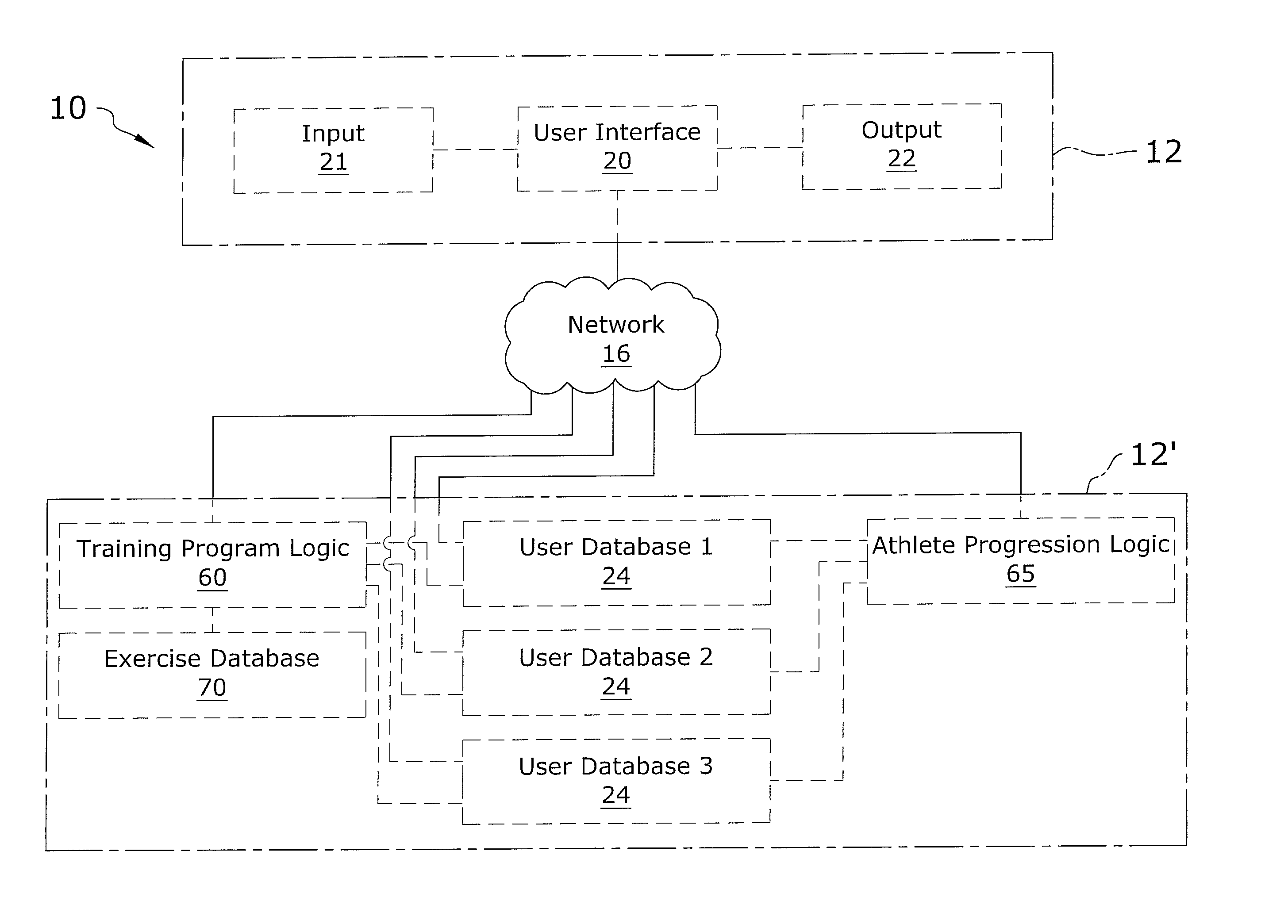
Sports specific training program application
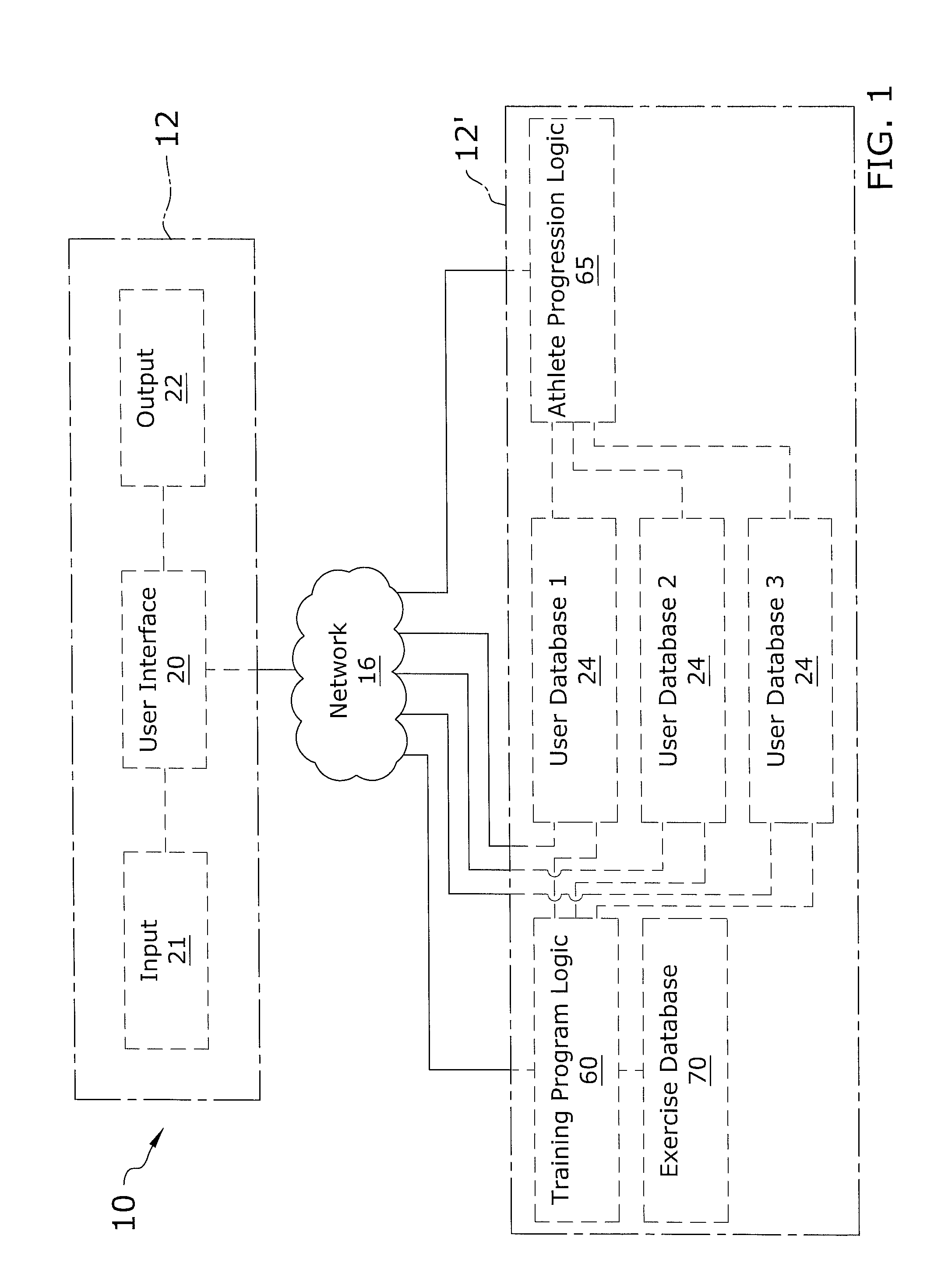
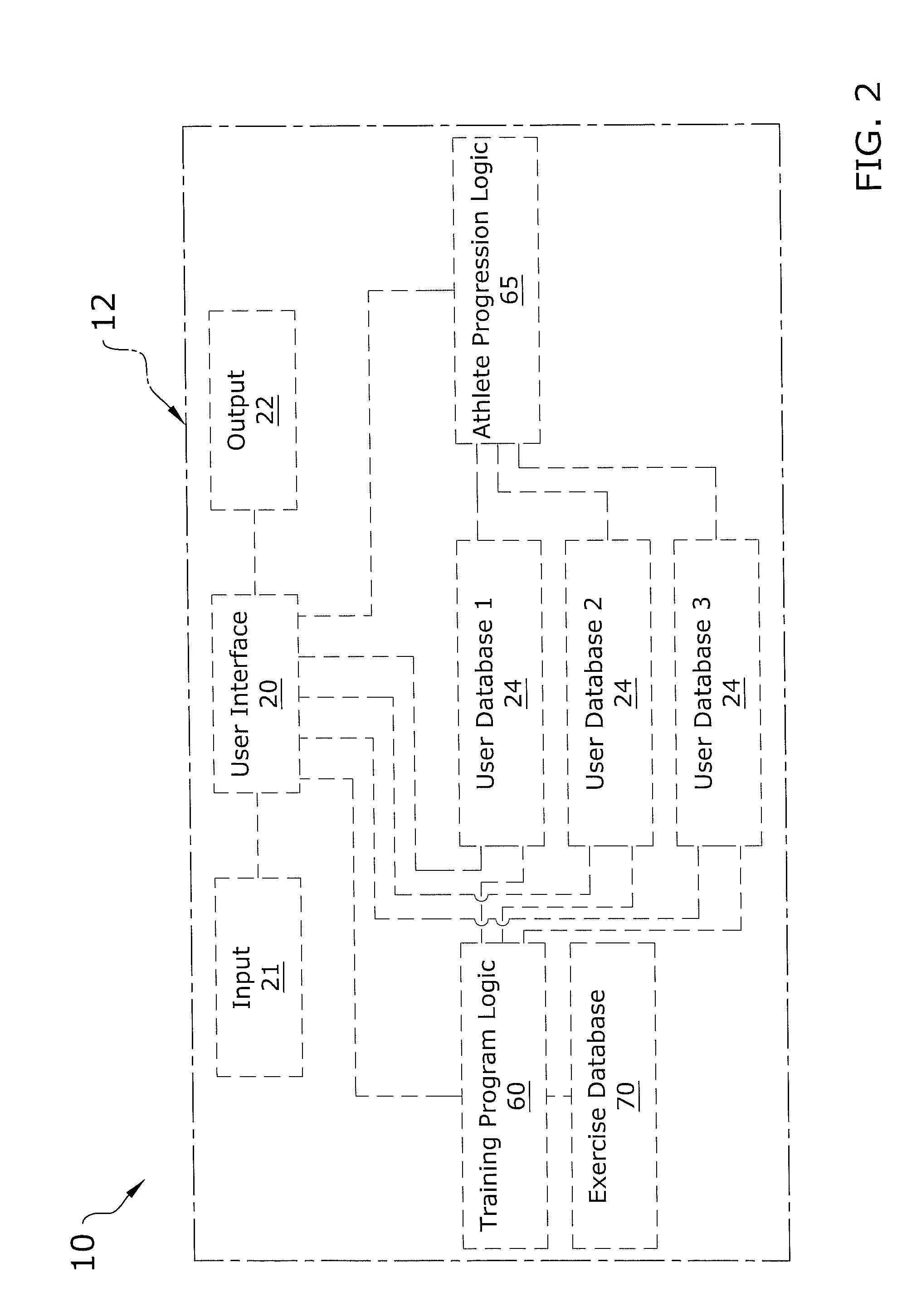
InactiveUS7942784B1Create efficientlyPhysical therapies and activitiesCosmonautic condition simulationsTraining programStandalone program
A sports specific training program application for creating a customizable training program for an athlete of a particular sport. The sports specific training program application includes a user interface preferably connected to and accessible through a network, the user interface allows a user to input user information to correlate with a particular athletic event into one or more user databases. The user information is matched with targeted exercises from an exercise database using training program logic and the resultant training program is outputted to the user, wherein the training program may be outputted in online, printed, or electronic file formats. The user may also input results from performing the training program into the user interface to receive a scorecard of processed results which details progress and history of the user's exercises and goals and for developing subsequent training programs. The present invention may be a stand-alone program without the network.
Owner:HYDE LEN +3
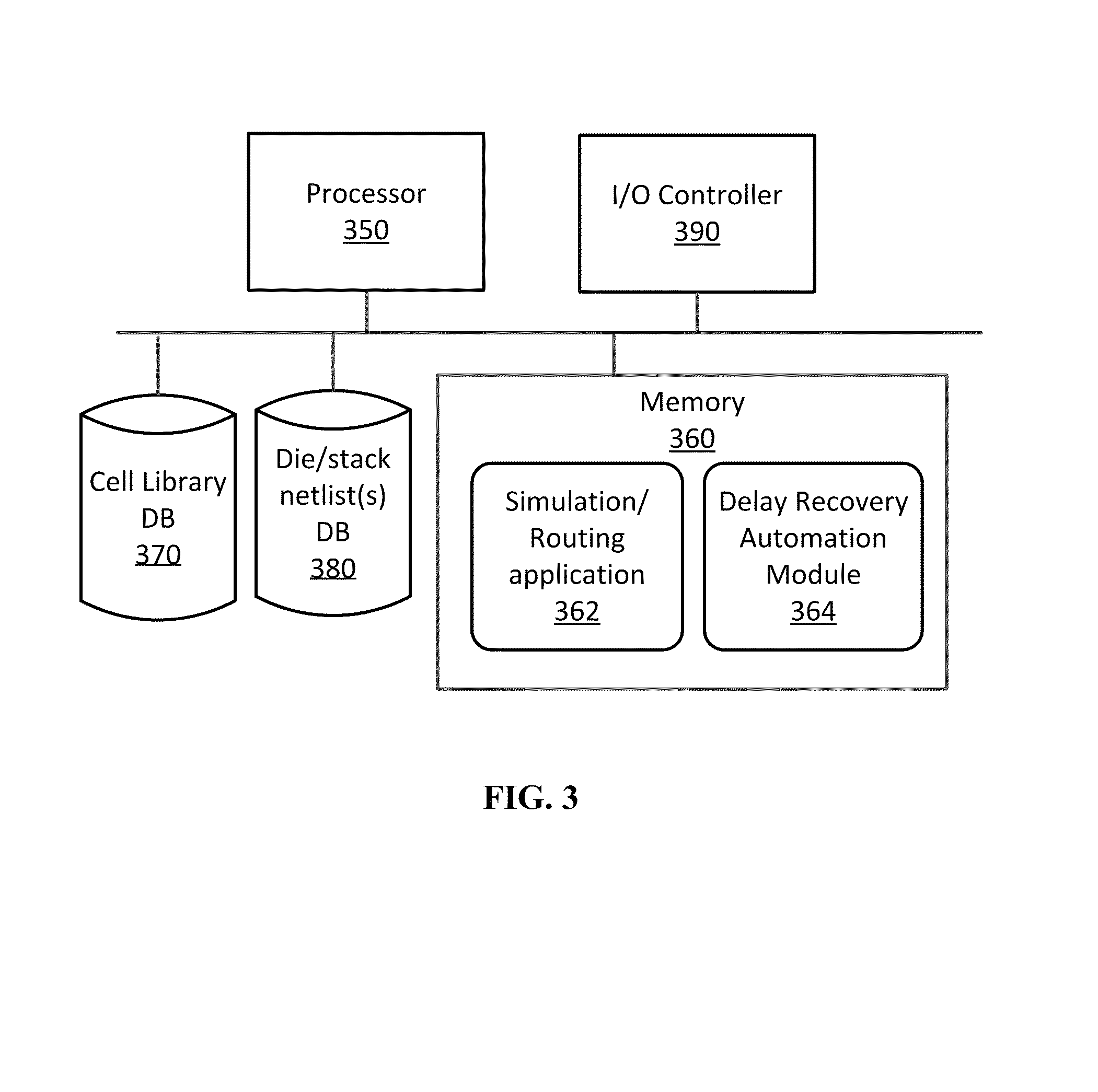
Retiming-based design flow for delay recovery on inter-die paths in 3D ICs
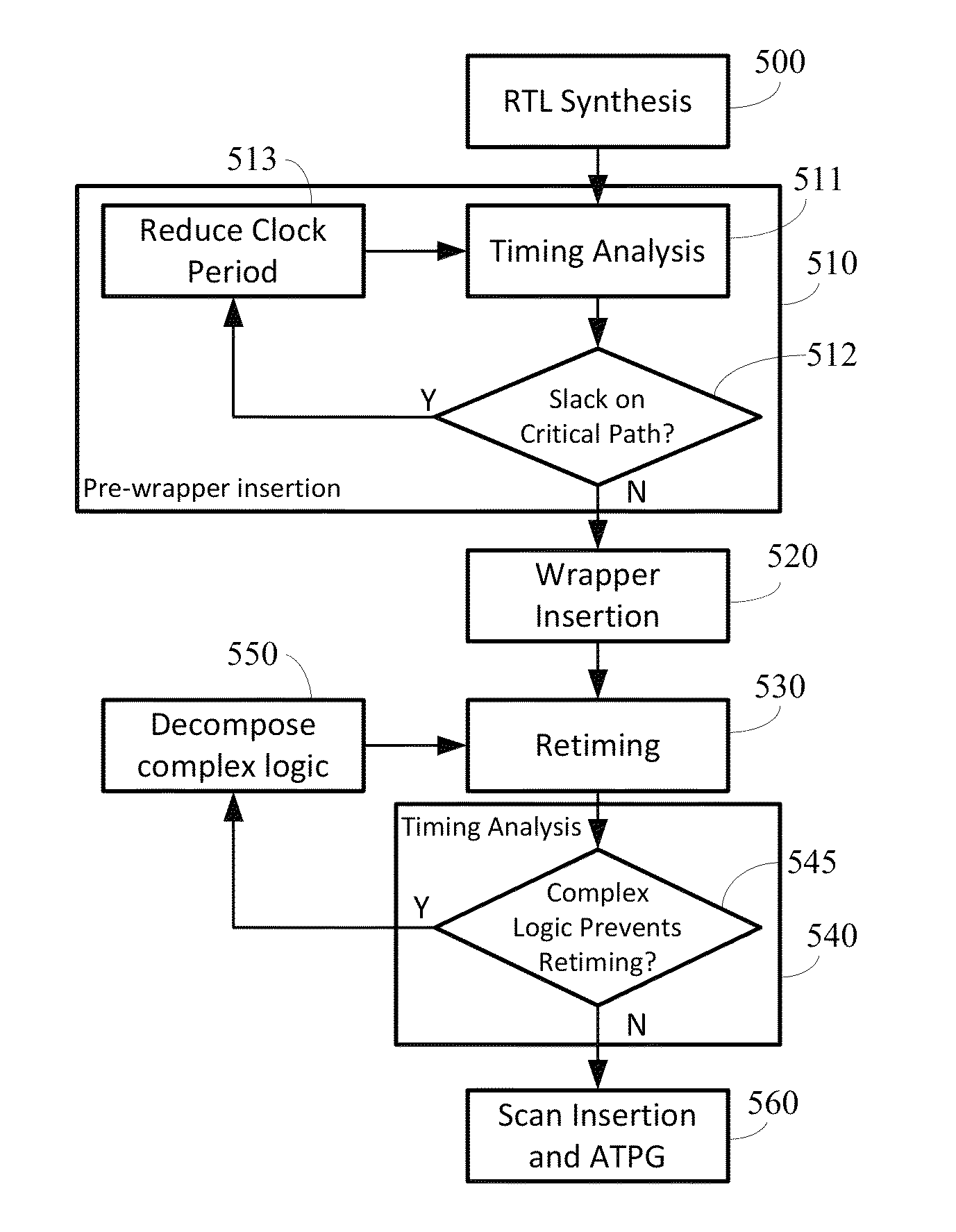
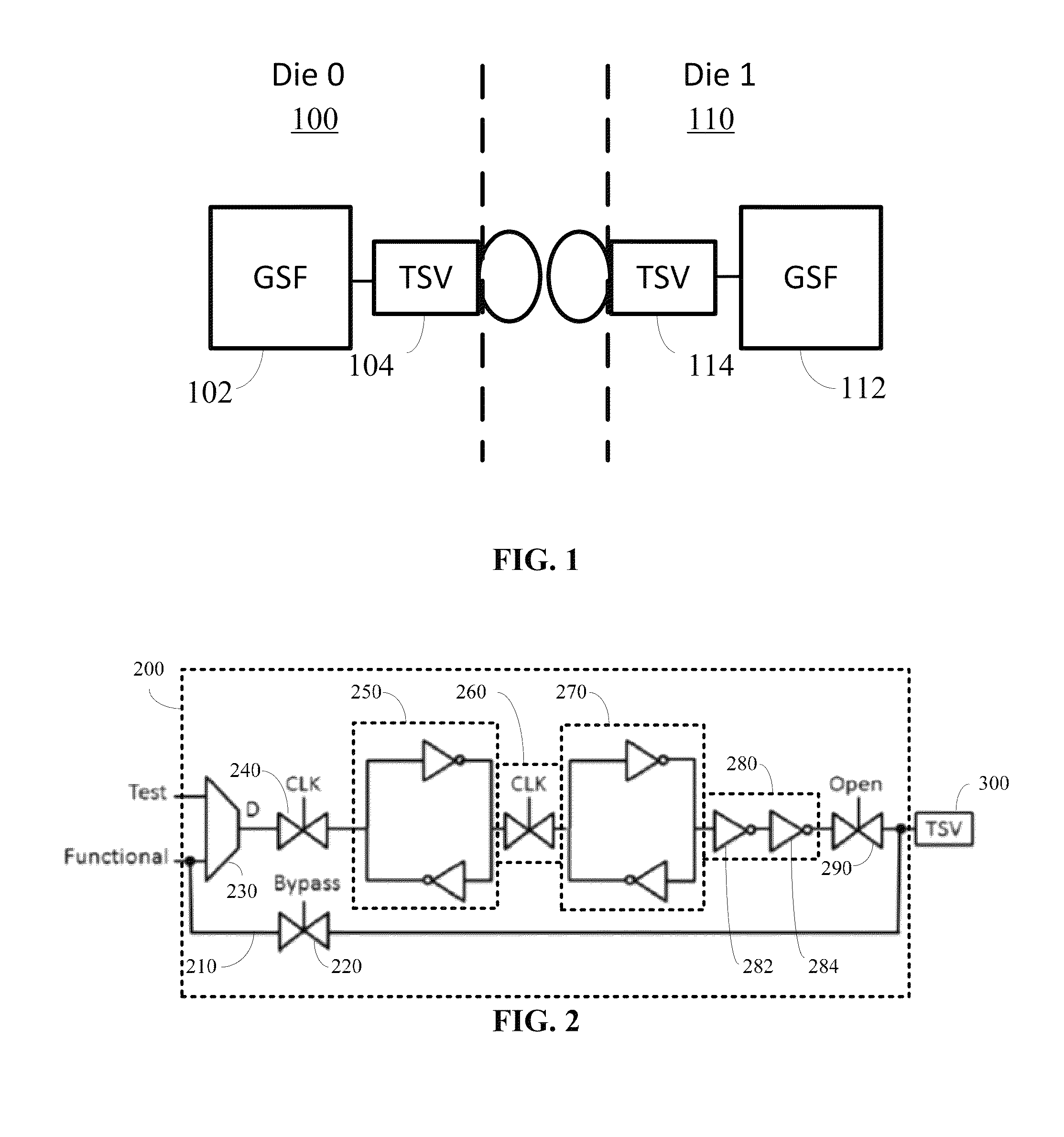
InactiveUS8832608B1Increase delayImprove latencyComputer aided designSpecial data processing applicationsDesign for testingDesign testing
A three dimensional (3D) stacked integrated circuit (IC) design-for-Testing (DfT) die-level wrapper boundary register having a bypass mode and design-level DfT delay recovery techniques are provided. Die wrappers that contain boundary registers at the interface between dies can be inserted into 3D ICs where the boundary registers include a gated scan flop with a bypass line passing the functional input to a through-silicon-via (TSV) in a manner avoiding the clocked stages of the gated scan flop during functional operation. A retiming process can be applied during design layout using a simulation / routing tool or standalone program to recover the additional delay added to the TSV paths by the DfT insertion. Retiming can be performed at both die and stack level, and in further embodiments, logic redistribution across adjacent dies of the stack can be performed for further delay optimization.
Owner:DUKE UNIV
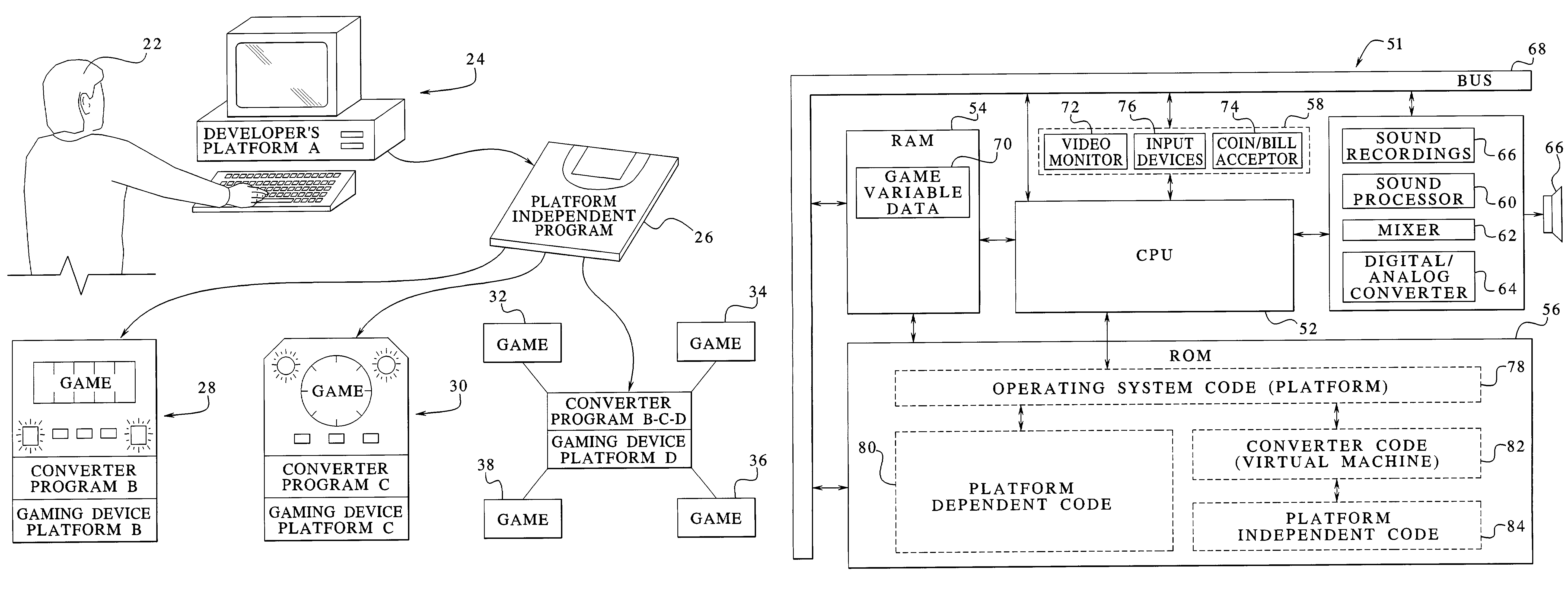
Gaming device operable with platform independent code and method
ActiveUS7901291B2Improve developmentVideo gamesSpecial data processing applicationsComputer hardwareStandalone program
A wagering gaming device which includes at least one converter program. The gaming device processor, which operates on a particular platform, can use the converter program to read and use programs otherwise incompatible with such platform, such as platform independent programs. This type of gaming device enables developers to develop code on platforms which are different in type from the gaming device platform, and the gaming device processor can read and use this code to operate the gaming device.
Owner:IGT
Foundational development framework
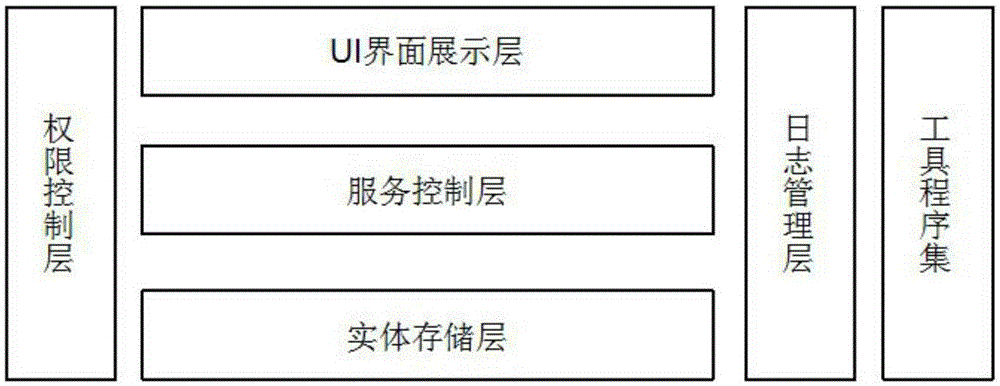
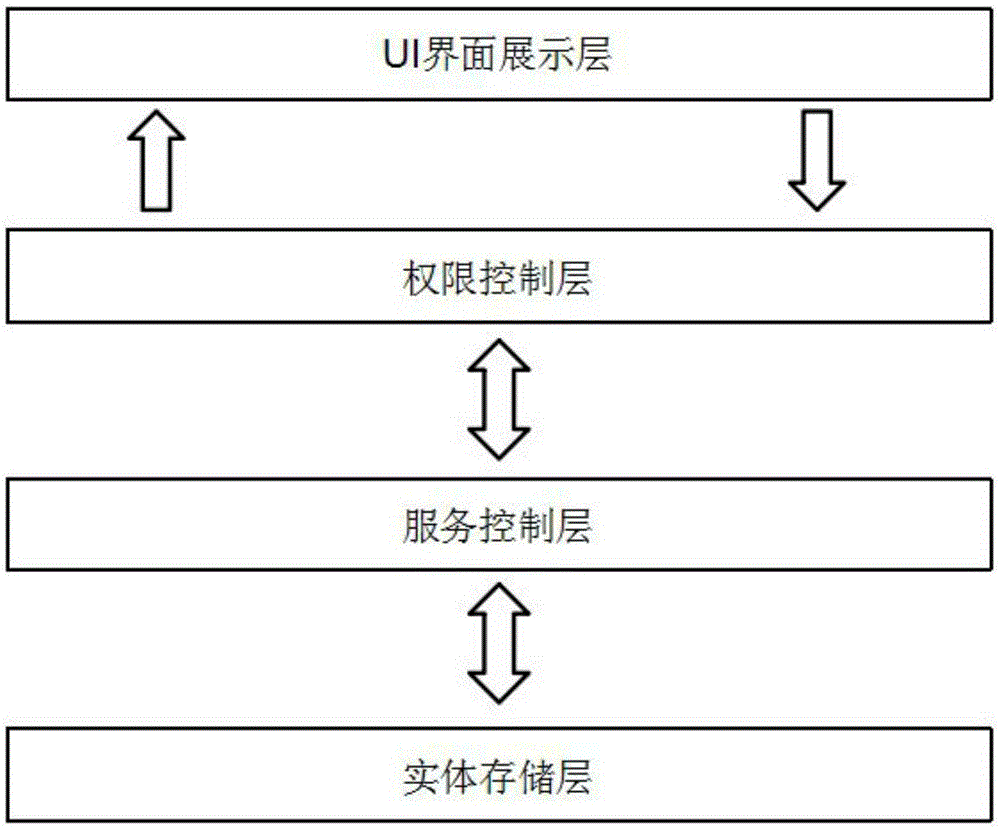
InactiveCN105302575AOperation will not affectNo need for secondary developmentSpecific program execution arrangementsExecution controlStandalone program
The invention relates to a foundational development framework. The foundational development framework adopts C#, HTML, CSS and Javascript languages for development and comprises a UI interface display layer, a service control layer, an entity storage layer, an authority control layer, a log management layer and a tool program set. The UI interface display layer, the authority control layer, the service control layer and the entity storage layer are sequentially connected. The UI interface display layer achieves cross-platform application development through an assembly composed of HTML, CSS and JavaScript, and is applicable to interface development of a Web application program of a B / S structure. For the service control layer, the entity storage layer, the authority control layer, the log management layer and the tool program set, Microsoft. NET Framework 4.0 is adopted as a foundation, and C# language is used for writing. The foundational development framework has the advantages that an independent program domain running mechanism is adopted, creating, updating and destruction of all independent program domains are managed in a unified mode by achieving a program executing pool, and monitoring is carried out by combining an authority control interface and a log production interface. A means is provided for service execution control.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
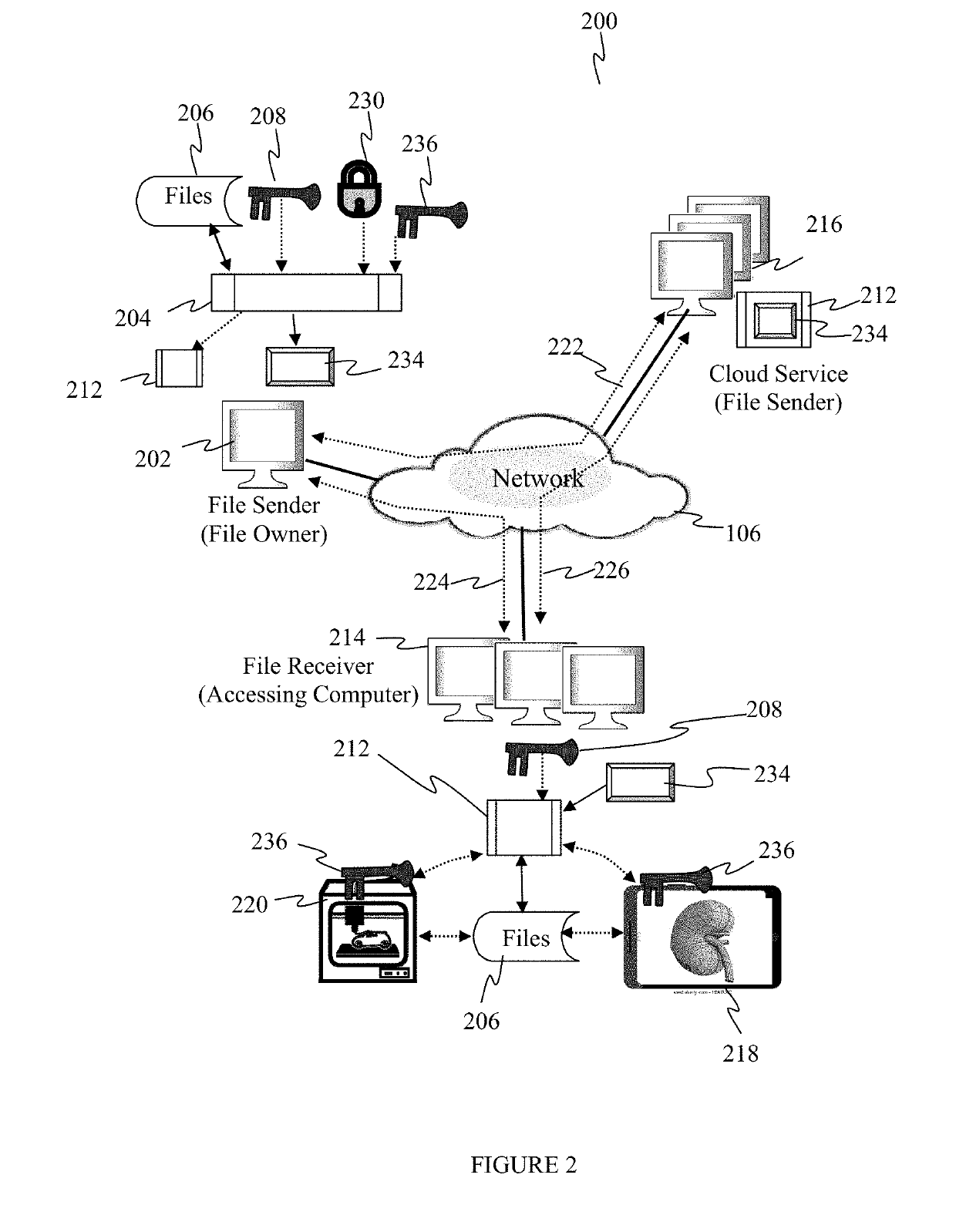
Systems, devices and methods for protecting and exchanging electronic computer files
ActiveUS20190121989A1Multiple keys/algorithms usageDigital data protectionOperational systemWeb browser
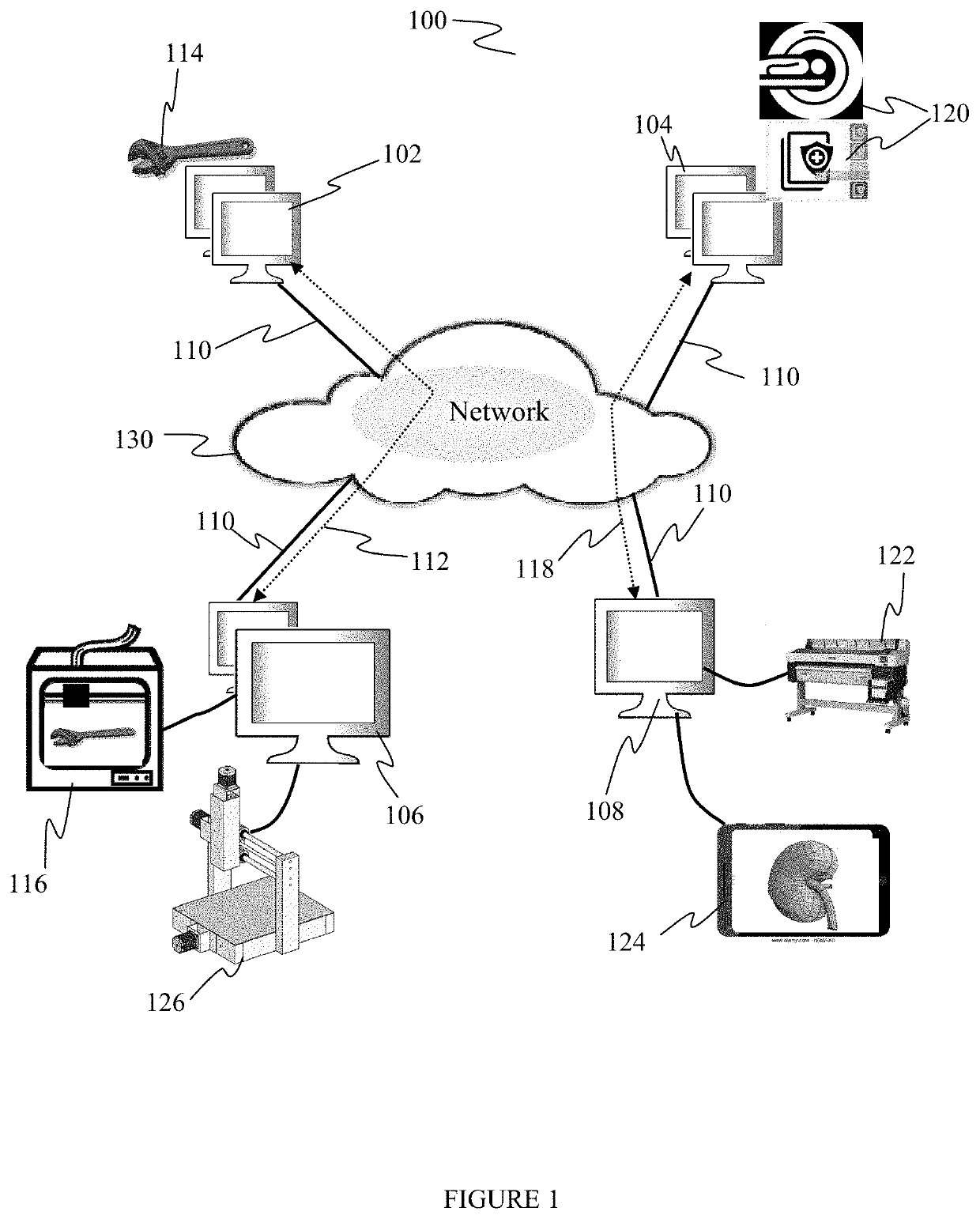
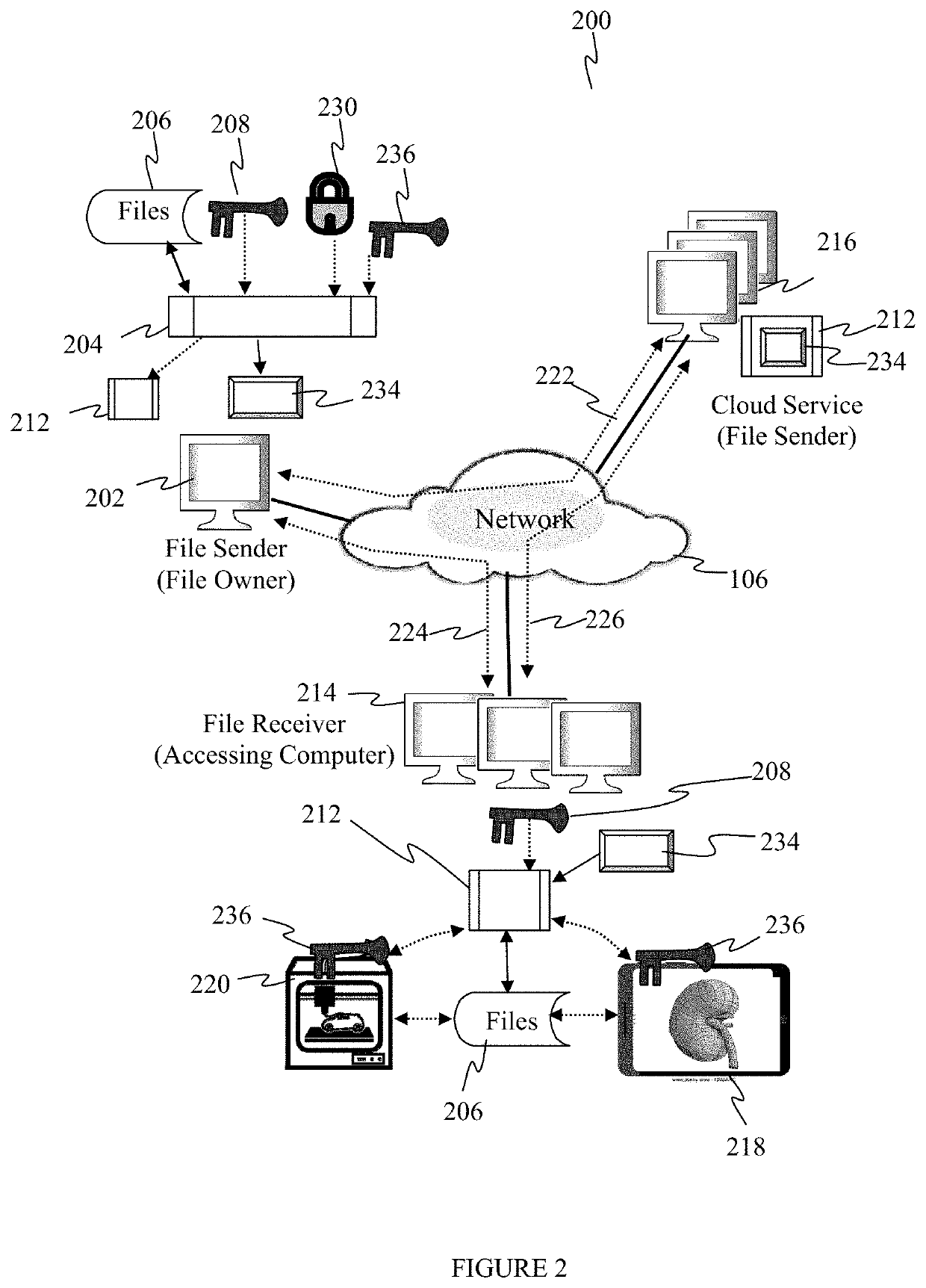
Embodiments described herein provide a system and method for controlling access to electronic files by linking the files to a file access monitoring system, called the file access monitor in this application. The file access monitor then authorizes the use of the one or more files by performing one or more qualifying steps on the accessing computer system. The file access monitor may be a standalone program or an embedded logic within a closed system like an application, an operating system (O / S), an external device like a printer, a web browser or a web browsing application. Access to electronic files can include the exchange, modification, execution, printing, viewing, listening, copying and replication of these files to name a few. A given protected electronic file is transferred from a sending computer system to a receiving computer system for eventual access. The receiving computer may also become the accessing computer should a user on the receiving computer wish to access the transferred file. To access a given protected file one or more qualifying steps must be performed to grant access and to unlock the file. In some cases the qualifying step involves a specific activity called a system attribute identification process.
Owner:3D BRIDGE SOLUTIONS INC
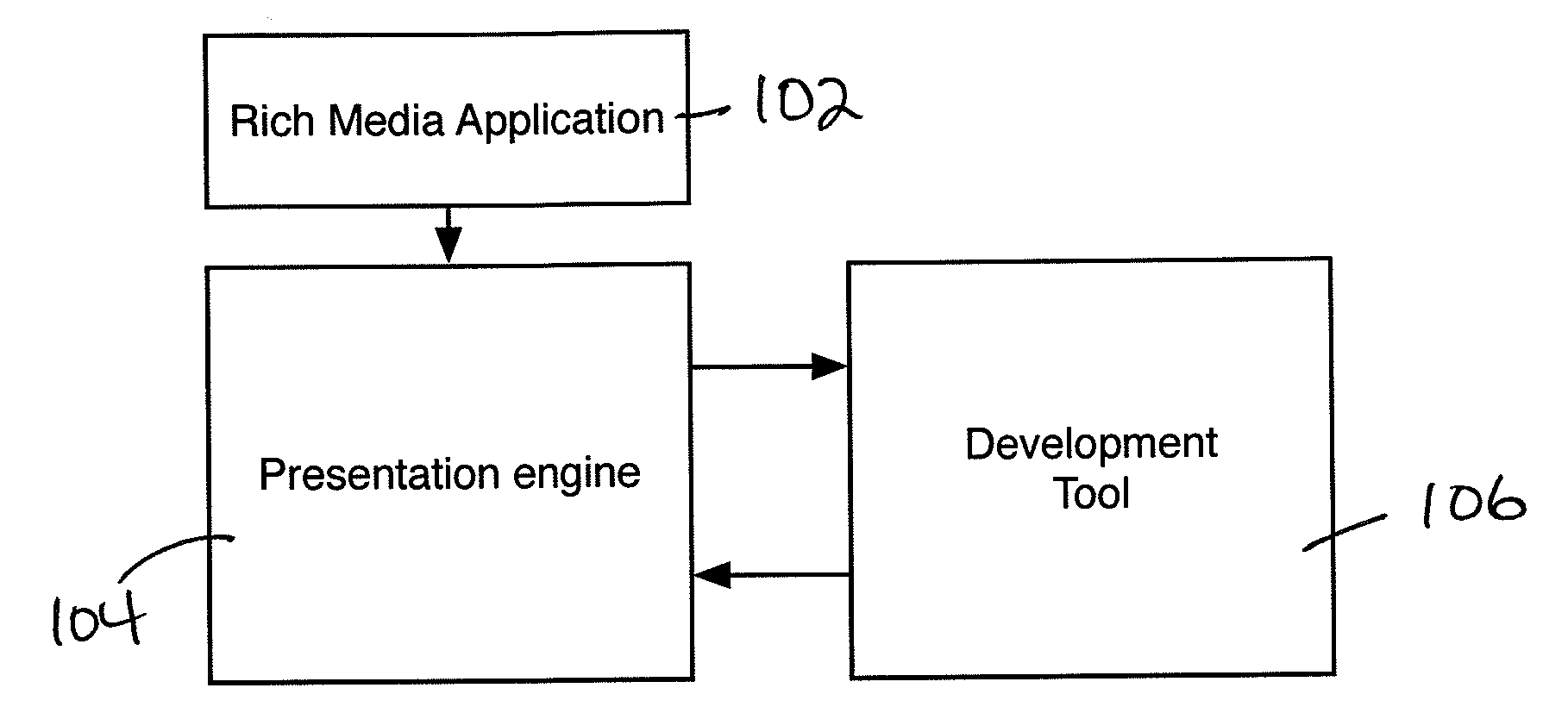
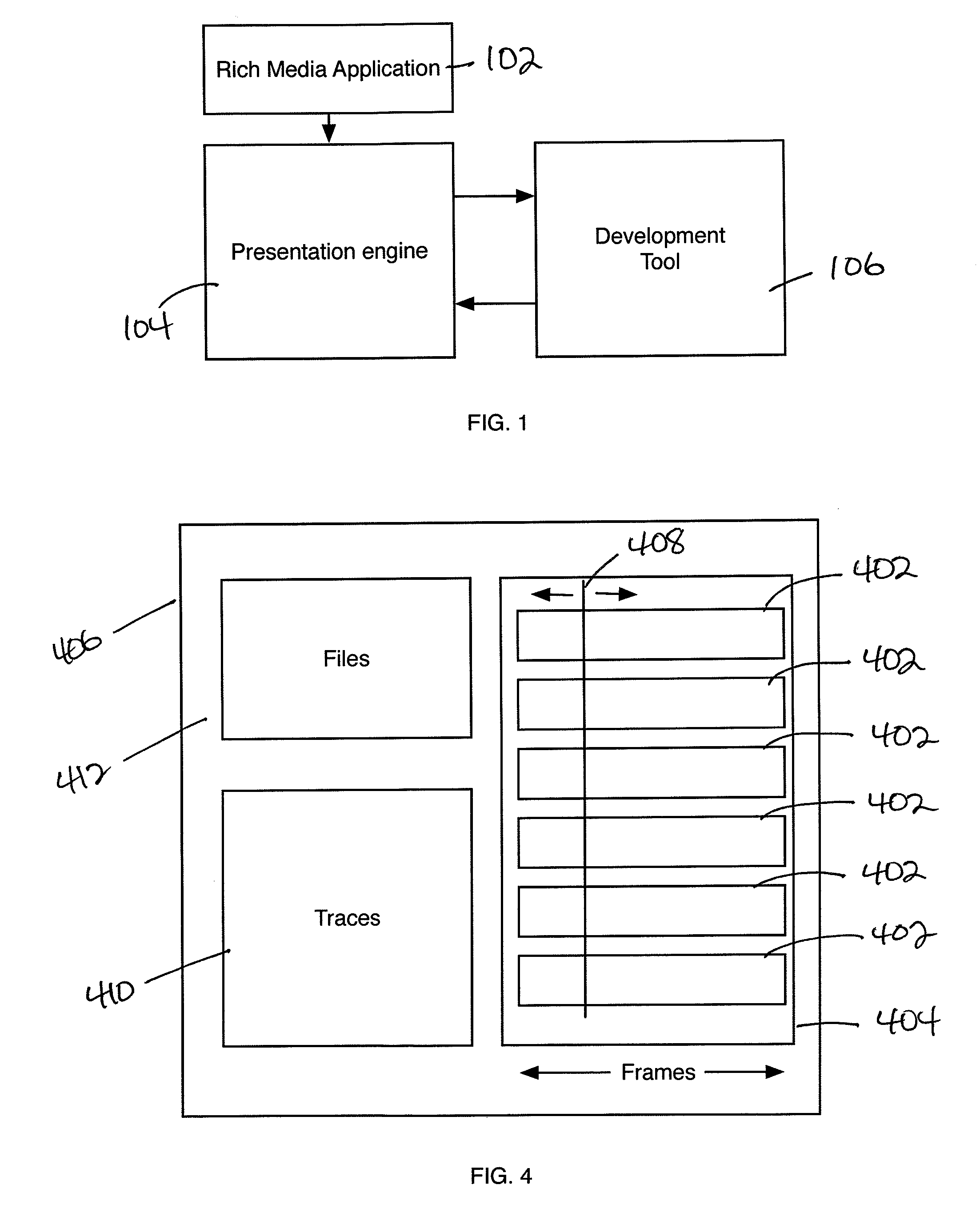
Development Tool for Animated Graphics Application
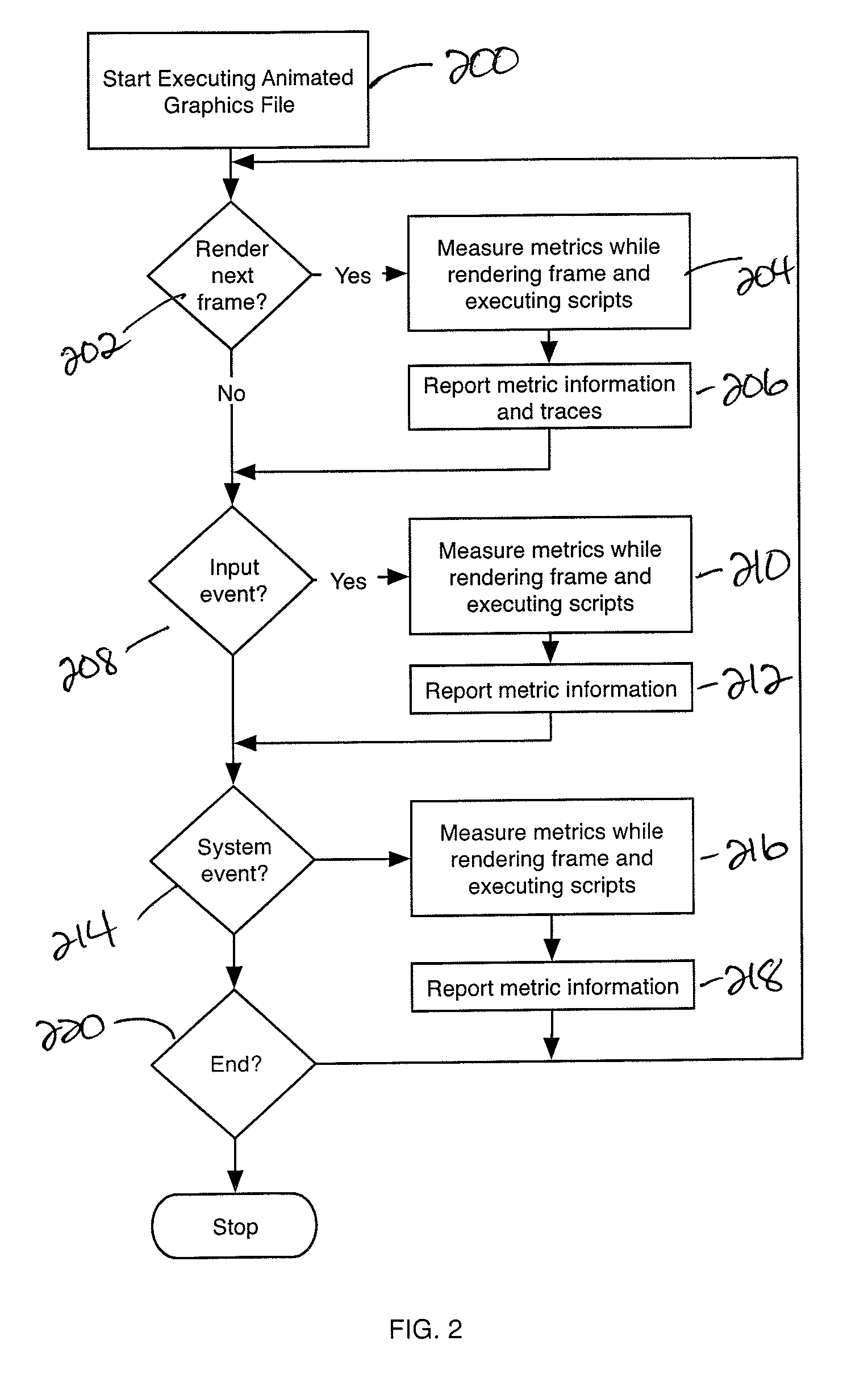
A presentation engine collects information concerning the rendering of the frames of an animated graphics application, such the time taken for rendering the frame and the amount of memory used. This information quantifies the amount of certain computing resources being utilized on a per-frame basis, enabling identification by the authors of the animated graphics application, particularly by the designers of the animated graphics, of frames that are problematic, especially on resource-limited devices. The generation of information does not depend on the animated graphics application being instrumented to generate the metrics. The method is adaptable to any resource-limited device, to which the presentation engine is ported or adapted to run. When executing on a resource-limited device, the information is sent to a workstation for analysis. An analysis tool, which may be a stand-alone program or part of an authoring tool or other program, displays the collected metrics graphically in relation to the frame.
Owner:BLUESTREAK TECH INC
System level testing for substation automation systems
ActiveCN101842713AEmergency protective circuit arrangementsCircuit interrupters testingTime informationElectricity
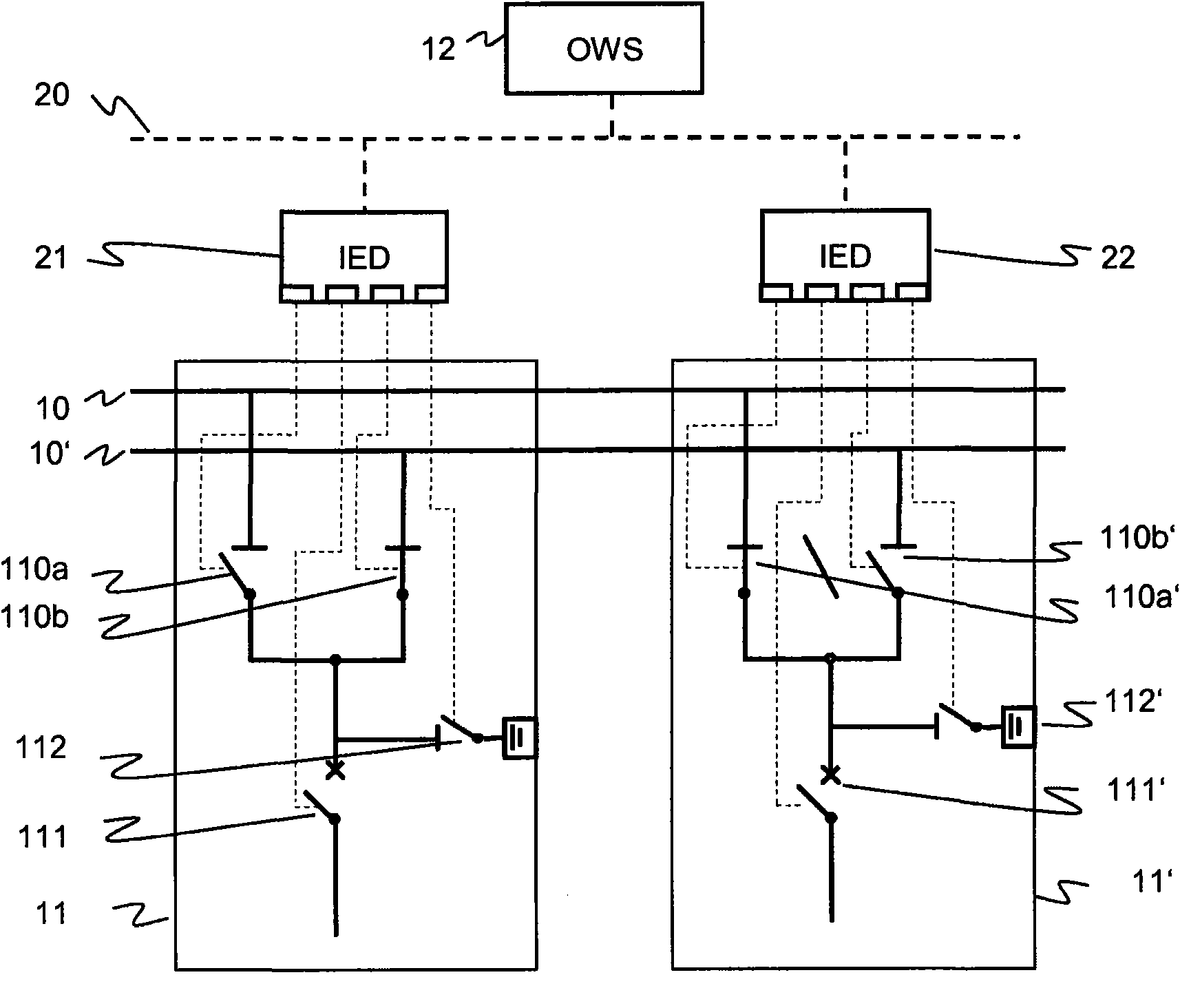
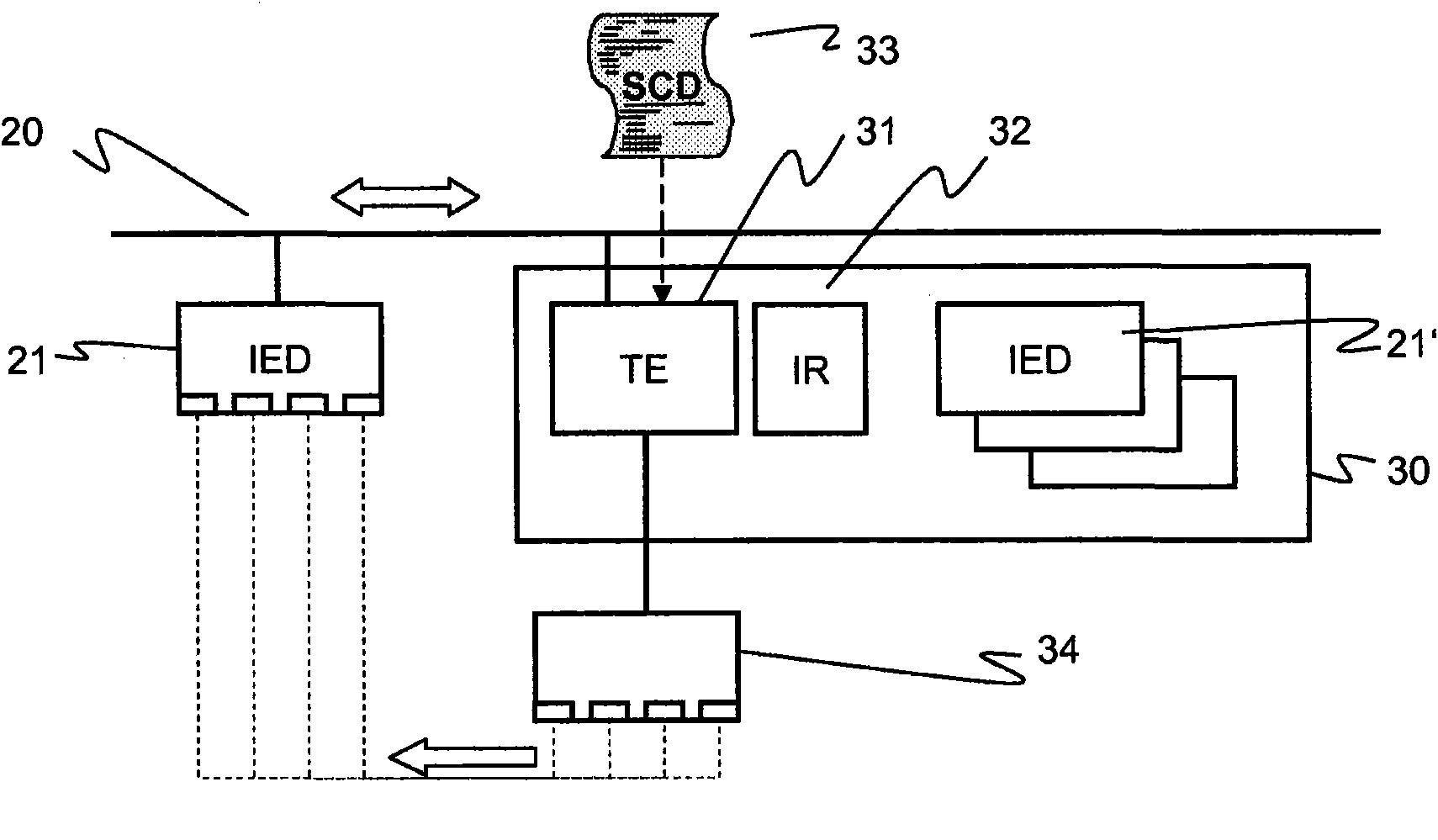
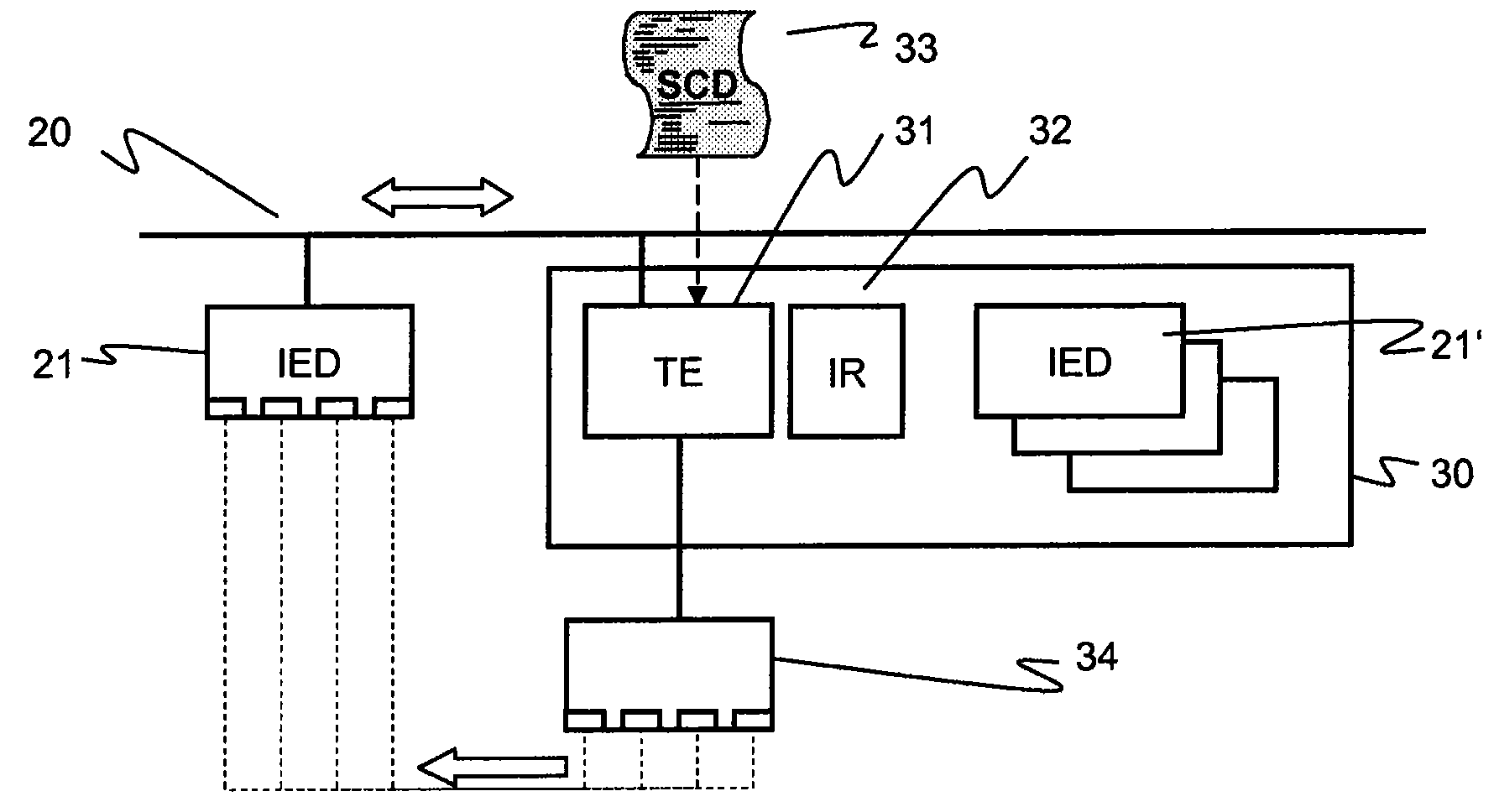
The present invention proposes that protection, measurement and control IEDs in a substation compute, according to interlocking rules or physical principles as well as a knowledge of the dynamic topology of the substation, for every switch they control if that switch may be operated safely, in contrast to a conventional and separate programming of the interlocking logic for each IED. To this purpose, the IEDs have access to the substation electrical topology, to the real-time information generated by other IEDs, and to the rules for interlocking. The invention takes advantage of a standardized Substation Configuration Description (SCD) of the substation for which the SA system is intended, as well as of a standardized description of the implemented device functions or capabilities of an individual IED. In particular, the substation topology is available from the substation configuration description (SCD file in IEC 61850 format), the real time information about the position of switches and line voltage / current can be read over the IEC 61850 protocol and the rules are available in script form. This concept applies both to simulated and real devices, and greatly increases system testing possibilities by supporting an efficient configuration of a simulation.
Owner:HITACHI ENERGY LTD
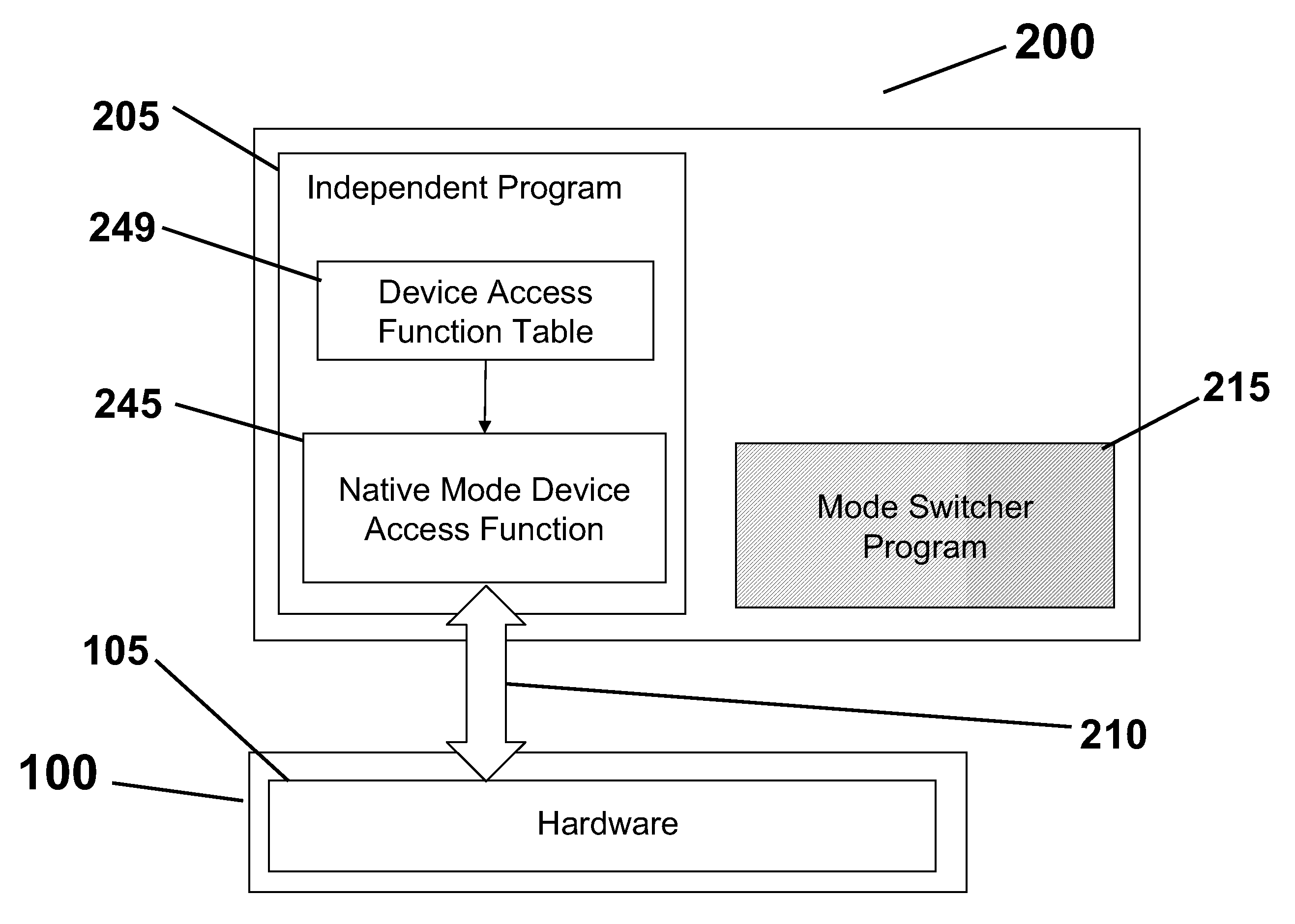
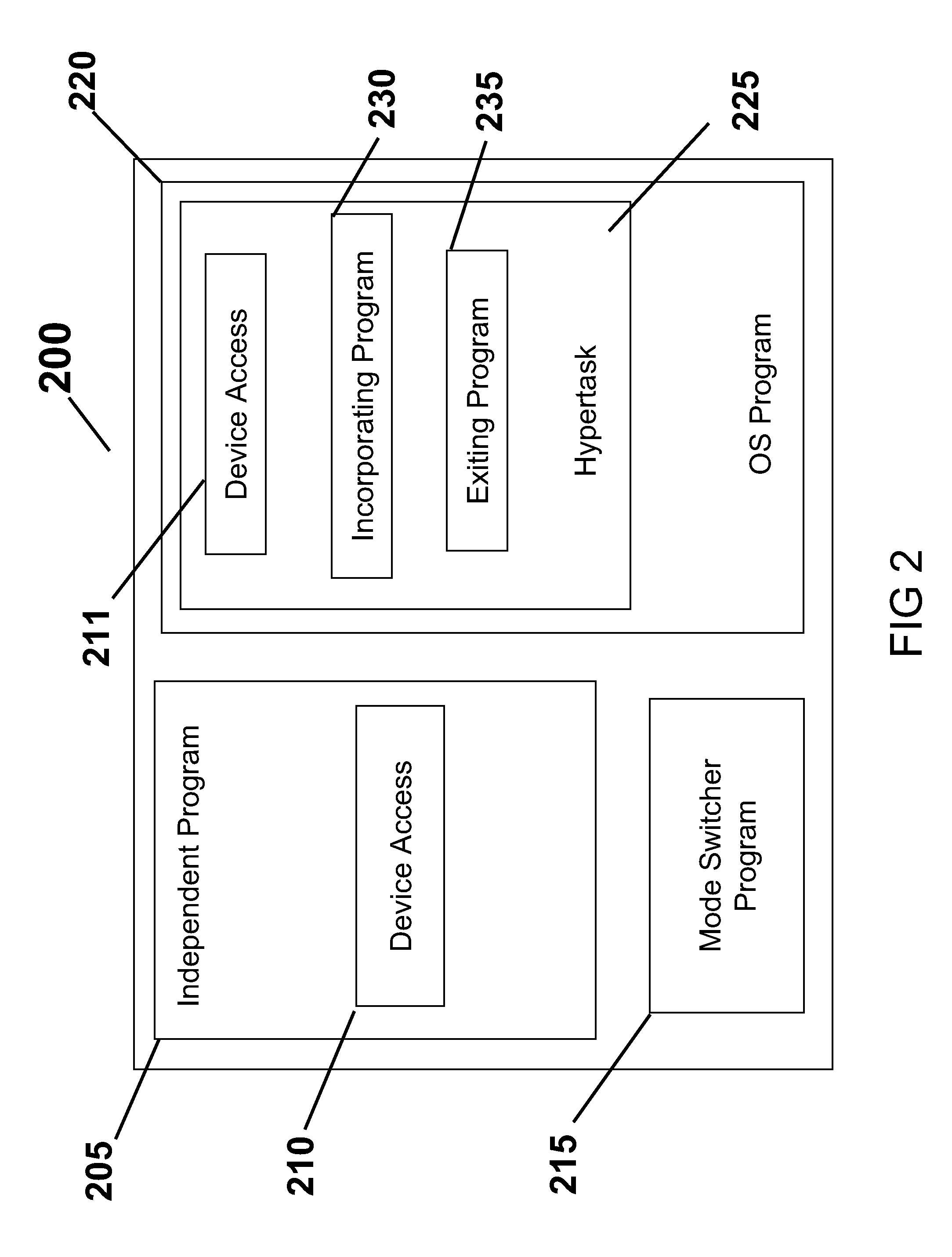
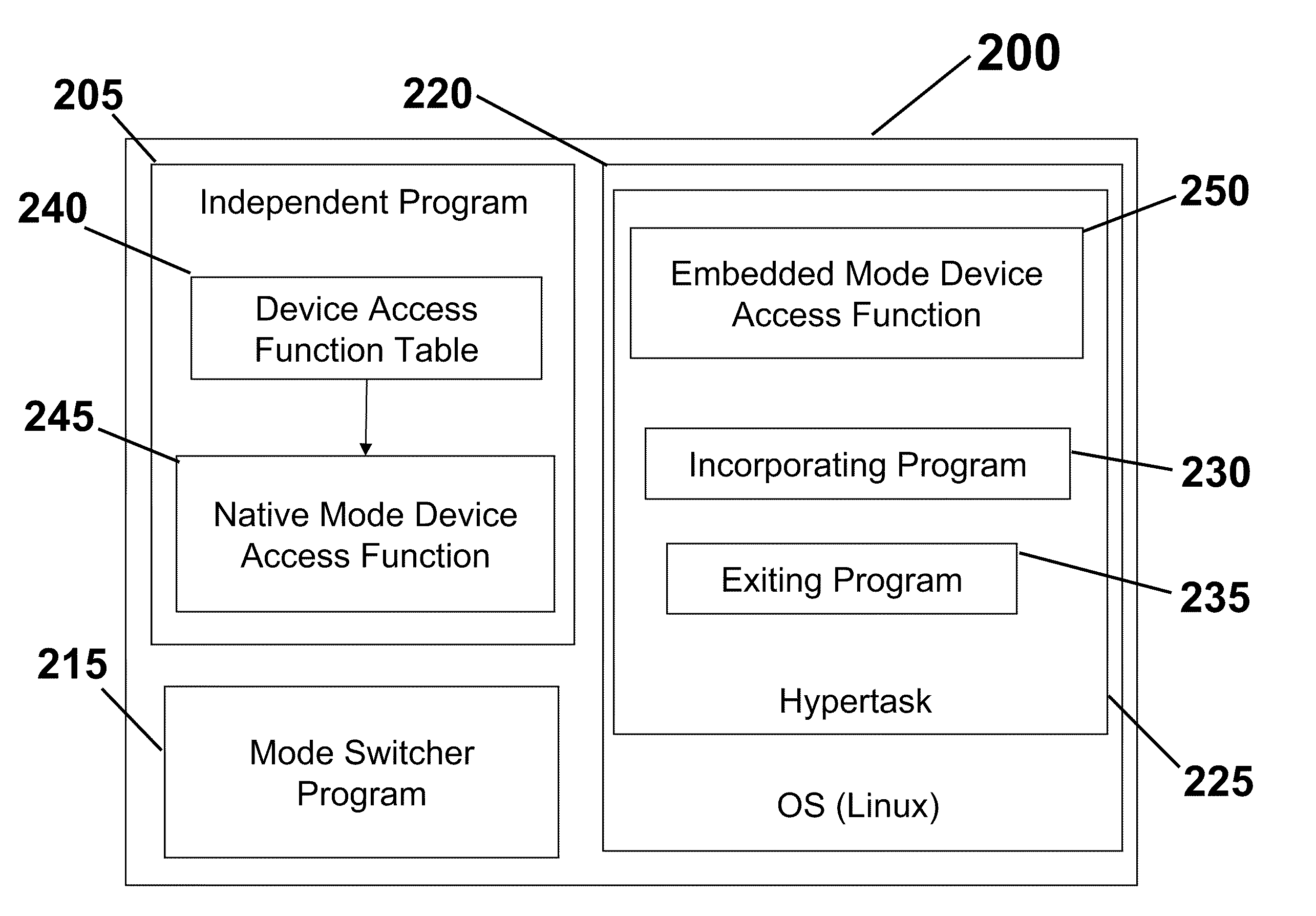
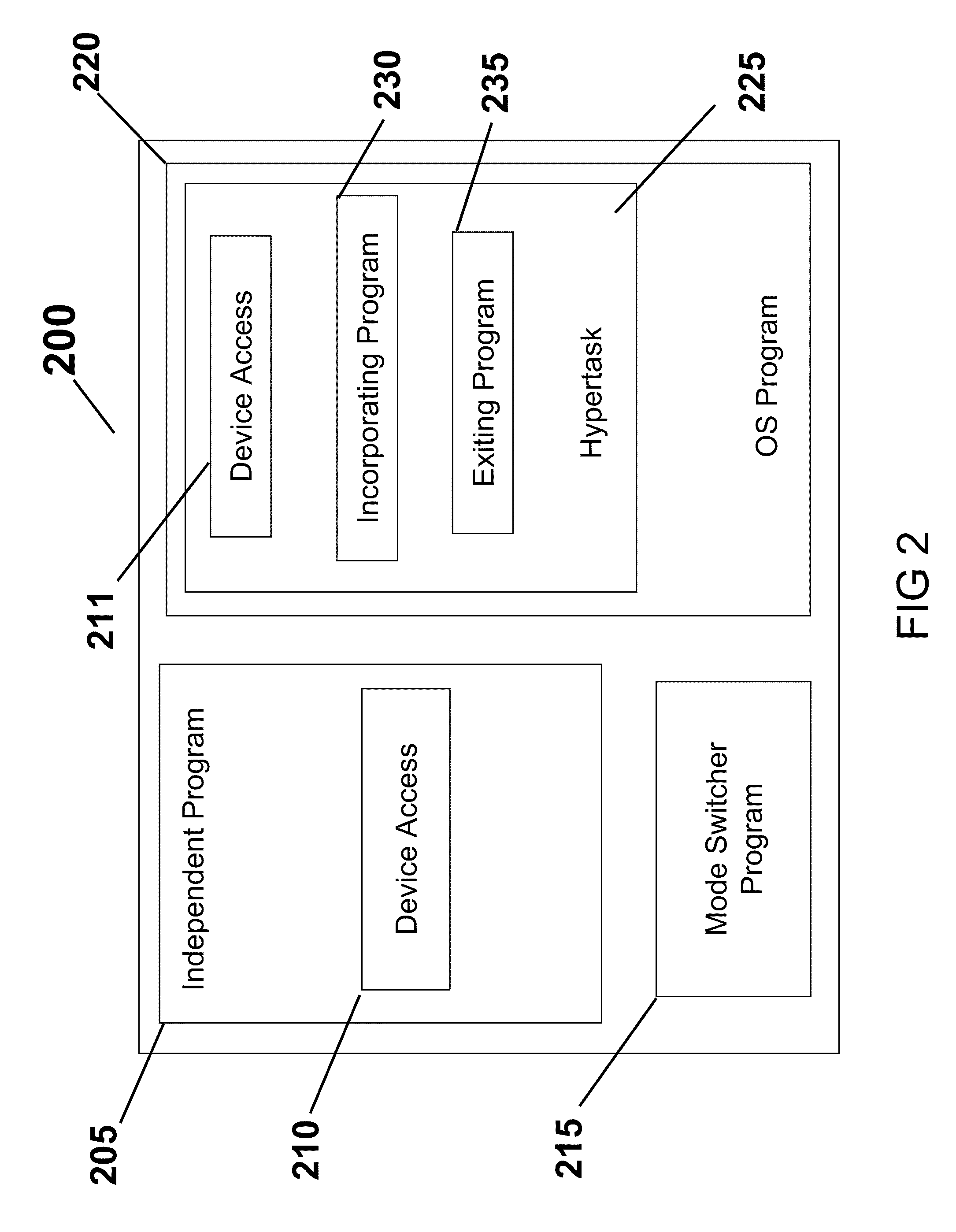
System and Methods for Migrating Independently Executing Program into and Out of an Operating System
This invention generally relates to a methods and system in the field of independent programs operating within an operating system such as Linux and more particularly to computer software embodied in a computer readable medium including: an independent program for running autonomously in a native mode within an associated computer processor; an operating system program for running autonomously within an associated computer processor; a mode switcher process for switching operation from the independent program to the operating system program whereby the independent program functions as an embedded entity of the operating system; and wherein the mode switcher program switches the independent program from the operating system program whereby the independent program runs autonomously in the native mode.
Owner:NETABPECTRUM
Method and apparatus for performing distributed processing of program code
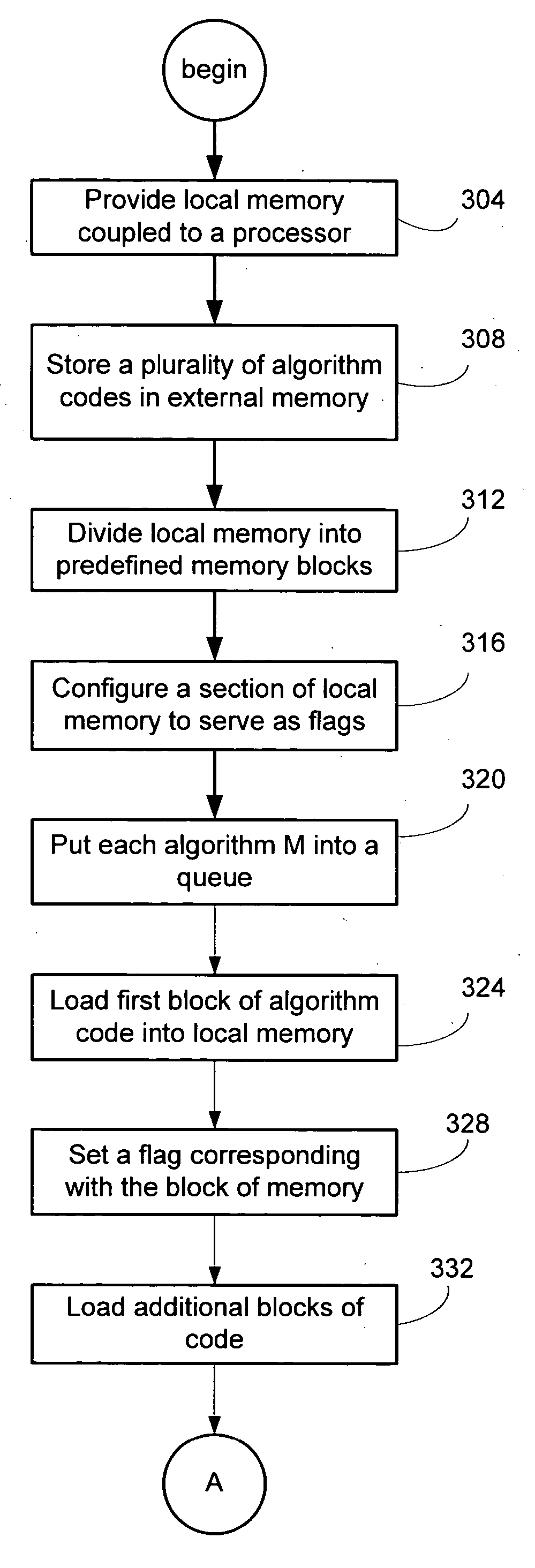
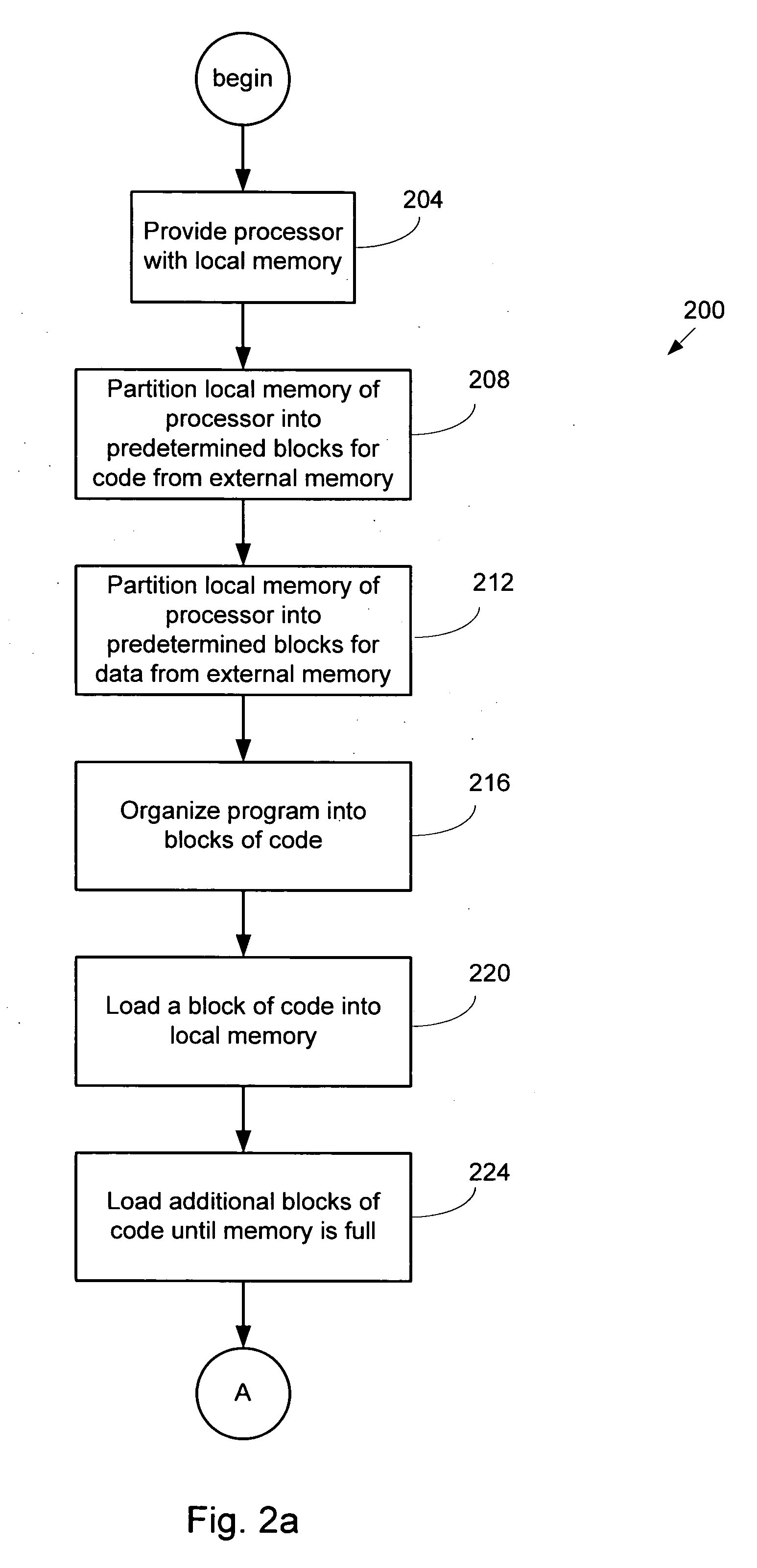
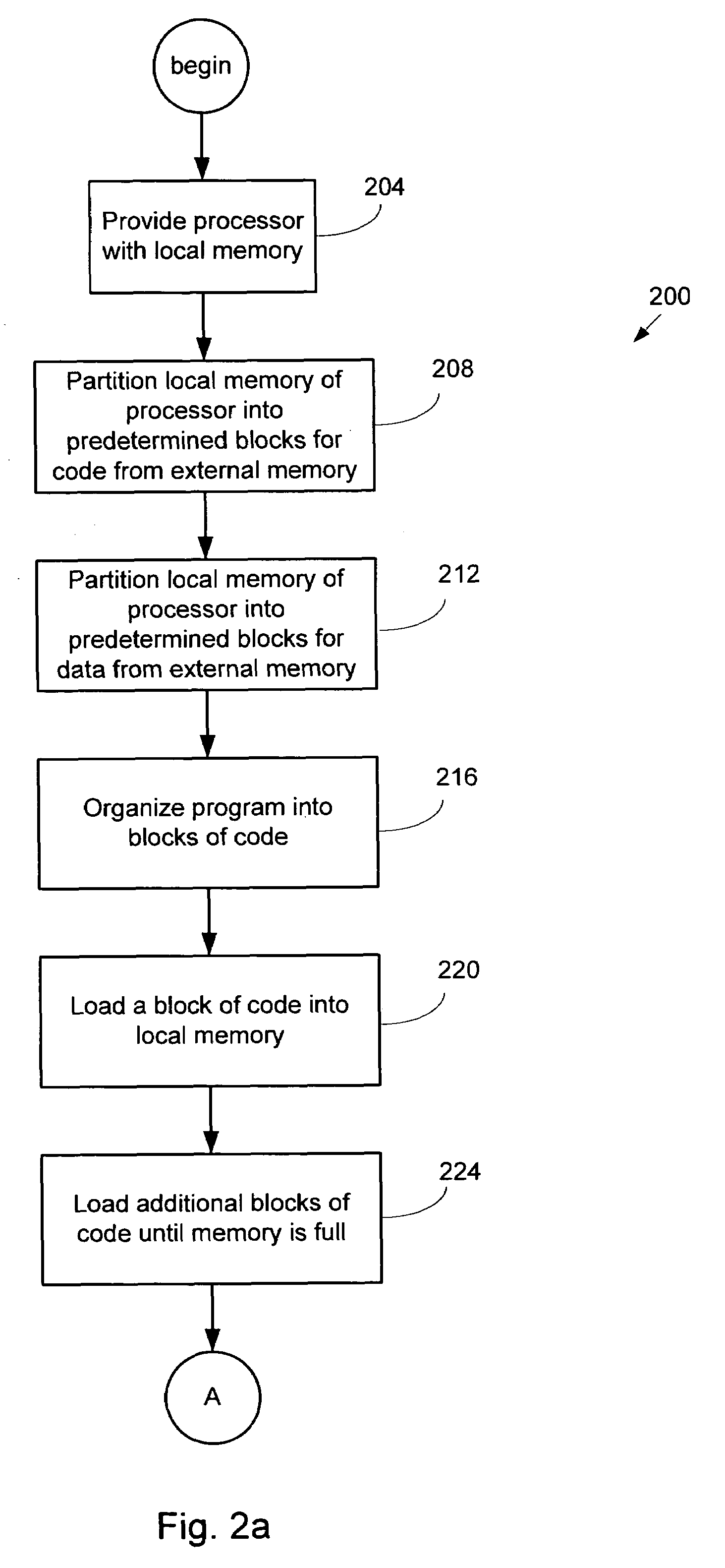
InactiveUS20050055515A1Program synchronisationMemory adressing/allocation/relocationExternal storageStandalone program
A processor having a limited amount of local memory for storing code and / or data utilizes a program stored in external memory. The program stored in external memory is configured into blocks which can be loaded individually into the local memory for execution. Queuing the individual blocks of code allows the program to be executed by the processor and also facilitates loading of the subsequent code to be executed. A semaphore system can be utilized to indicate which blocks of local memory are available / unavailable. The system can support the interaction of multiple independent programs in external memory.
Owner:TAMIRAS PER PTE LTD LLC
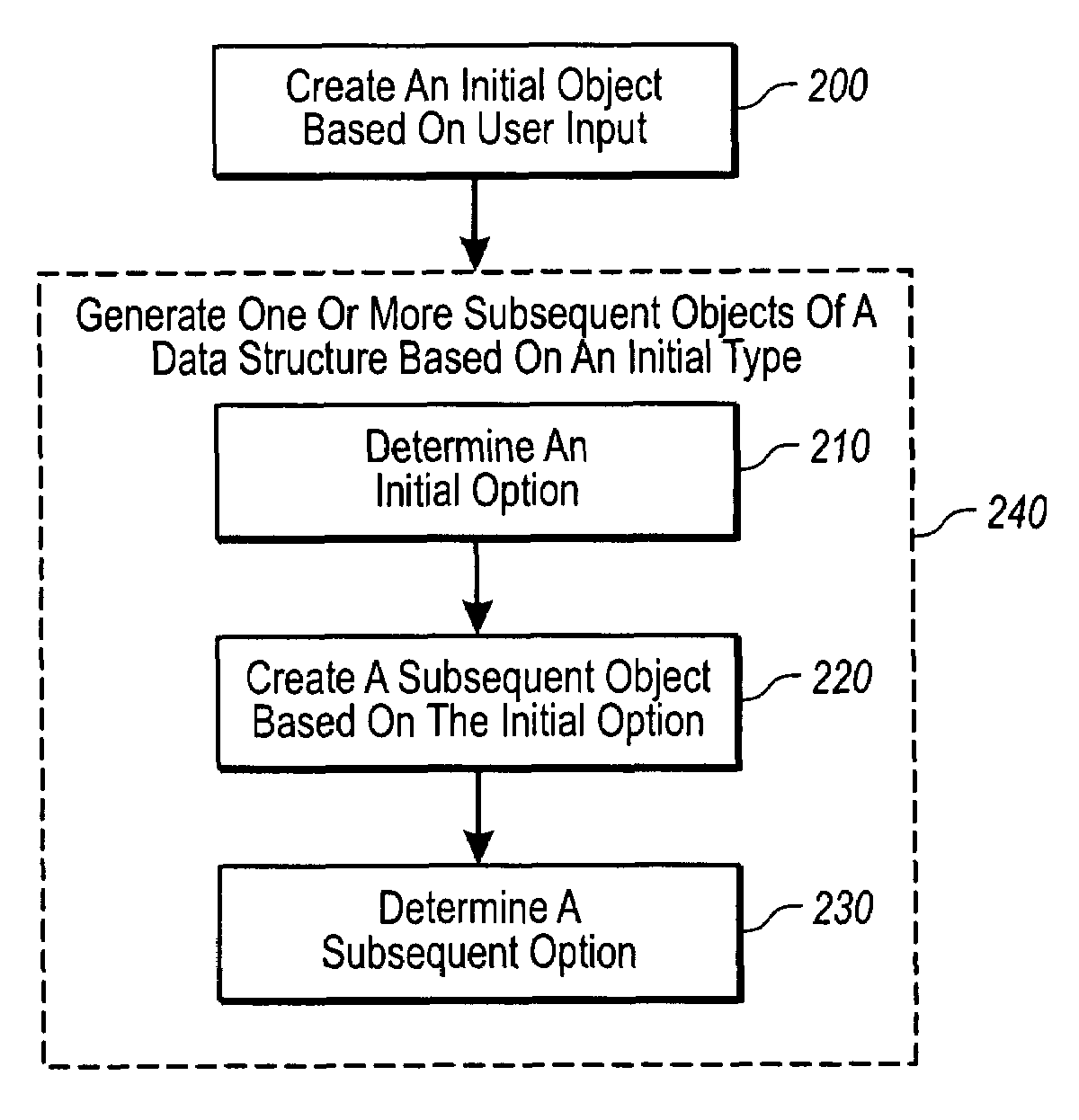
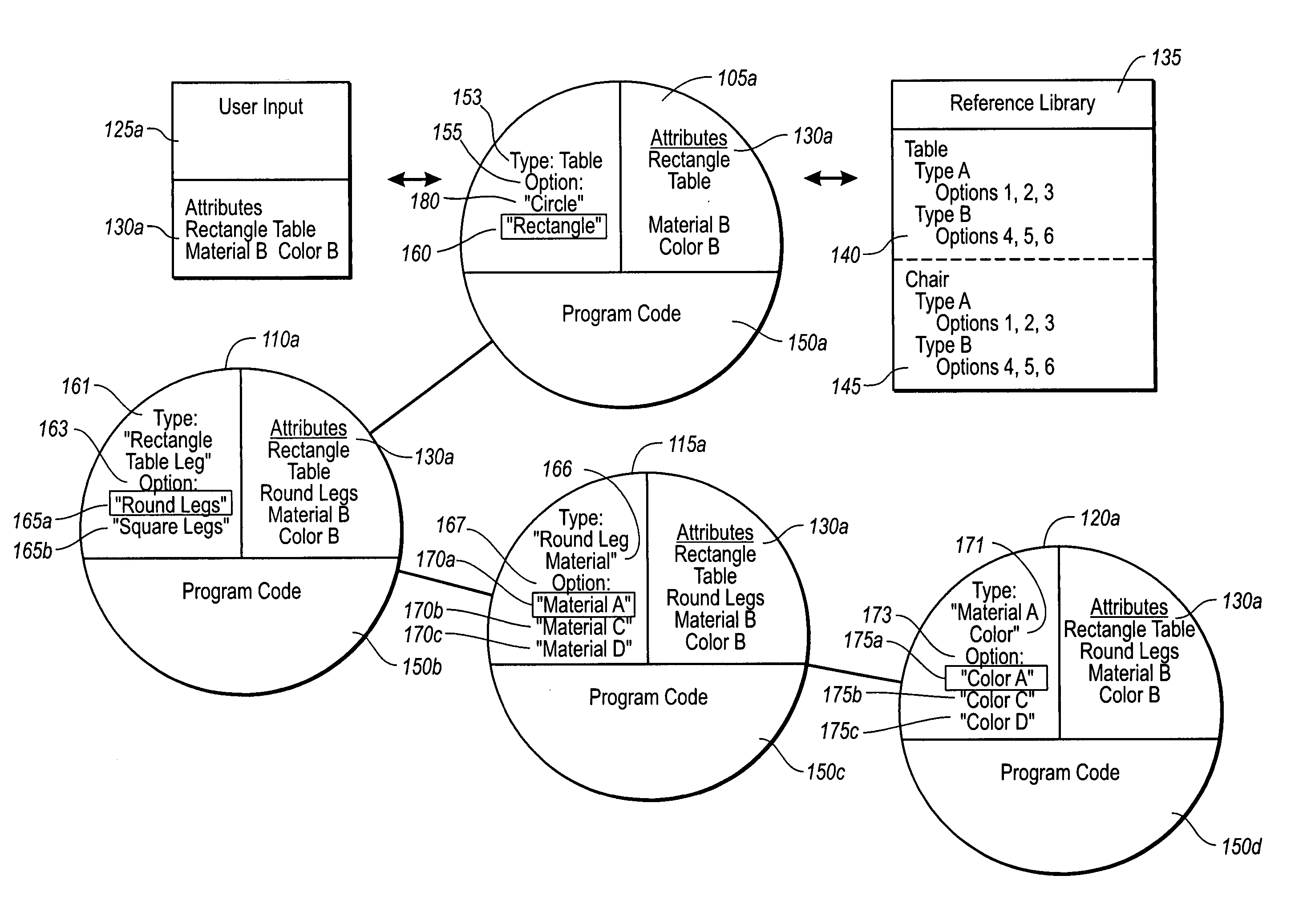
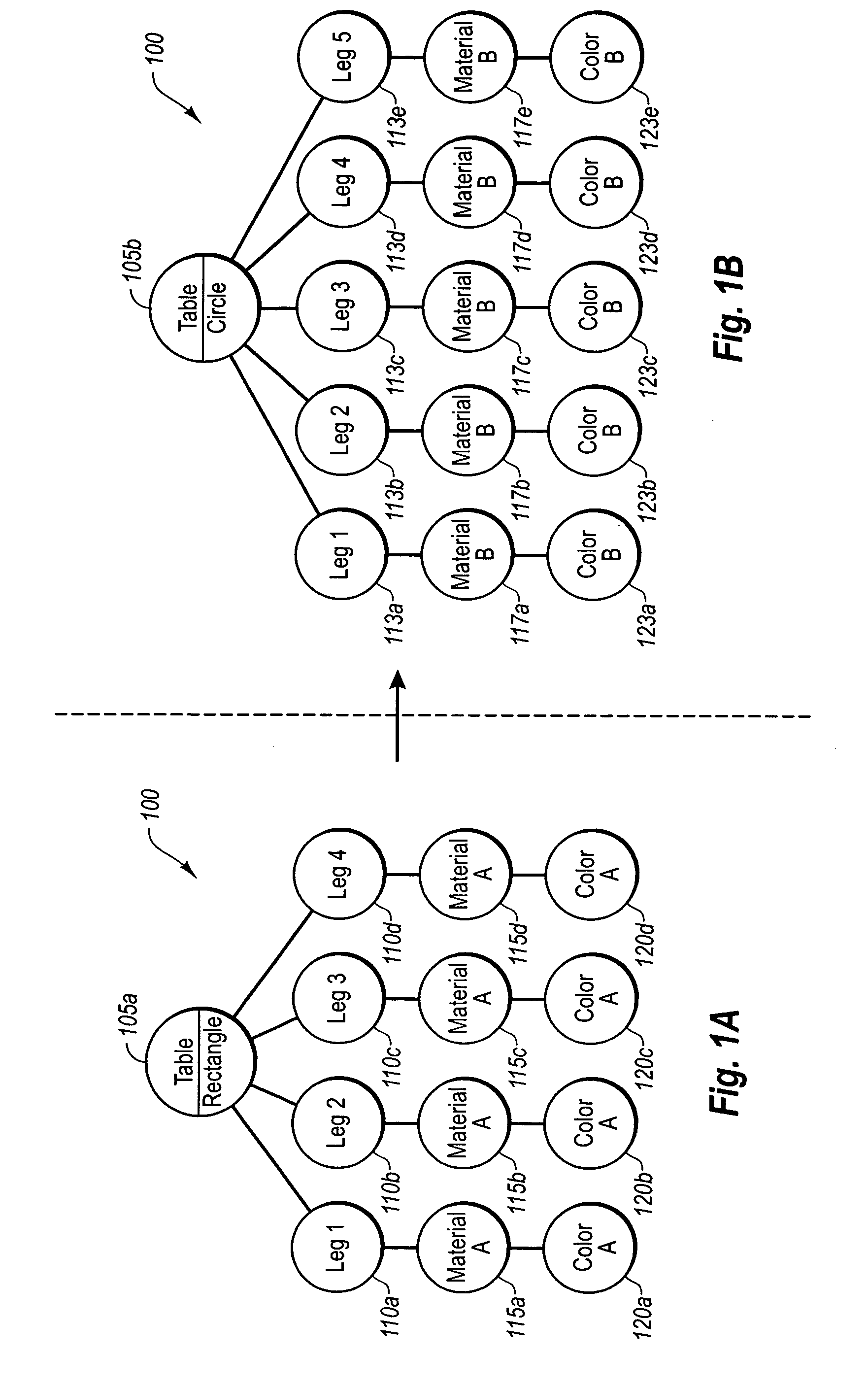
Capturing a user's design intent with resolvable objects
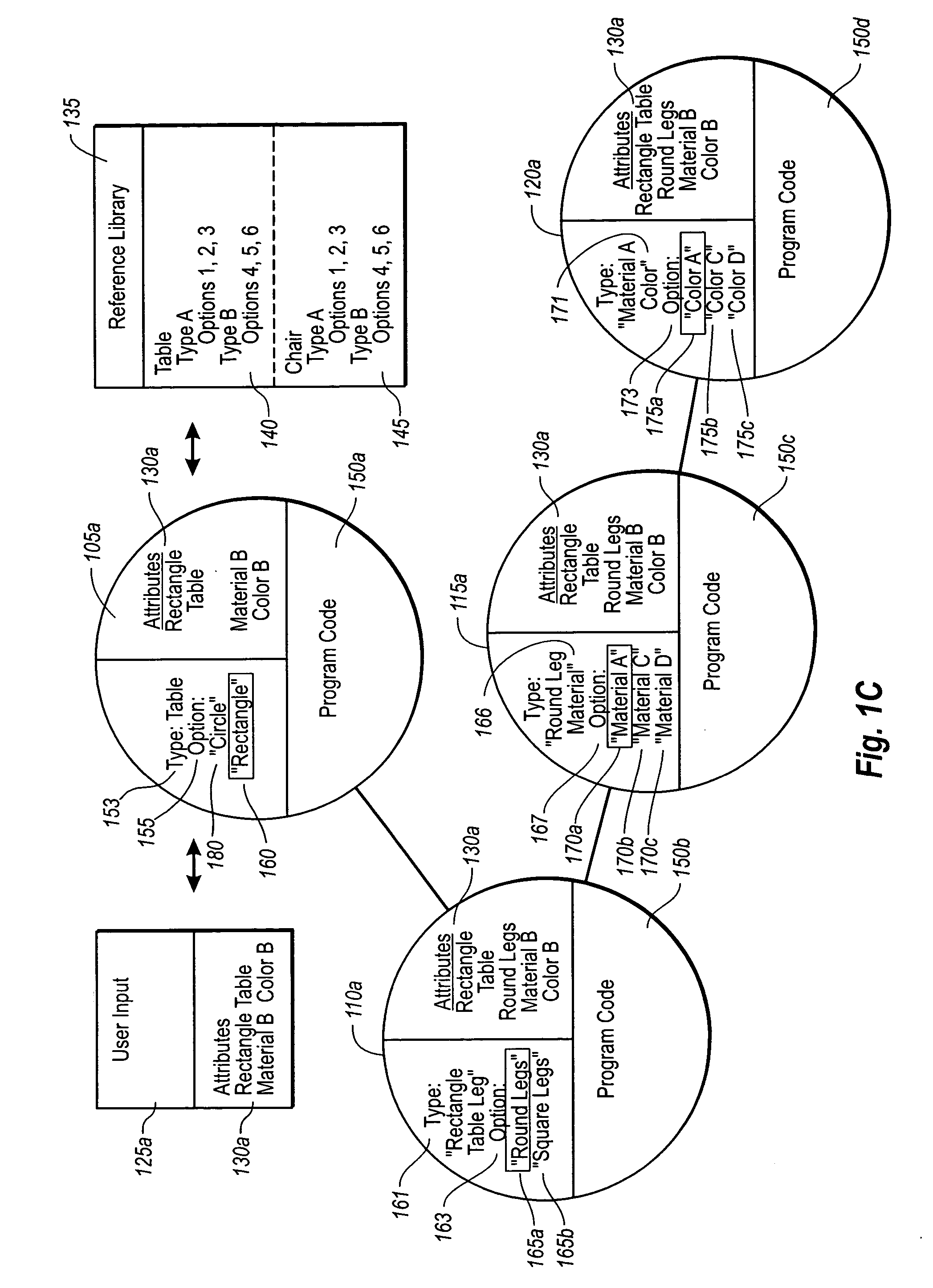
Software for designing interior and / or exterior spaces efficiently ensures that user intent is captured in a timely, practical manner. When a user creates an input, such as selecting a shape of a table to put into a design space, the design software creates an initial object that is managed as part of a data structure. Generally, the initial object includes a type element having one or more options. Program code in the created initial object determines an appropriate option based on any number of factors including, but not limited to, elements of the user's original input. A subsequent child object with a set of independent program code is also created, which has as its type the option determined from the previous initial object. The subsequent object also determines its options based on attributes of the user's input, and creates any additional child objects where appropriate.
Owner:ARMSTRONG WORLD INDUSTRIES
System and methods for migrating independently executing program into and out of an operating system
This invention generally relates to a methods and system in the field of independent programs operating within an operating system such as Linux and more particularly to computer software embodied in a computer readable medium including: an independent program for running autonomously in a native mode within an associated computer processor; an operating system program for running autonomously within an associated computer processor; a mode switcher process for switching operation from the independent program to the operating system program whereby the independent program functions as an embedded entity of the operating system; and wherein the mode switcher program switches the independent program from the operating system program whereby the independent program runs autonomously in the native mode.
Owner:NETABPECTRUM
Automatic order placing method and system for curtain wall surface skin
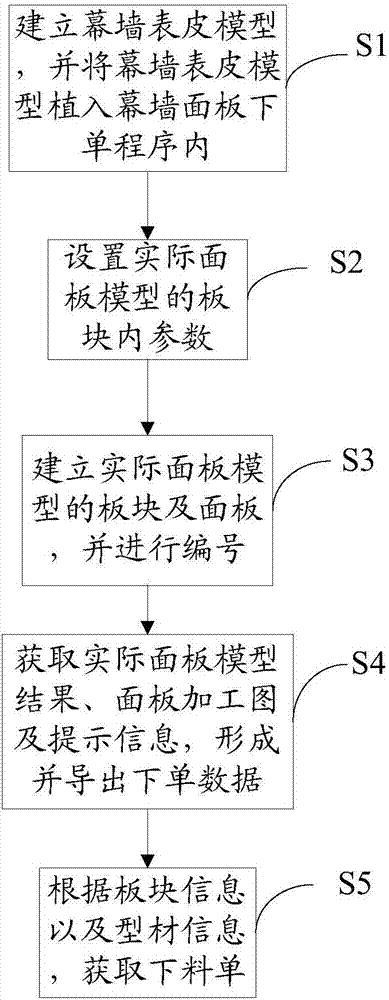
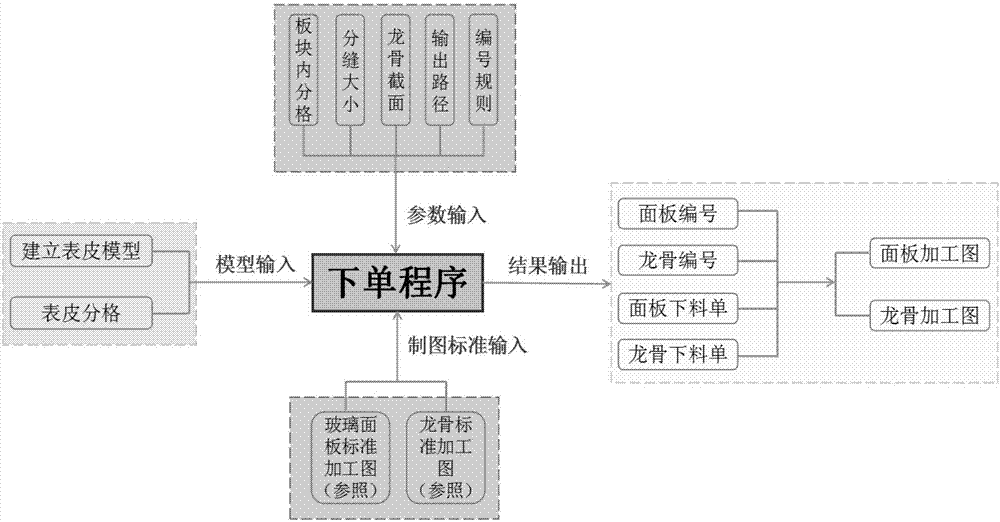
ActiveCN108009144AImprove accuracyEfficiencyNatural language data processingBuying/selling/leasing transactionsStandalone programEngineering
The invention relates to an automatic order placing method and system for a curtain wall surface skin. The method comprises the following steps that: establishing a curtain wall surface skin model, and implanting the curtain wall surface skin model into a curtain wall panel order placing program; setting parameters in a plate of a practical panel model; establishing the plate and the panel of thepractical panel model, and carrying out numbering; obtaining a practical panel model result, a panel working diagram and prompt information, and forming and exporting order placing data; and accordingto the plate information and section bar information, obtaining a baiting list. By use of the method, the model is implanted into the order placing program of the curtain wall panel, a parameterizedway is used for compiling the order placing process of the whole curtain wall panel into an independent program, the independent program is packaged and solidified into an independent order placing program, a port for required input and output parameters is reserved, a user only needs to input the required parameters according to different projects to obtain the relevant order placing data of thepanel, the method is simple in use, order placing is accurate and efficient, the order placing accuracy and efficiency of the panel is improved, and applicability is high.
Owner:珠海市三鑫科技发展有限公司
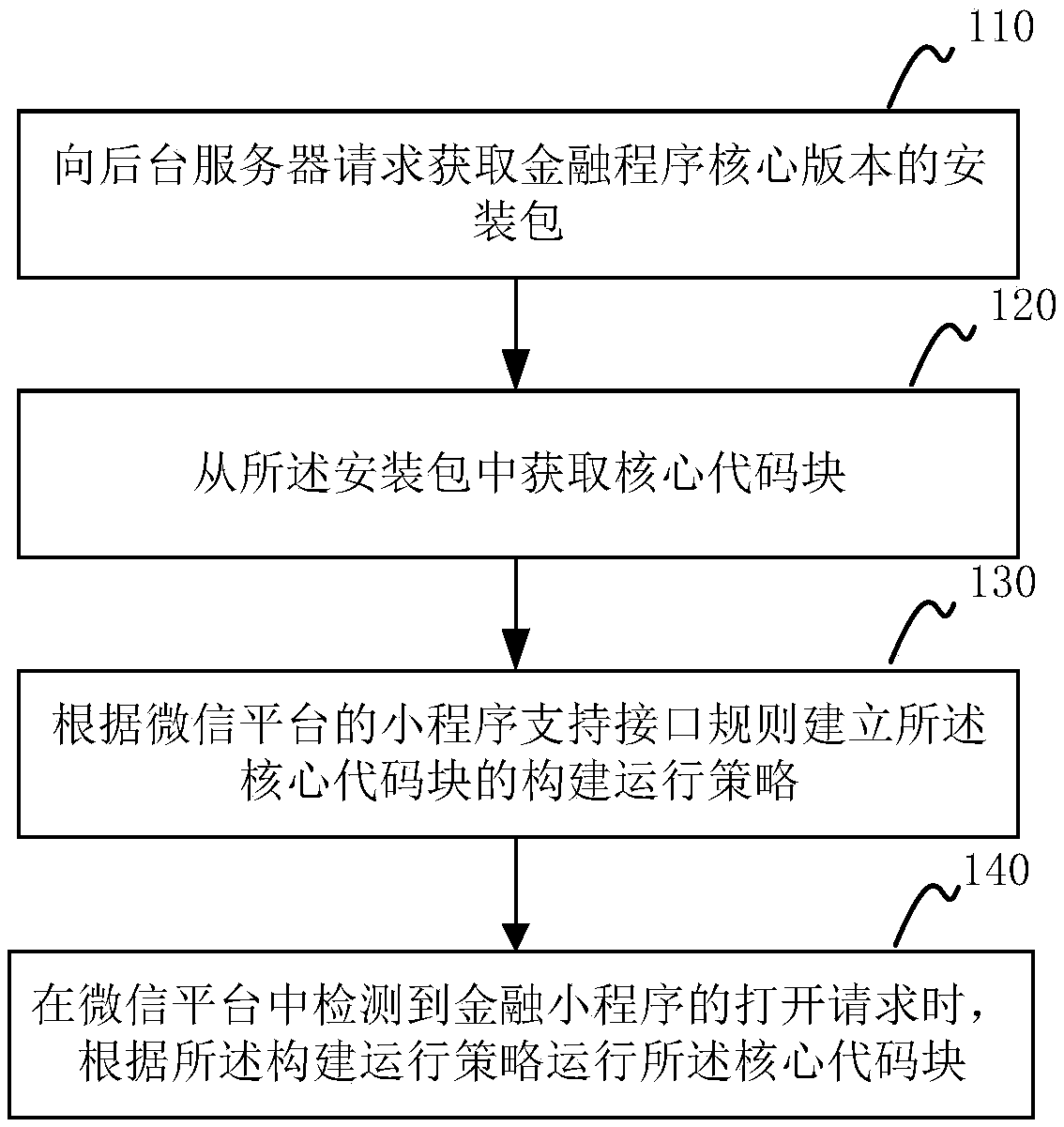
Implementation method and device of financial applet, computer equipment and storage medium
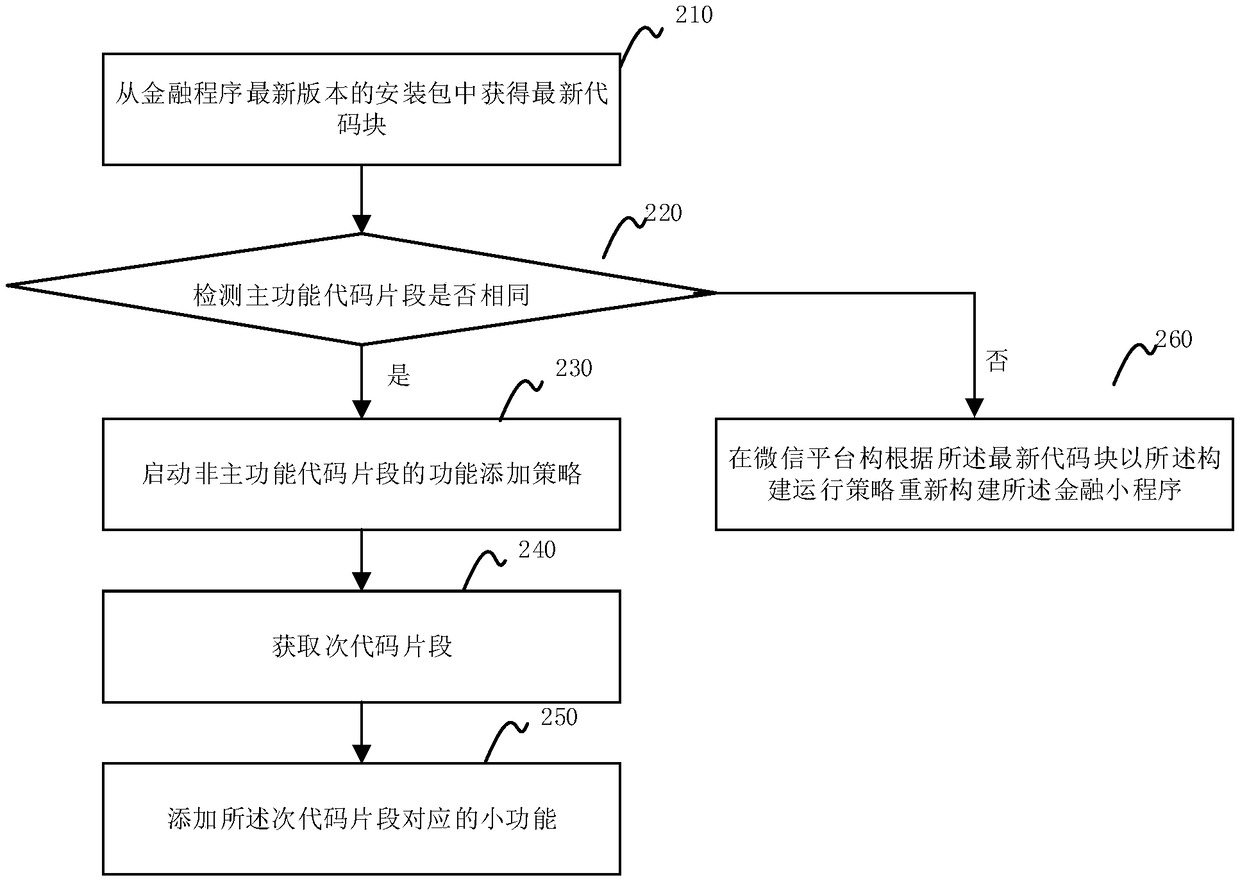
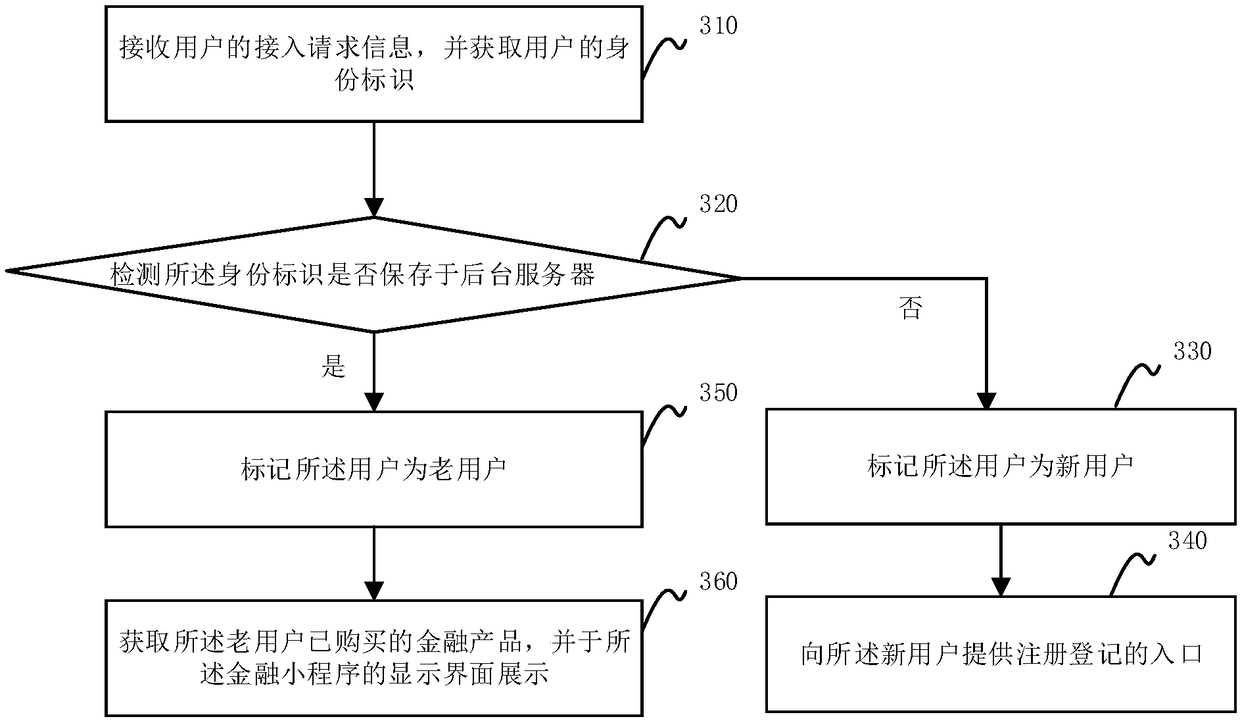
PendingCN109491672AAvoid opening independent financial APPs separatelyImprove retentionFinanceVersion controlCoding blockComputer module
The invention provides a financial applet implementation method and device and a readable storage medium. The method comprises the following steps: requesting a background server to obtain an installation package of a core version of a financial program; obtaining a core code block from the installation package; establishing a construction operation strategy of the core code block according to a widget support interface rule of the WeChat platform; and when an opening request of the financial applet is detected in the WeChat platform, operating the core code block according to the constructionoperation strategy. The beneficial effects of the invention are as follows: the paint has good effects; related functions of a part of financial products of a financial independent program are provided. Loan application; progress query, Credit query; post-loan information query and the like are realized in a mini-program of the WeChat platform; a client can quickly log in through the applet of the WeChat platform and operate related function modules, the situation that the client independently opens an independent financial APP is avoided, the risk that the client is lost due to the fact thatdownloading and opening of the financial APP are too complex is avoided, and the retention rate of the client is greatly increased.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
XEmbed-based interactive map component dynamic embedding method and system
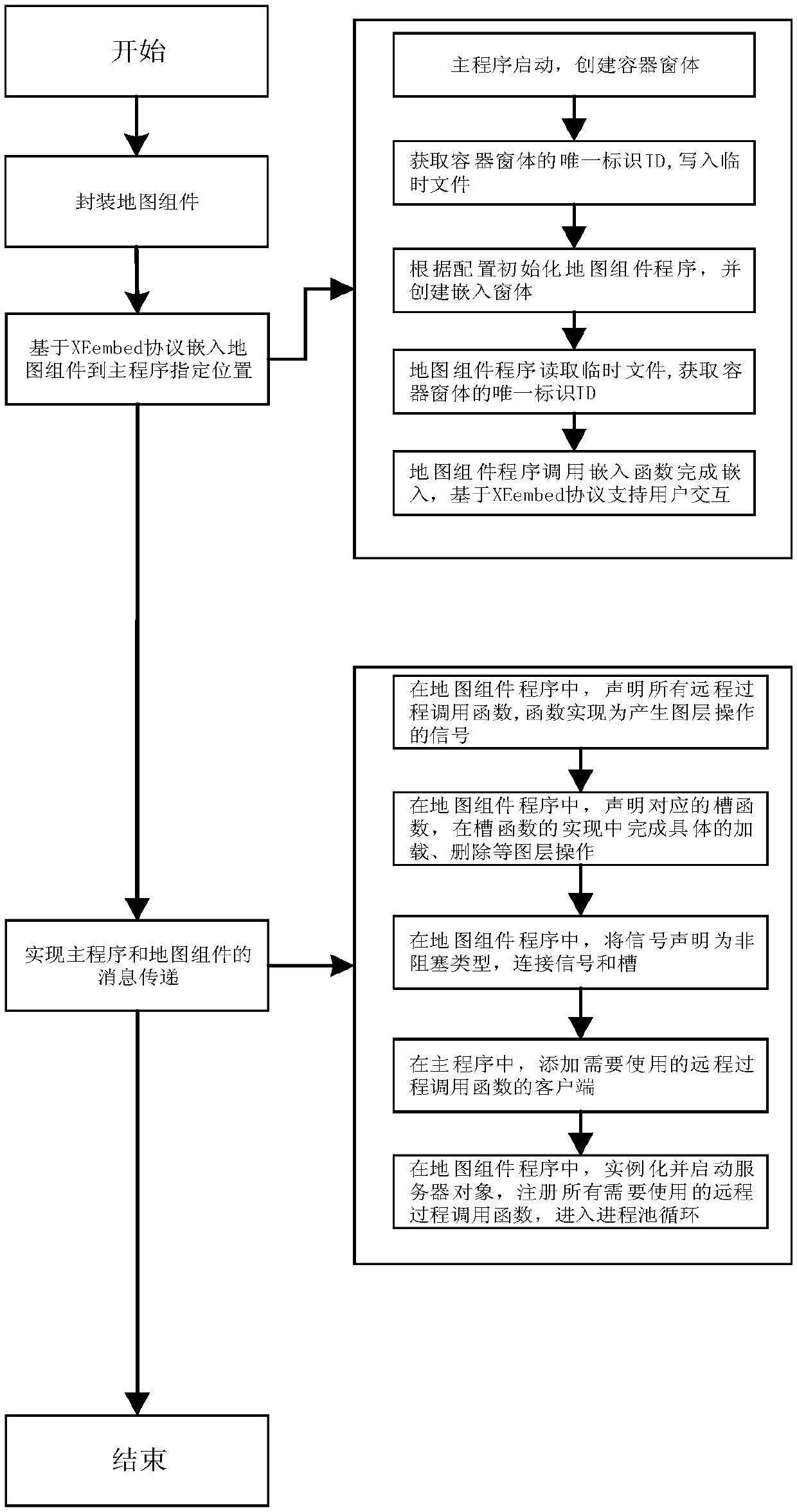
ActiveCN109582308AThe interface style is seamlessImprove interoperabilitySoftware engineeringStandalone programMessage passing
The invention discloses an XEmbed-based interactive map component dynamic embedding method and system. The method comprises the following steps: firstly, pre-packaging a map component to become a configurable function and style independent program capable of being embedded into a window, then embedding the map component window into a main program based on an XEmbed protocol, and realizing basic user interaction operation by using an XEmbed protocol mechanism. designing a set of message transmission mechanism based on remote procedure call to support message transmission between the main program and the map component program, so that complete interaction of the map component is realized. A user can dynamically embed a map component in an existing application program of the user, seamlesslydisplay the map component at any specified position in a program interface, operate the map component and call related functions. The method is easy to implement, only configuration modification is needed, and extra programming work and professional geographic information system knowledge are not needed. And a simple, quick and novel method is provided for the user to realize the interactive map function in scientific research.
Owner:CHINA CENT FOR RESOURCES SATELLITE DATA & APPL
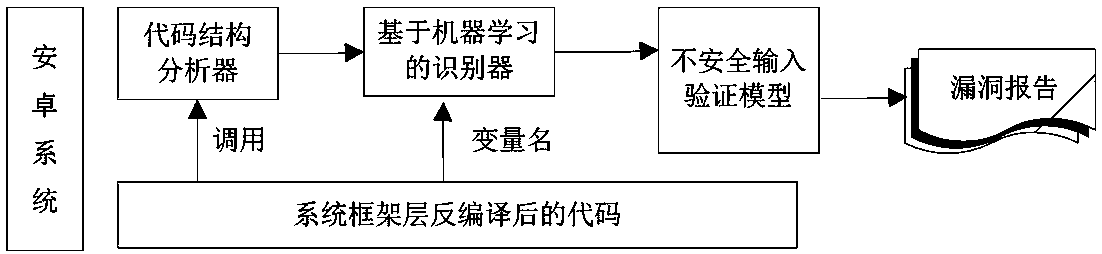
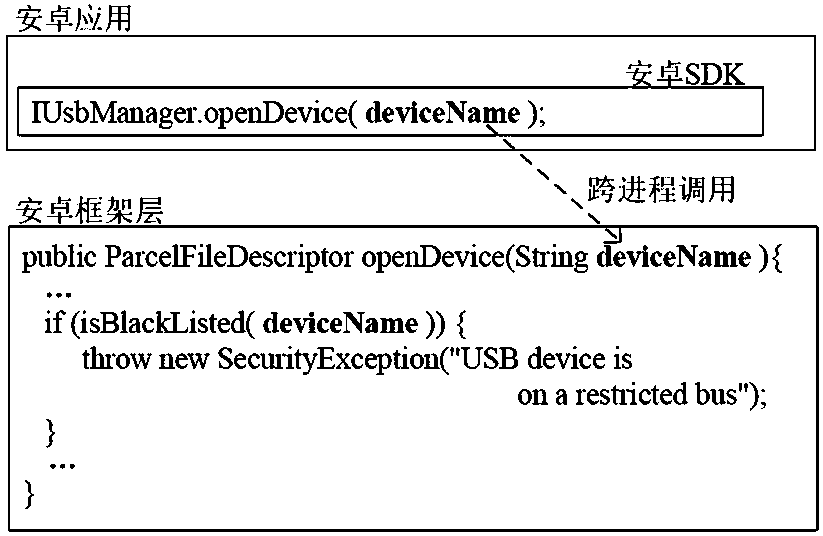
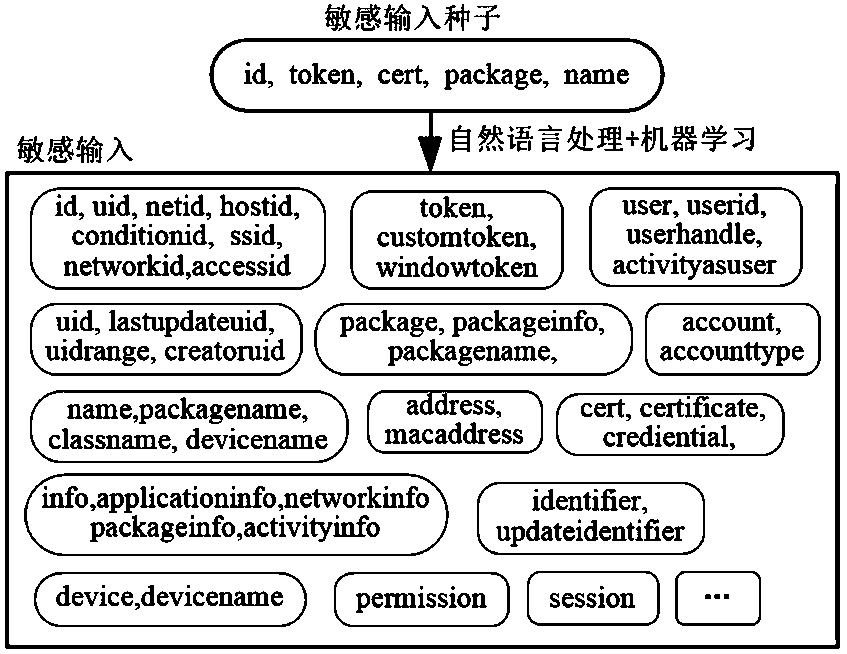
A method for validate and identifying unsafe sensitive input in Android system
The invention belongs to the technical field of program security analysis vulnerability mining, in particular to an unsafe sensitive input verification identification method in an Android system. Themethod comprises the following steps: input validation identification, firstly, extracting interrupt branch in program code, analyzing code structure characteristics, finding out independent program branch containing interrupt instruction, and judging whether current program execution includes the intention of checking input; sensitive input validation identification, using natural language processing to cluster a large number of input parameters based on semantics, and then using machine learning to infer other unknown sensitive parameters by specifying a few known sensitive parameters; Finally, loophole identification, by checking whether these input validation with sensitive parameters meet the security rules to determine whether it is unsafe input validation. Through the identificationof this kind of input verification, we can determine the system-level security vulnerabilities, which is of great significance to enhance the security of mobile systems and prevent system-level attacks.
Owner:FUDAN UNIV
Method and apparatus for performing distributed processing of program code
InactiveUS7100017B2Program synchronisationMemory adressing/allocation/relocationExternal storageStandalone program
A processor having a limited amount of local memory for storing code and / or data utilizes a program stored in external memory. The program stored in external memory is configured into blocks which can be loaded individually into the local memory for execution. Queuing the individual blocks of code allows the program to be executed by the processor and also facilitates loading of the subsequent code to be executed. A semaphore system can be utilized to indicate which blocks of local memory are available / unavailable. The system can support the interaction of multiple independent programs in external memory.
Owner:TAMIRAS PER PTE LTD LLC
Electronic device with programs capable of being updated in segmented manner
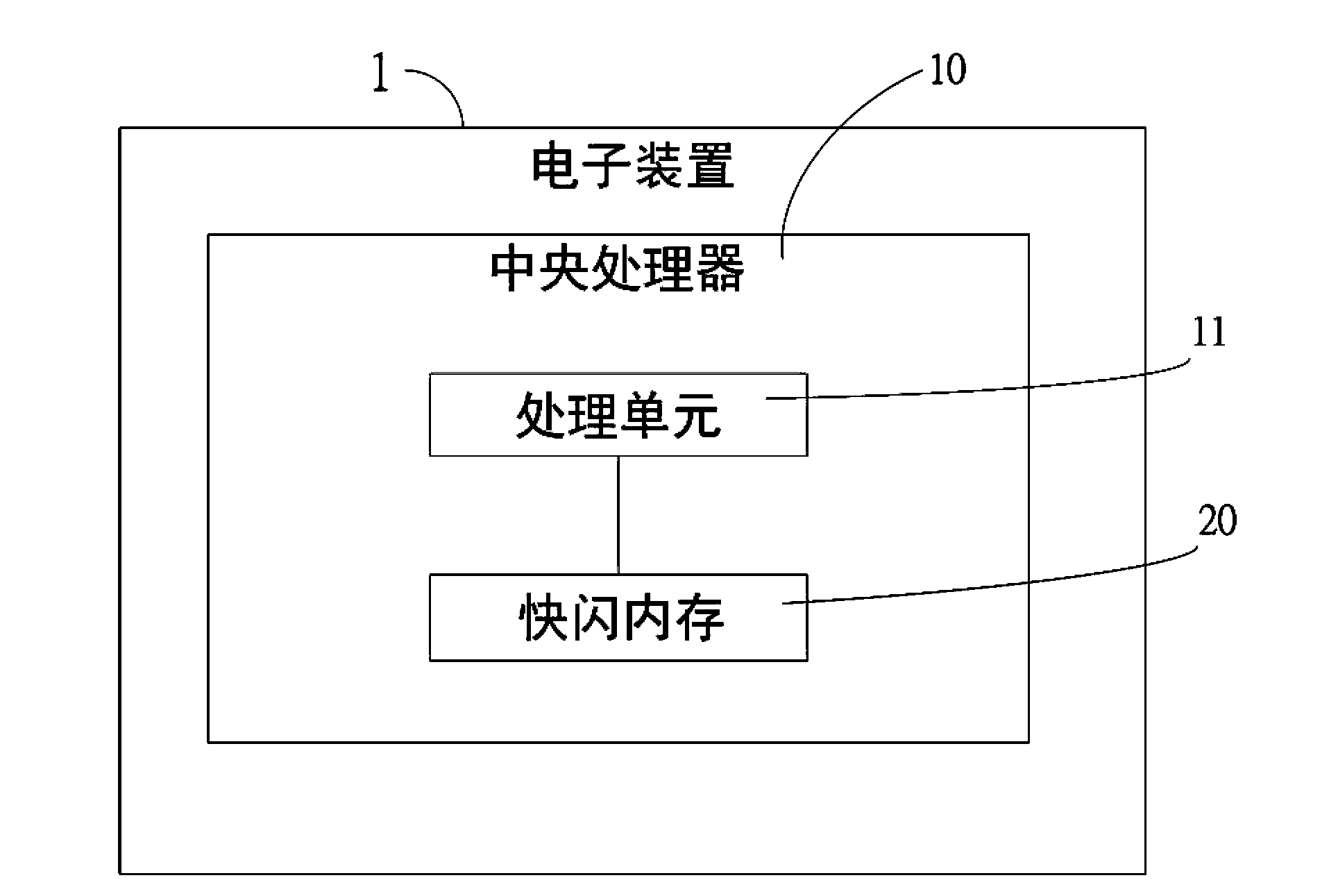
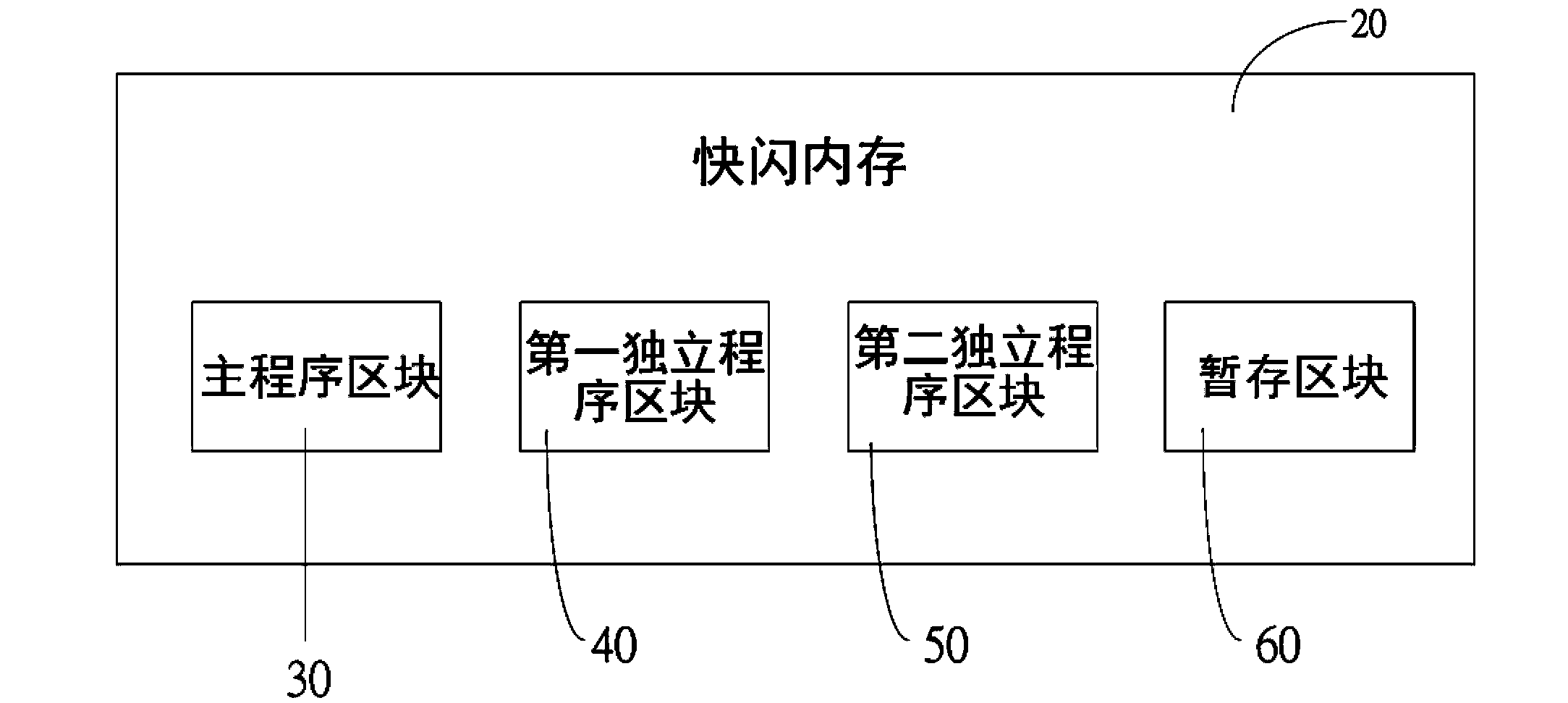
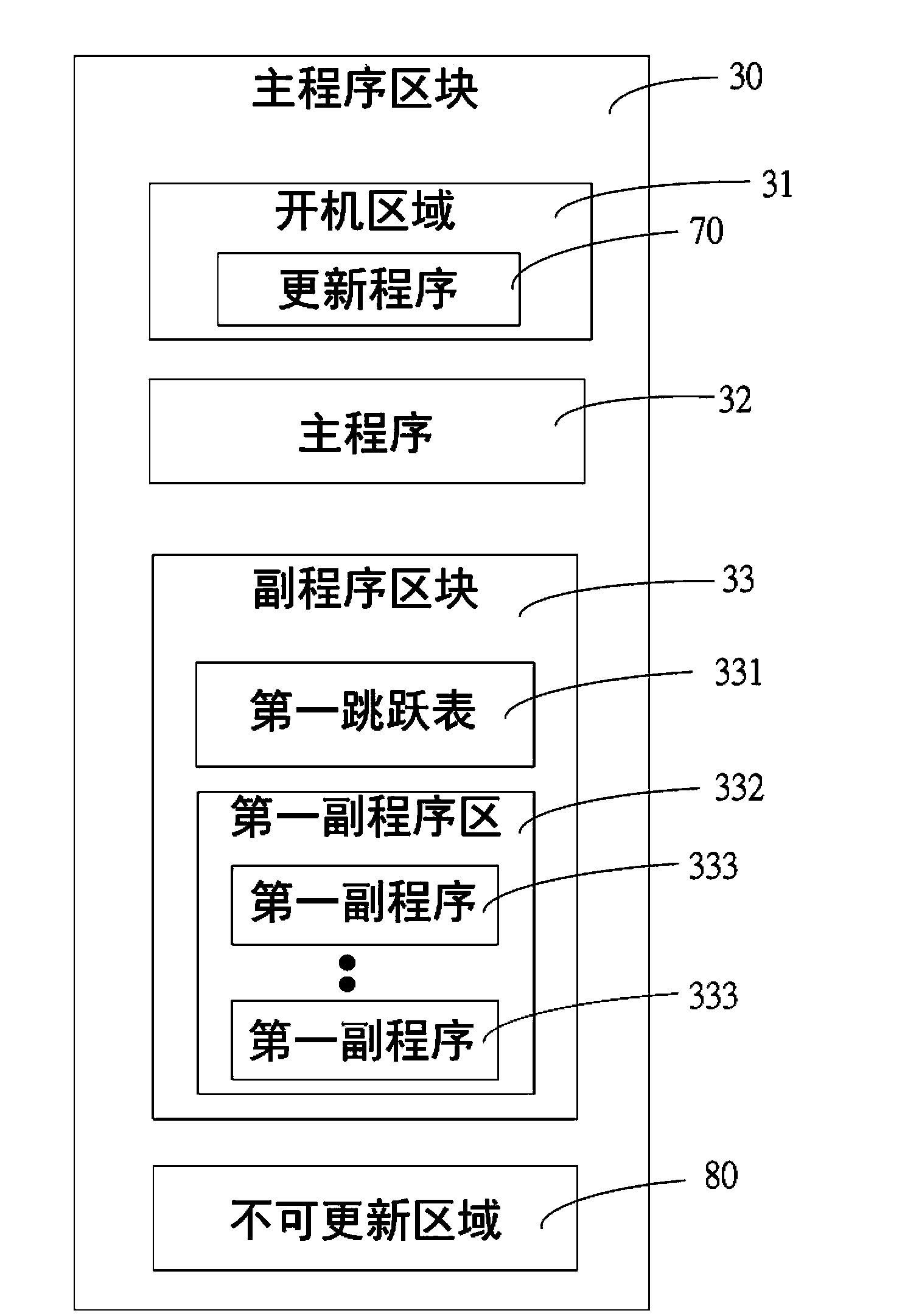
ActiveCN103823688AGuaranteed normal operationEasy to updateProgram loading/initiatingSkip listStandalone program
The invention discloses an electronic device with programs capable of being updated in a segmented manner. The electronic device comprises a processing unit and a central processing unit with a flash memory. The flash memory comprises a main program bank, a plurality of independent program banks and a temporary storage bank, the main program bank comprises a main program bank and an auxiliary program bank, and the auxiliary program bank comprises a first skip list and a first auxiliary program area. A main program can be executed in the main program bank by the processing unit, and the first skip list can be called to be connected with the first auxiliary program area by the main program bank. The various independent program banks respectively comprise second skip lists and second auxiliary program areas. The second skip lists can be called to be connected to the second auxiliary program areas in the independent program banks by the processing unit. The temporary storage bank is used for storing program codes downloaded from far ends, and the program codes can be updated into at least one of the independent program banks or the main program bank by the processing unit.
Owner:TAIWAN SECOM CO LTD
Method and system for site configurable error reporting
Embodiments of the present invention relate generally to error reporting methods and systems. An error reporting application may be configured to be a stand-alone program, embedded within another application, or added as a plug-in application. The error reporting application may also be configured to provide a mechanism for a user to describe a problem with another application and send the problem description to a configurable, user defined location. The error report from the error reporting application may then be processed by an error processing system at the user-defined location.
Owner:RED HAT
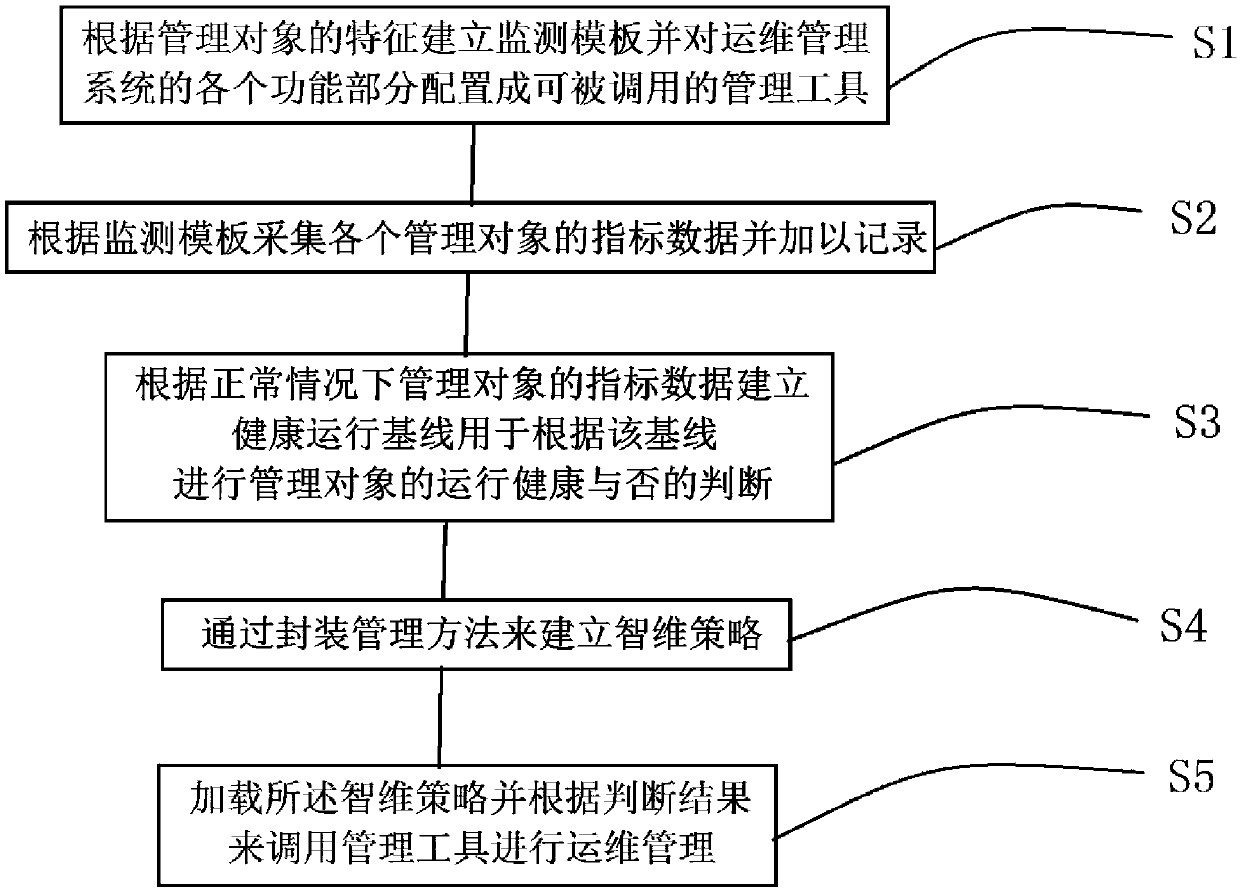
Intelligent operation and maintenance management method and system
InactiveCN105512792AEnhance intelligent processing capabilitiesImprove operation and maintenance management levelResourcesMaintenance strategyManagement object
The invention discloses an intelligent operation and maintenance management method and system. A fixed monitoring product structure is changed into an open-type monitoring product which can be additionally provided with an intelligent maintenance strategy, and the data collection, abnormality judgment and data processing are separated from each other. The intelligent maintenance strategy with the clear boundary is taken as an independent program body, and can be loaded into the management system, thereby continuously improving the intelligent processing capability of the system. The method extracts the health standard of each management object correlated with the time dimension through employing an algorithm, continuously collects the operation data of all monitoring points, compares the operation data with the health standard of this time period, obtains a deviation value of health conditions, carries out the statistics of off-normal conditions, and obtains the operation health degree trend of the system, finds a problem symptom, timely prompts a user, and takes preventive measures. The method can be suitable for different conditions, can be continuously changed according to the actual conditions, and continuously improves the operation and maintenance management level.
Owner:上海北塔软件股份有限公司
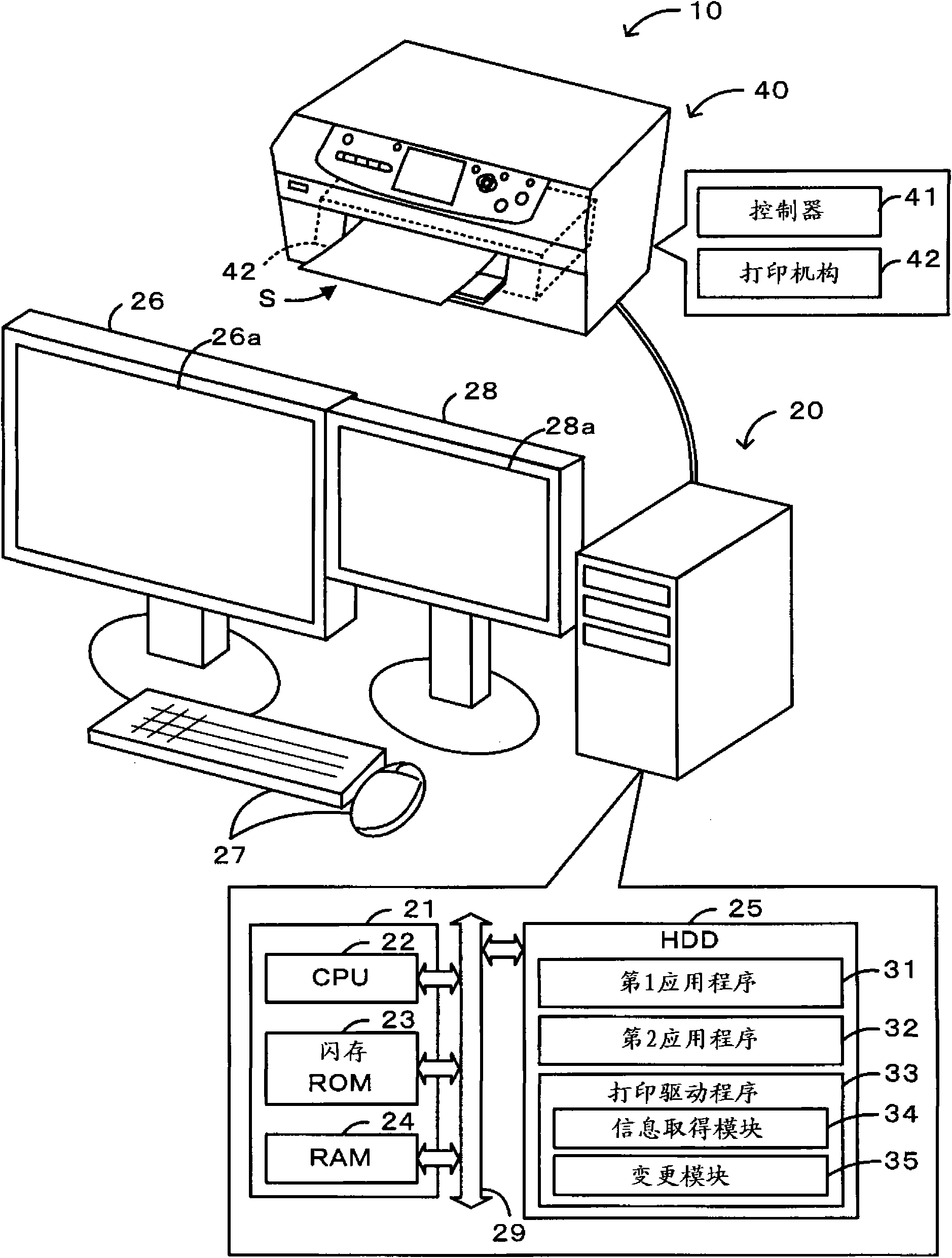
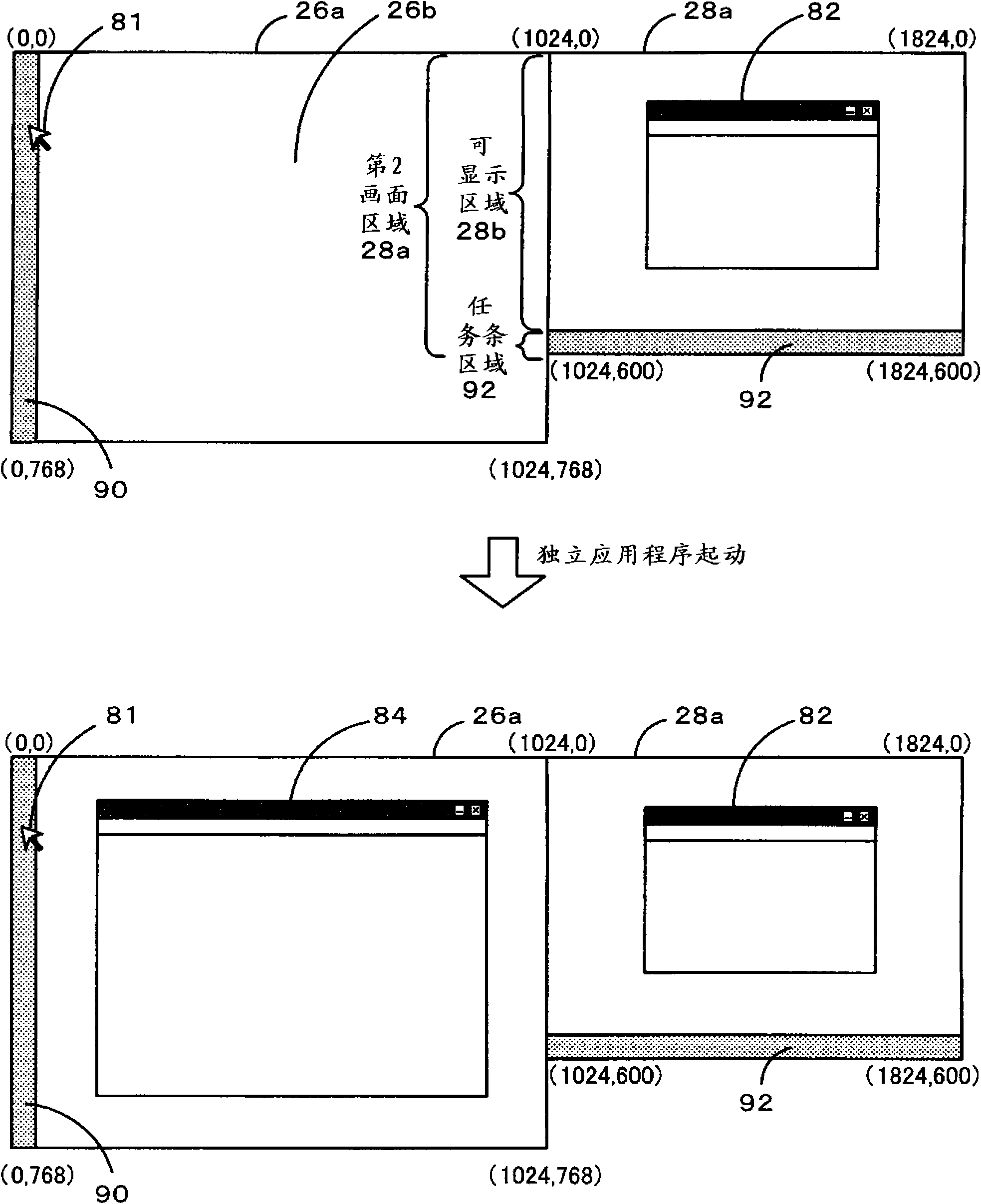
Image processing method, program and device
ActiveCN101788895AEasy to operateCathode-ray tube indicatorsDigital output to display deviceImaging processingDisplay device
The invention relates to an image processing method, program and device, capable of increasing user operability when performing the program using a plurality of display portions. The user PC (20) uses an API of OS to obtain display information that a window of a first application program (31) (independent program) is displayed on which display. The display information is used to judge whether the display capable of displaying the first window of the first application program (31) is different from the display of an initial start object, when the judgment result is that the two displays are same, the movable treatment is not performed; when the judgment result is that the two displays are different, the cooperation window to be displayed moves towards the display displaying the first window at an observable state. Thus the newly-displaying window is displayed on the same display even though it is a cooperated independent program.
Owner:SEIKO EPSON CORP
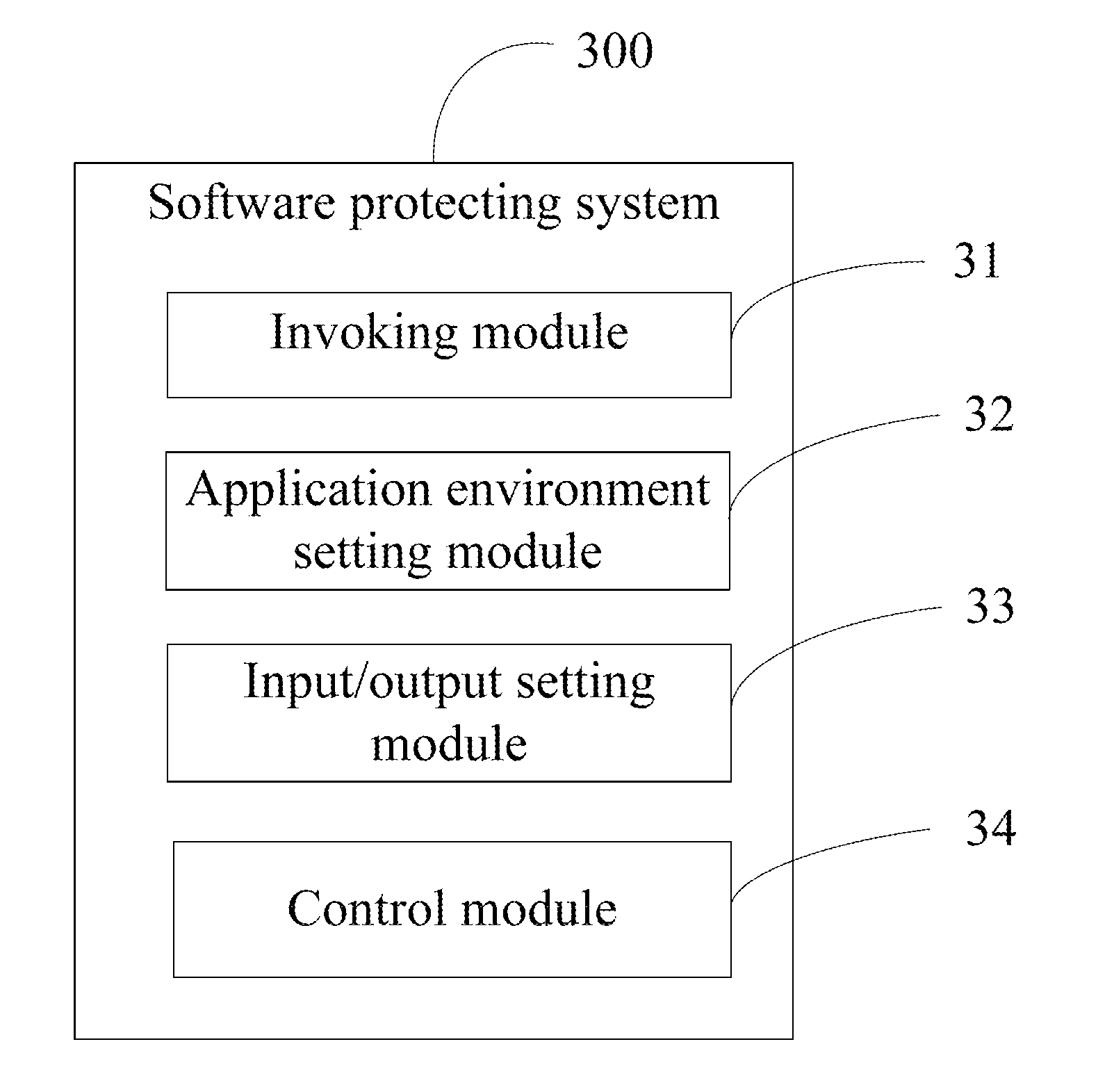
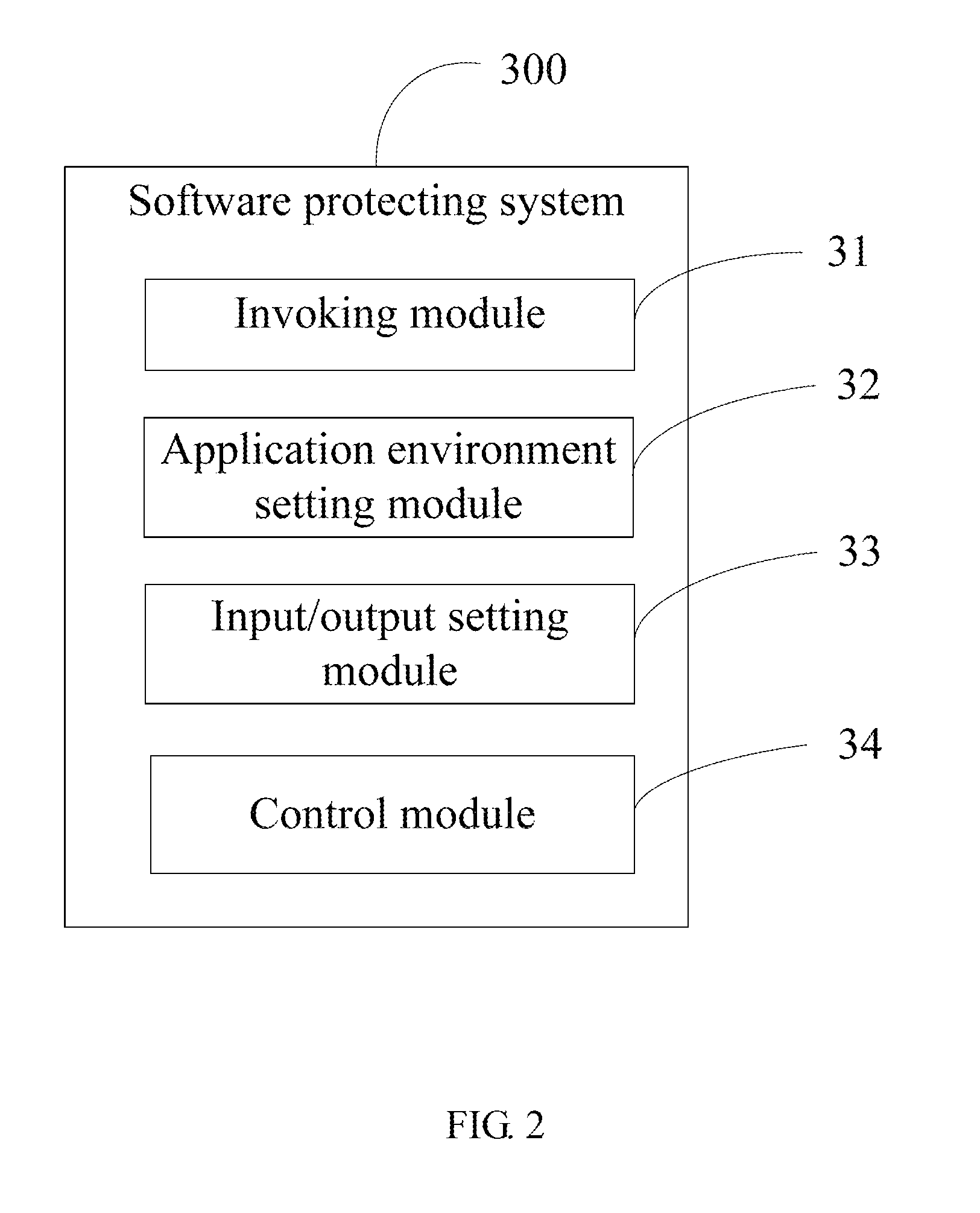
Software protecting system and electronic device using the same
InactiveUS20140351944A1Digital data processing detailsAnalogue secracy/subscription systemsStandalone programInput/output
A software protecting system existing as an independent program in an electronic device protects against misuse of new software to be installed. The protecting system includes an invoking module and an input / output setting module. The invoking module invokes the genuine software in response to user input but the input / output setting module sets input / output functions of the genuine software when the genuine software is run to prevent complete of peripheral functionality during any trial period of use. An electronic device with the software protecting system is also provided.
Owner:FU TAI HUA IND SHENZHEN +1
Standard component library construction and application method, plug-in or system capable of realizing no-component statistics
PendingCN113591291AImplement Aided DesignNatural language data processingDesign optimisation/simulationDesign softwareStandalone program
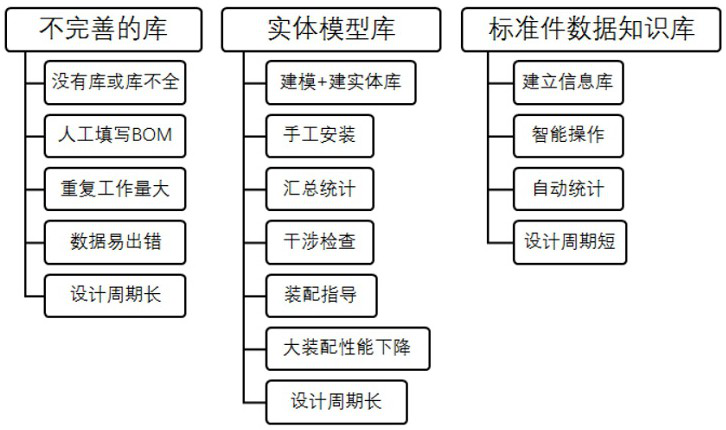
The invention provides a standard component library construction method and application method, a plug-in or a system capable of realizing no-component statistics. The method is specifically characterized in that when a product is subjected to three-dimensional design, in an assembly body model, the complete BOM of the assembly body can be generated without assembling standard parts, and the generated BOM can comprise complete and accurate standard part information actually needed by equipment. By the adoption of the method, an entity standard part model file does not need to be established, only the standard part data knowledge base needs to be constructed and maintained, and the required standard part data information needs to be called when the assembly body model is designed, so that the design process of the product can be completed. The method can be realized by writing an independent program, a plug-in program and an integrated system, can be divided into a management module and a user module, and can be integrated and in data communication with existing design software and management software.
Owner:慧德敏学(北京)科技有限公司
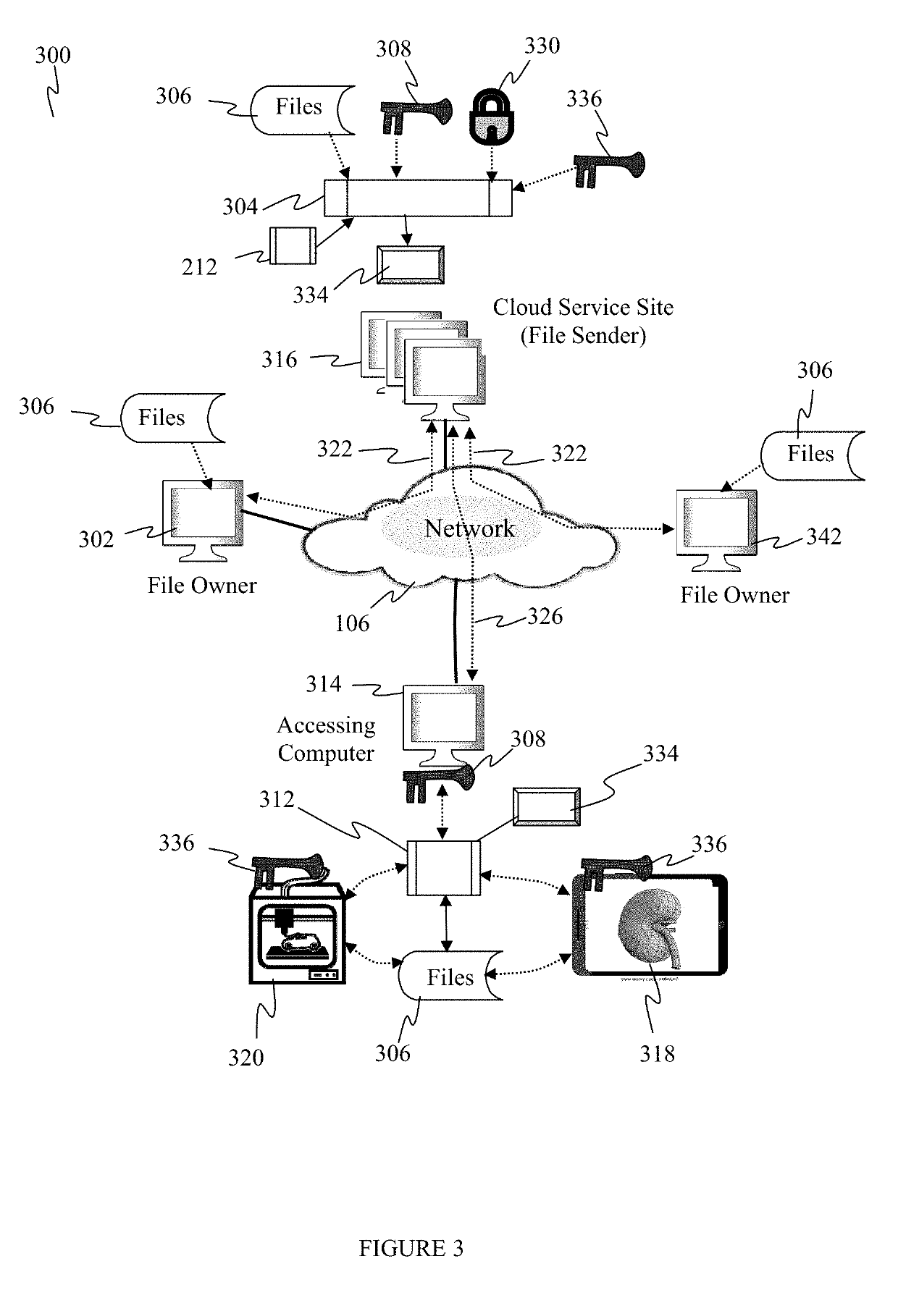
Systems, devices and methods for protecting and exchanging electronic computer files
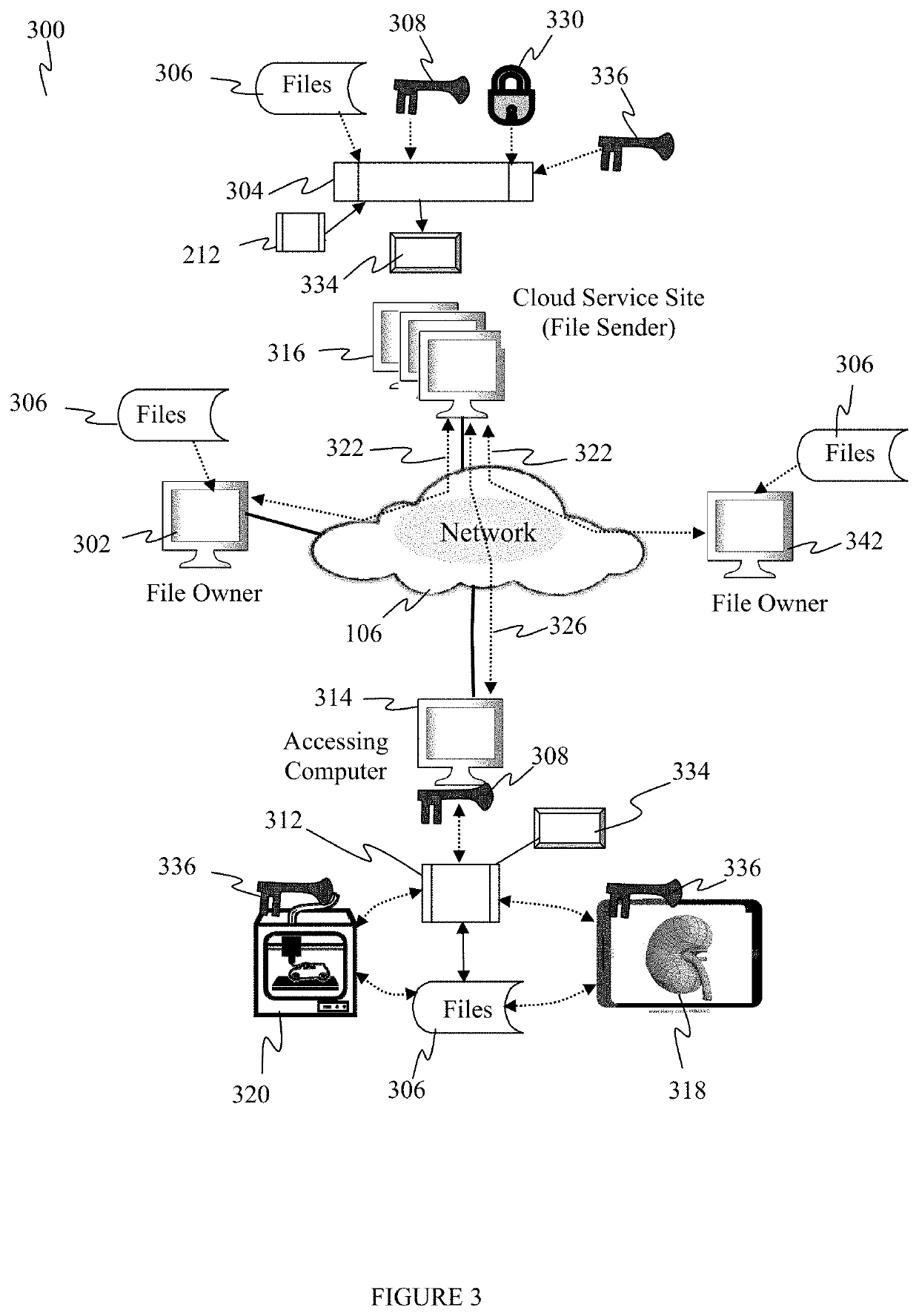
ActiveUS11170116B2Multiple keys/algorithms usageUser identity/authority verificationOperational systemWeb browser
Owner:3D BRIDGE SOLUTIONS INC
Application registration method, device and apparatus, computer readable storage medium and product
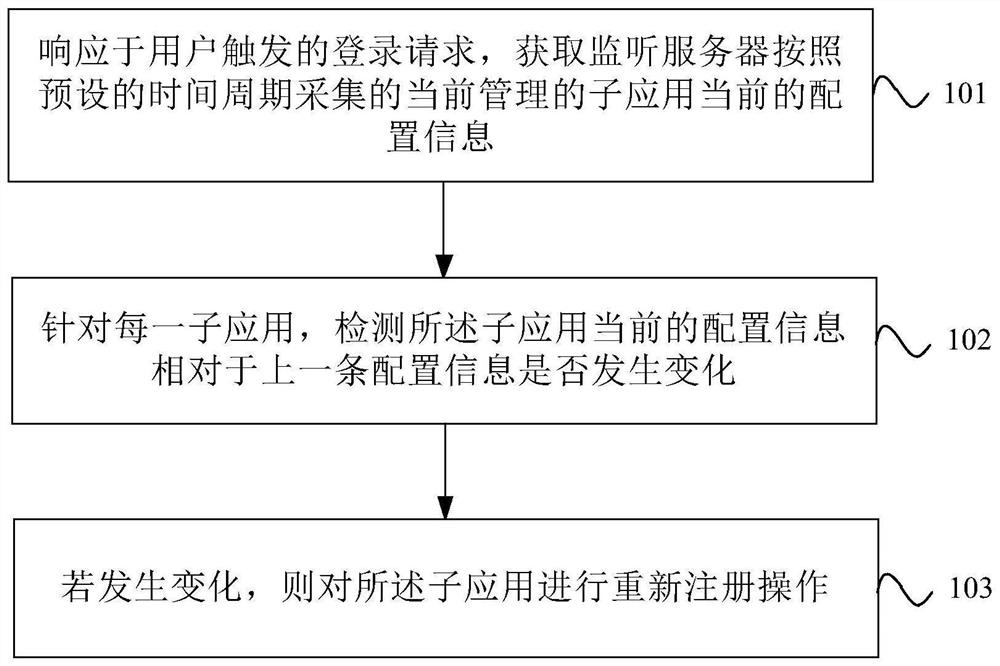
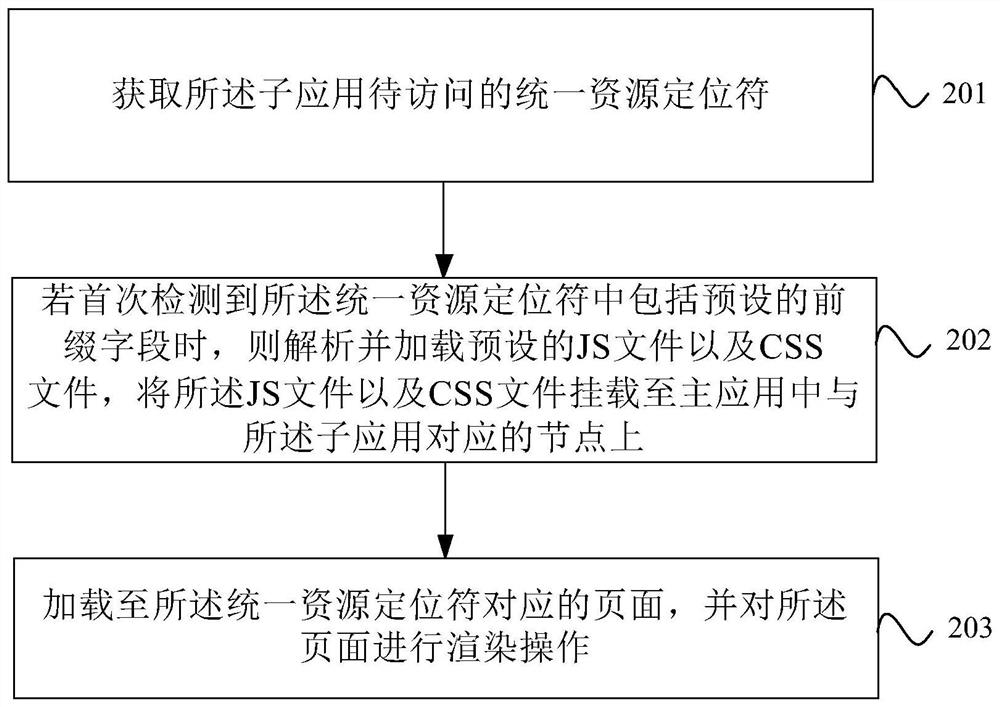
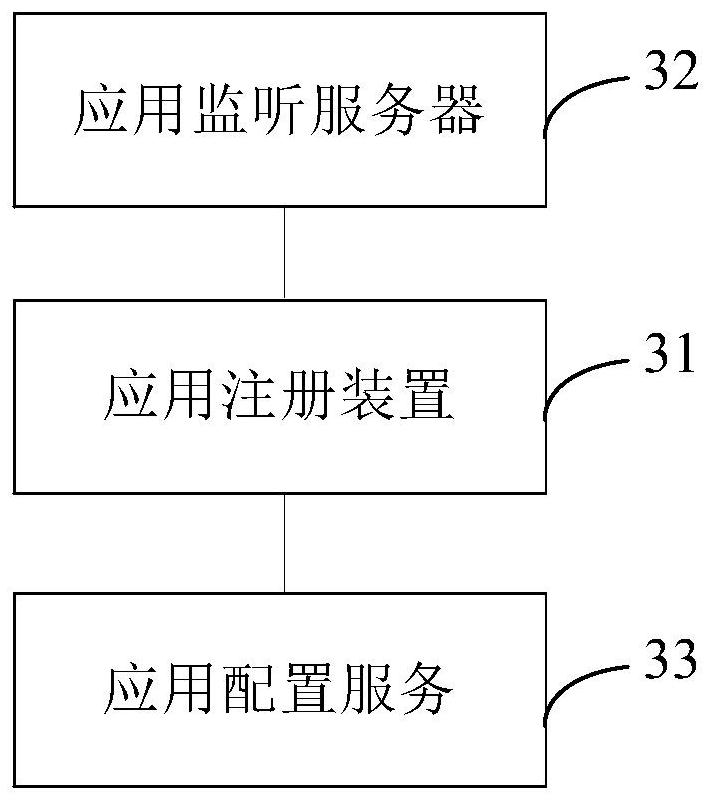
PendingCN113590174AImplement update registration operationAvoid App Performance ImpactVersion controlComputer hardwareStandalone program
The invention provides an application registration method, device and apparatus, a computer readable storage medium and a product, and the method comprises the steps: obtaining current configuration information of a currently managed sub-application collected by a monitoring server according to a preset time period in response to a login request triggered by a user; for each sub-application, detecting whether the current configuration information of the sub-application is changed relative to the previous configuration information; and if so, carrying out re-registration operation on the sub-application. Therefore, updating and registering operation of the sub-application can be dynamically achieved, due to the fact that the sub-application configuration information change detection is put into an independent program of the server side, configuration service information is provided for the client side through the server side service, application logic and data comparison are separated, and the influence of frequent data comparison on application performance is avoided.
Owner:AGRICULTURAL BANK OF CHINA
Software management method and device in cloud data system
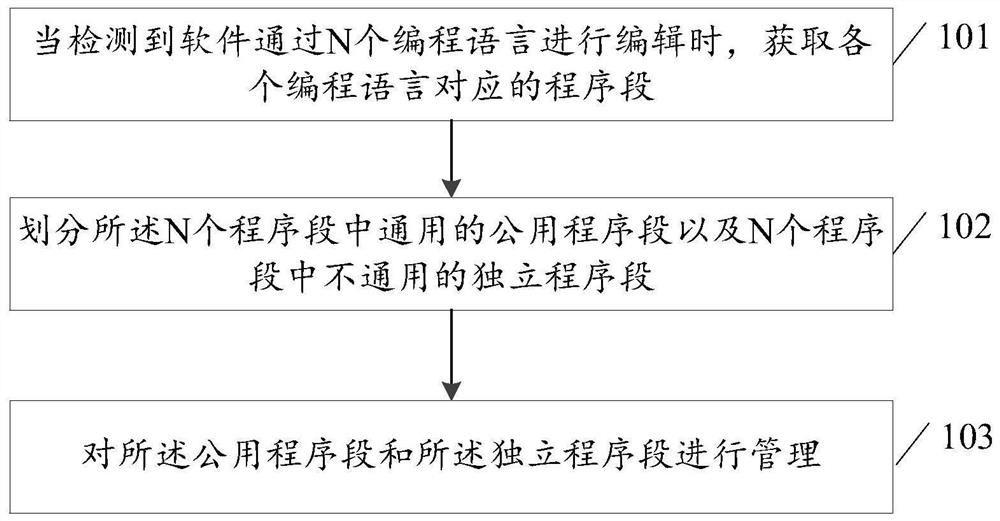
ActiveCN109002287BSolve conflictsAvoid mistakesCode refactoringCreation/generation of source codeProgram segmentSoftware engineering
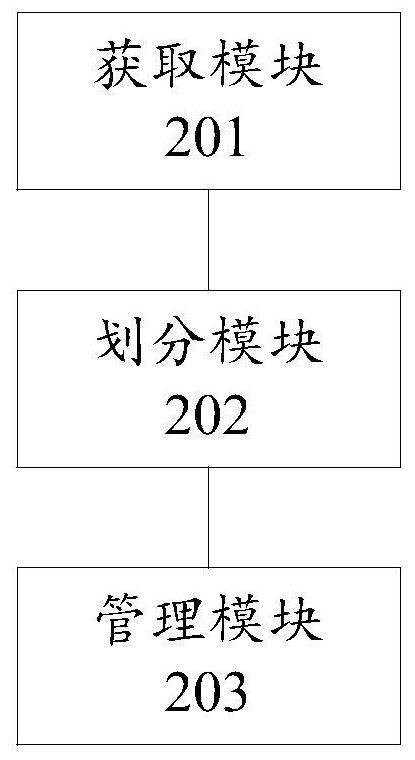
The invention discloses a software management method and device in a cloud data system. The method includes: when it is detected that the software is edited by N programming languages, obtaining program segments corresponding to each programming language, wherein N is an integer greater than or equal to 2; dividing common common program segments among the N program segments and An independent program segment that is not common among the N program segments; managing the common program segment and the independent program segment.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com