Contribution type group key management method depending on sequential exponentiations
A management method and a modulo index technology, applied in the field of network communication security, can solve problems such as large time consumption, reduce the single point failure problem, solve the effect of independence and complete forward secrecy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
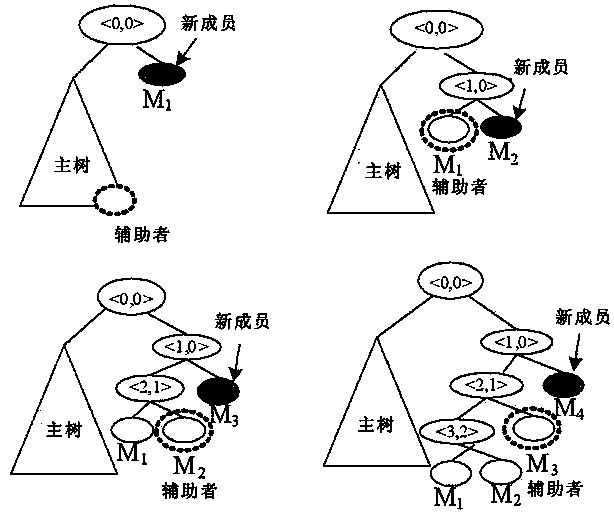
[0066] In this embodiment, the key tree introduced into the join tree is a binary tree, and the logical tree structure is as follows figure 1 . N M and N J Indicates the number of members in the main tree and the joining tree, C J Indicates the capacity to join the tree. Such as figure 1 shown.
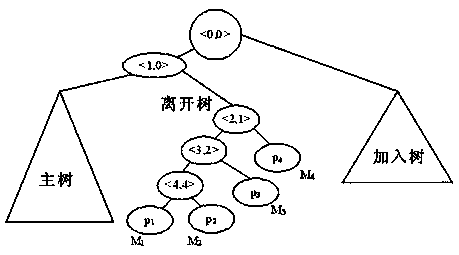
[0067] Such as figure 2 As shown, the leaving tree is introduced, and the members to be leaving are moved to the leaving tree, and the overhead is reduced by introducing the leaving tree. The leaving tree is a weight tree composed of members' leaving probabilities, and the positions of members in the leaving tree are determined according to their leaving probabilities. The greater the probability of leaving, the closer the member's position is to the root of the tree.
[0068] 1. Member Joining Change Process
[0069] When the group members change, in order to ensure communication security, it is necessary to change the key group, and the new members join the following steps...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com