Tag-based process enforcement behavior control method and system
A process control block and behavior technology, applied in the computer field, can solve the problems of destroying system security, single judgment logic, and object association, and achieve the effect of ensuring tight coupling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below through specific embodiments and accompanying drawings.
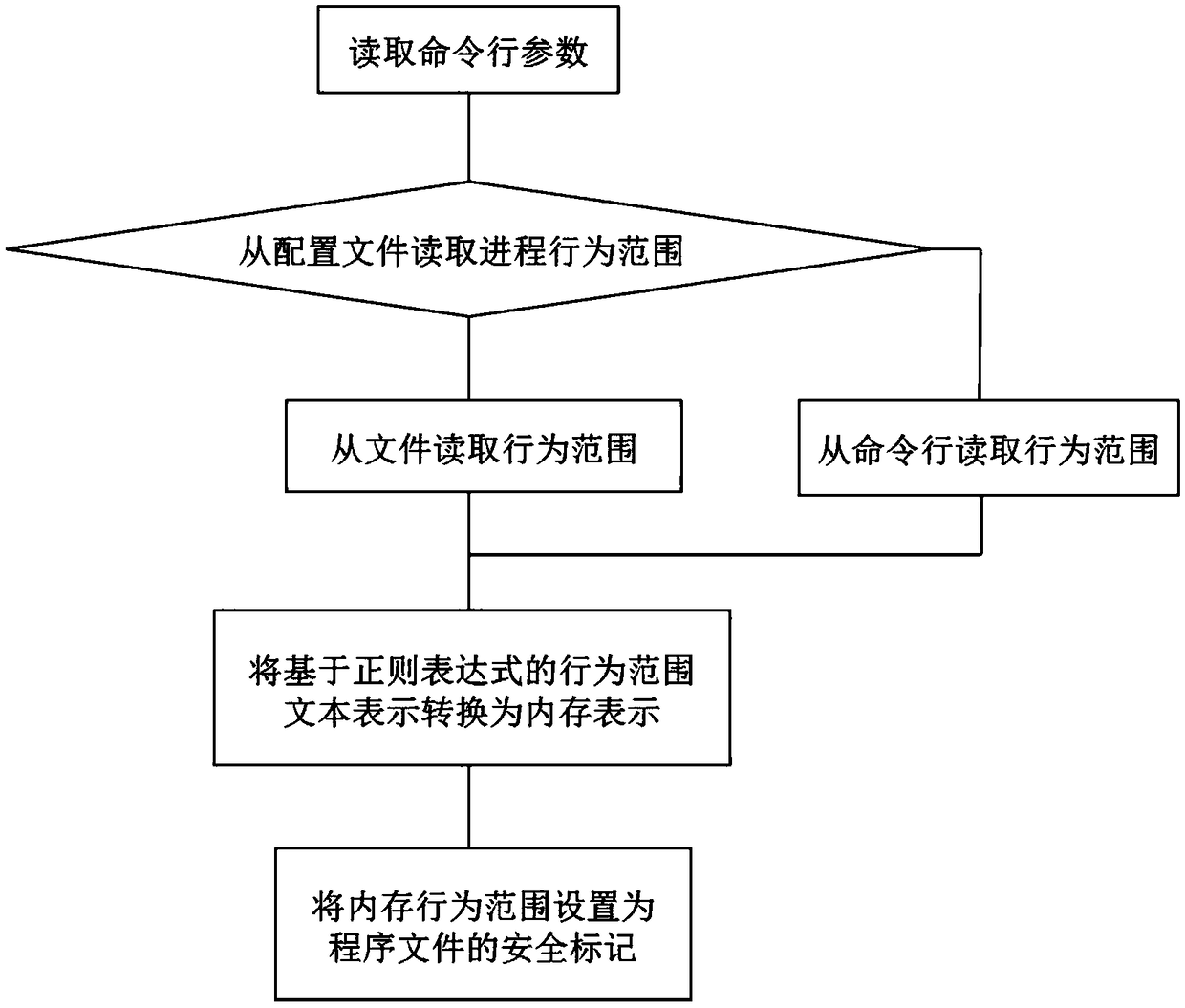
[0067] This embodiment provides a tag-based process enforcement behavior control method, the overall flow of which is:
[0068] 1. Use a specific system tool to set the security flag of the program file, and the security flag is stored in the extended attribute of the program file to realize the binding with the program file.
[0069] 2. When the program with the security flag is running, the kernel of the operating system reads the rule content of the security flag in the extended attribute of the program file. The rule content is converted into a rule linked list, which is stored in the process control block of the newly created process when the program is running.
[0070] 3. When the process needs to execute a new program, match the path of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com