A method for analyzing potential malicious software based on virtualization technology and related devices
A virtualization technology and malware technology, applied in the fields of computer-readable storage media and potential malware analysis devices, can solve problems such as blue screen, inability to analyze, and hidden safety hazards, so as to avoid cracking operations, improve the scope of use, and improve efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
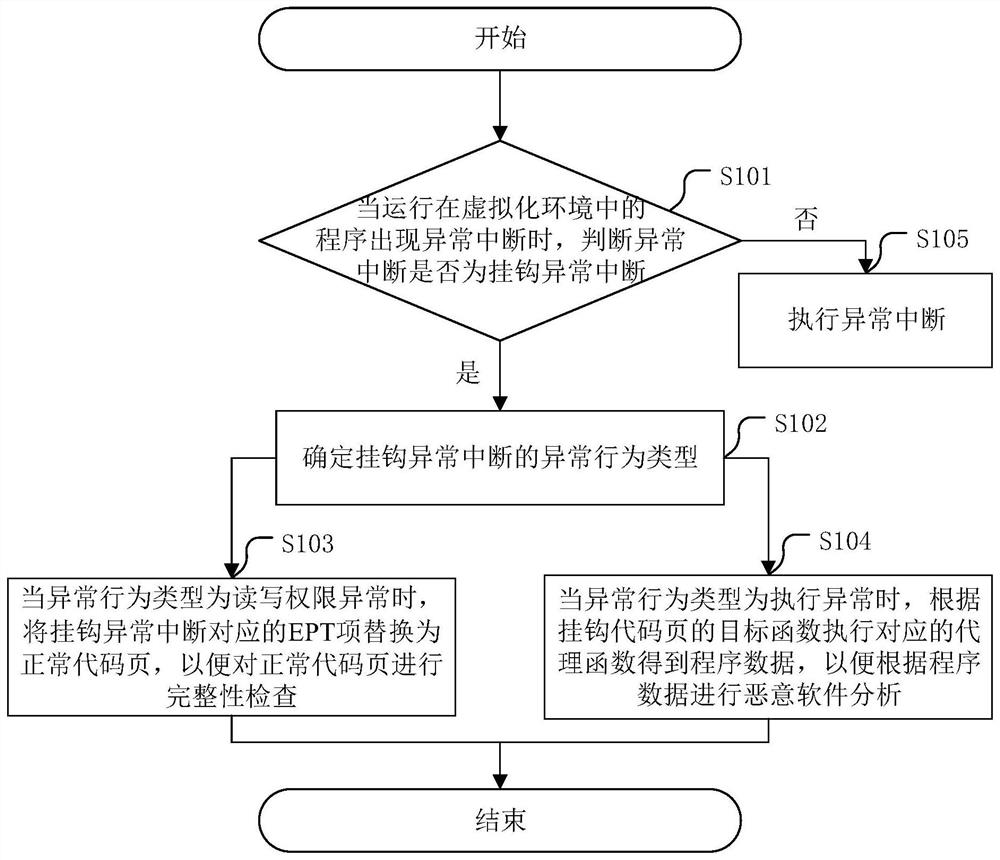
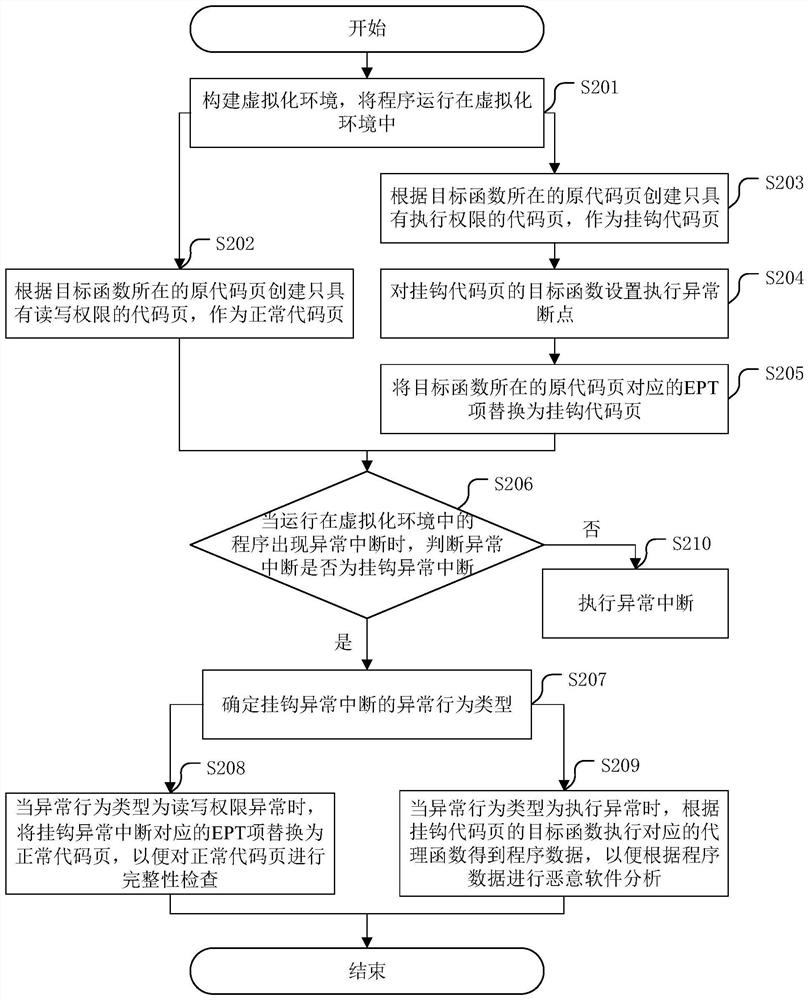
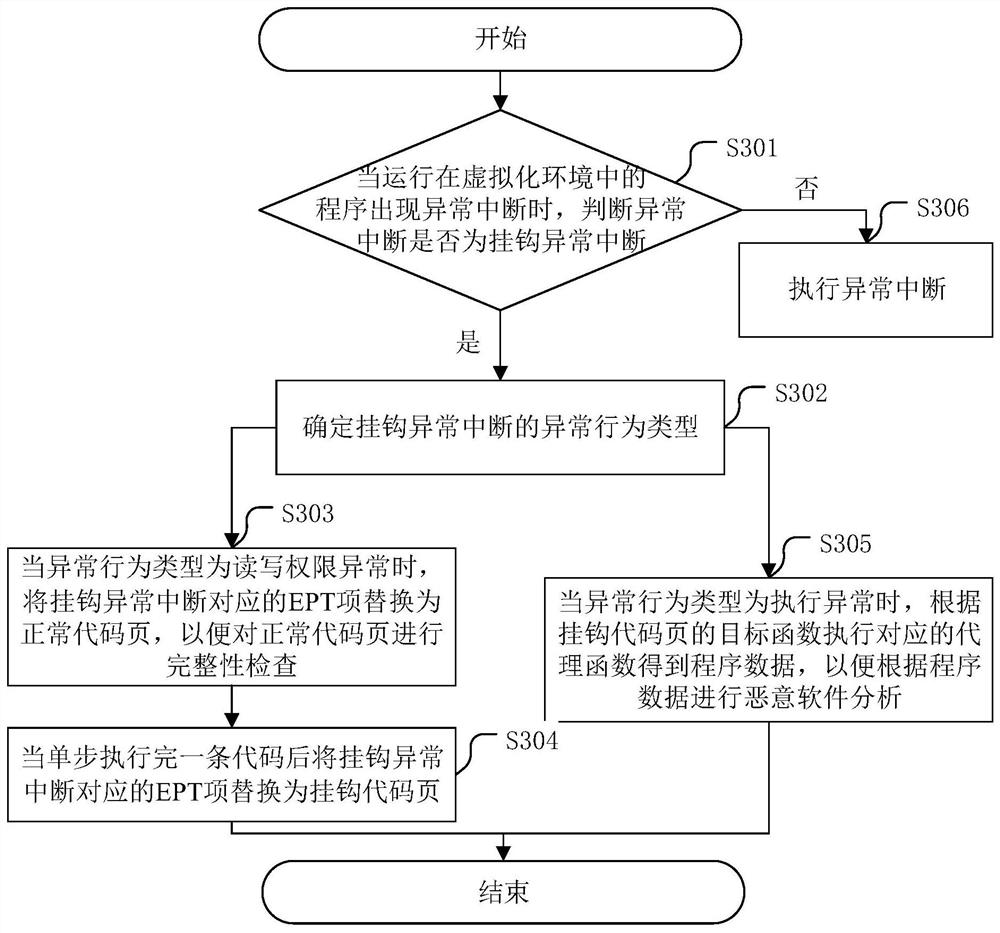
[0045] The core of the present application is to provide a potential malware analysis method based on virtualization technology, a potential malware analysis device, a server, and a computer-readable storage medium, and replace the normal code page with the hook code page by hooking the type of abnormal interruption, so that Through the integrity check, the program data is obtained when the proxy function corresponding to the hooked code page is executed, and malware analysis is realized under the integrity check, which improves the analysis efficiency.
[0046] In order to make the purposes, technical solutions and advantages of the embodiments of the present application clearer, the technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the drawings in the embodiments of the present application. Obviously, the described embodiments It is a part of the embodiments of this application, not all of them...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com