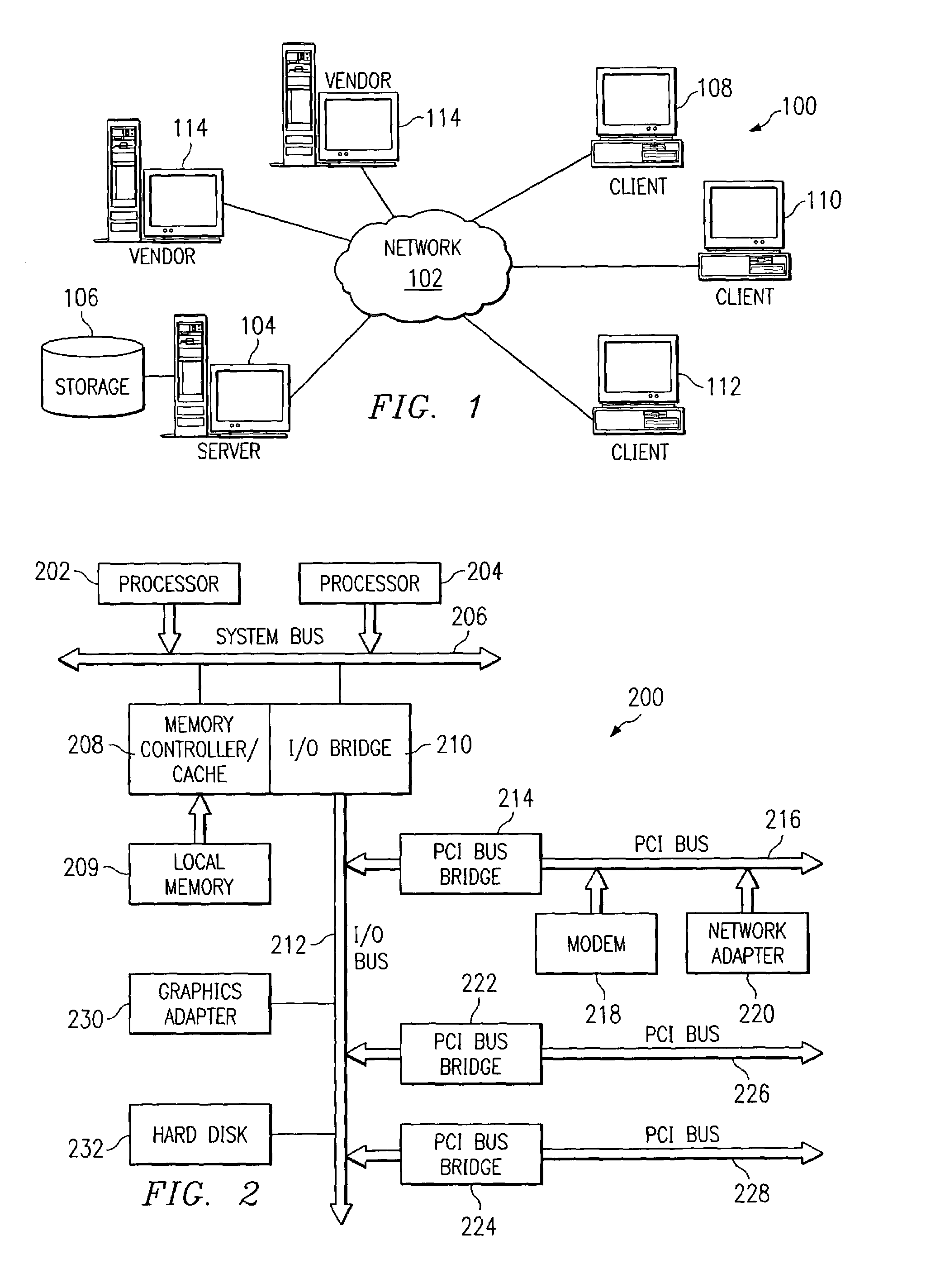
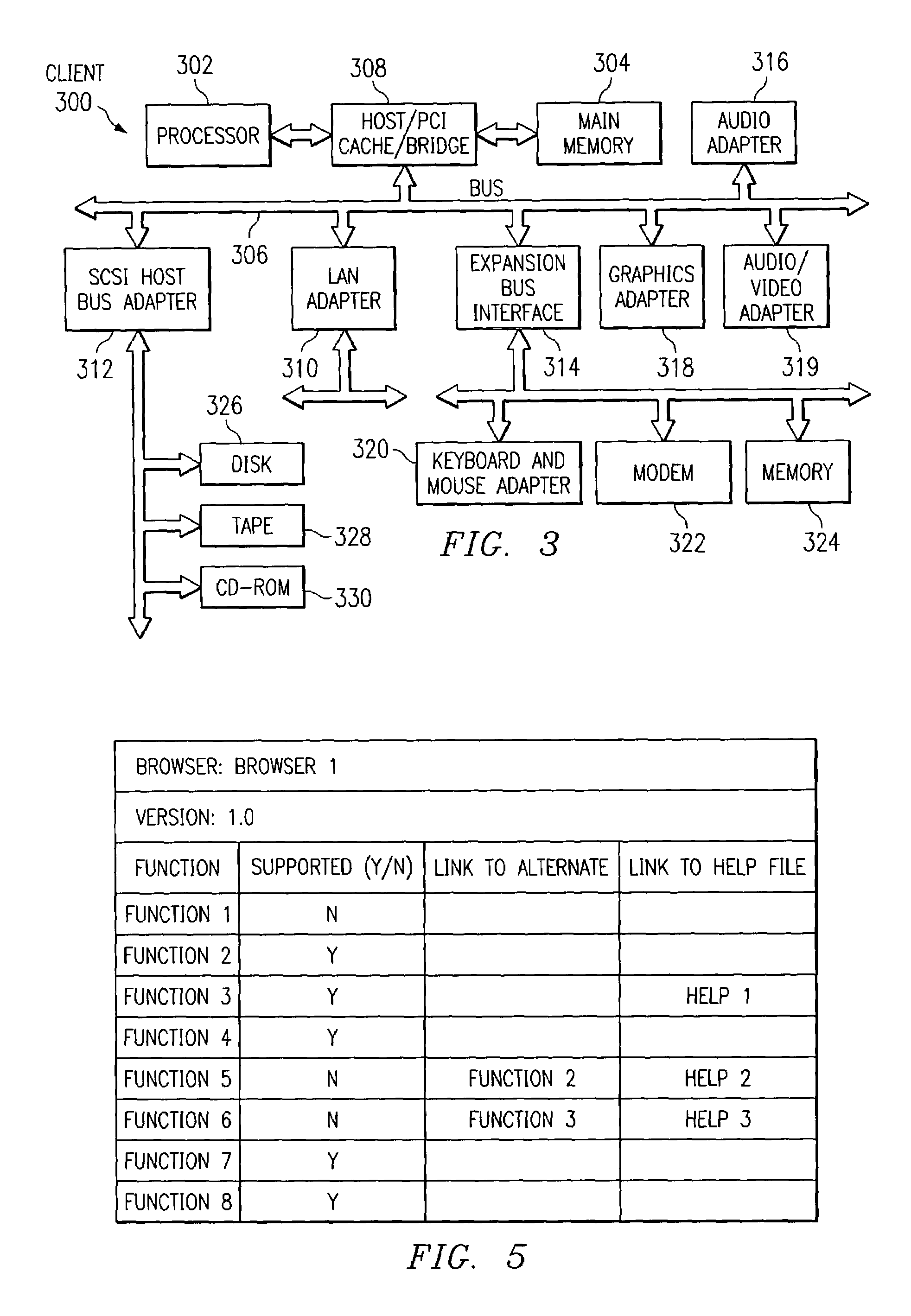
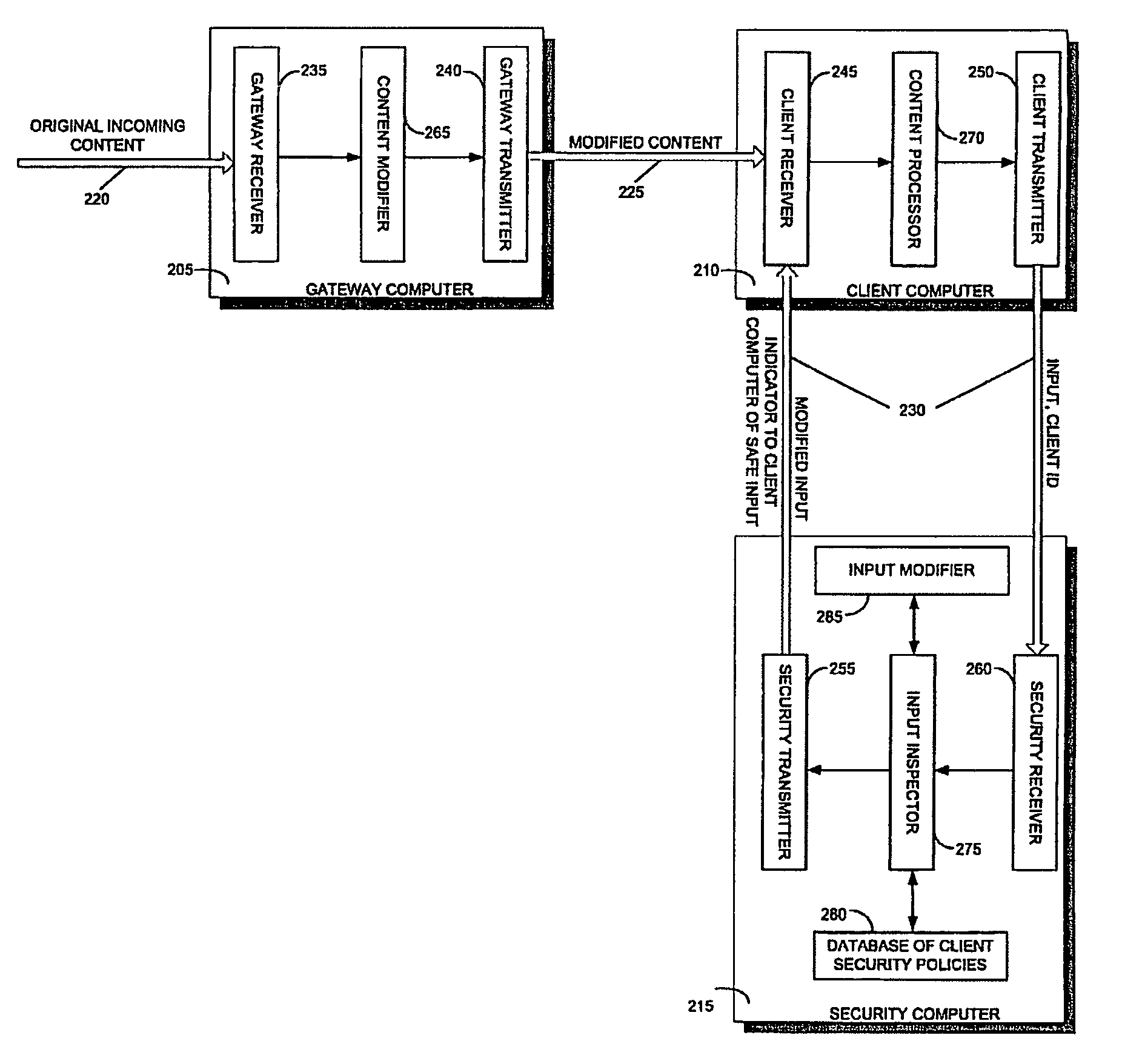
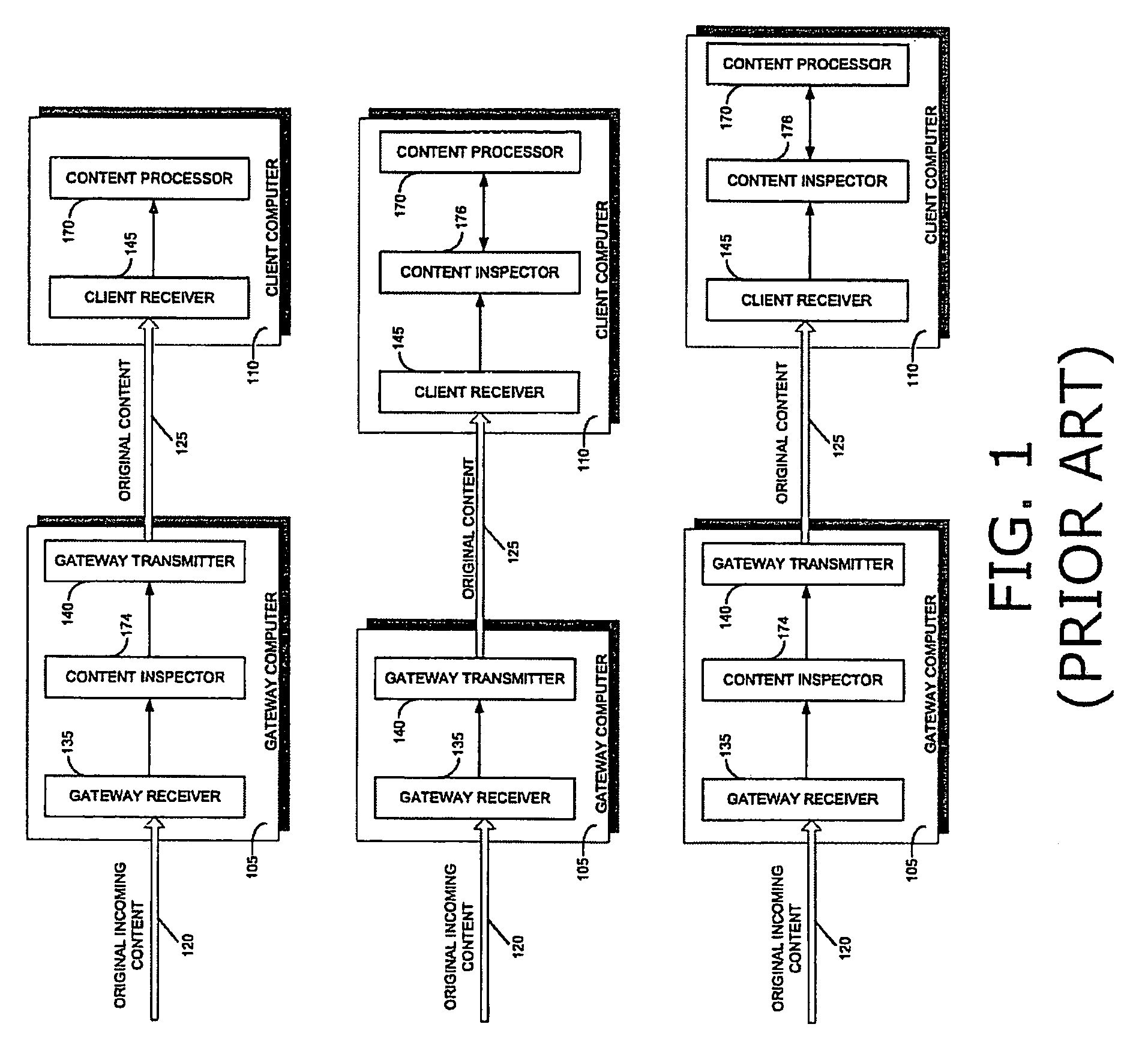
Patents
Literature
37 results about "Surrogate function" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A surrogate is a function that approximates an objective function. The surrogate is useful because it takes little time to evaluate. So, for example, to search for a point that minimizes an objective function, simply evaluate the surrogate on thousands of points, and take the best value as an approximation to the minimizer of the objective function.
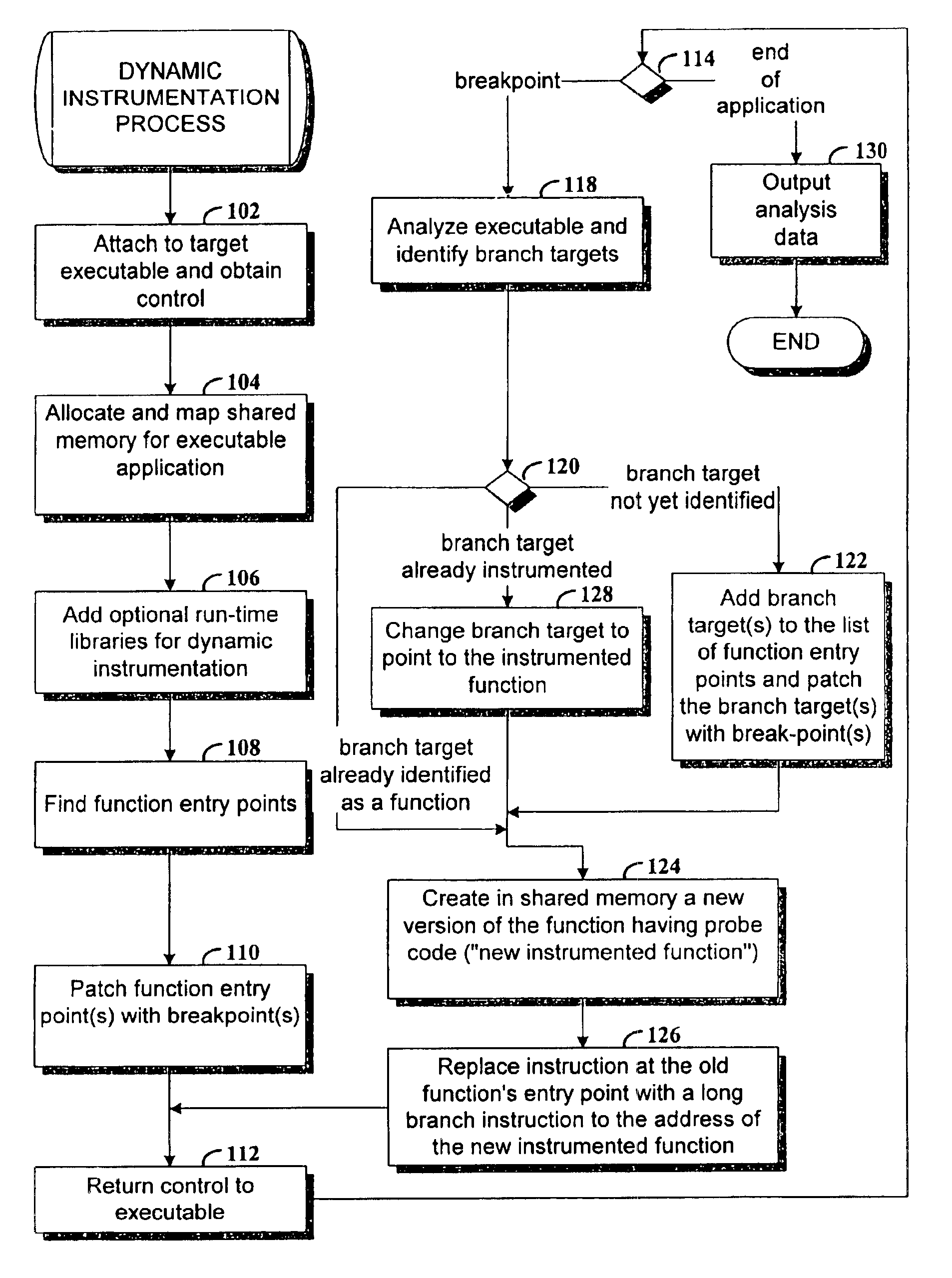
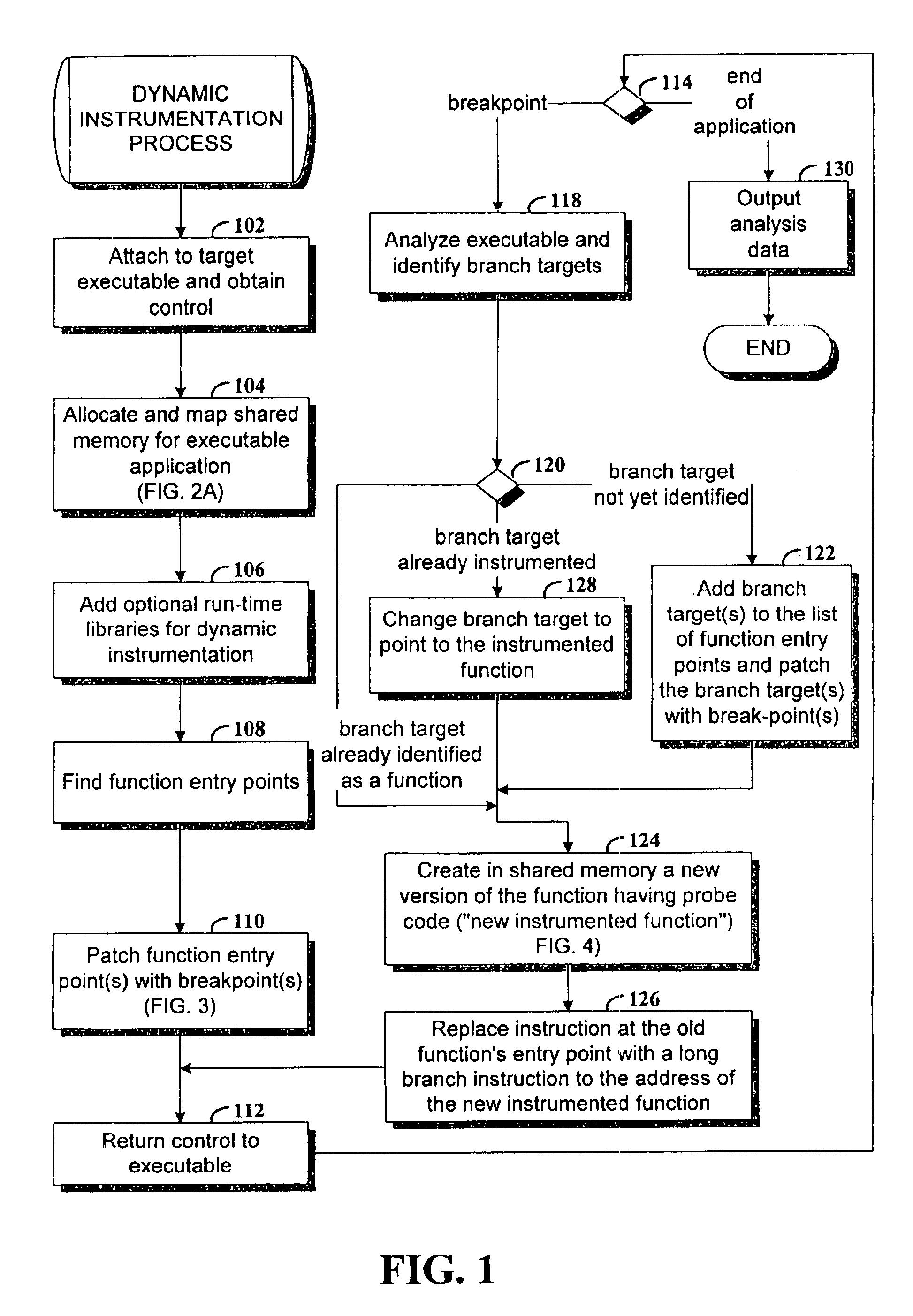
Dynamic instrumentation of an executable program by means of causing a breakpoint at the entry point of a function and providing instrumentation code
InactiveUS6918110B2Software testing/debuggingSpecific program execution arrangementsDynamic instrumentationEntry point
Method and apparatus for dynamic instrumentation of an executable application program. The application program includes a plurality of functions, each function having an entry point and an endpoint. When the application is executed, a shared memory segment is created for an instrumentation program and the application program. Upon initial invocation of the original functions in the application program, corresponding substitute functions are created in the shared memory segment, the substitute versions including instrumentation code. Thereafter, the substitute functions are executed in lieu of the original functions in the application program.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
System, method and software for creating or maintaining local or distributed mapping and transparent persistence of complex data objects and their data relationships
InactiveUS20080189240A1Database management systemsSpecial data processing applicationsSemi automaticProject management
The invention provides computer systems, computer data stores and methods and software for accessing and utilizing data stores. More particularly, the present invention provides systems, methods and software for creating or maintaining local or distributed mapping and optional transparent persistence of data objects, objects for stored procedures, complex data objects, data object graphs and associated data stores. The present invention further provides a computer system and software implemented method for a development mapping workspace for improved project management of mapping and persistence development activities along with a system implemented organization of mapping projects. In another aspect, the invention provides a computer system and software implemented methods for automatically mapping objects to one or more data source with an interface for setting variable stringency for such automatic mapping with an optional interface for editing the resulting system generated mapping, which system and software implemented methods may be collectively referred to as a “magic mapper” system. Further, such systems and software implemented methods are optionally integrated with IDEs, case tools and other third party platform or development environments to provide an extension of functionality or alternative functionality to such IDEs, third party platforms and other development environments, and to optionally provide for improved automatic or semi-automatic logic code generation.
Owner:MULLINS WARD R +1
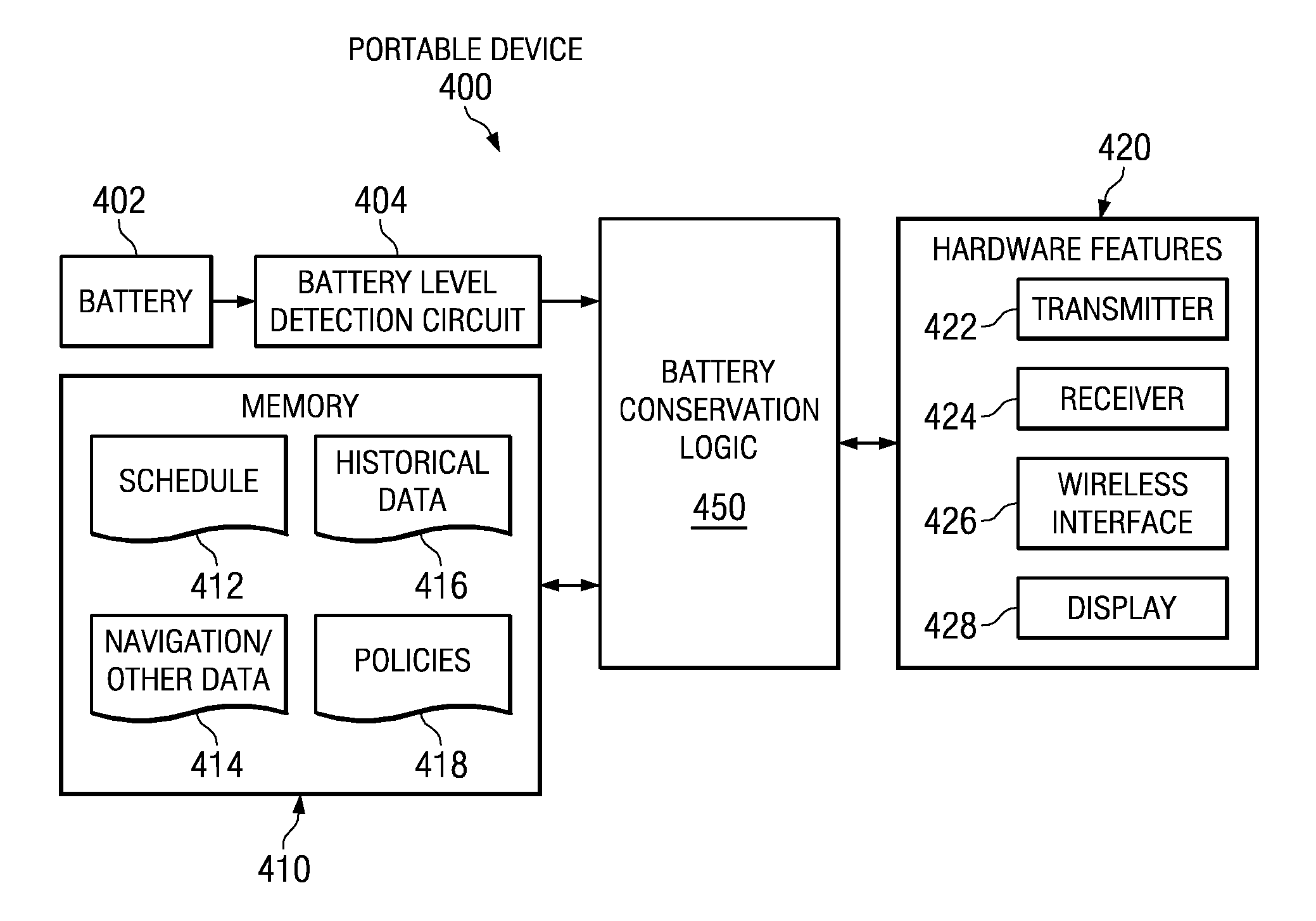
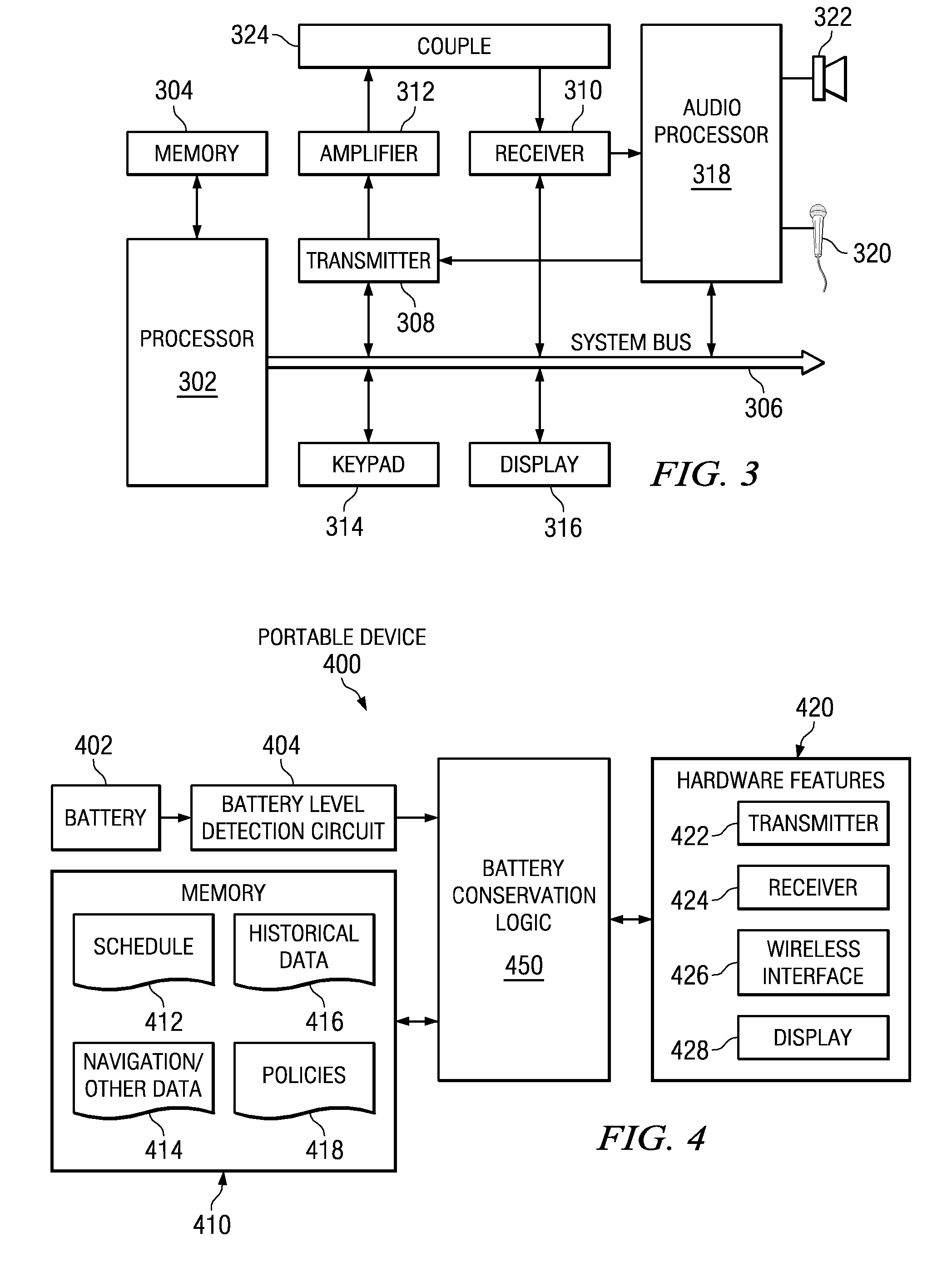
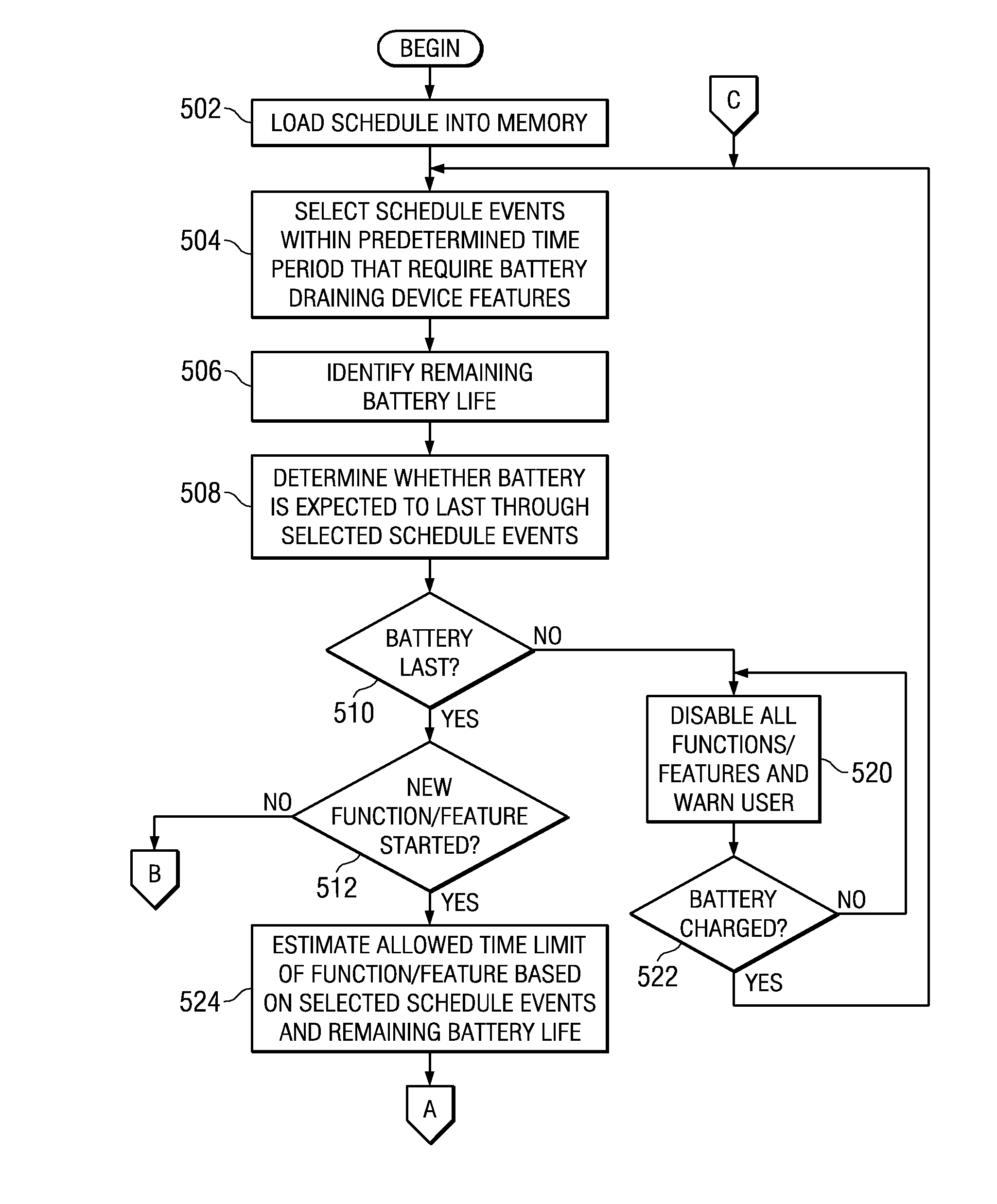
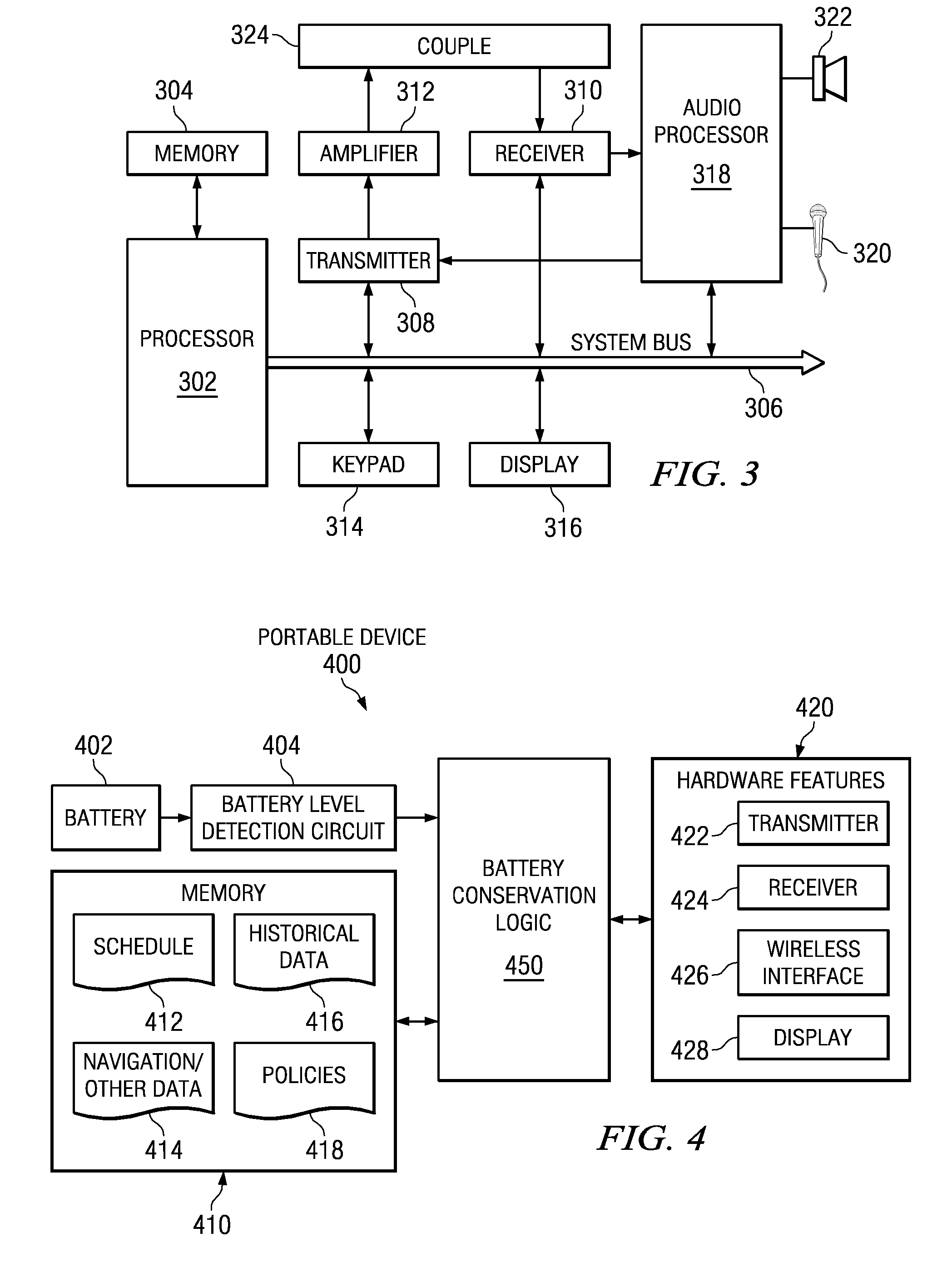
Method, apparatus, and computer program product to manage battery needs in a portable device
ActiveUS20090187780A1Solve the lack of battery lifeVolume/mass flow measurementPower supply for data processingBattery chargeLife time
A battery conservation component synchronizes with a user's schedule or calendar. The battery conservation component may disable functions or features to ensure that the device has sufficient battery life for selected calendar events. The battery conservation component may warn the user if a battery charge is necessary to make selected calendar events. The battery conservation component may be applied to a wide variety of portable devices with time-sensitive events. For example, the battery conservation component may be applied to a device with vehicle navigation and estimate time-sensitive events based on waypoints in the vehicle's route. The battery conservation component may synchronize with a user's travel itinerary. Alternatively, the battery conservation component may suggest alternative functions or features based on a time-sensitive event, such as suggesting a shorter movie on a flight or road trip.
Owner:IBM CORP
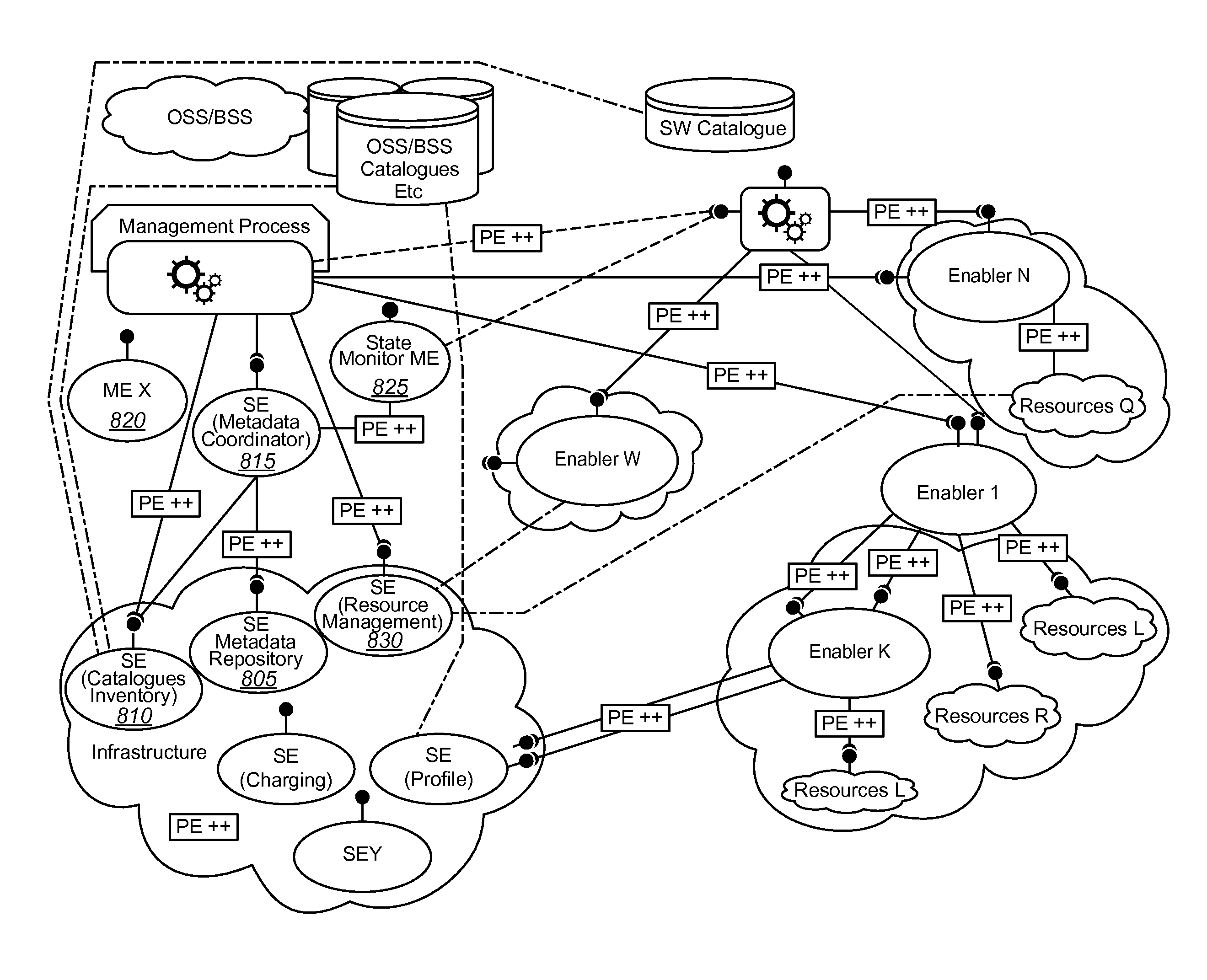
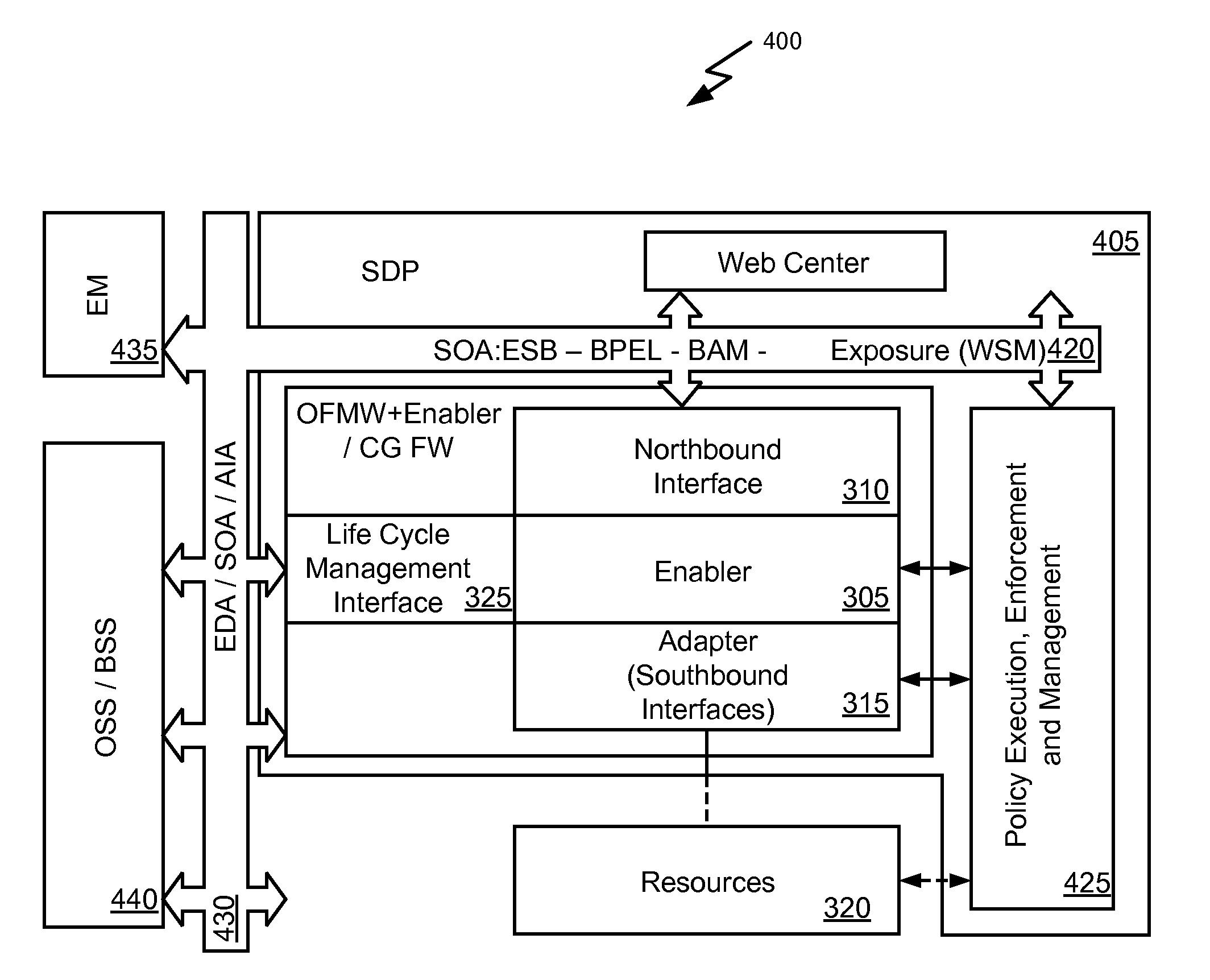
Resource abstraction via enabler and metadata
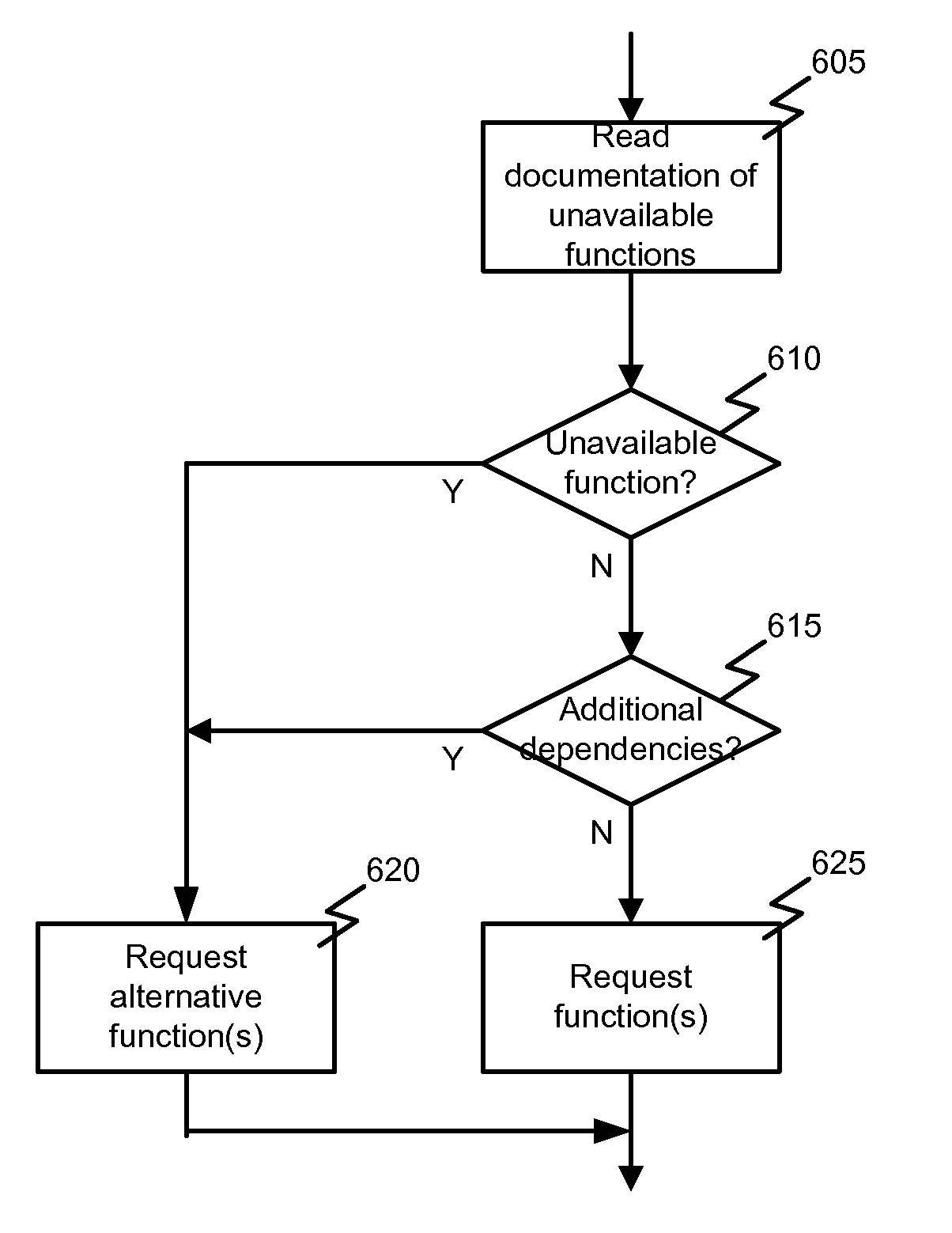
Embodiments of the invention provide systems and methods for managing an enabler and dependencies of the enabler. According to one embodiment, a method of managing an enabler can comprise requesting a management function via a management interface of the enabler. The management interface can provide an abstraction of one or more management functions for managing the enabler and / or dependencies of the enabler. In some cases, prior to requesting the management function metadata associated with the management interface can be read and a determination can be made as to whether the management function is available or unavailable. Requesting the management function via the management interface of the enabler can be performed in response to determining the management function is available. In response to determining the management function is unavailable, one or more alternative functions can be identified based on the metadata and the one or more alternative functions can be requested.
Owner:ORACLE INT CORP
Resource abstraction via enabler and metadata
Embodiments of the invention provide systems and methods for managing an enabler and dependencies of the enabler. According to one embodiment, a method of managing an enabler can comprise requesting a management function via a management interface of the enabler. The management interface can provide an abstraction of one or more management functions for managing the enabler and / or dependencies of the enabler. In some cases, prior to requesting the management function metadata associated with the management interface can be read and a determination can be made as to whether the management function is available or unavailable. Requesting the management function via the management interface of the enabler can be performed in response to determining the management function is available. In response to determining the management function is unavailable, one or more alternative functions can be identified based on the metadata and the one or more Falternative functions can be requested.
Owner:ORACLE INT CORP
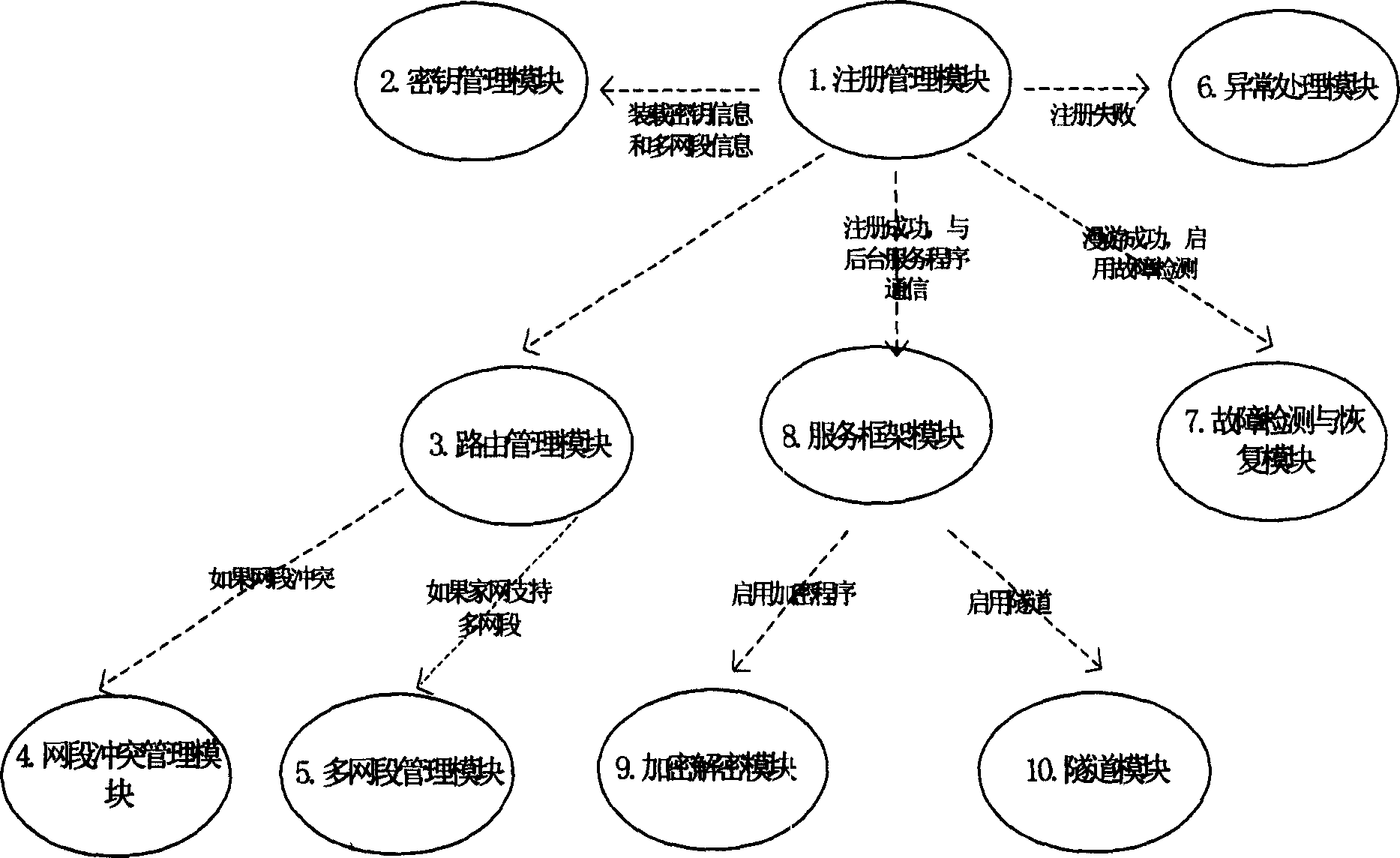
Method for realizing self surrogate function for mobile node
ActiveCN1589060ASafe roamingPrevent eavesdroppingRadio/inductive link selection arrangementsTransmissionEncryption decryptionComputer science
A method for making a mobile nod to realize self agent function is camed out by getting a legal configuration transmit address after panning in the expanding network domain then starting the register rule: certifying to the base domain management entity and informing it the acquired configuration transmit address, getting the ARP agent to the base domain network host to automatically respond the access request of the upper layer protocol stock and determine the path communicated with its host setting up a background service frame to integrate the ciphering and deciphering module and tunnel module and enter into the frame carrying out tunnel packaging and de-packaging operation data, negotiating on dynamic session cipher key and ciphering and de-ciphering user actual transmission data done before dellvery.
Owner:CHINA IWNCOMM
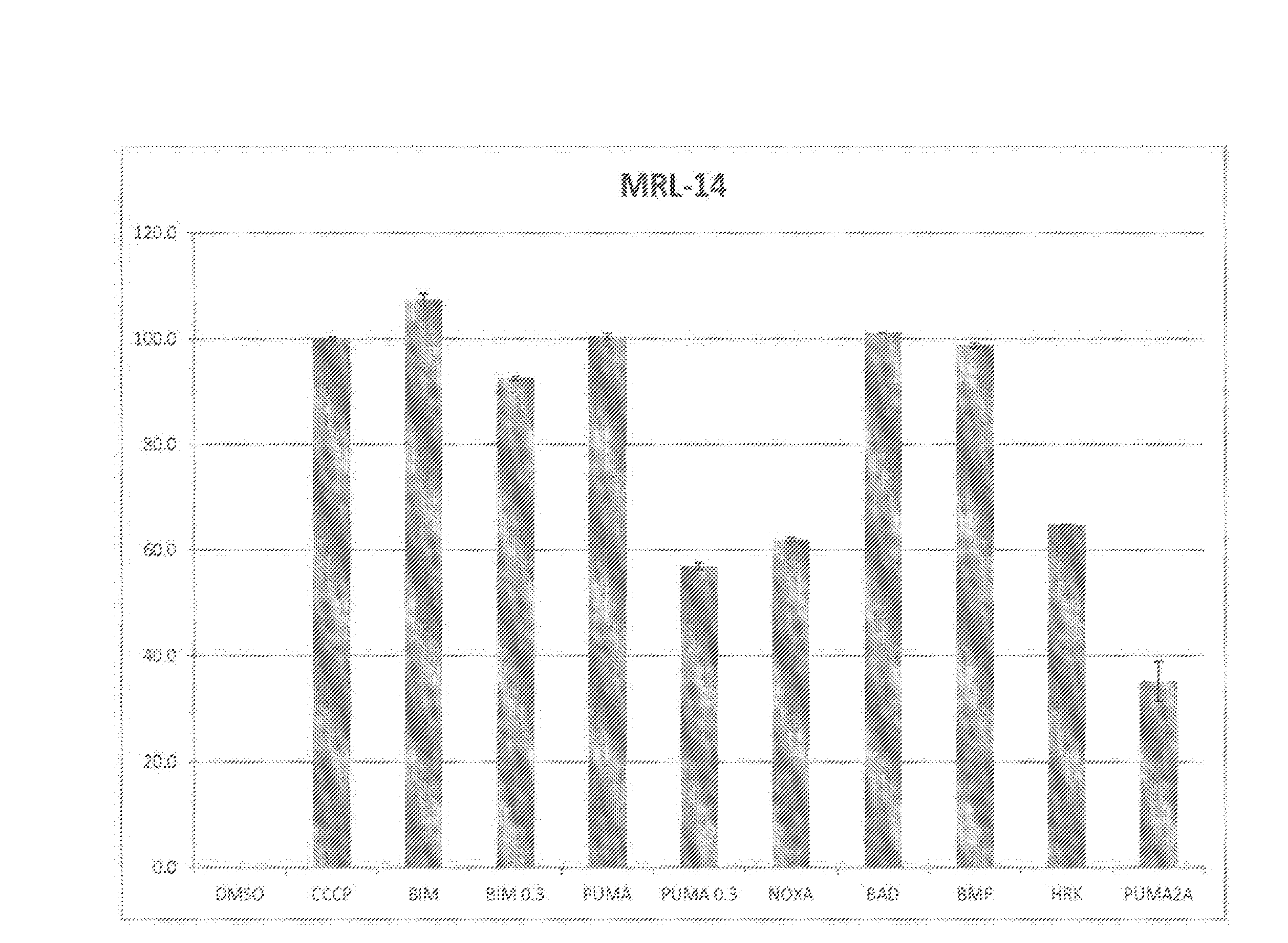
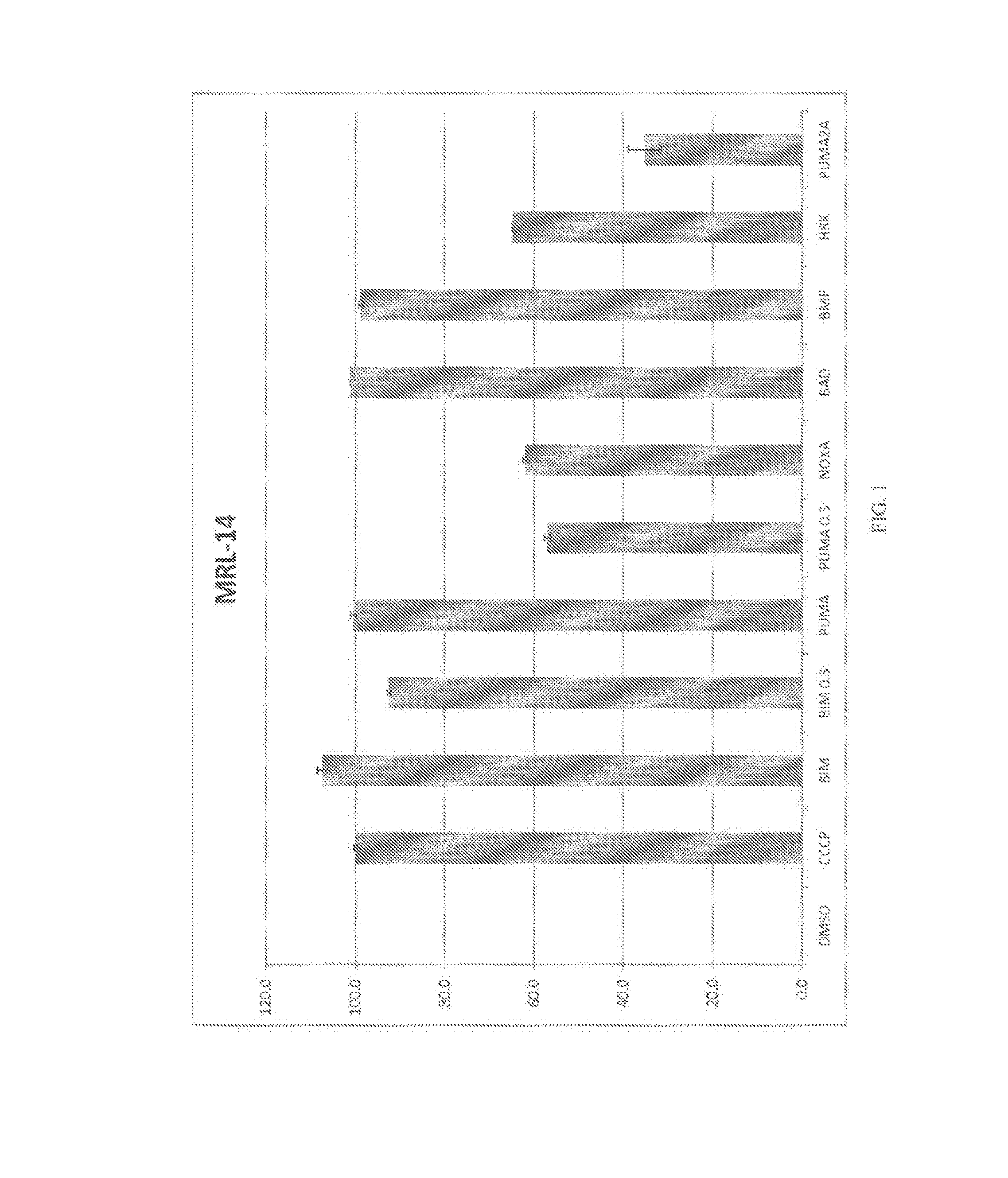
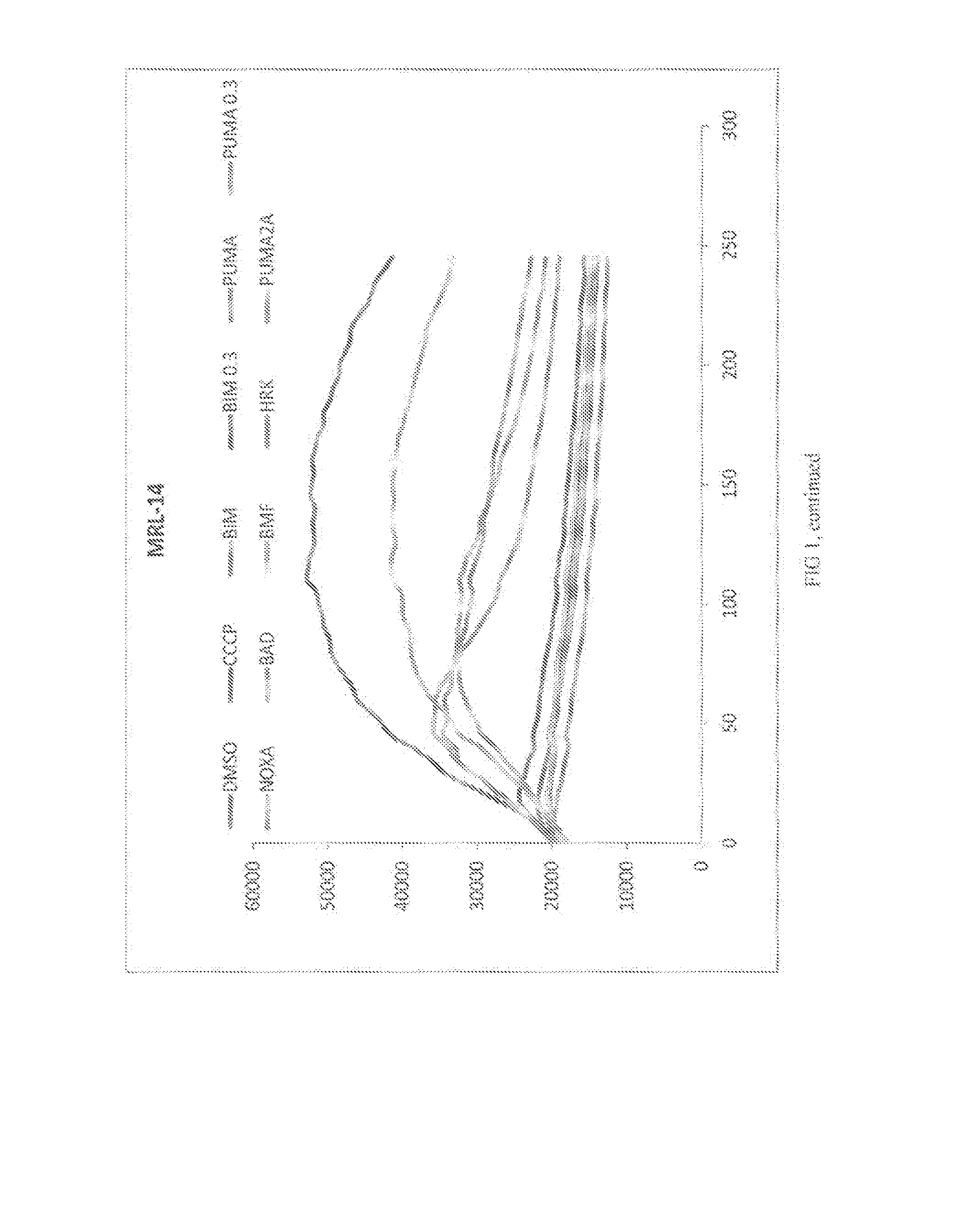
Surrogate functional diagnostics test for cancer
InactiveUS20150301053A1Strong specificityHigh sensitivityMicrobiological testing/measurementLibrary screeningDiagnostic testOncology
The present invention relates to diagnostic methods that are relevant to various cancers and which comprise improvements on a BH3 profiling diagnostic method.
Owner:EUTROPICS PHARMA
Application requesting management function based on metadata for managing enabler or dependency
ActiveUS8458703B2Multiprogramming arrangementsMultiple digital computer combinationsComputer scienceSurrogate function
Embodiments of the invention provide systems and methods for managing an enabler and dependencies of the enabler. According to one embodiment, a method of managing an enabler can comprise requesting a management function via a management interface of the enabler. The management interface can provide an abstraction of one or more management functions for managing the enabler and / or dependencies of the enabler. In some cases, prior to requesting the management function metadata associated with the management interface can be read and a determination can be made as to whether the management function is available or unavailable. Requesting the management function via the management interface of the enabler can be performed in response to determining the management function is available. In response to determining the management function is unavailable, one or more alternative functions can be identified based on the metadata and the one or more alternative functions can be requested.
Owner:ORACLE INT CORP
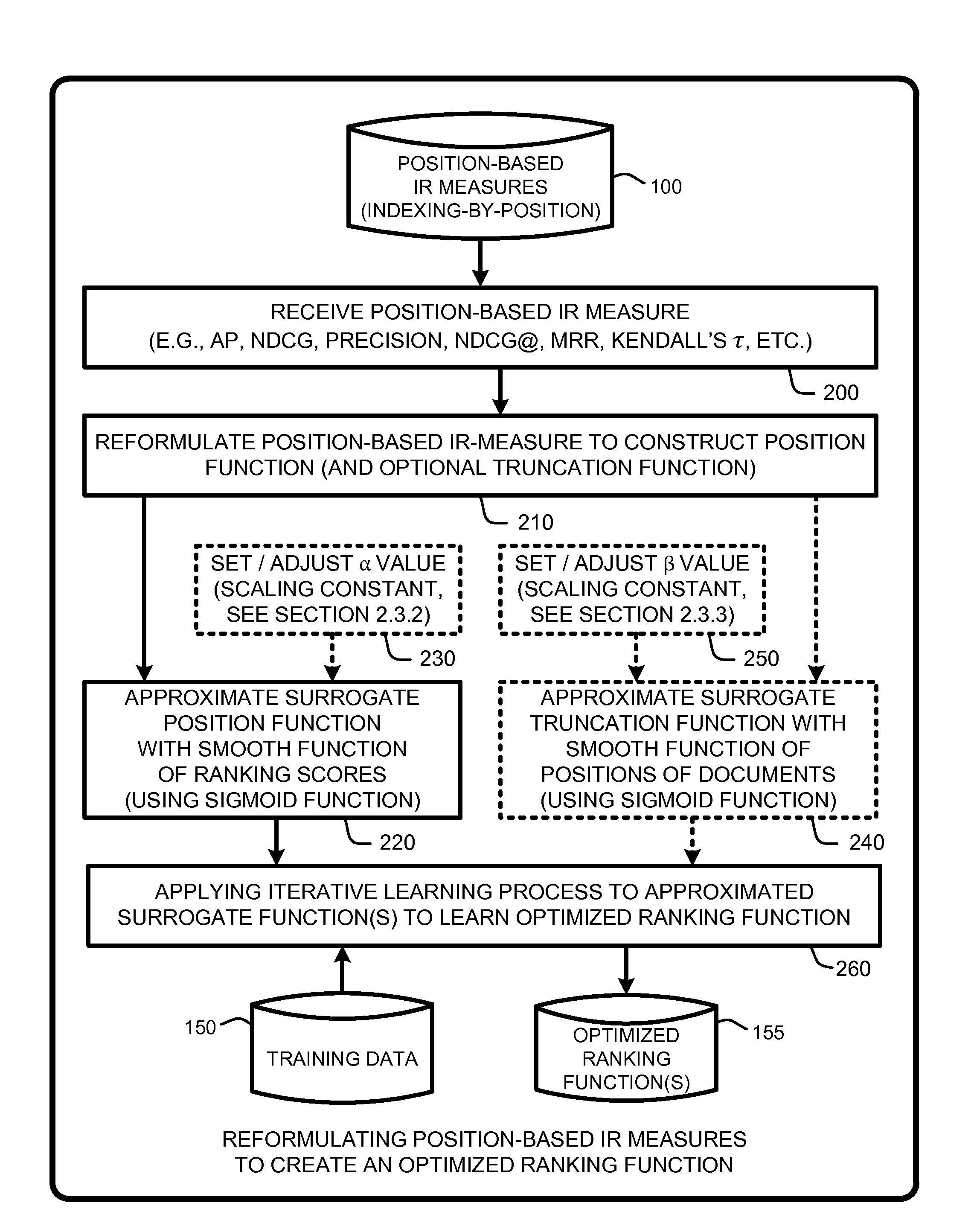
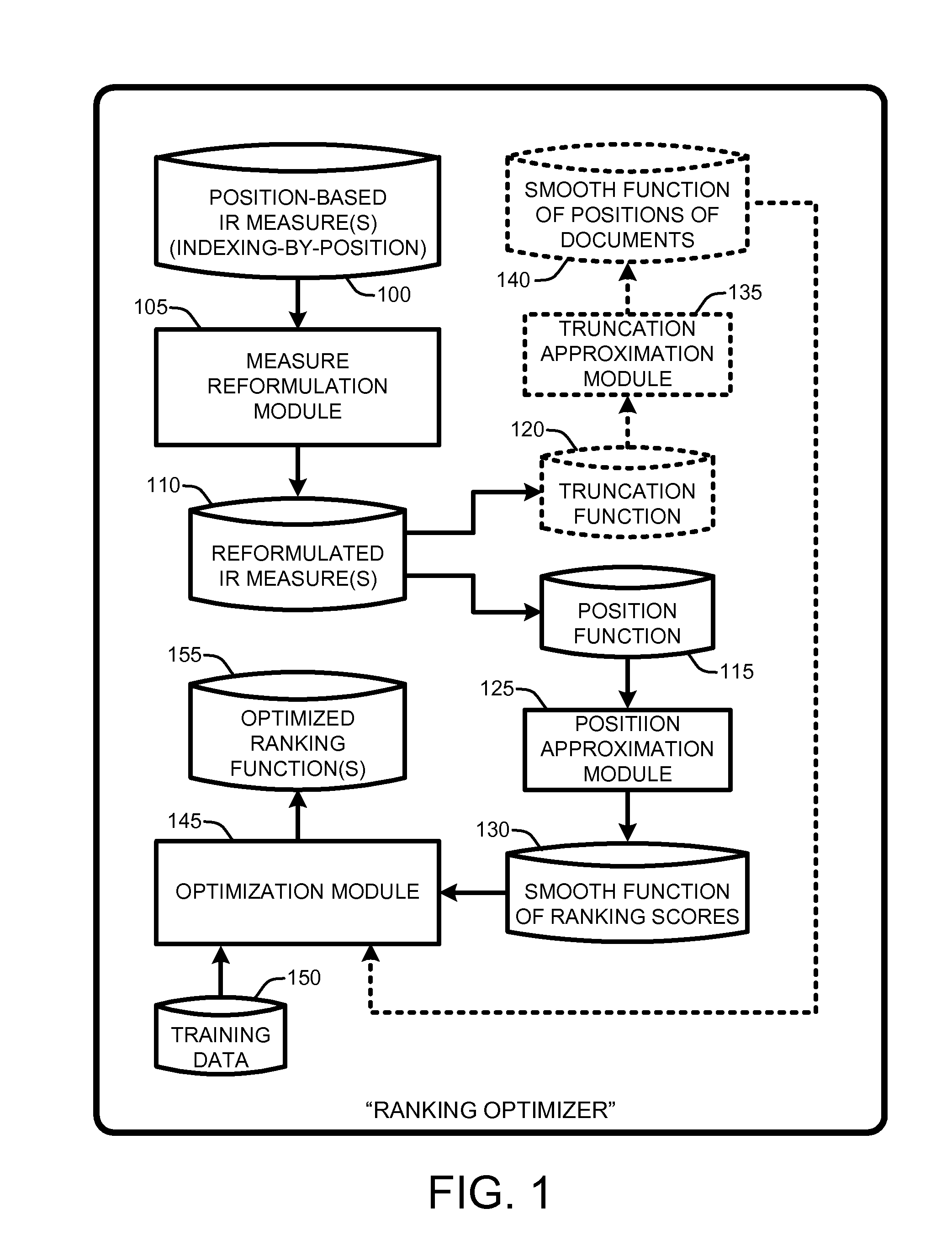
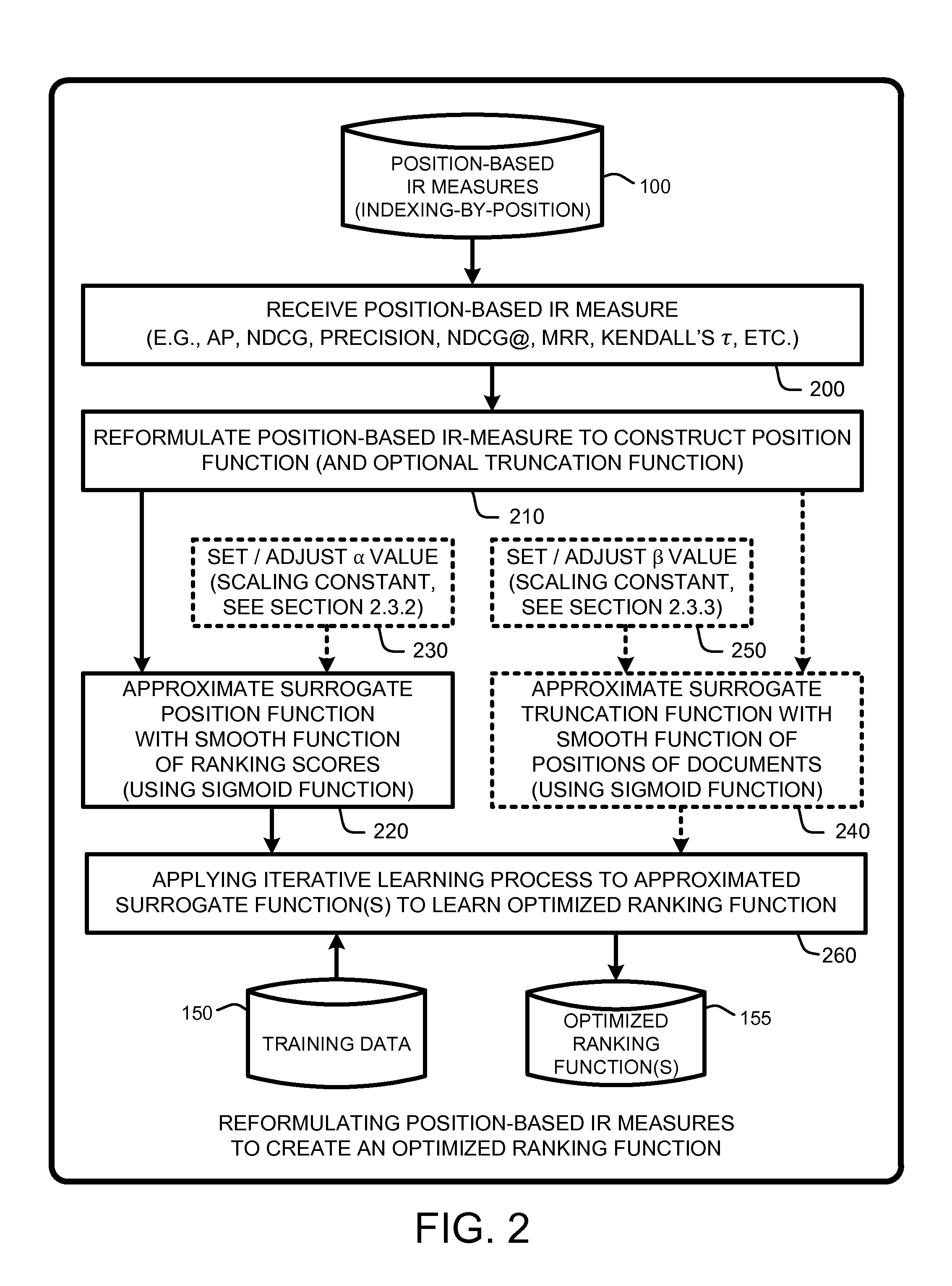
Approximation framework for direct optimization of information retrieval measures
InactiveUS20110302193A1Improve approximation accuracyPrecise positioningDigital data information retrievalDigital data processing detailsDocumentationComputer science
A “Ranking Optimizer,” provides a framework for directly optimizing conventional information retrieval (IR) measures for use in ranking, search, and recommendation type applications. In general, the Ranking Optimizer first reformats any conventional position based IR measure from a conventional “indexing by position” process to an “indexing by documents” process to create a newly formulated IR measure which contains a position function, and optionally, a truncation function. Both of these functions are non-continuous and non-differentiable. Therefore, the Ranking Optimizer approximates the position function by using a smooth function of ranking scores, and, if used, approximates the optional truncation function with a smooth function of positions of documents. Finally, the Ranking Optimizer optimizes the approximated functions to provide a highly accurate surrogate function for use as a surrogate IR measure.
Owner:MICROSOFT TECH LICENSING LLC
Managing battery needs in a portable device
A battery conservation component synchronizes with a user's schedule or calendar. The battery conservation component may disable functions or features to ensure that the device has sufficient battery life for selected calendar events. The battery conservation component may warn the user if a battery charge is necessary to make selected calendar events. The battery conservation component may be applied to a wide variety of portable devices with time-sensitive events. For example, the battery conservation component may be applied to a device with vehicle navigation and estimate time-sensitive events based on waypoints in the vehicle's route. The battery conservation component may synchronize with a user's travel itinerary. Alternatively, the battery conservation component may suggest alternative functions or features based on a time-sensitive event, such as suggesting a shorter movie on a flight or road trip.
Owner:INT BUSINESS MASCH CORP
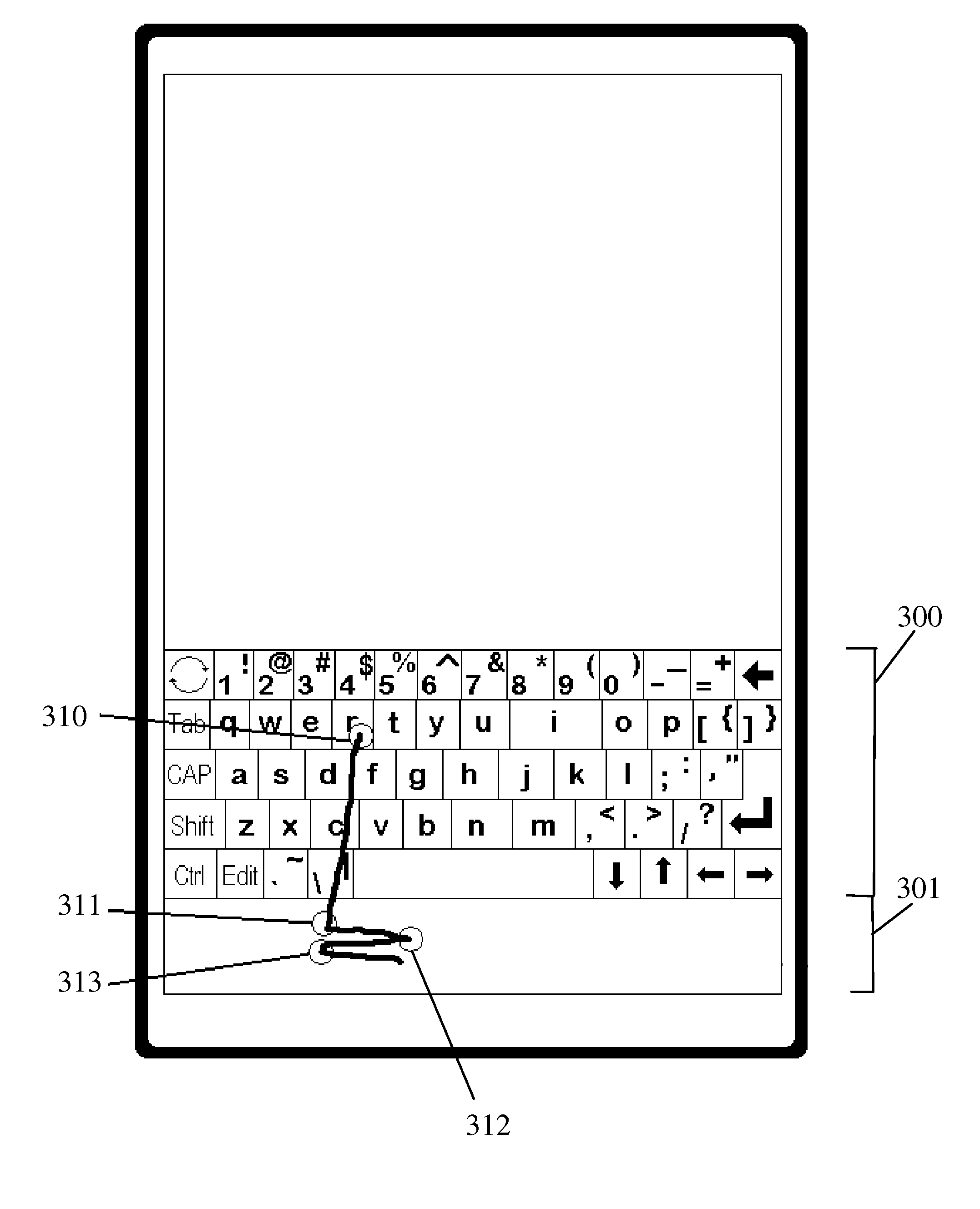
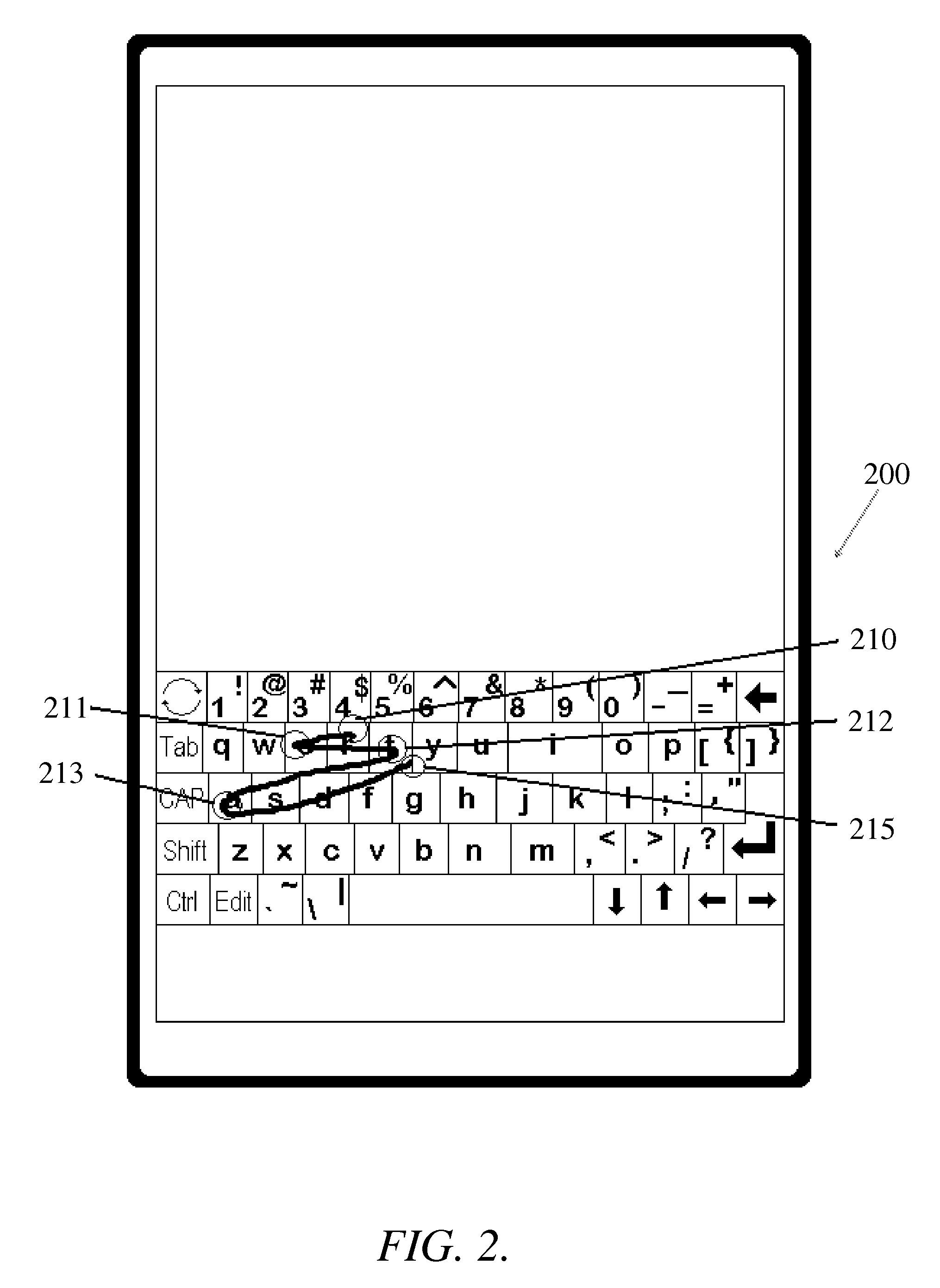
Gesture-based repetition of key activations on a virtual keyboard
ActiveUS8884872B2Easy to repeat quicklyRapid repetitionInput/output for user-computer interactionCathode-ray tube indicatorsBiological activationSurrogate function
Owner:CERENCE OPERATING CO
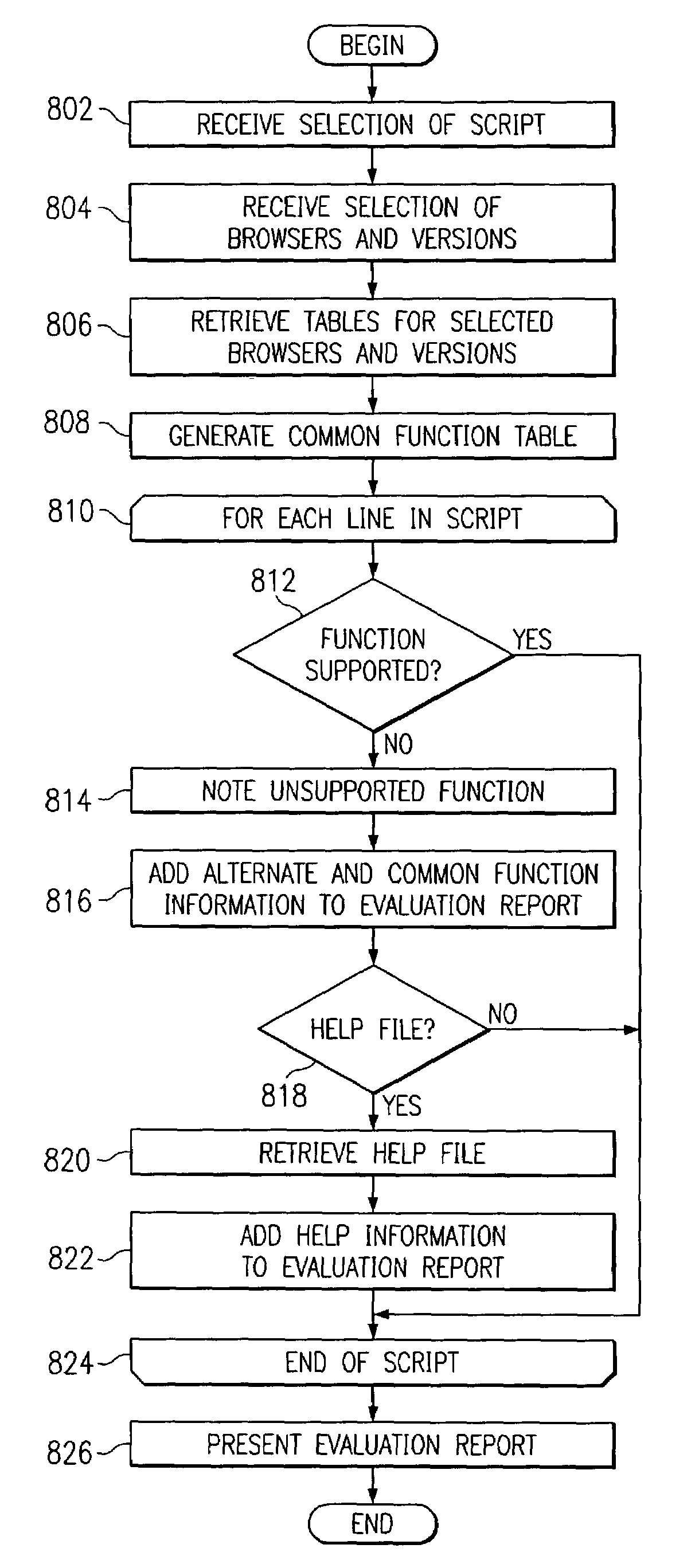
Script evaluator
ActiveUS7000221B2Reverse engineeringSpecific program execution arrangementsSoftware vendorProgram analysis
A script evaluator analyzes script code and identifies possible problems with respect to given browsers and given browser versions. When configuring the parameters of analysis of the script evaluator, the user may select versions of known browsers for which support is desired. The script evaluator may point out functions in the script code that are not supported by certain versions of selected browsers. The evaluator may also suggest alternative functions that may be supported by all desired browser versions. Help information may be provided to assist the user. The script evaluator may receive browser support and help information from a library. The library may be collected from the browser software vendors or may be supplied with the script evaluator. The script evaluator may also include an editor or may be part of an existing developer tool.
Owner:TWITTER INC
System and method for inspecting dynamically generated executable code
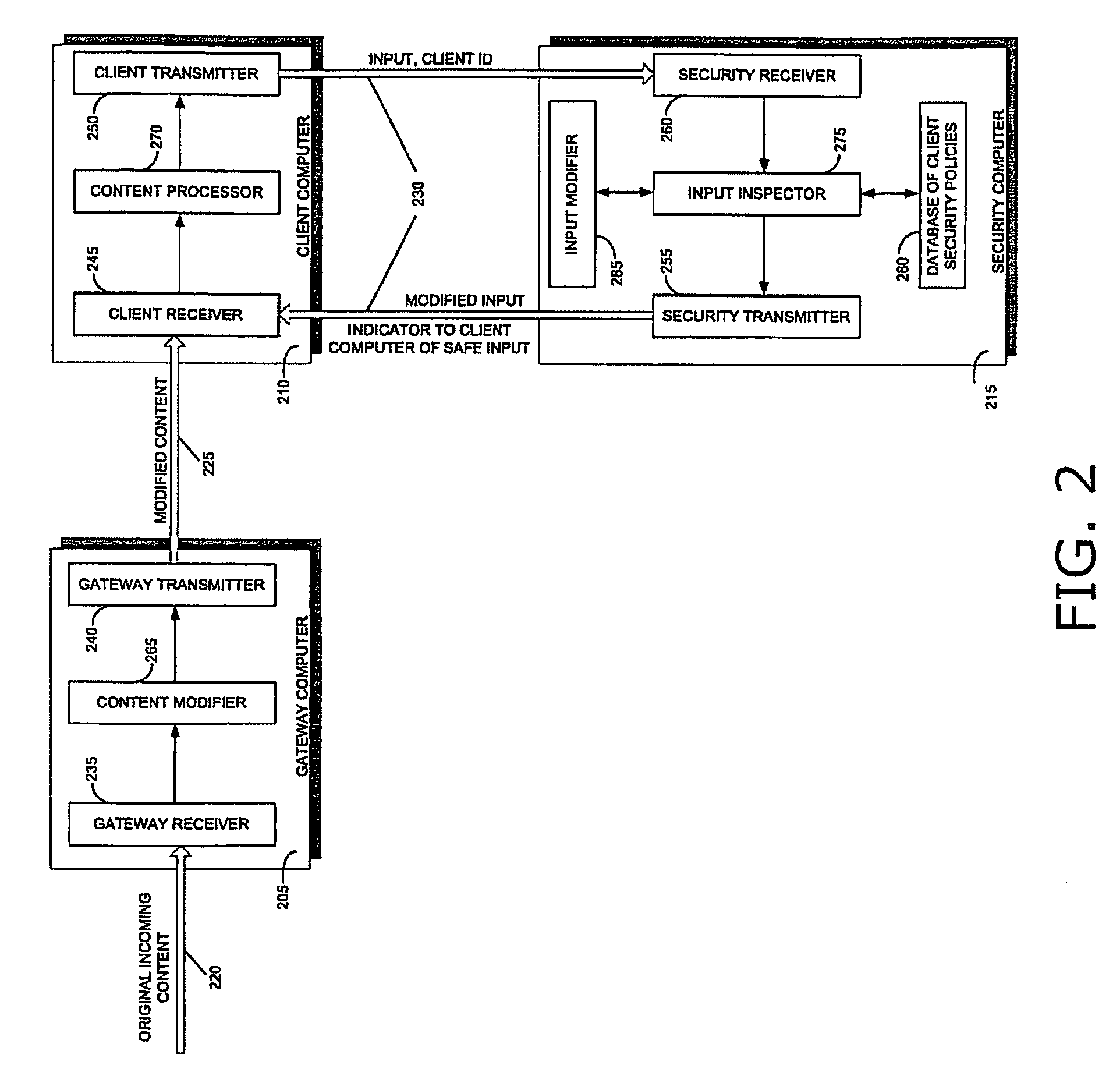
A method for protecting a client computer from dynamically generated malicious content, including receiving at a gateway computer content being sent to a client computer for processing, the content including a call to an original function, and the call including an input, modifying the content at the gateway computer, including replacing the call to the original function with a corresponding call to a substitute function, the substitute function being operational to send the input to a security computer for inspection, transmitting the modified content from the gateway computer to the client computer, processing the modified content at the client computer, transmitting the input to the security computer for inspection when the substitute function is invoked, determining at the security computer whether it is safe for the client computer to invoke the original function with the input, transmitting an indicator of whether it is safe for the client computer to invoke the original function with the input, from the security computer to the client computer, and invoking the original function at the client computer with the input, only if the indicator received from the security computer indicates that such invocation is safe. A system and a computer-readable storage medium are also described and claimed.
Owner:FINJAN LLC
Vehicle instability pre-warning system and method
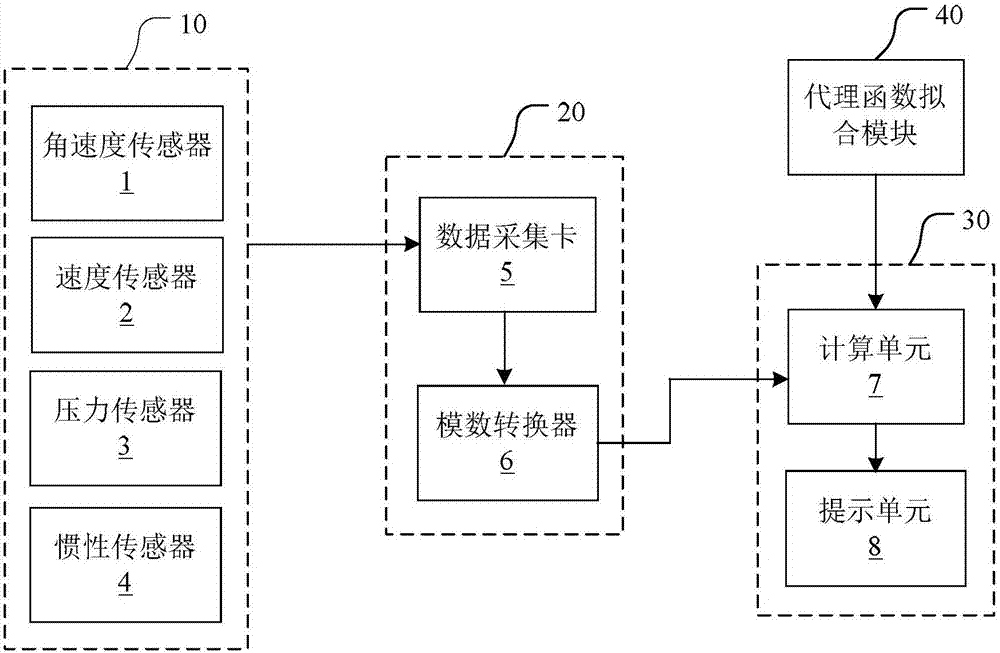
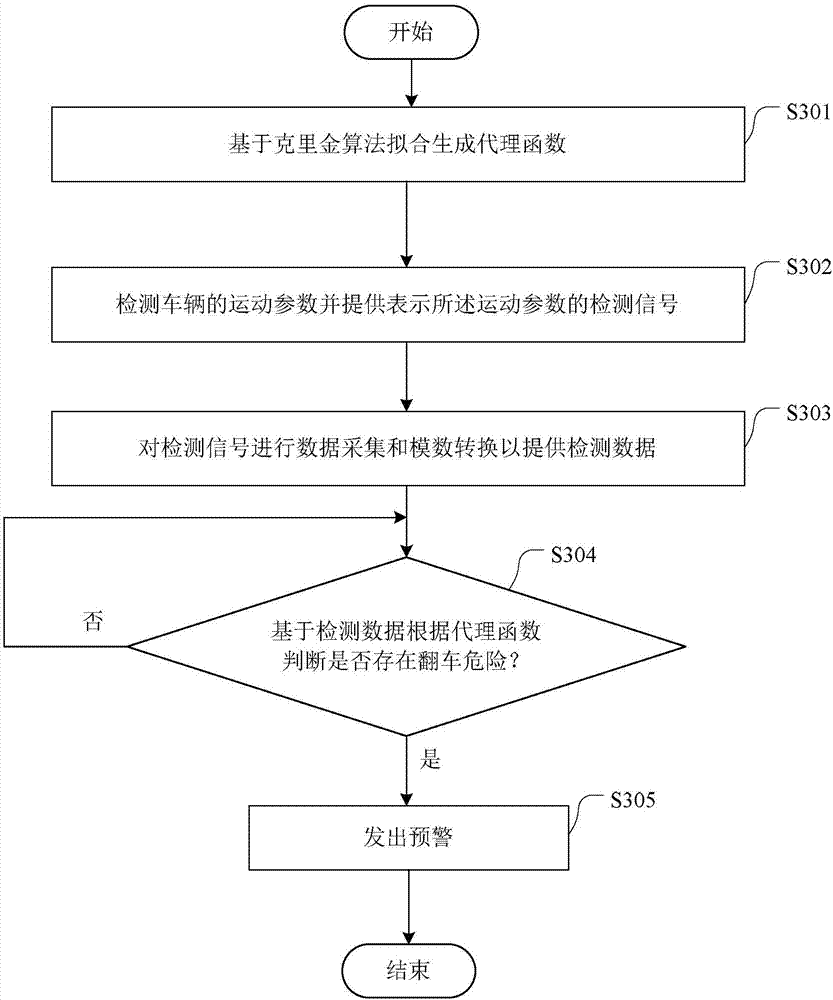
The invention provides a vehicle instability pre-warning system and method. The vehicle instability pre-warning system comprises a detecting module, a data collecting module and a pre-warning module, wherein the detecting module is used for detecting a state parameter of a vehicle and providing a detection signal that expresses the state parameter; the data collecting module is used for filtering the detection signal from the detecting module so as to obtain detection data; the pre-warning module is used for judging whether vehicle turnover danger exists or not according to a surrogate function on the basis of the detection data and giving pre-warning if the vehicle turnover danger exists, wherein the surrogate function is fitted by using Kriging algorithm in advance on the basis of the detection data. As the surrogate function is built by using the Kriging algorithm, the function relation between the state parameter of the vehicle and the vehicle body stability can be established to improve the pre-warning accuracy.
Owner:JILIN UNIV
Image forming apparatus
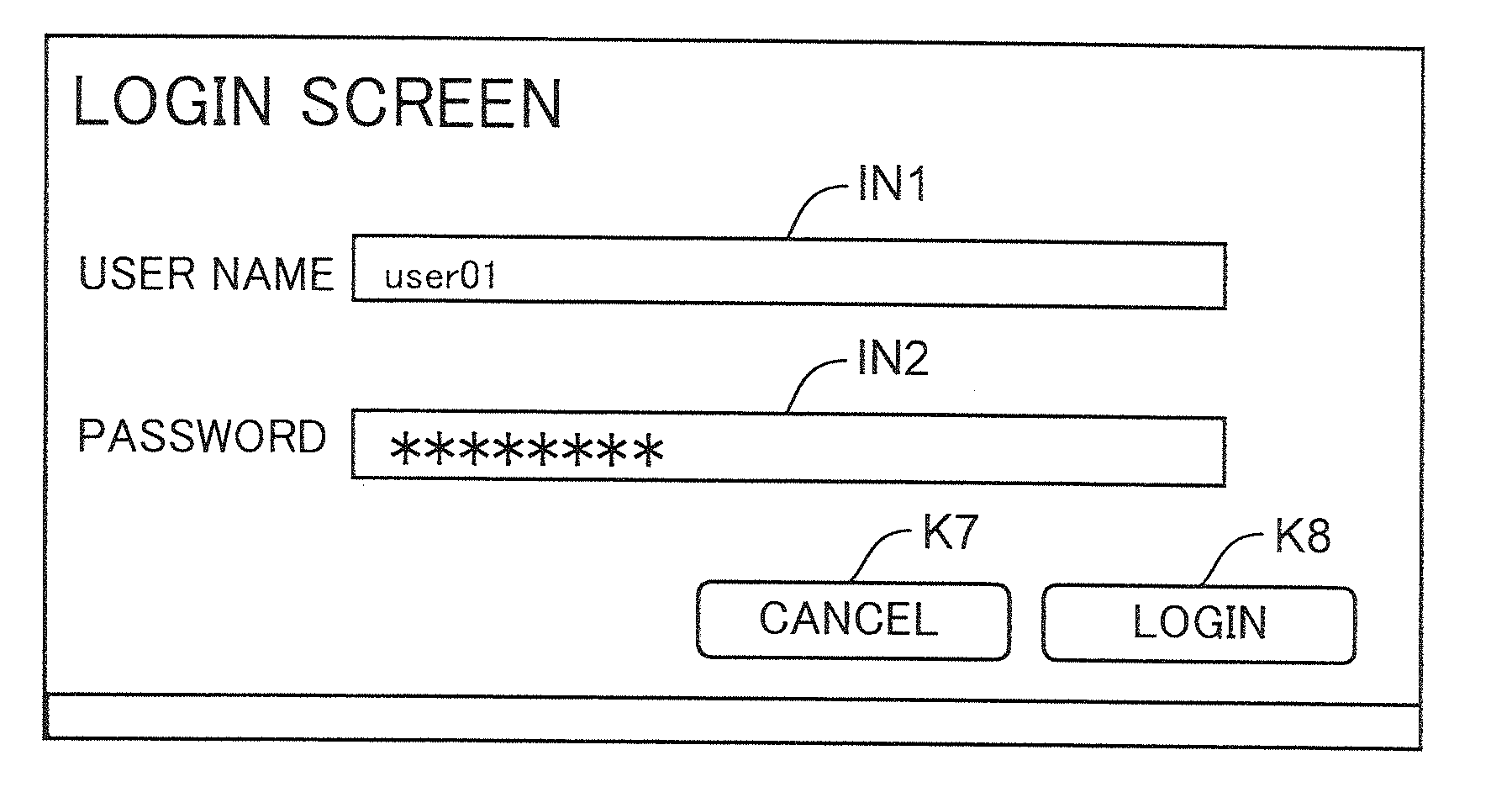
ActiveUS20130347098A1Reduce troubleDigital data processing detailsUnauthorized memory use protectionInternet privacyImage formation
An image forming apparatus includes a control unit, a login information storage, a login information receiver, a login authenticator, a target function setter, an authorization information storage, an alternative function information storage and a target function changer. The target function changer sets a user alternative function matching a user authorized function related to an authenticated user as a target function out of functions alternative to a user prohibited function and determined by alternative function information instead of the user prohibited function different from the user authorized function related to the authenticated user out of target functions when the authenticated user is set in a login state.
Owner:KYOCERA DOCUMENT SOLUTIONS INC
Modifying and simulating the operating software of a technical system
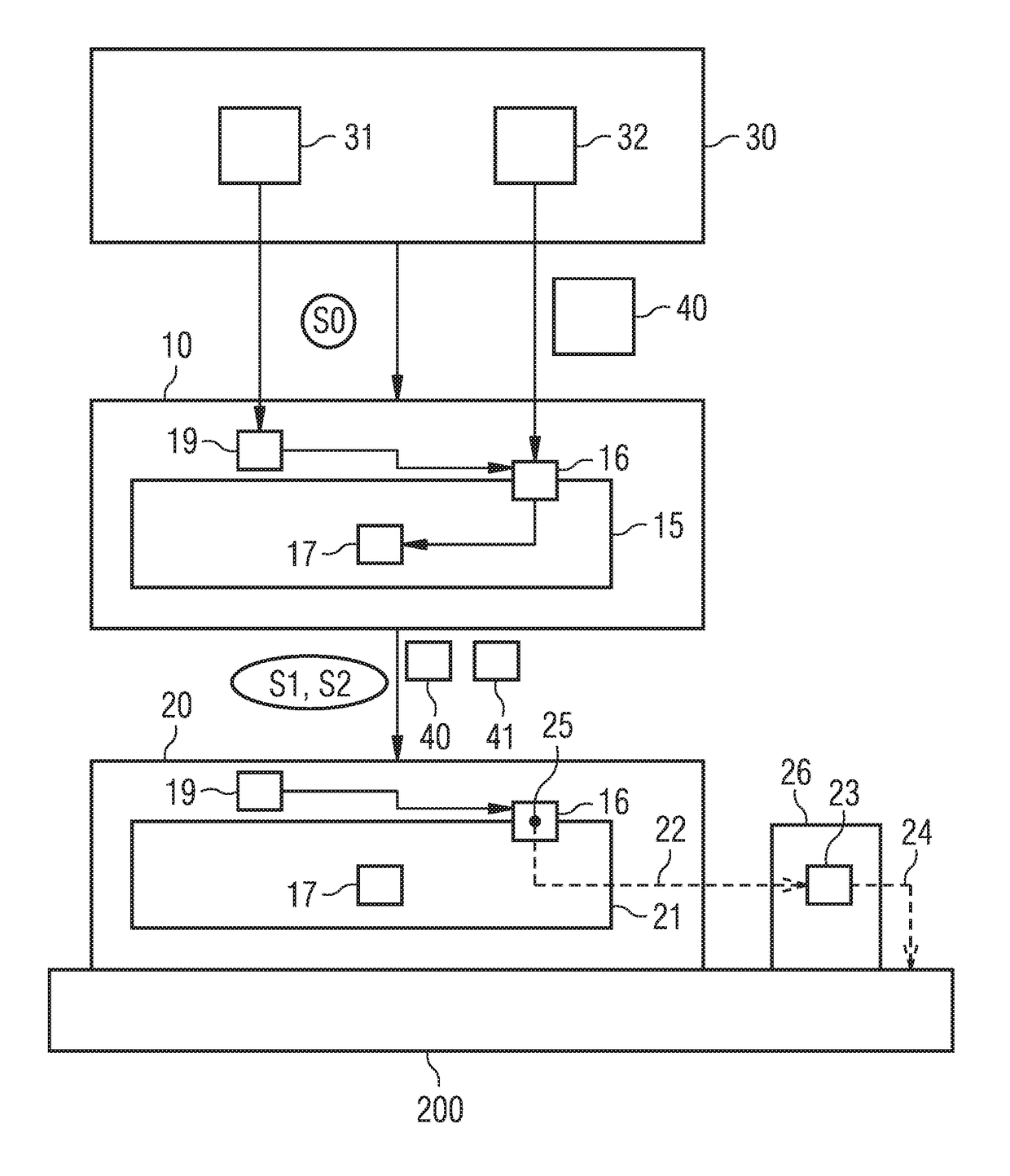
ActiveUS20180052698A1Simple and inexpensiveProgram initiation/switchingDesign optimisation/simulationEmbedded systemSurrogate function
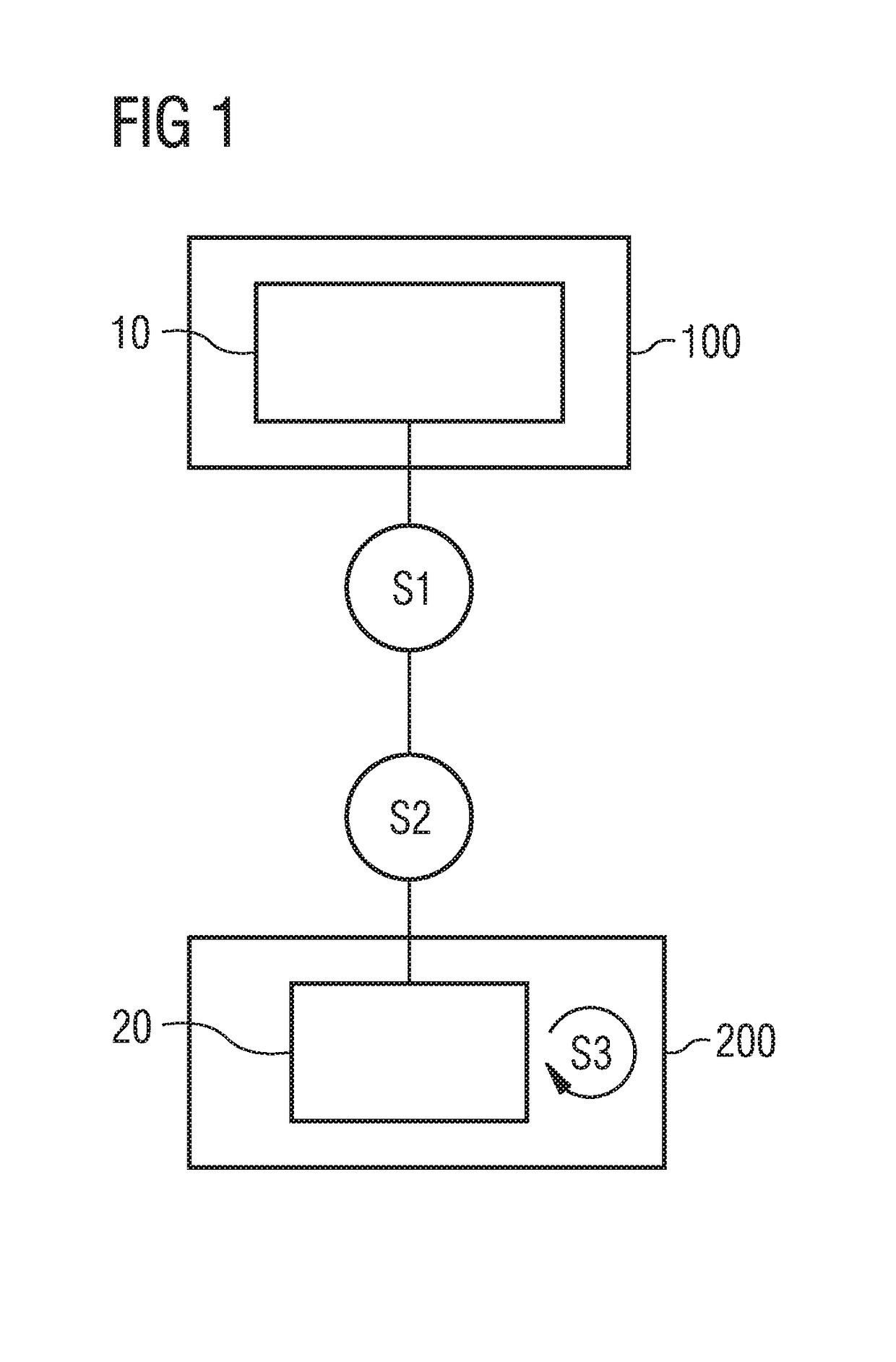
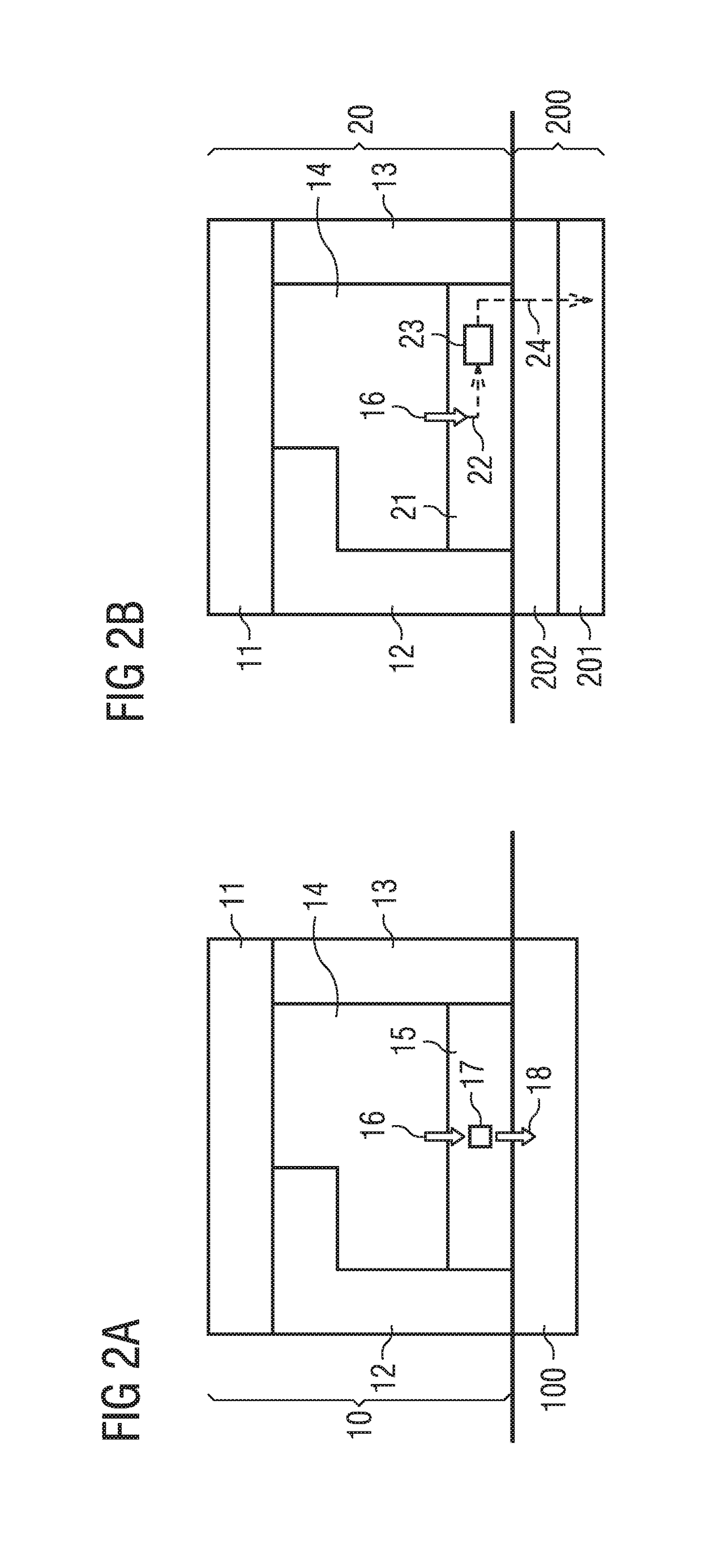
According to the invention, the operating software 10 of a technical system, particularly of a controller for controlling or regulating at least one technical device, is modified by virtue of hardware-dependent software components in the operating software 10 executable directly on the technical system not being executed and instead the functional behavior of the hardware-dependent software components being recreated by substitute functions 23. To this end, the hardware-dependent software components are automatically identified (step S1), and the substitute functions 23 are automatically ascertained or produced. On execution in a suitable simulation environment 200 (step S3), the operating software 20 modified in this way simulates the technical system independently of the real hardware 100 thereof.
Owner:DSPACE DIGITAL SIGNAL PROCESSING & CONTROL ENG
Efficient method for semi-supervised machine learning
A method is disclosed. The method includes a) obtaining a data set comprising a subset of labeled data and a subset of unlabeled data, b) determining a minimization equation characterizing a semi-supervised learning process, the minimization equation comprising a convex component and a non-convex component; c) applying a smoothing function to the minimization equation to obtain a smoothed minimization equation; d) determining a surrogate function based on the smoothed minimization equation and the data set, wherein the surrogate function includes a convex surrogate function component and a non-convex surrogate function component; e) performing a minimization process on the surrogate function resulting in a temporary minimum solution; and f) repeating d) and e) until a global minimum solution is determined. The method also includes creating a support vector machine using the global minimum solution.
Owner:VISA INT SERVICE ASSOC
A potential malware analysis method apparatus based on virtualization technology and related
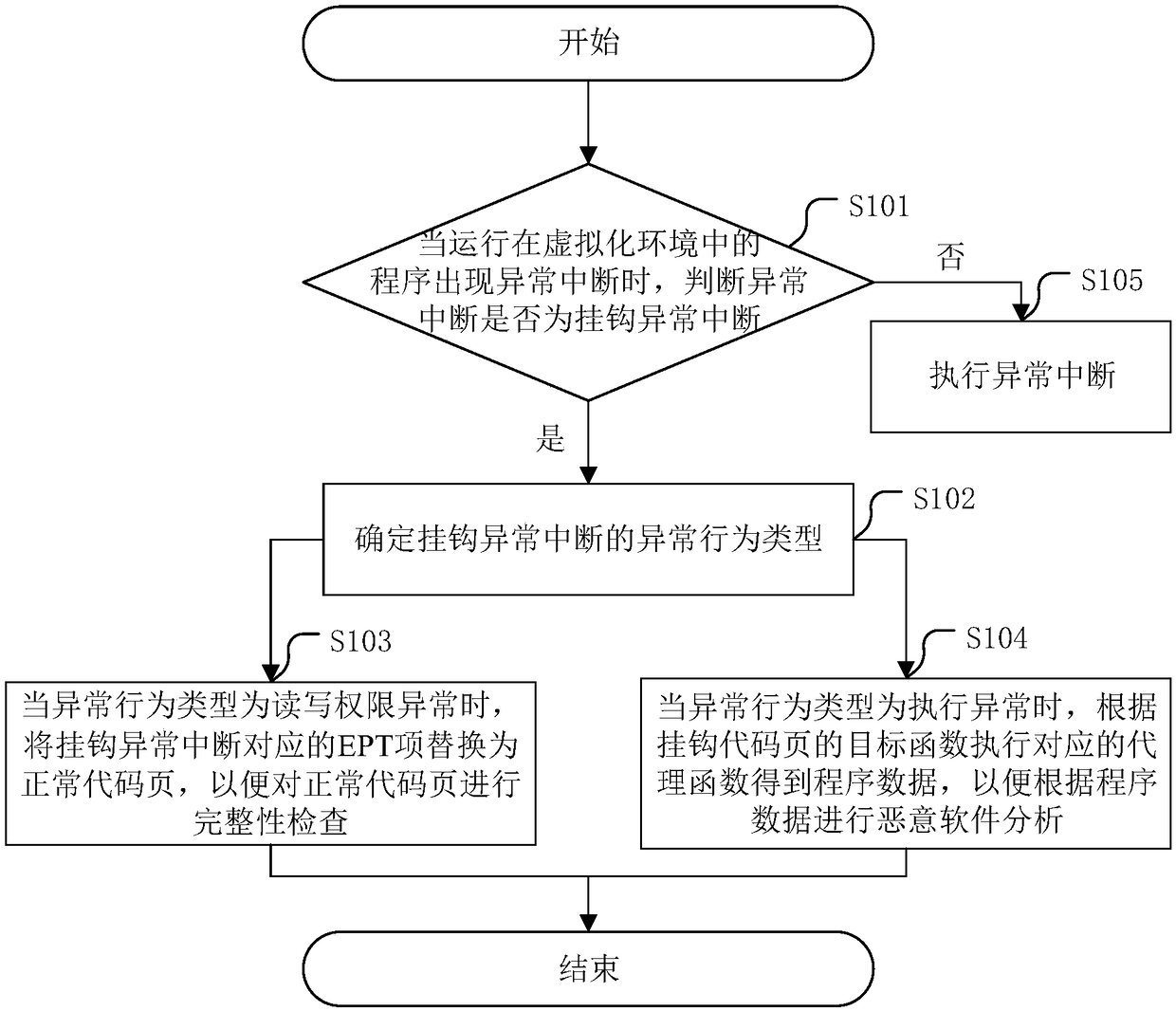
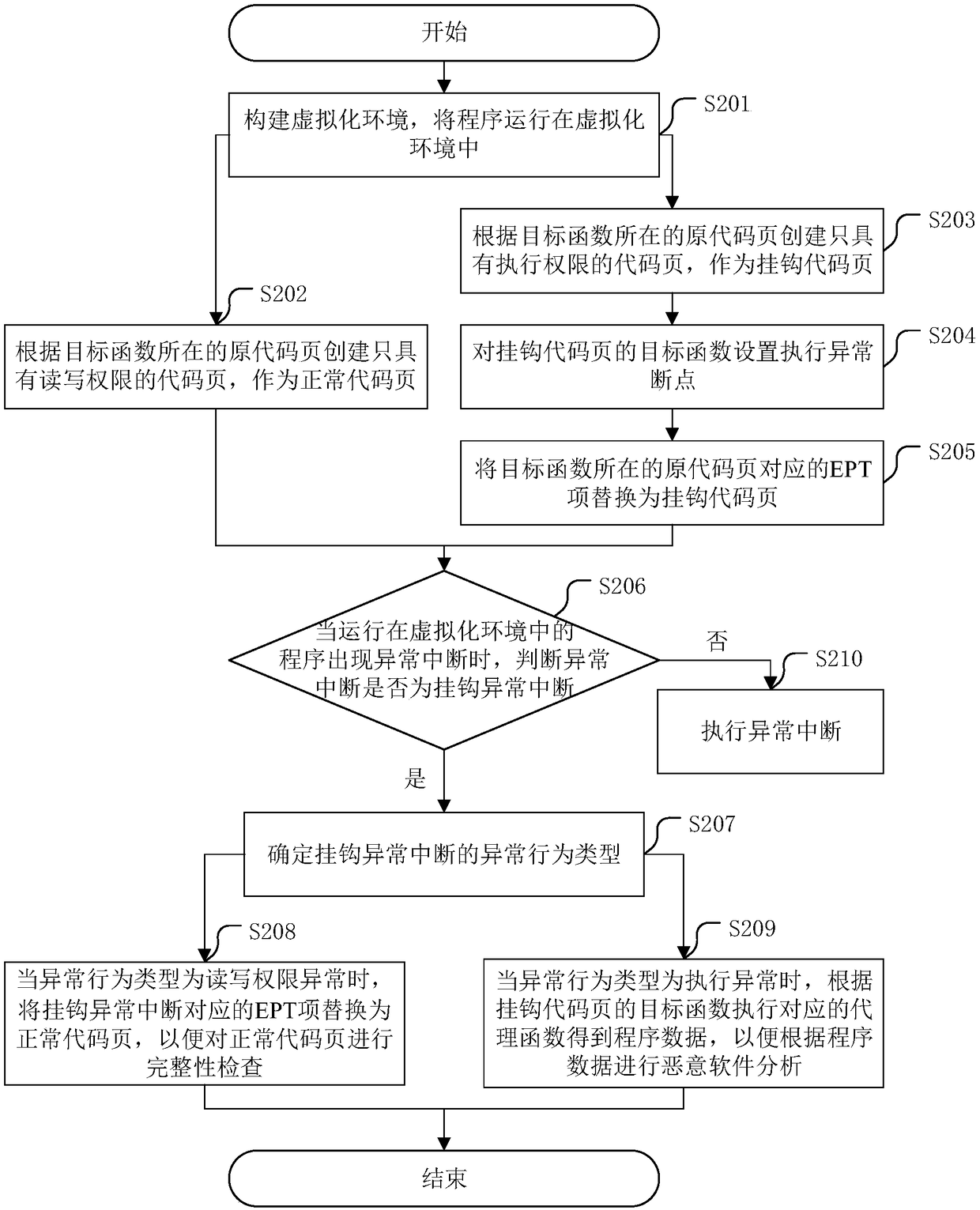
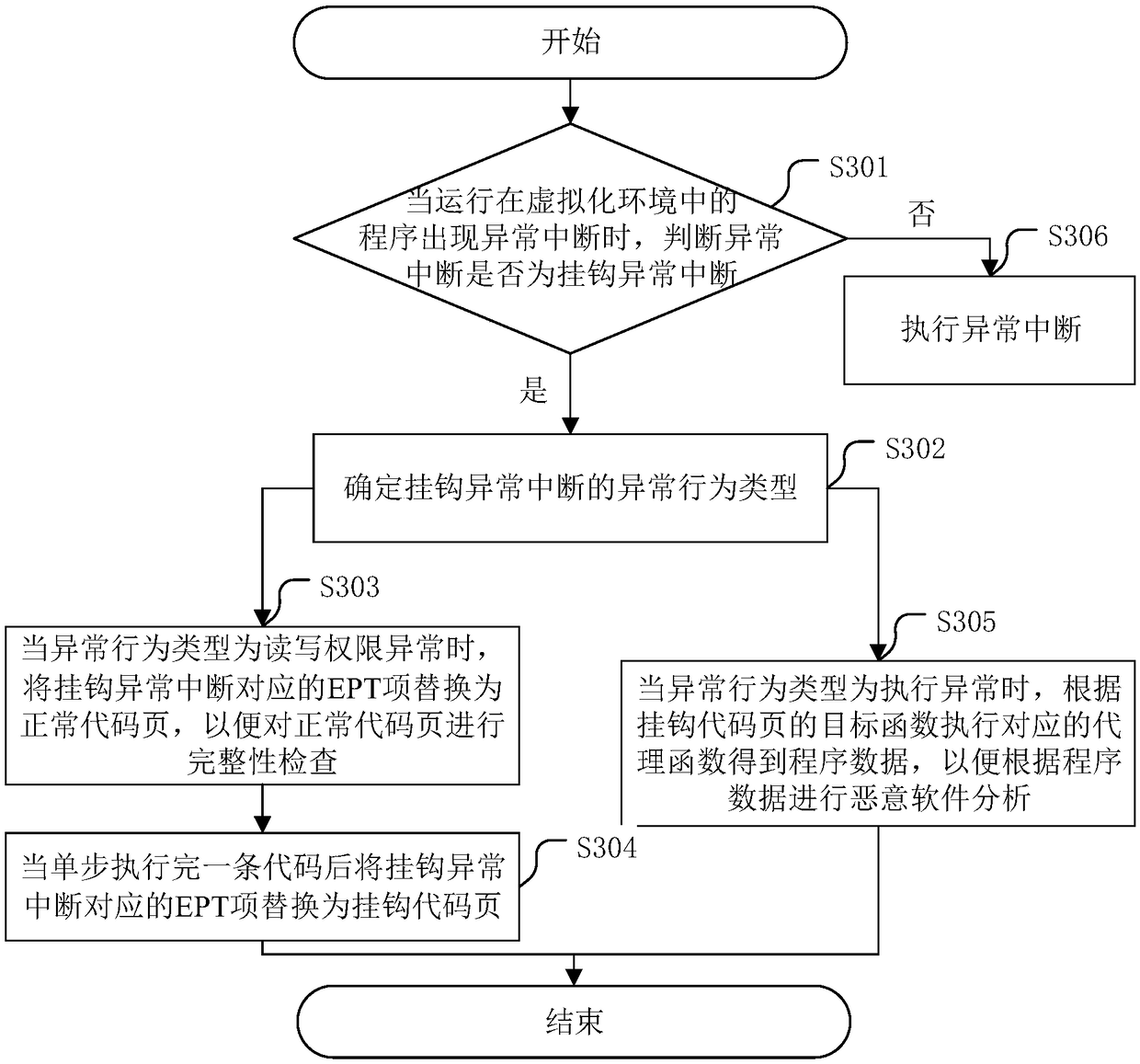
ActiveCN109388948AAvoid cracking operationsImprove analysis efficiencyPlatform integrity maintainanceVirtualizationMalware analysis
The invention discloses a potential malware analysis method based on virtualization technology and a related device. The method comprises the following steps: when an abnormal interrupt occurs to a program running in a virtualization environment, judging whether the abnormal interrupt is a hook abnormal interrupt or not; if so, the abnormal behavior type of hook abnormal interruption is determined; when the exception behavior type is read / write permission exception, the EPT entry corresponding to hook exception interrupt is replaced with normal code page to check the integrity of normal code page. When the abnormal behavior type is execution exception, the program data is obtained by executing the corresponding surrogate function according to the objective function of the hook code page, so as to perform malware analysis according to the program data. The normal code page is replaced with the hook code page by the type of hook abnormal interrupt, so that program data can be obtained when executing the proxy function corresponding to the hook code page through integrity check, malware analysis is realized under the integrity check, and the analysis efficiency is improved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
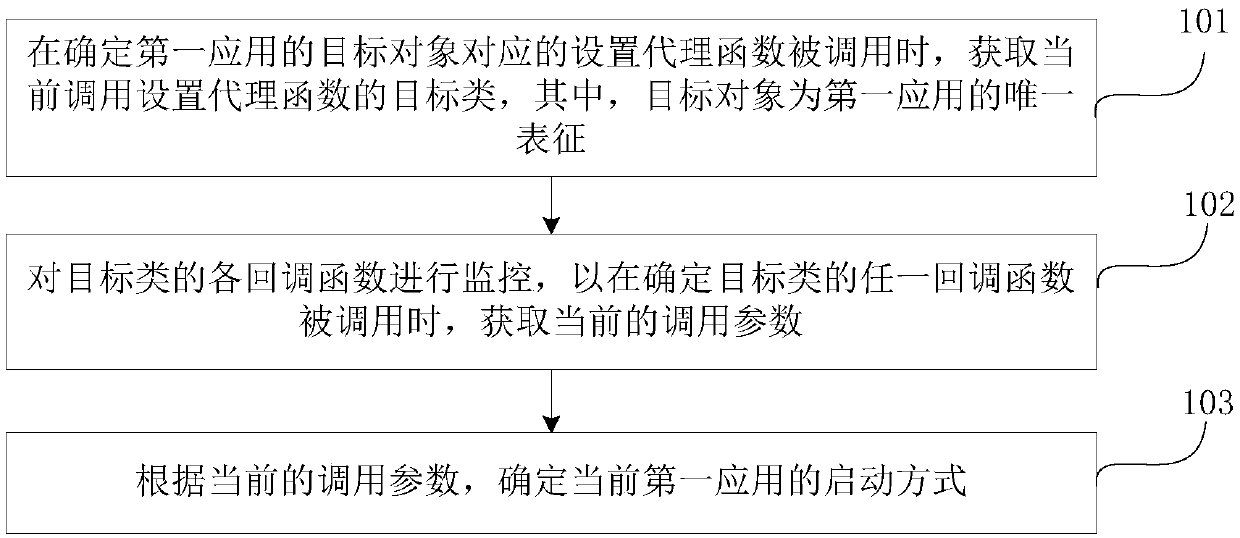
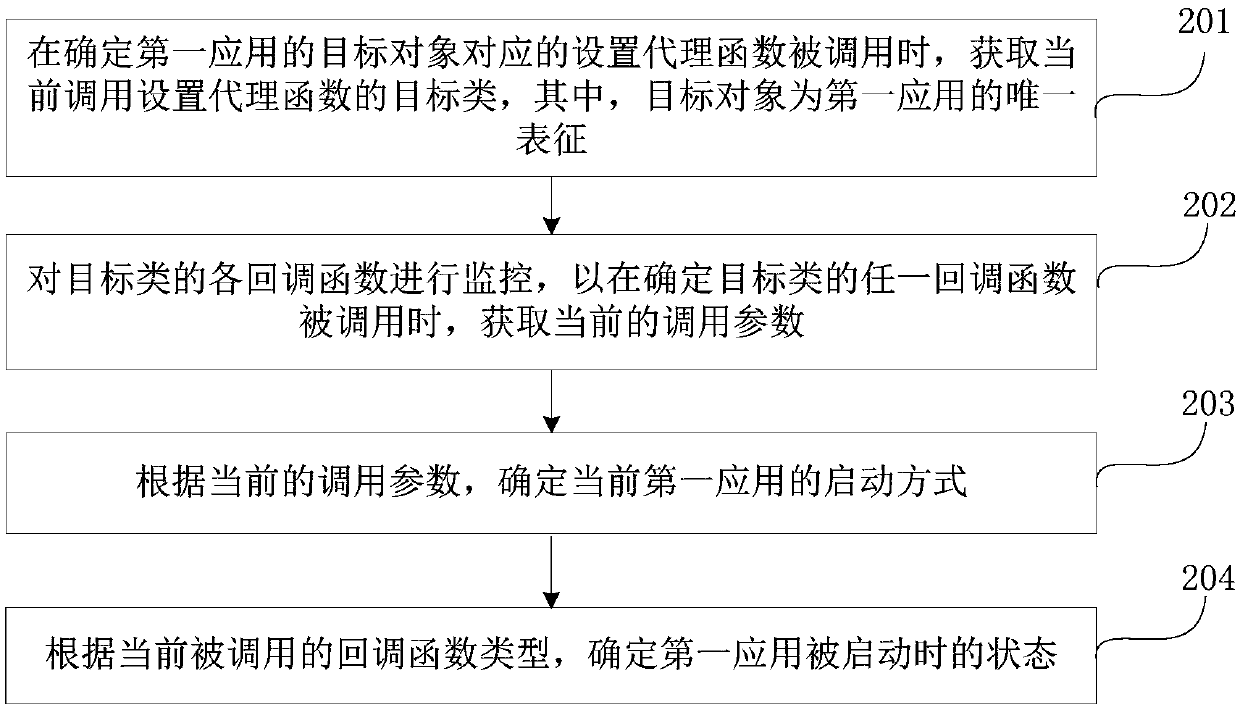
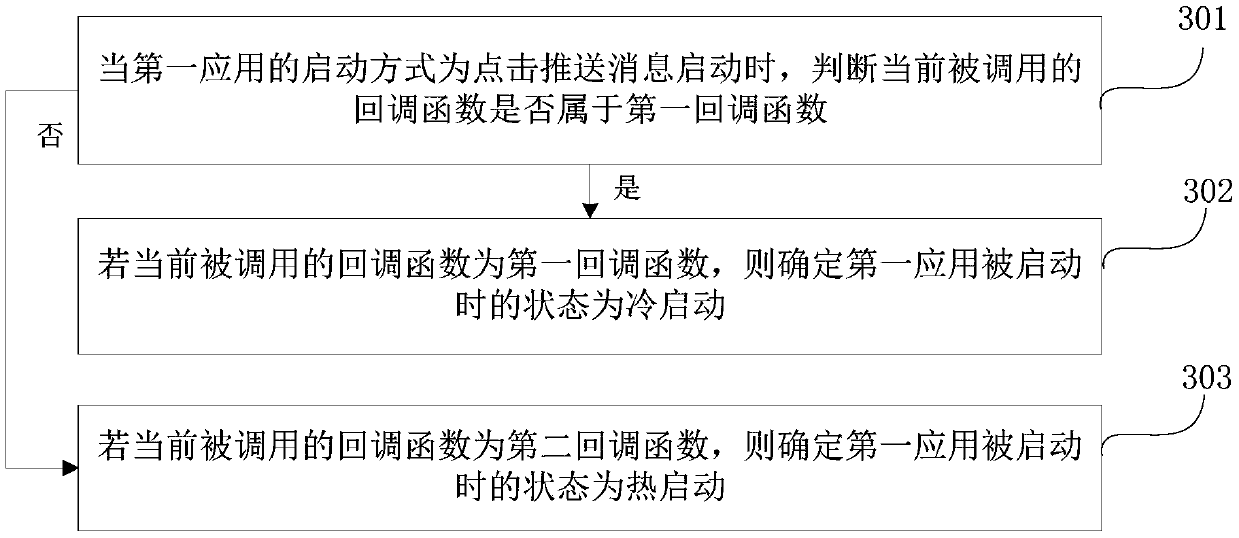
Application starting monitoring method, device and equipment
PendingCN111124795AReduce workloadShorten the development cycleHardware monitoringEnergy efficient computingCallbackSoftware engineering
The invention discloses an application starting monitoring method, device and equipment, and the method comprises the steps: obtaining a target class of a currently called setting agent function whena setting agent function corresponding to a target object of a first application is determined to be called, wherein the target object is the unique representation of the first application; monitoringeach callback function of the target class so as to obtain a current calling parameter when determining that any callback function of the target class is called; and determining a starting mode of the current first application according to the current calling parameter. According to the method and the device, the starting mode corresponding to application starting is automatically acquired according to the calling parameter corresponding to each callback function when the callback function is called, so that operations such as manual point burying by developers are effectively avoided, the whole development period is shortened, and the task load of the developers is reduced.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
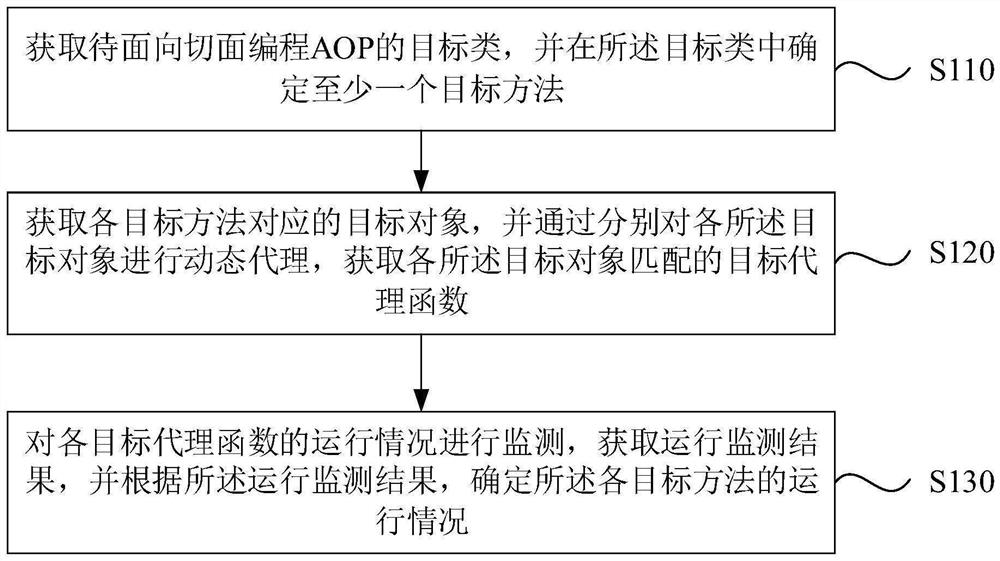
Code running monitoring method and device, equipment and storage medium
PendingCN113900896AReduce complexityReduce maintenance costsHardware monitoringEnergy efficient computingRound complexityMonitoring methods
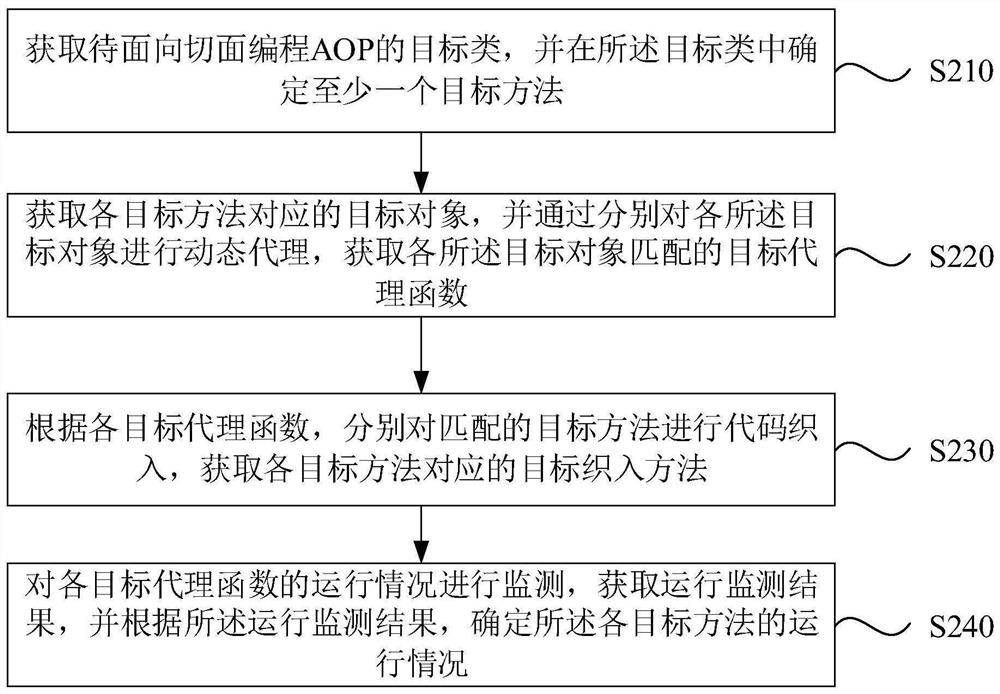
An embodiment of the invention discloses a code running monitoring method and device, equipment and a storage medium. The method comprises the steps of: acquiring a target class to be subjected to aspect oriented programming (AOP), and determining at least one target method in the target class; acquiring target objects corresponding to the target methods, and acquiring target proxy functions matched with the target objects by conducting dynamic proxy on the target objects; and monitoring the operation condition of each target proxy function to obtain an operation monitoring result, and determining the operation condition of each target method according to the operation monitoring result. According to the code running monitoring method and device provided by the embodiment of the invention, the target objects corresponding to the method to be monitored are acquired, and unified dynamic proxy is performed on the target objects, so that efficient monitoring of a large number of methods is realized, meanwhile, the code quantity and the code complexity of weaving codes required to be written during AOP are reduced, and the maintenance cost of the weaving codes is further reduced.
Owner:北京博睿宏远数据科技股份有限公司
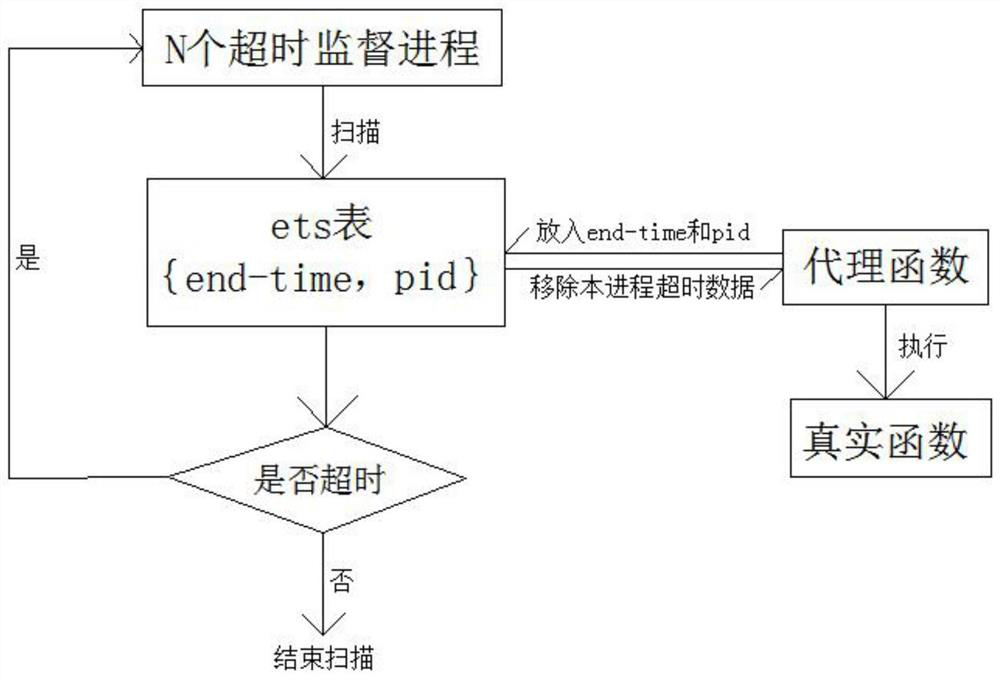
An erlang process timeout management method
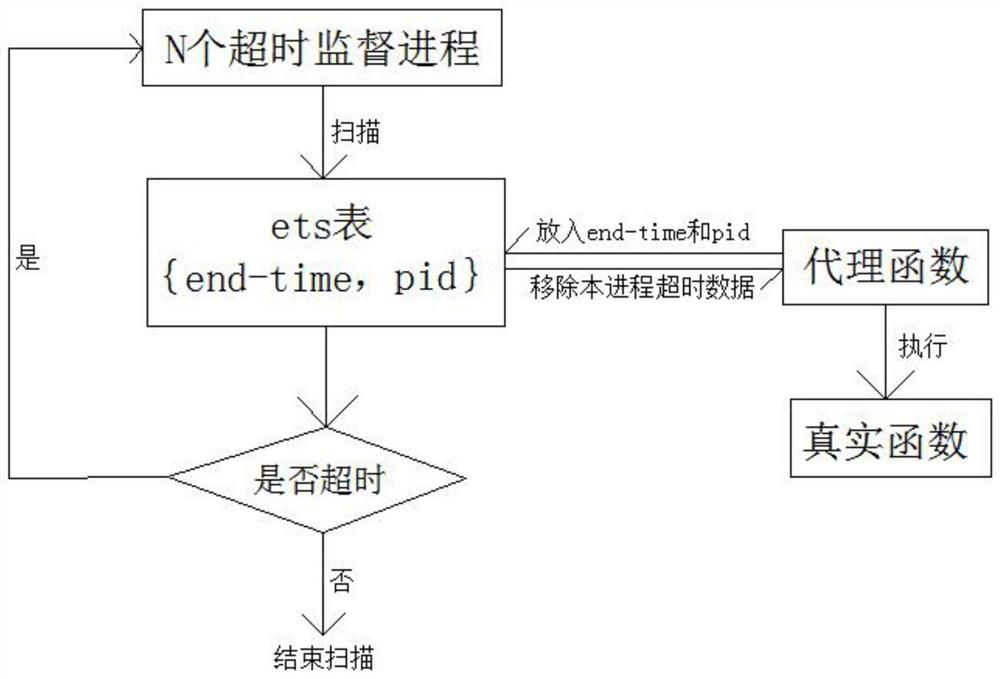
The invention discloses an Erlang process overtime management method, comprising the following steps: S1, creating N overtime supervisory processes equal to the number of CPU cores; S2, creating an ordered ets table when each overtime supervisory process starts; S3. Use the proxy function as the entrance of the Erlang process to be supervised. The proxy function randomly selects an ets table, and puts the process execution expiration time end-time and process identity pid in the ets table to form a primary key {end-time, pid }; S4, the agent function executes the real entry point function and parameters; S5, each timeout supervisory process scans out the primary key whose end-time is less than the current time in the ets table at a set interval, and executes the process identity pid corresponding to the primary key operation, and remove the primary key from the ets table; S6, the proxy function removes the timeout data of the process whose primary key is {end-time, pid}. The invention provides a process overtime monitoring method with little performance loss, no single-point bottleneck, and full use of multi-core CPUs, which avoids the devastating impact of abnormal processes such as infinite loops on system performance.
Owner:厦门极致互动网络技术股份有限公司
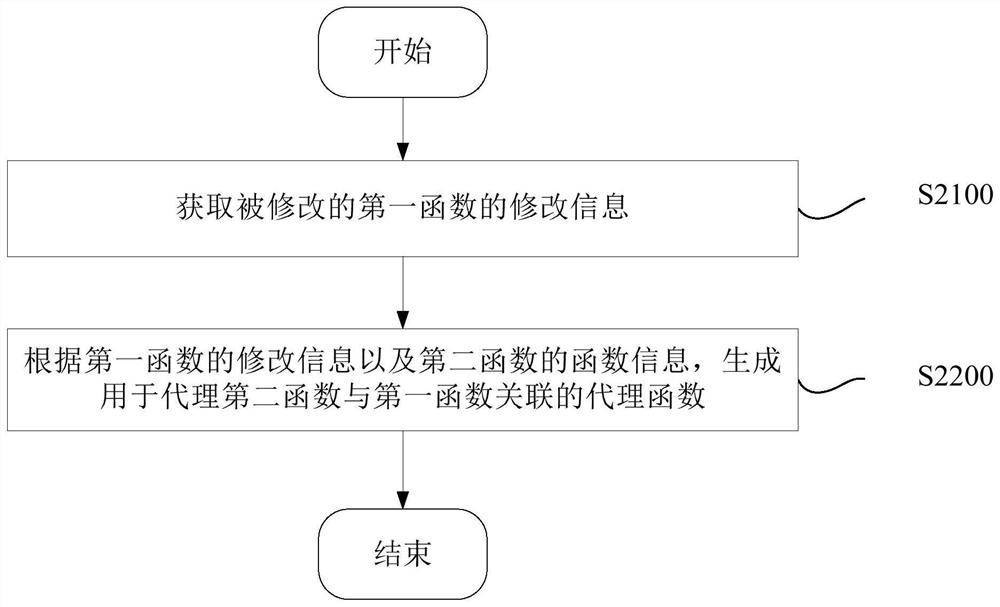
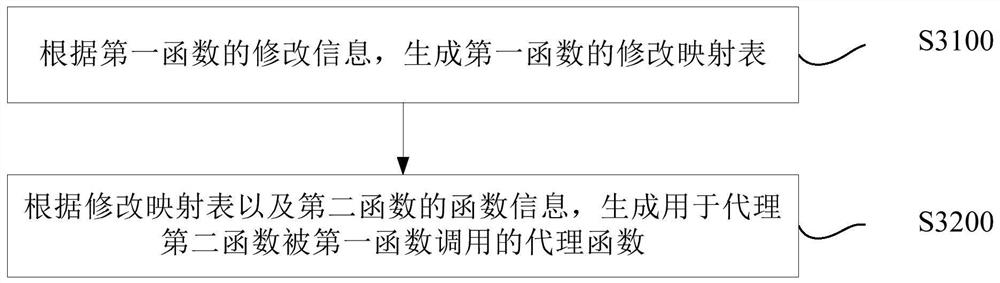
Agent method and device for dynamic library
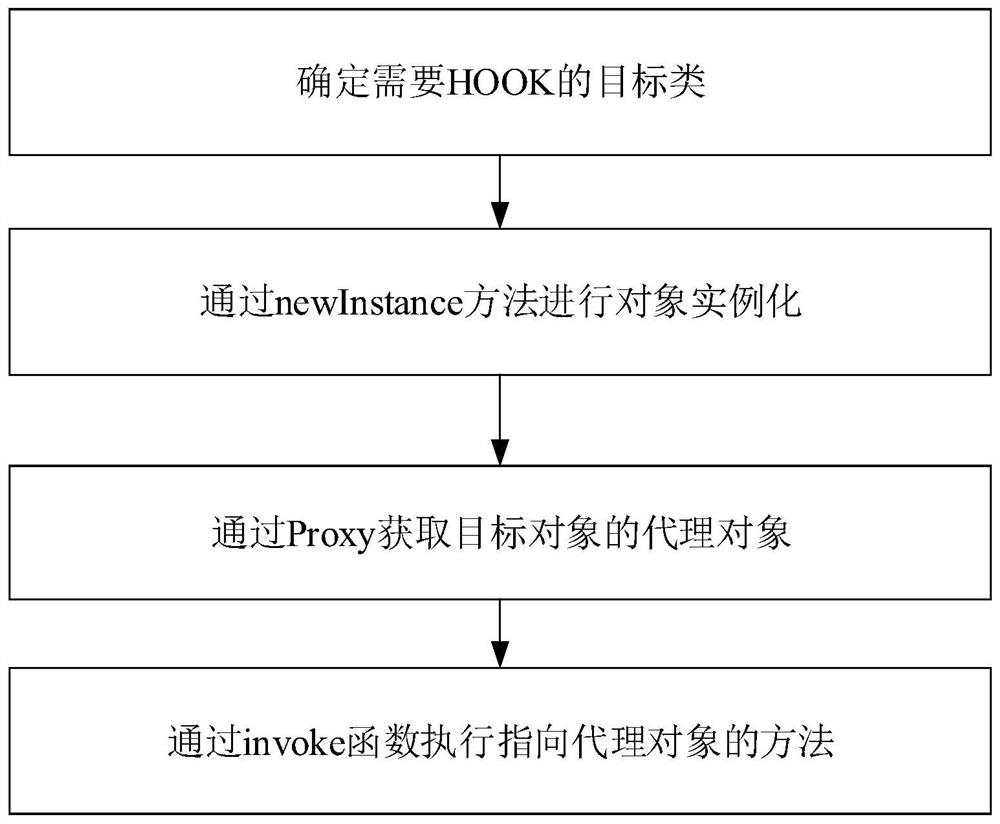
The invention discloses a dynamic library agent method and equipment. The method includes: obtaining modification information of the modified first function; and generating a proxy function used to proxy the association between the second function and the first function according to the modification information of the first function and the function information of the second function. Through the present invention, after the first function is modified, the dynamic library can work normally without modifying the second function in the dynamic library associated with the first function. Reduce the modification cost of the first function. It is especially suitable for application scenarios where the second function cannot be modified.
Owner:北京顶象技术有限公司
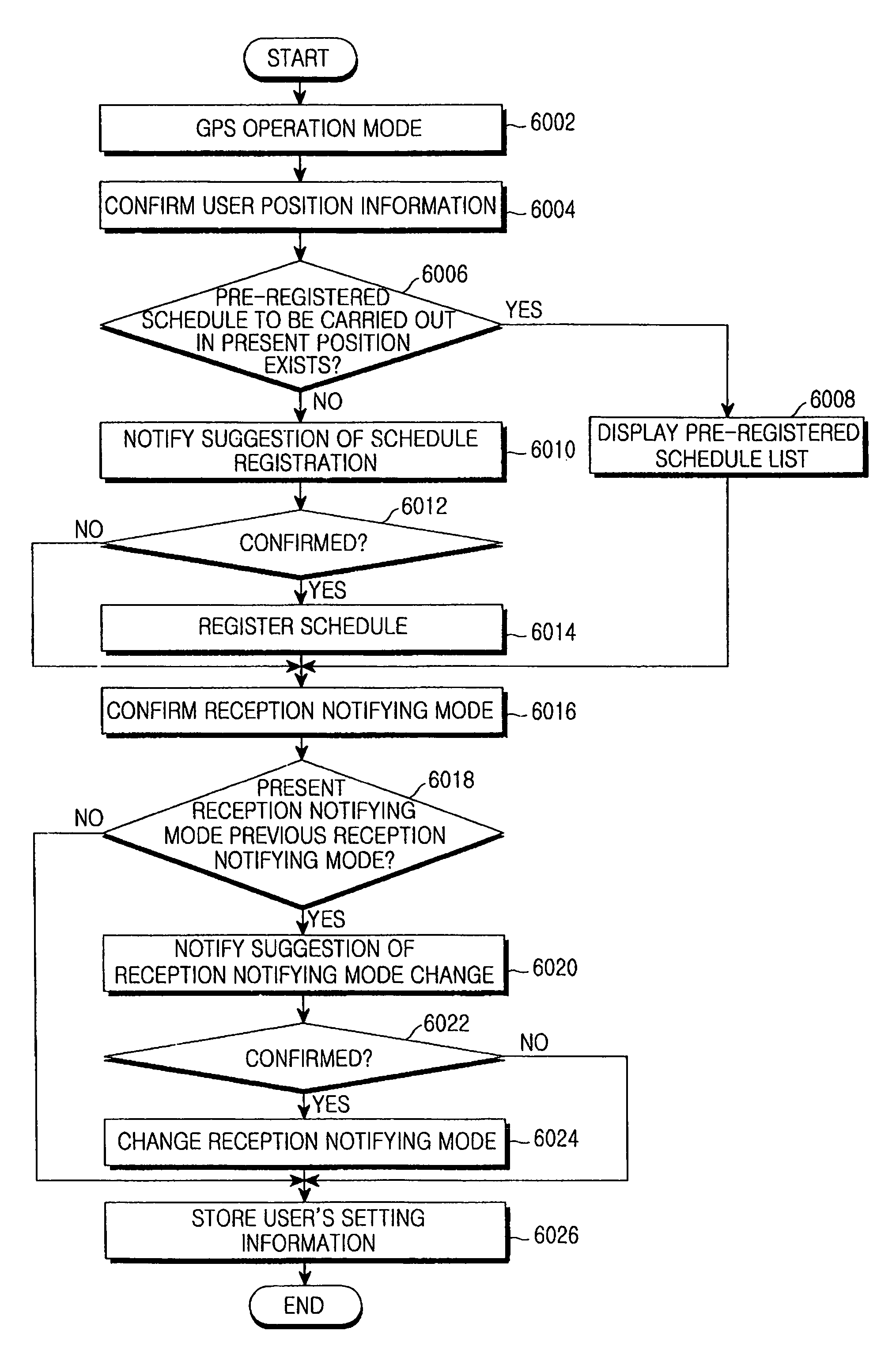
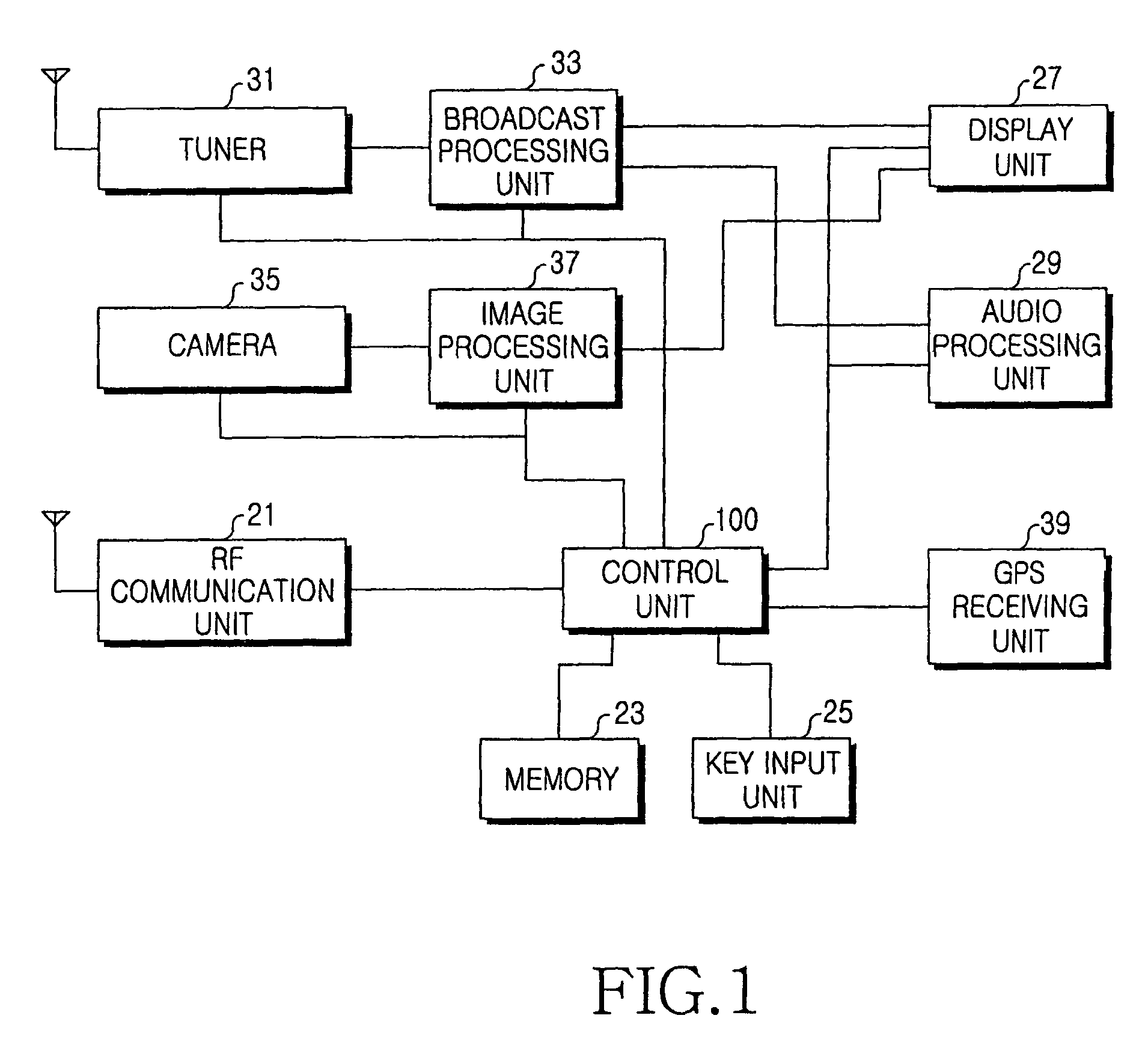
Apparatus and method for function setting event in mobile terminal according to user position information
ActiveUS8055250B2Devices with GPS signal receiverSpecial service for subscribersArtificial intelligenceUser interface
Owner:HUAWEI TECH CO LTD
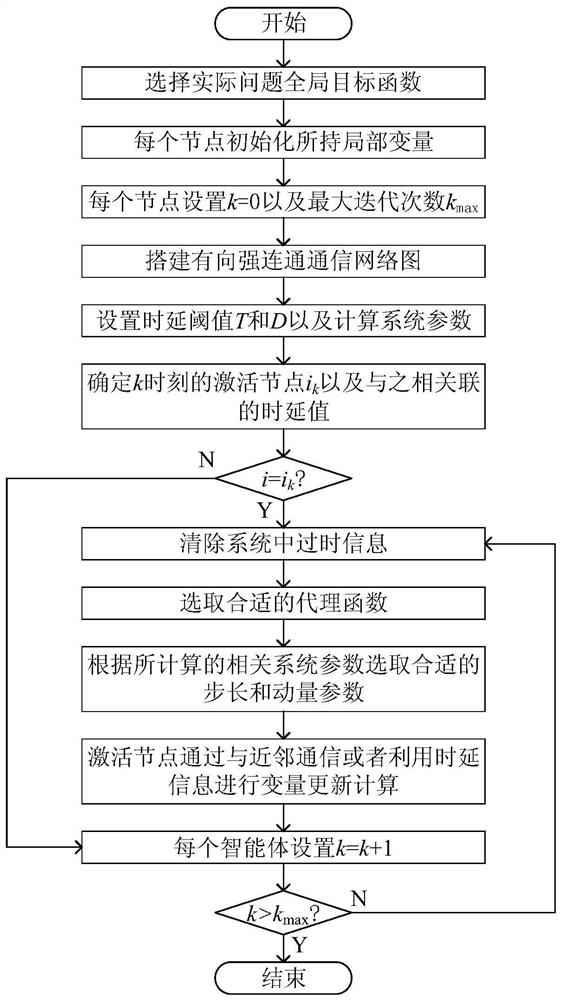
Distributed asynchronous optimization method based on continuous convex approximation
InactiveCN111865678AImprove robustnessStrong fault toleranceData switching networksTime delaysSurrogate function
The invention relates to a distributed asynchronous optimization method based on continuous convex approximation and belongs to the field of network communication. The method comprises the following steps of: S1, constructing a problem model, namely selecting a global objective function of an actual problem; S2, initializing a local variable held by each node, and setting the maximum number of iterations; S3, constructing a directed strongly-connected unbalanced source network, and adding virtual nodes on the basis of the directed strongly-connected unbalanced source network to construct an augmented network; S4, setting a time delay threshold, the number of iterations and system parameters; S5, determining the relationship between an activated node and a time delay value associated with the activation node; S6, clearing out-of-date information in the system; S7, selecting an agent function, and setting proper step length and momentum parameters; and S8, enabling the activated node tocommunicate with the neighborhood or update by utilizing a time delay value variable, and enabling a non-activated node to keep the current variable value to enter the next iterative update until thethreshold value of the number of iterations is reached. The method has high robustness and fault tolerance for an asynchronous network, and the utilization efficiency of a communication link is improved.
Owner:SOUTHWEST UNIVERSITY
Erlang process timeout management method
The invention discloses an Erlang process timeout management method. The method comprises the following steps: S1, creating N timeout supervision processes of which the number is equal to the number of cores of a CPU; S2, when each timeout supervision process is started, creating an ordered ts table; S3, using an agent function as an entrance of the Erlang process to be supervised, randomly selecting an ts table by the agent function, and putting process execution expiration time endtime and a process identity pid into the ts table to form a primary key {endtime, pid}; S4, executing a real entry point function and parameters by the agent function; S5, enabling each timeout supervision process to scan out a primary key with endtime smaller than the current time in the ts table at set intervals, executing an ending operation on a process identity pid corresponding to the primary key, and removing the primary key from the ts table; S6, enabling the proxy function to remove timeout data ofthe process with the primary key being {end-time, pid}. The invention provides a process timeout supervision method which is extremely low in performance loss, has no single-point bottleneck and makes full use of a multi-core CPU, and destructive influence of abnormal processes such as endless loop and the like on system performance is avoided.
Owner:厦门极致互动网络技术股份有限公司
Surrogate functional diagnostics test for cancer
InactiveUS20180246106A1Improve predictive performanceMedical automated diagnosisDisease diagnosisOncologySurrogate function
The present invention relates to diagnostic methods that are relevant to various cancers and which comprise improvements on a BH3 profiling diagnostic method.
Owner:EUTROPICS PHARMA
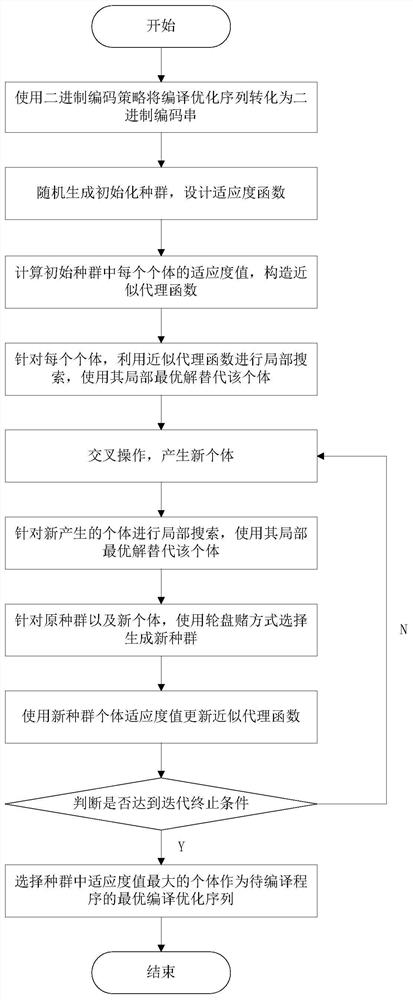
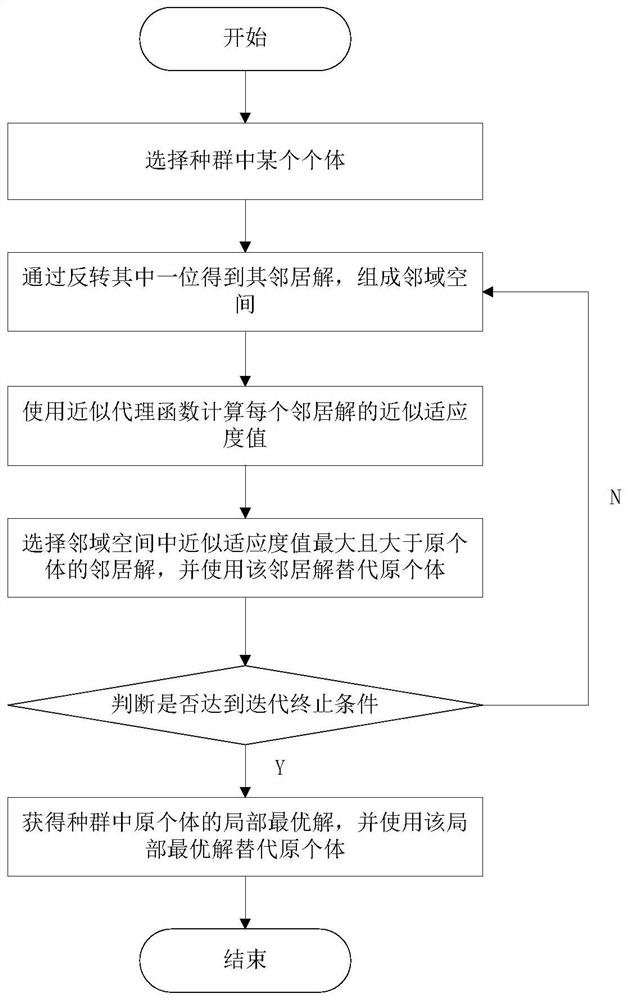
An Efficient Optimization Method for Computational Cost Constrained Problems in Compiler Optimization
ActiveCN110321116BReduce compilation timesReduce running timeCompiler constructionParser generationLocal search (optimization)Local optimum
The invention provides an efficient optimization method oriented to the calculation cost constraint problem in compilation optimization, is a solution to the calculation cost constraint problem, and belongs to the field of compiler optimization. In this method, the compiled optimization sequence is first binary coded and the fitness function is designed, and a new population is iteratively generated by crossover operation and selection operation, so as to obtain the optimal solution. In this iterative process, an approximate surrogate function is constructed using the compiled optimization sequence and the corresponding fitness value, a local search is performed for each individual in the population, and the individual is replaced with a local optimal solution, thereby improving evolutionary efficiency. The invention can effectively select the optimal compilation optimization sequence for the program to be compiled, accelerate the iteration speed, and improve the operation efficiency of the algorithm.
Owner:DALIAN UNIV OF TECH
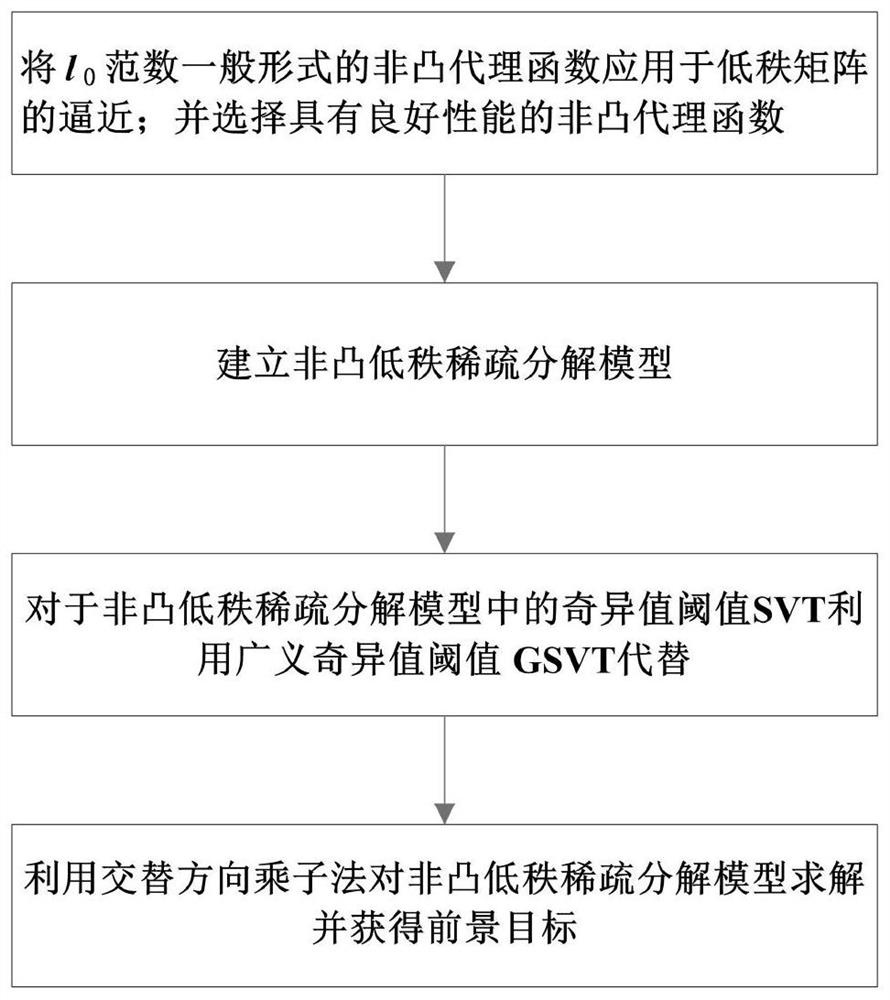
A moving object detection method based on non-convex low-rank sparse decomposition
ActiveCN110210282BAccurate portrayalSolve the problem of decreased accuracy of foreground targetsImage analysisCharacter and pattern recognitionSingular value thresholdingThresholding
The invention discloses a moving target detection method based on non-convex low-rank sparse decomposition, the steps are: 1. 0 The non-convex surrogate function in the general form of norm is applied to the approximation of low-rank matrices; and the non-convex surrogate function with good performance is selected; 2. The non-convex low-rank sparse decomposition model is established; 3. The singular value threshold SVT uses the generalized singular value The threshold GSVT is used instead; 4. Use the alternating direction multiplier method to solve the non-convex low-rank sparse decomposition model, and obtain the foreground target according to the obtained solution. The invention solves the problem that the approximate expression of the rank function in the existing method is inaccurate, resulting in that the recovered background is not clean enough and the accuracy of the extracted foreground target decreases.
Owner:NANJING UNIV OF POSTS & TELECOMM
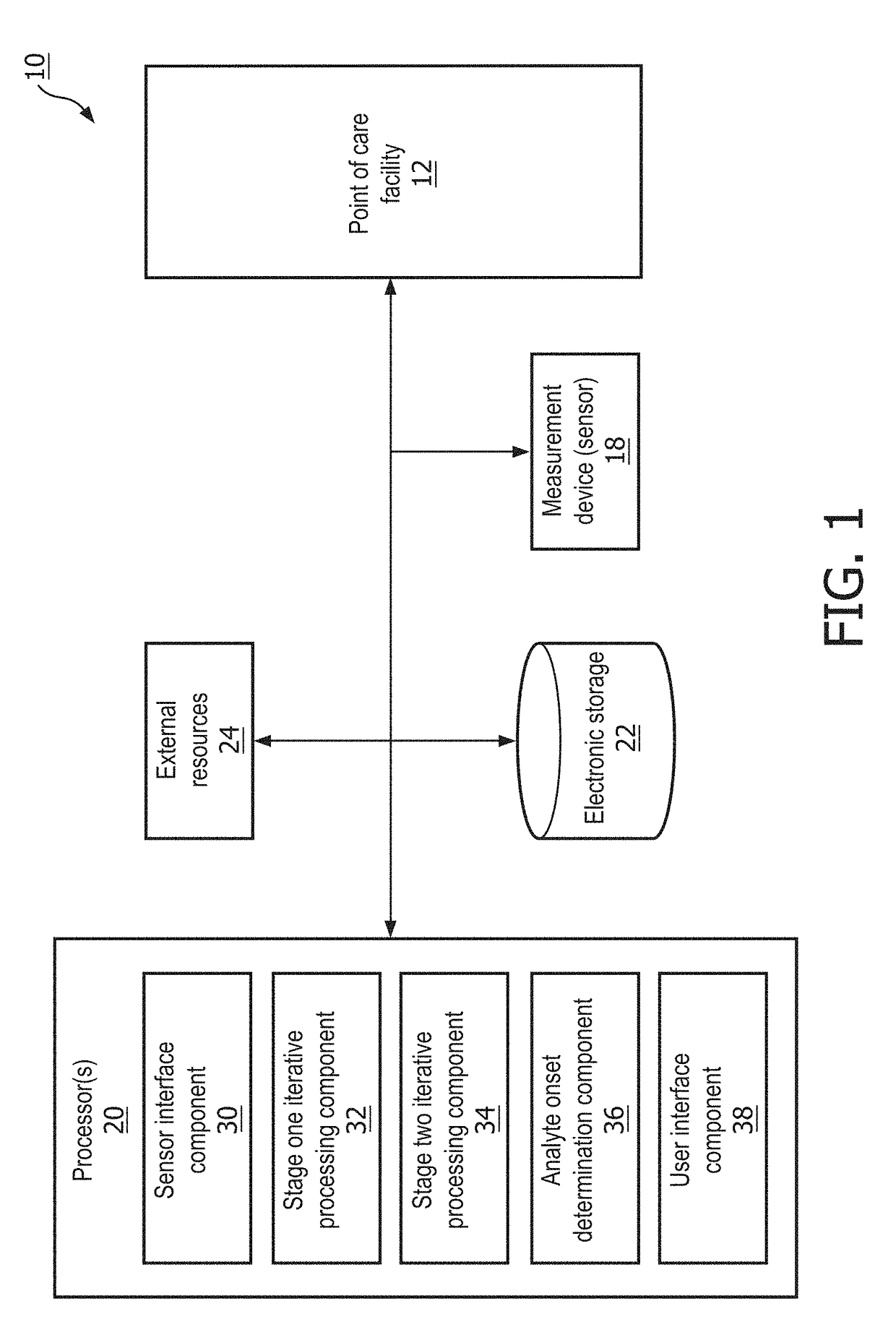
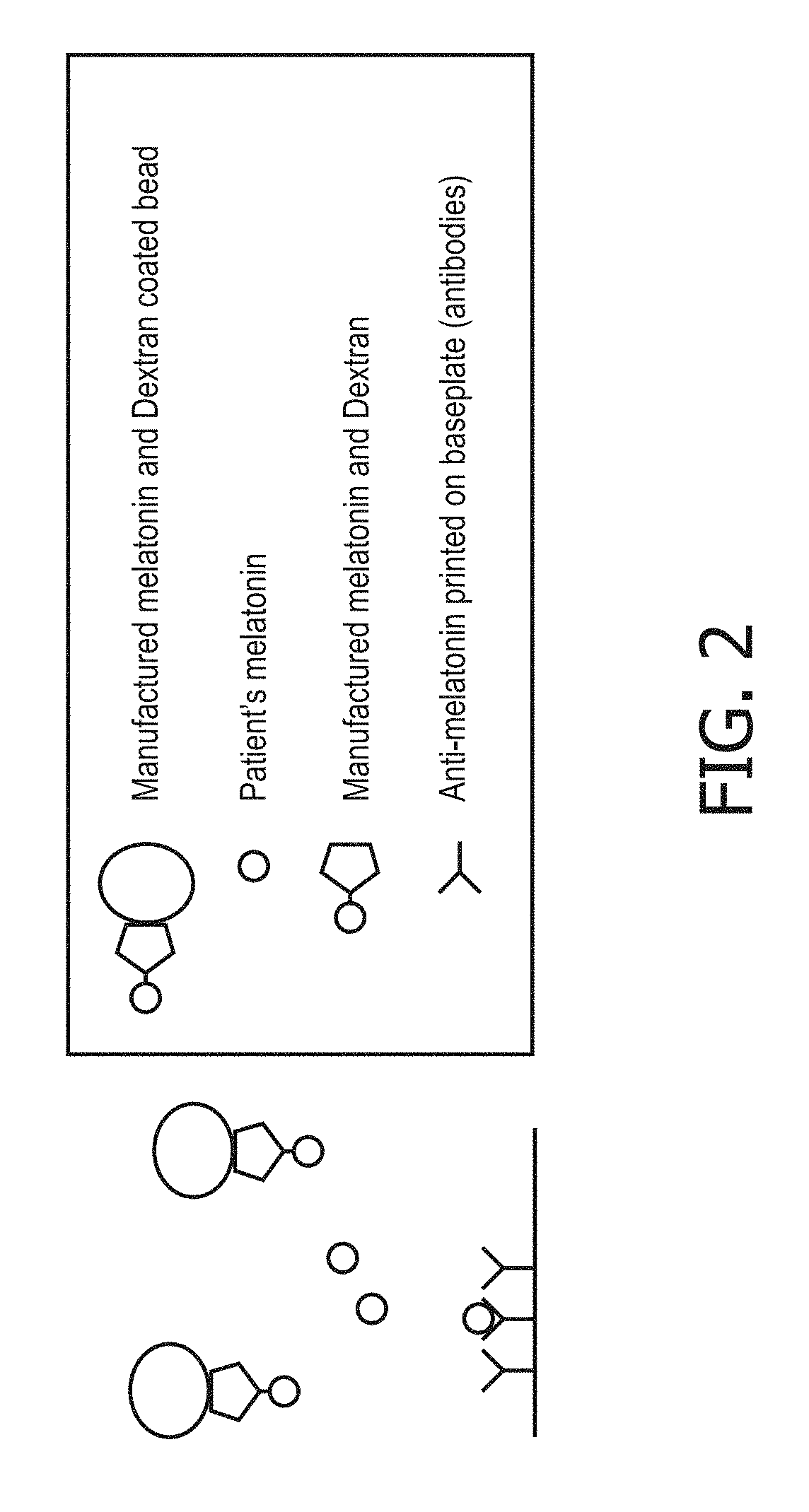
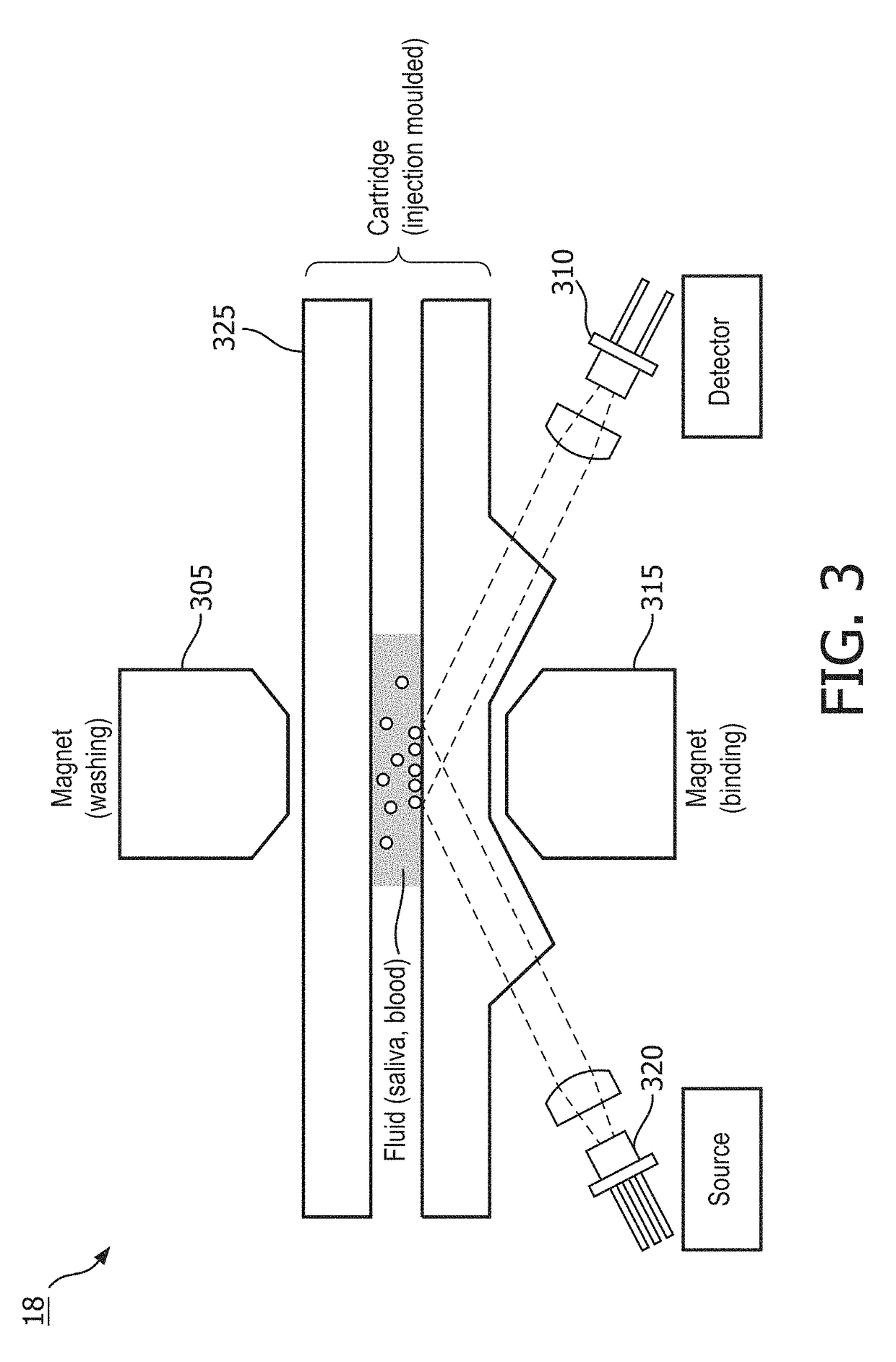
Determining onset of a sleep-related analyte
Disclosed is a method for determining onset of a sleep-related analyte. The method includes: obtaining first surrogate measurement(s) of a sleep-related analyte based on signal(s) obtained via sensor(s) during a first time period of observation; obtaining second surrogate measurement(s) of the sleep-related analyte based on signal(s) obtained via sensor(s) during a second time period of observation; determining a first surrogate function or value based on the first surrogate measurement(s) and a second surrogate function or value based on the second surrogate measurement(s); and predicting an onset of the sleep-related analyte for a first individual based on the first surrogate function or value and the second surrogate function or value such that the prediction of the onset of the sleep-related analyte is performed without determining an absolute concentration value for the sleep-related analyte.
Owner:KONINKLJIJKE PHILIPS NV
A data calling method and data calling device
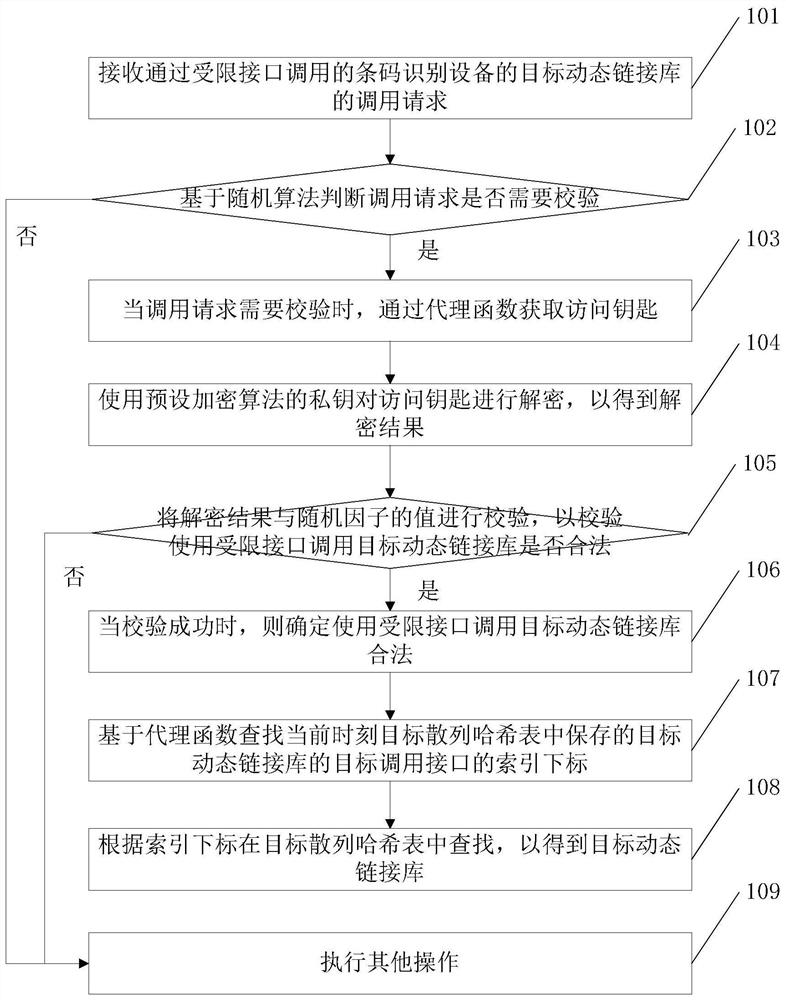
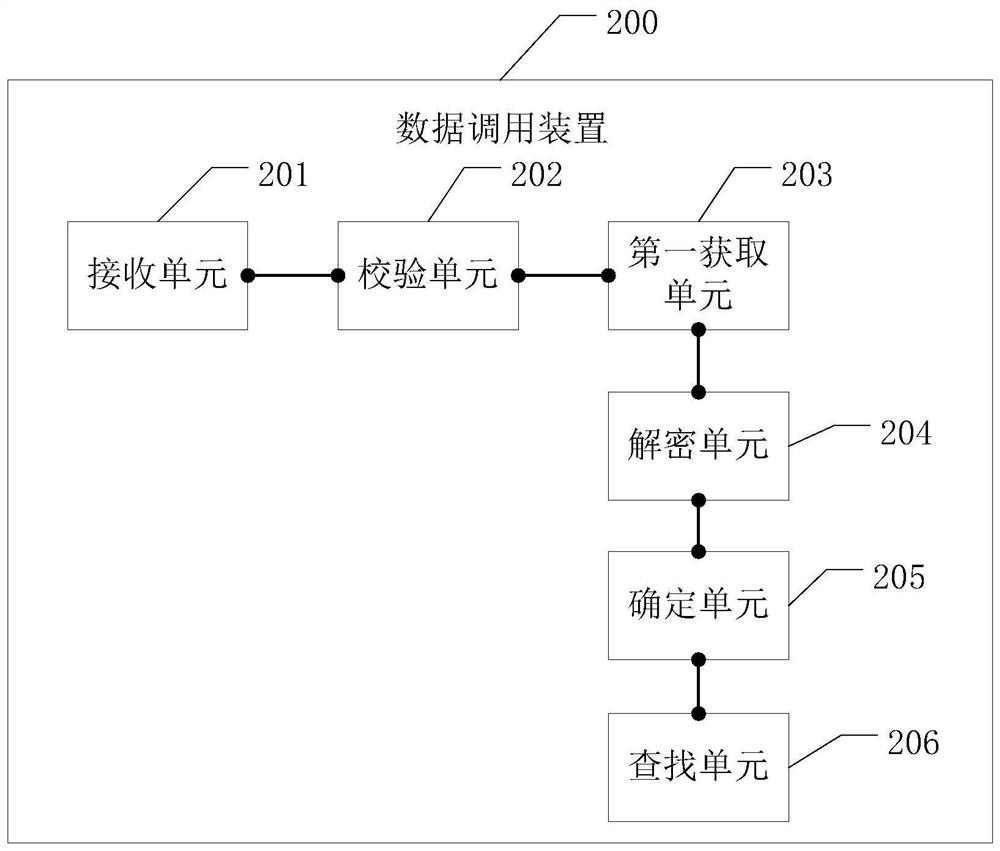
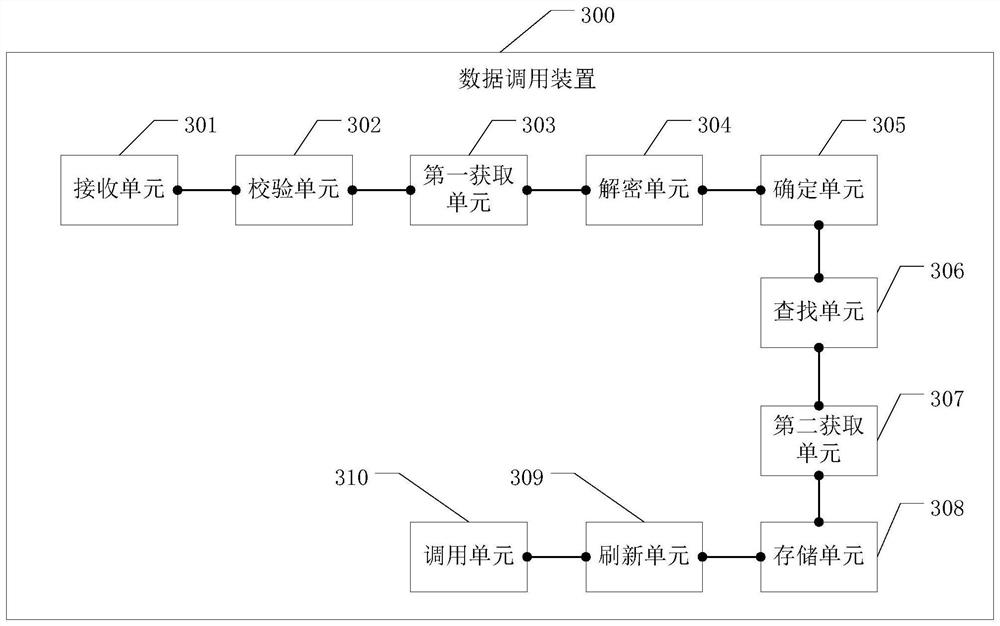
ActiveCN108628611BInseparable strong couplingIncrease the difficultyDecompilation/disassemblySecuring communicationStochastic algorithmsBarcode
The embodiment of the invention discloses a data calling method and a data calling device, which can increase the difficulty of cracking the core dynamic link library. The method includes: receiving a call request for calling a target dynamic link library of a barcode recognition device through a restricted interface; judging whether the call request needs to be verified based on a random algorithm; when the call request needs to be verified, obtaining an access key through a proxy function; Set the private key of the encryption algorithm to decrypt the access key to obtain the decryption result; verify the decryption result and the value of the random factor to verify whether it is legal to use the restricted interface to call the target dynamic link library; when the verification is successful, then It is determined that it is legal to use the restricted interface to call the target dynamic link library; based on the proxy function, the index subscript of the target call interface address of the target dynamic link library stored in the target hash table at the current moment is searched; Look up in the column hash table to get the target dynamic link library.
Owner:WUXI IDATATECHNOLOGYCOMPANYLTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com