User state verification method in service grid
A user state, grid technology, applied in the field of distributed systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
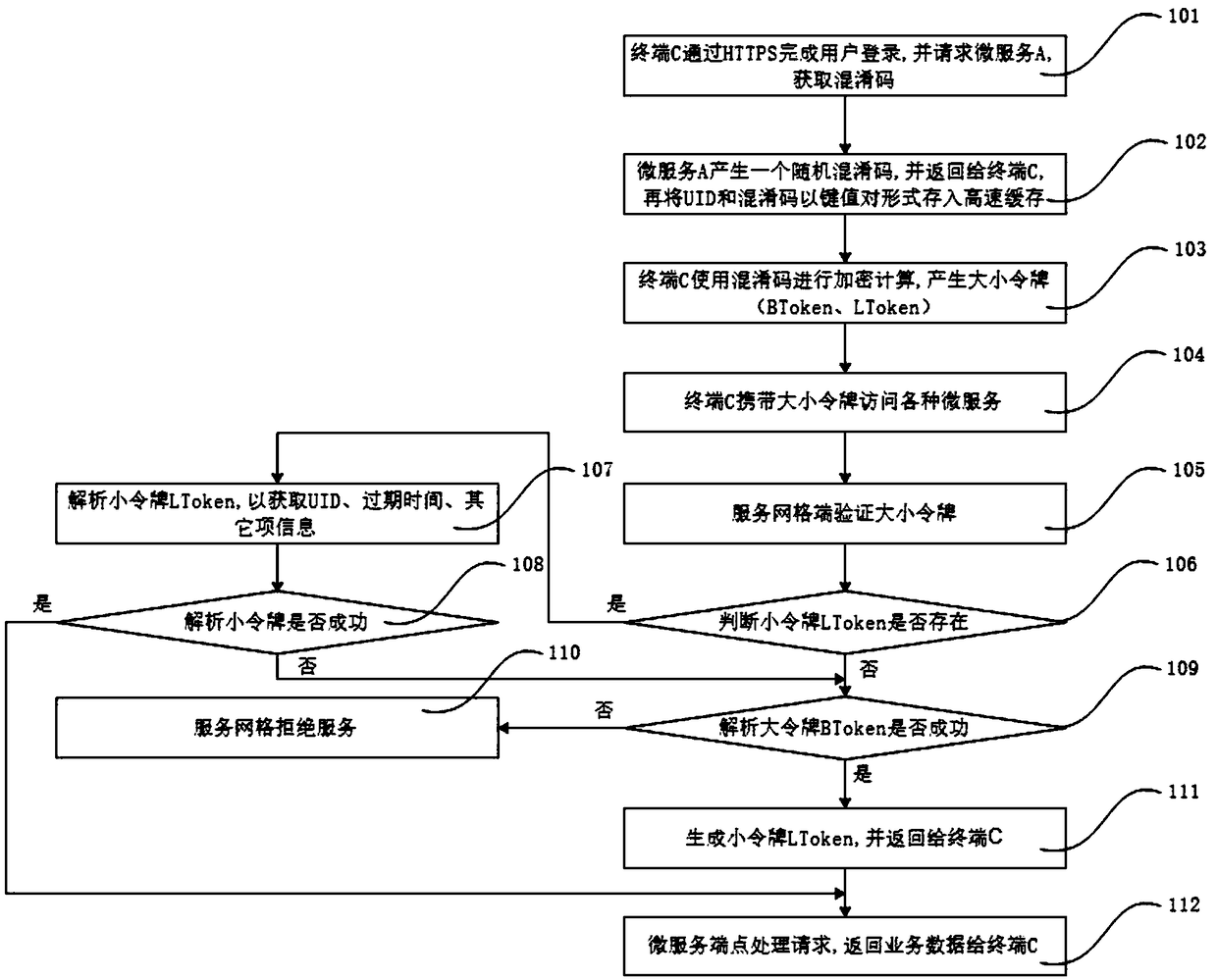
[0030] Such as figure 1 As shown, a schematic flow diagram of a method for verifying user status in a service grid, the method can be applied to a microservice architecture, and can be applied to data centers such as a service grid platform. The method mainly includes the following steps:
[0031] In step 101, terminal C completes user login through HTTPS, and requests microservice A to obtain an obfuscated code.
[0032] For user login, a safer implementation is to transmit sensitive information of the user through the HTTPS protocol to complete the verification.
[0033] The microservice A is a microservice dedicated to providing obfuscated codes in the service grid.
[0034] In specific implementation, terminal C may initiate a registration / login request to the login service in the service grid to complete the user's registration and login verification; it may also be that terminal C initiates a registration / login request to the single sign-on server SSO to complete the us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com