Domain name resolution method and domain name resolution device
A technology for domain name resolution and encrypted communication, applied in the field of domain name resolution methods and devices, can solve the problems of domain name access failure, access error, domain name hijacking, etc., and achieve the effect of improving security and avoiding the risk of domain name hijacking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
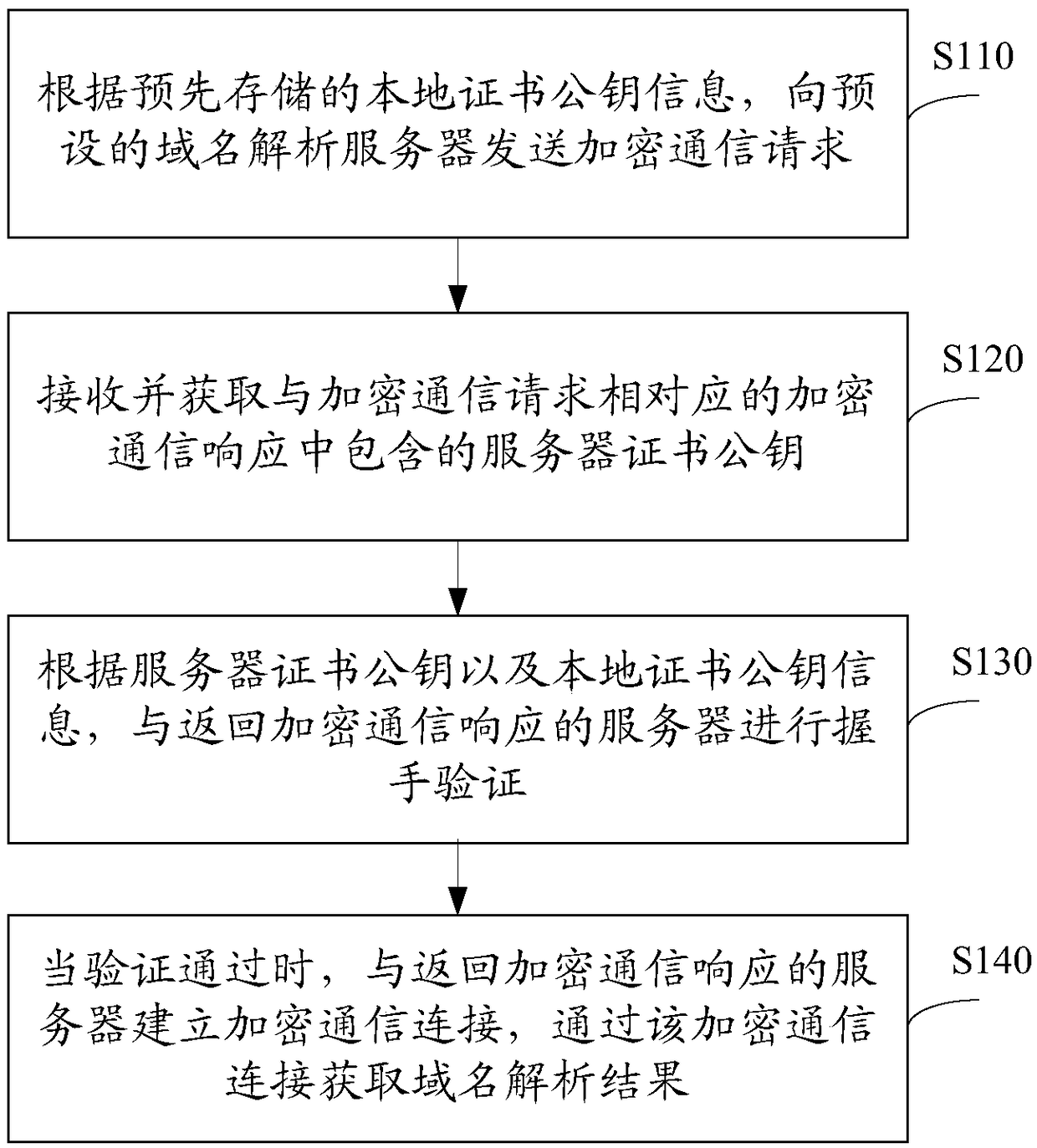
[0067] In this example, the handshake verification between the client and the server is mainly based on the random numbers generated by both parties. The client only judges the integrity and legality of the certificate returned by the server, and does not verify whether the server's certificate public key is correct. Specifically include the following steps:
[0068] Step 1: The client generates a first random number, that is, the random number R1, and sends the random number R1 to the server through an encrypted communication request.
[0069] Step 2: The server obtains R1 according to the received encrypted communication request, saves R1 for subsequent use; and generates a second random number, that is, random number R2, and encrypts R2 and the server certificate (including the public key in the certificate) The communication response is sent to the client.
[0070] Step 3: After the client receives the encrypted communication response, it checks the server certificate con...
example 2
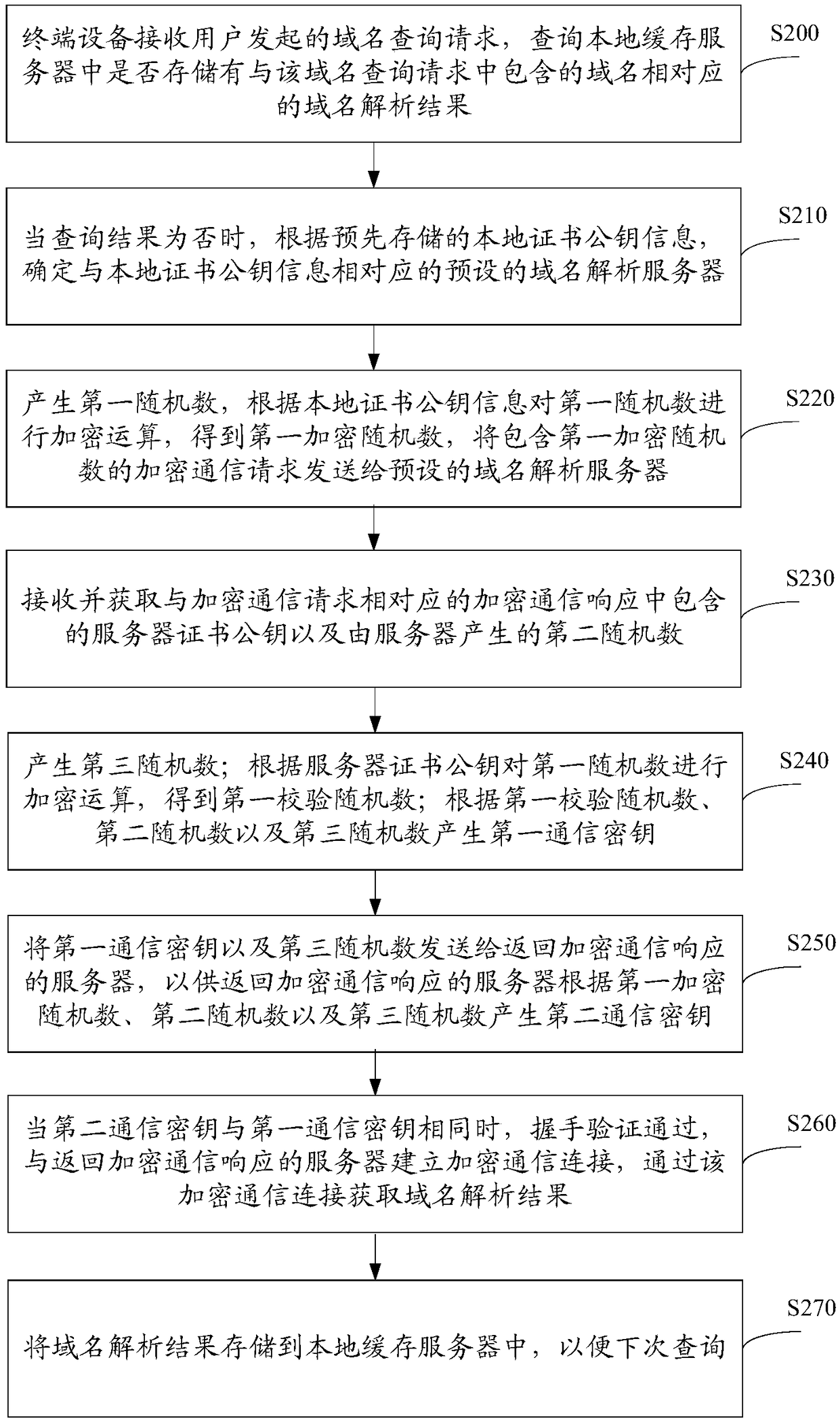
[0078] In this example, the client pre-stores the hash value (Hash value) Hp of the server certificate public key of the anti-hijacking DNS server (that is, the local certificate public key information mentioned above) in the application program in a hard-coded manner . Correspondingly, the client and the server not only realize the handshake verification based on the random numbers generated by both parties, but also further verify the identity of the server according to the locally stored certificate public key, which specifically includes the following steps:
[0079] Step 1: The client generates the first random number, that is, the random number R1, and then encrypts it with the Hash value Hp of the public key of the server certificate stored in a hard-coded manner, and obtains the ciphertext R1' corresponding to R1 (that is, the first encrypted random number number). In this embodiment, R1'=SHA256(R1||Hp), and the first encrypted random number R1' is sent to the server ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com