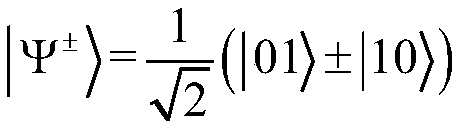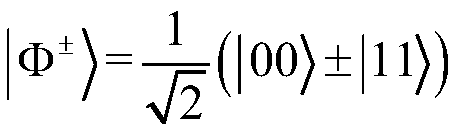Quantum secure direct communication method based on Omega state and ultra dense coding
A technology of secure direct communication and ultra-dense encoding, applied in the field of quantum secure direct communication based on Omega state and ultra-dense encoding, can solve problems such as poor efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0008] 1. The communication protocol process between the receiver and the sender is as follows:
[0009] The four Bell states are:
[0010]
[0011]
[0012] The Omega state mentioned in the article is:
[0013]
[0014] in B 1 >∈{|Ψ ± >,|Φ ± >}, so there are 16 Omega states that can be generated from Bell states. In this paper, we assume that |B 0 >=|Φ + >,|B 0 >=|Φ - >. We can use |Ω> to enhance the efficiency of intrusion detection.
[0015] Assume four unitary operations {U 0 ,U 1 ,U 2 ,U 3} After operating on one of the particles in the Bell state, the Bell state |Φ + > Converted to |Φ + >,|Ψ + >,|Ψ - >,|Φ - >. Then the four unitary operations can be agreed as 00, 01, 11, 10 respectively. By analyzing the change of the Bell state at the corresponding position when sending and receiving, Bob can analyze what type of unitary operation Alice uses, so that Alice and Bob complete the transmission of two classical bits by transmitting one qubit. Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com