Method and system for encryption and authorization of algorithm library
An authorization system and algorithm library technology, which is applied in transmission systems, digital transmission systems, user identity/authority verification, etc., can solve problems such as difficulty in setting charging prices, loss of algorithm suppliers, and false authorization quantity, etc., to achieve transaction security Guarantee, convenient cost statistics, convenient authorization management effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
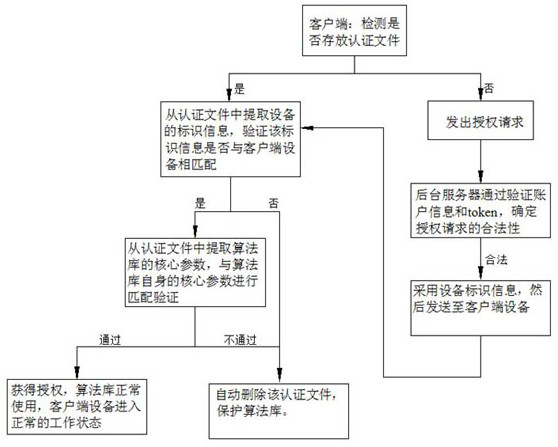
[0029] see figure 1 , an algorithm library encryption authorization method, the algorithm library is installed on a client device, and when the client device enables the algorithm library, the following steps are performed:
[0030] Detect whether the authentication file is stored in the client device, if there is, execute the decoding step; if not, send an authorization request: collect the identification information of the client device, and then together with the account information and token of the client device (Chinese translation: order card) to the background server, the background server verifies the account information and token to determine the legitimacy of the authorization request, after the verification is passed, the core parameters corresponding to the algorithm library are called from the background server, and then combined with the device identification information to create an authentication file , and then sent to the client device; the client device save...
Embodiment 2
[0041] An encryption authorization system for an algorithm library, including a client device and a background server, the client device is loaded with an algorithm library;
[0042] see figure 1 , when the client device enables the algorithm library, it detects whether the authentication file is stored in the client device, and if so, decodes it; if not, sends an authorization request: collect the identification information of the client device, and then together with the client device account The information and the token are sent to the backend server together; the backend server confirms the legitimacy of the authorization request by verifying the account information and the token, and after the verification is passed, calls the core parameters corresponding to the algorithm library from the backend server, and then combines the device identification information making an authentication file, and then sending it to the client device; the client device saves the received au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com