Mobile sensor network intrusion detection and self-adaptive response method
A technology of network intrusion detection and mobile sensors, which is applied in transmission systems, wireless communications, electrical components, etc., can solve problems such as network intrusion attacks that cannot be solved, and achieve the effect of effective intrusion response
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0030] Specific implementation mode 1: The specific process of a mobile sensor network intrusion detection and adaptive response method in this implementation mode is as follows:
[0031] Step 1. Monitor the network and collect data;
[0032] Step 2, processing the collected data, and storing the processed data in the initial configuration file (ITP);
[0033] Step 3. Based on Step 2, the management node uses the parameters in the network characteristic matrix to identify intrusions in the network by using an abnormality-based intrusion detection method;
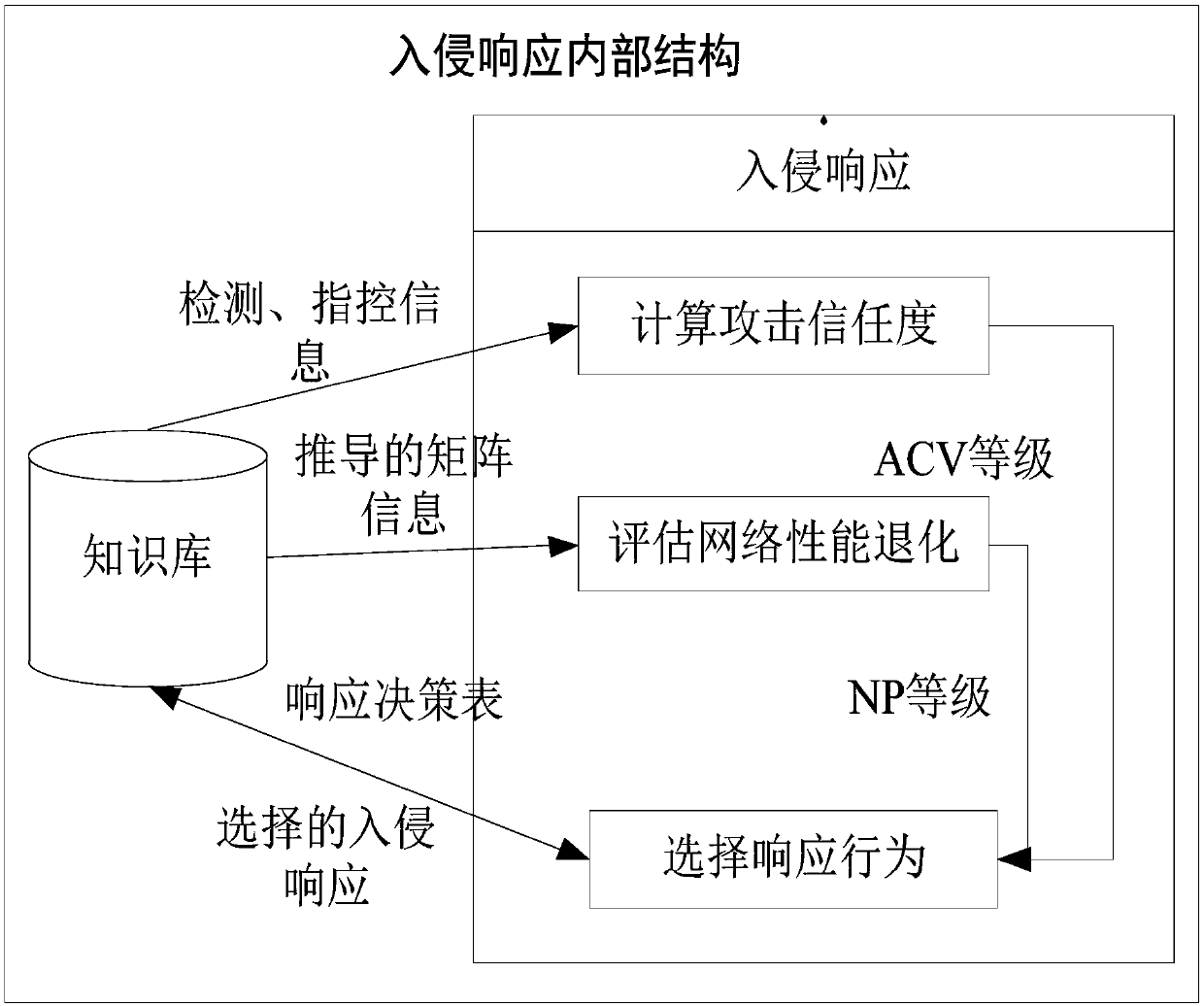
[0034] Step 4. Calculate the attack trust value (ACV) and network performance degradation value (NP) based on step 3; establish an adaptive intrusion response behavior list based on the attack trust value (ACV) and network performance degradation value (NP); Establish a decision table based on the severity level, network performance degradation level, and adaptive intrusion response behavior list, and select an intrusion re...
specific Embodiment approach 2
[0041] Embodiment 2: The difference between this embodiment and Embodiment 1 is that in the first step, the network is monitored and data is collected; the specific process is:
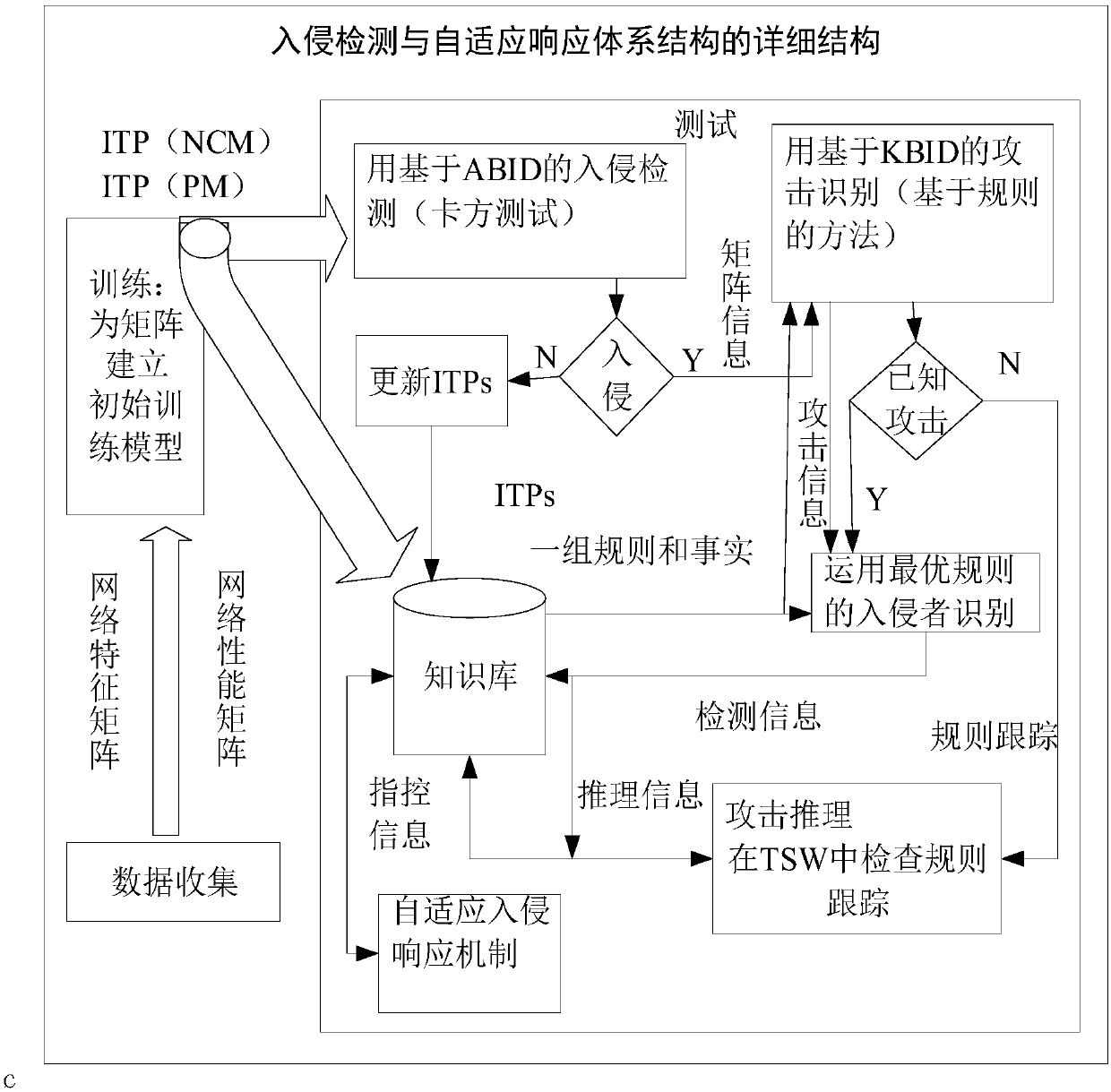
[0042] figure 1 For the architecture of IDARM, the first step is to carry out network monitoring and data collection. In order to realize intrusion detection and provide prevention and protection during the life cycle of the entire network, IDARM will periodically collect data in the network to monitor the entire network.
[0043] Collecting data means that after each interval, cluster heads collect data from cluster nodes in their virtual clusters; these data will be stored in the form of a matrix in the network feature matrix and performance matrix;
[0044] The cluster head reports the network feature matrix and performance matrix to the management node;
[0045]Wherein the network characteristic matrix is made up of 7 parameters of routing reply, routing request, routing error, time-to-live v...
specific Embodiment approach 3
[0056] Specific embodiment three: the difference between this embodiment and specific embodiment one or two is that the collected data is processed in the step two, and the processed data is stored in the initial configuration file (ITP); the specific process is :
[0057] Cluster heads continuously collect data from cluster nodes in their virtual clusters; these data will be stored in the network feature matrix and performance matrix in the form of a matrix; the cluster head will update the network feature matrix and performance The matrix reports to the management node;
[0058] The expected value of the network feature matrix is given by express, is a set of random variables representing the network feature matrix;
[0059] Where a represents the ath time interval, b represents the bth parameter of the network feature matrix, c represents the number of random variables in the bth parameter of the network feature matrix, 1≤c≤M, M is the network in the ath time interva...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com