A mobile sensor network intrusion detection and adaptive response method
A technology of network intrusion detection and mobile sensors, applied in transmission systems, electrical components, security devices, etc., can solve problems such as network intrusion attacks that cannot be solved
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0030]DETAILED DESCRIPTION OF THE INVENTION First: The specific process of moving sensor network intrusion detection and adaptive response method is:
[0031]Step 1. Monitor the network and collect data;
[0032]Step 2, the collected data is processed, and the processed data is stored in the initial configuration file (ITP);
[0033]Step 3, based on step two, management nodes use the parameters in the network feature matrix, adopt an invasion in the network based on abnormal intrusion detection method;
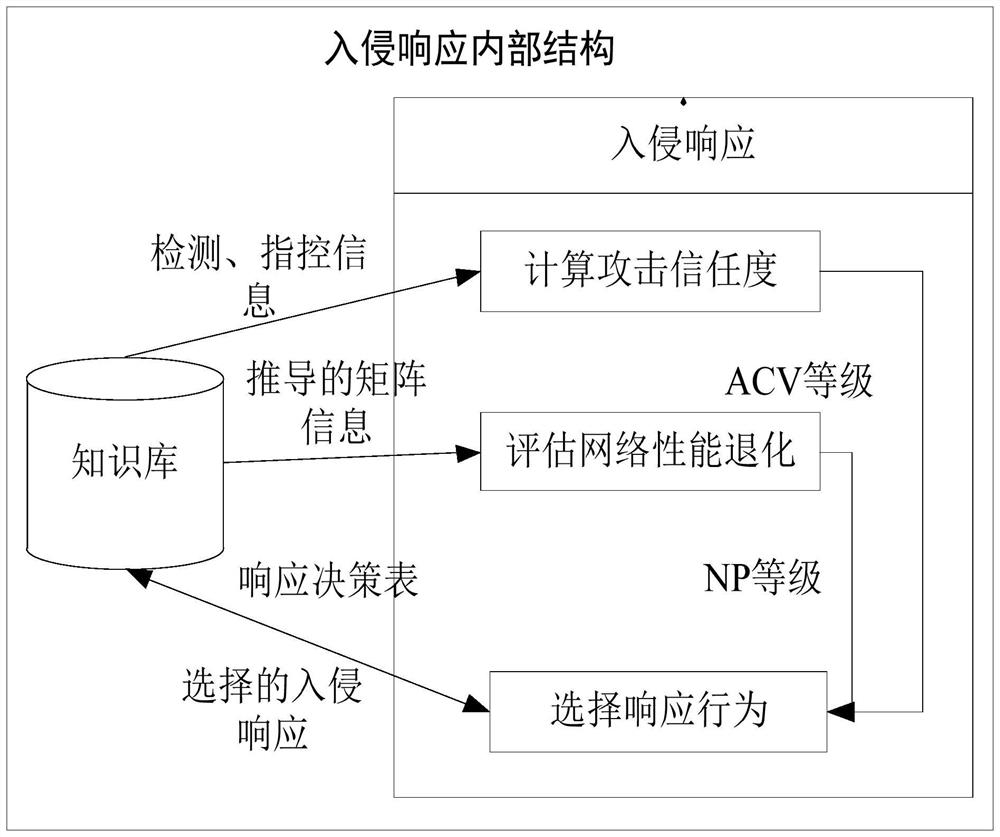
[0034]Step 4. Based on step three to calculate the attack trust value (ACV) and network performance degradation values (NP); establish an adaptive intrusion response behavior list according to the attack trust value (ACV) and network performance degradation value (NP); based on attack trust The degree level, network performance degradation level and adaptive intrusion response behavior list establish a decision table, select intrusion response based on the established decision table. Such asf...
specific Embodiment approach 2
[0041]DETAILED DESCRIPTION OF THE INVENTION Different from the specific embodiment, the steps are monitored and collected in the steps; the specific process is:
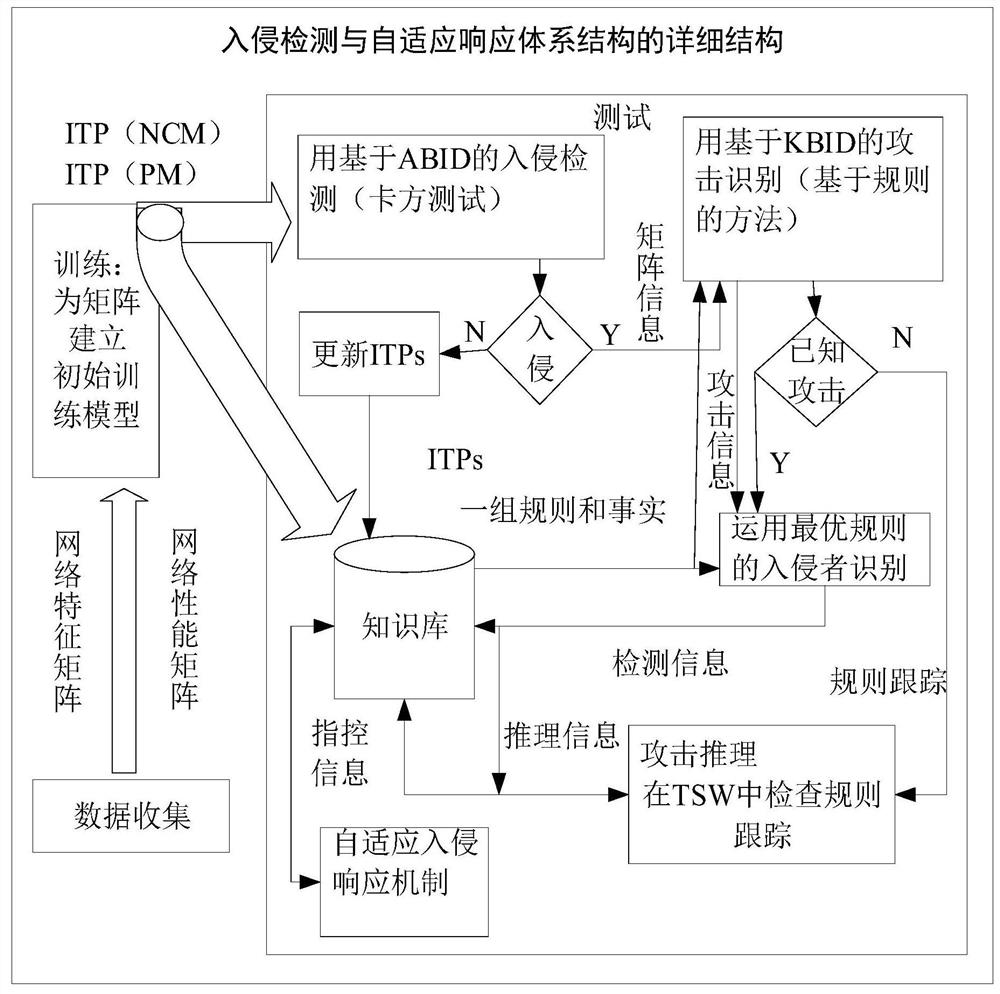
[0042]figure 1 The first step is to collect network monitoring and data collection. Idarm provides intrusion detection and protection in the life cycle of the entire network, which will periodically collect data in the network to achieve monitoring of the entire network.
[0043]Collecting data refers to the cluster header data from the cluster node from their virtual cluster; these data are stored in the form of a web feature matrix and performance matrix;
[0044]The cluster head reports the network feature matrix and performance matrix to the management node;
[0045]The network feature matrix is composed of sequences of routing reply, routing requests, routing errors, survival values, routing request sources, routing replies, and routing request destination sequences; (detects directly with data);
[0046]The network feature matrix...
specific Embodiment approach 3
[0056]DETAILED DESCRIPTION OF THE INVENTION The present embodiment is different from that of the specific embodiment, and the collected data is processed in the second step, which is stored in the initial configuration file (ITP); the specific process is :
[0057]The cluster head is constantly collecting data from the cluster node from their virtual clusters; these data is stored in the form of a matrix in the network feature matrix and performance matrix; the cluster head will use the network feature matrix and performance within a fixed time interval. Matrix report to the management node;
[0058]The expected value of the network feature matrix isIndicated thatIt is a set of random variables representing the network feature matrix;
[0059]Where A represents the first time interval, b represents the number B parameter of the network feature matrix, and the number of random variables in the third parameters of the network feature matrix, 1 ≤ C ≤ M, M is in the first time interval network T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com