Data desensitization processing method and device and electronic equipment
A technology of data desensitization and processing method, applied in the field of devices and electronic equipment, data desensitization processing method, can solve problems such as economic loss and enterprise trust crisis, and achieve the effect of solving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
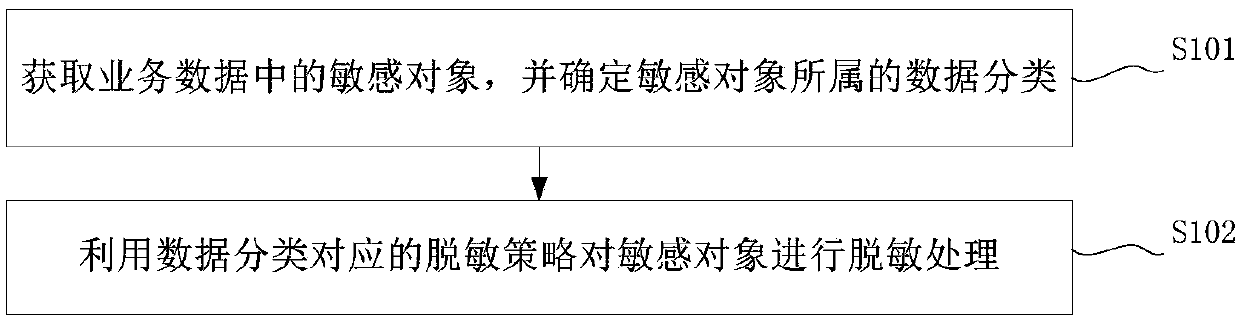
[0053] The embodiment of this application provides a data desensitization processing method, such as figure 1 As shown, the method includes: step S101 and step S102.
[0054] Wherein, step S101, acquire sensitive objects in business data, and determine the data category to which the sensitive objects belong.
[0055] For this embodiment of the application, the sensitive data refers to the data that needs to be anti-disclosure processing so as to prevent others from directly viewing it.
[0056] In practical applications, business data can be customer information, specifically including customer name, contact information, company account number and other information with commercial value; or, business data can also be other personal information, specifically including mobile phone number, name, ID card Key information such as number, residential address, etc.
[0057]Specifically, the method provided by the embodiment of the present application can be applied to testing tools...
Embodiment 2
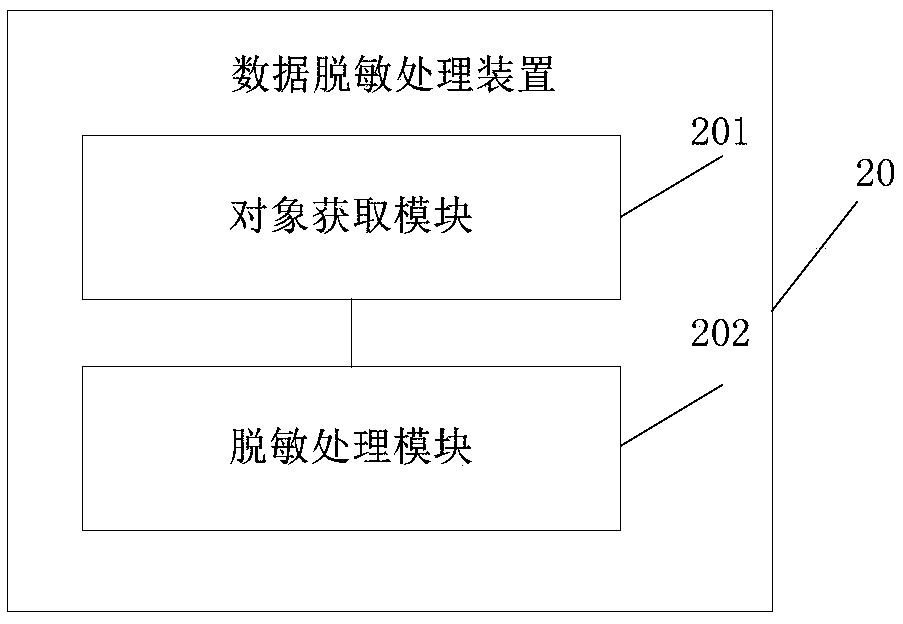
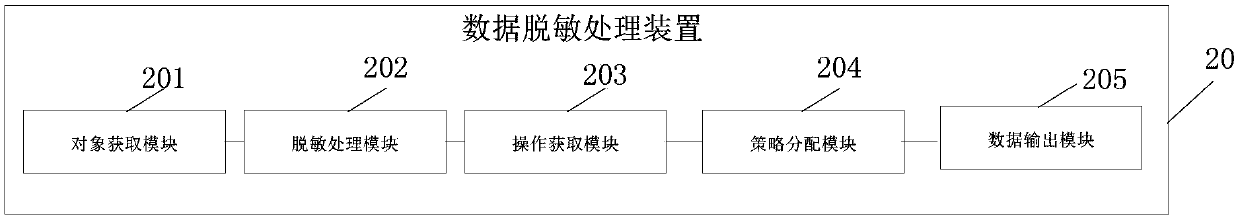
[0080] The embodiment of the present application provides a data desensitization processing device, such as figure 2 As shown, the data desensitization processing apparatus 20 may include: an object acquisition module 201 and a desensitization processing module 202 .
[0081] Wherein, the object obtaining module 201 is used to obtain sensitive objects in business data, and determine the data category to which the sensitive objects belong;
[0082] The desensitization processing module 202 is configured to desensitize sensitive objects using a desensitization policy corresponding to the data classification.
[0083] For the embodiment of the present application, the desensitization policy is set for different data categories, so as to desensitize sensitive data.
[0084] For example, assume that the desensitization strategy library includes four desensitization strategies: strategy 1, strategy 2, strategy 3, and strategy 4. The data classification may include name, age, gende...
Embodiment 3
[0104] The embodiment of the present application provides an electronic device, such as Figure 4 as shown, Figure 4 The electronic device 400 shown includes: a processor 4001 and a memory 4003 . Wherein, the processor 4001 is connected to the memory 4003 , such as through a bus 4002 . Further, the electronic device 400 may further include a transceiver 4004 . Wherein, the transceiver is used for providing communication functions between electronic devices and other devices. It should be noted that, in practical applications, the transceiver 4004 is not limited to one, and the structure of the electronic device 400 does not limit the embodiment of the present application.
[0105] The processor 4001 may be a CPU, a general processor, DSP, ASIC, FPGA or other programmable logic devices, transistor logic devices, hardware components or any combination thereof. It can implement or execute the various illustrative logical blocks, modules and circuits described in connection w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com