Dual-system peripheral resource allocation method, terminal device and storage medium
A configuration method and resource configuration file technology are applied in the configuration field of dual-system peripheral resources to achieve the effect of solving security and ensuring convenience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
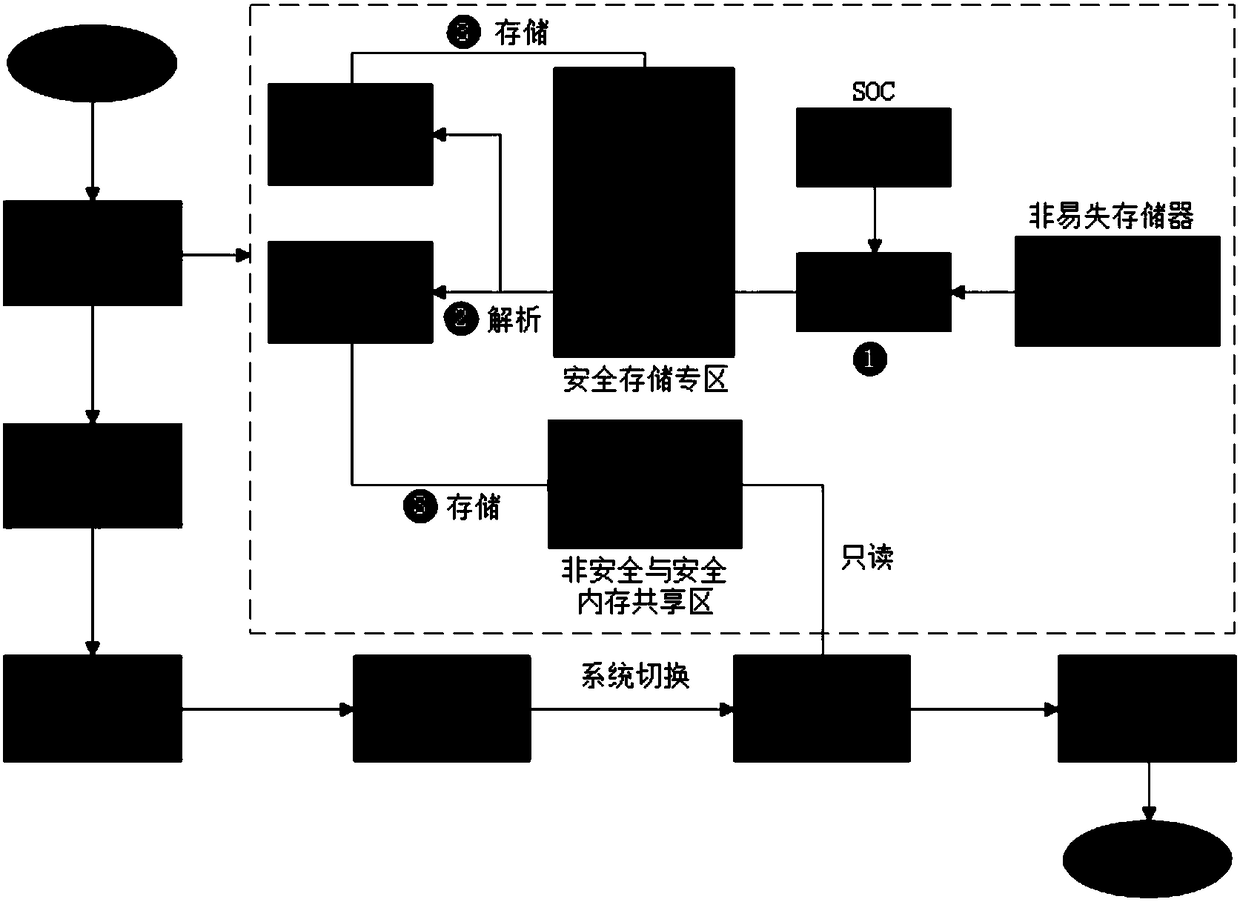
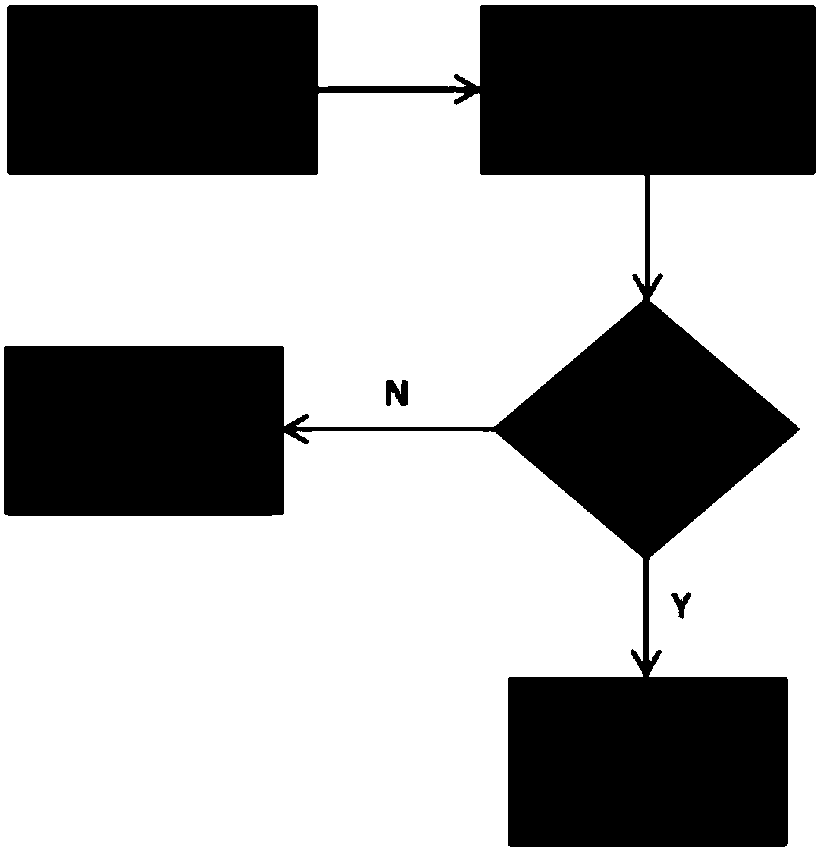
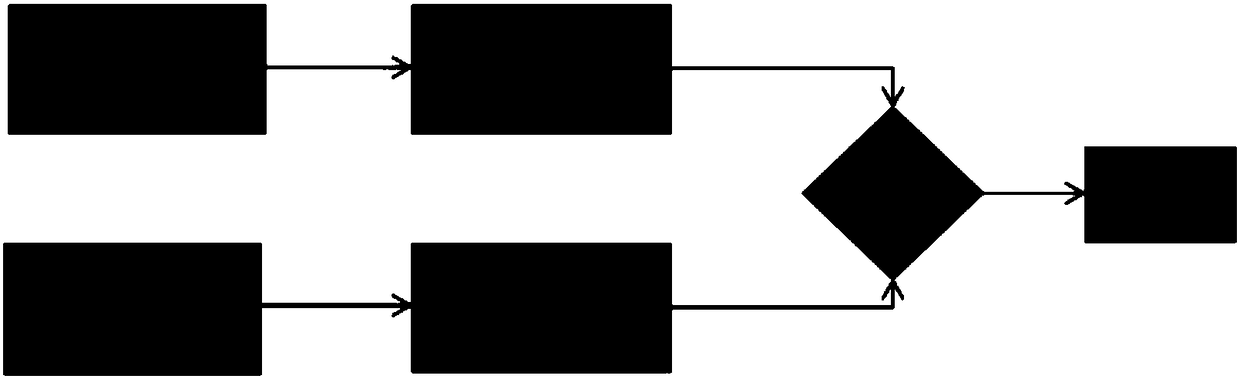
[0035] see Figure 1-Figure 3 As shown, the present invention provides a method for configuring peripheral resources of a dual system,
[0036] The concrete process of the method described in the present invention is as follows:
[0037] (1) Before the dual system starts, configure the peripheral resource configuration file of the MCU peripheral resource security and non-secure status, after encryption, download the ciphertext to the non-volatile memory, and burn the decryption key to the security The operating system can only be accessed on the system-on-chip SOC.
[0038] (2) The dual system is started, the safety operating system is started first, and the ciphertext of the peripheral resource configuration file is decrypted using the decryption key of the soc.
[0039] (3) Allocate a memory space used by a secure operating system, i.e. a secure storage area, which cannot be accessed by a non-secure operating system, and then store the decrypted peripheral resource configu...
Embodiment 2
[0051] The present invention also provides a dual-system peripheral resource configuration terminal device, including a memory, a processor, and a computer program stored in the memory and operable on the processor, and the processor executes the computer program When implementing the steps in the above-mentioned method embodiments of the embodiments of the present invention, for example Figure 1-Figure 3 Method steps for the steps shown.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com