Captured host automatic judgment method and device, electronic equipment and memory medium
An automatic determination and host technology, applied in the field of network security, can solve the problem of not being able to automatically determine whether the host has been compromised, and achieve the effect of reducing losses and saving human resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
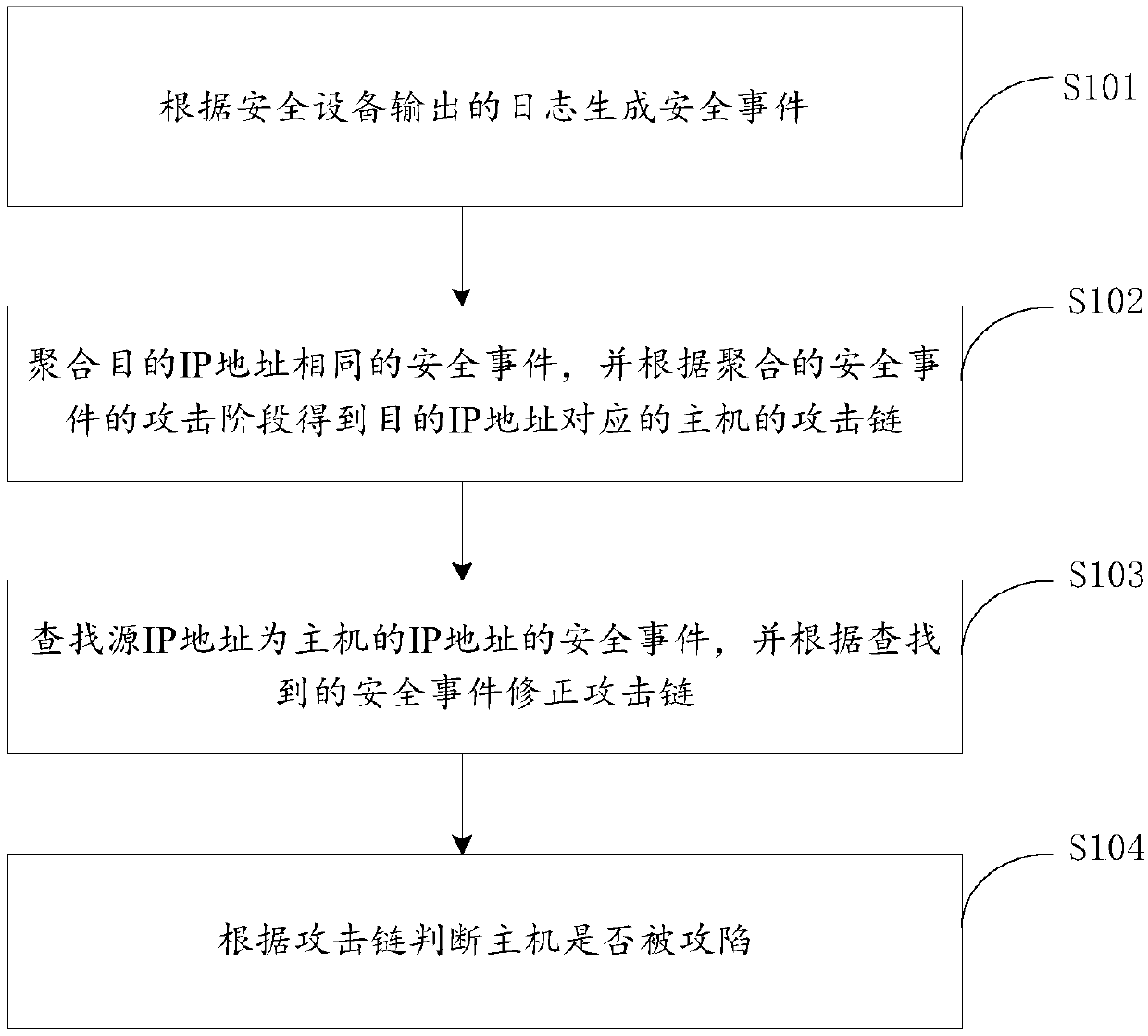
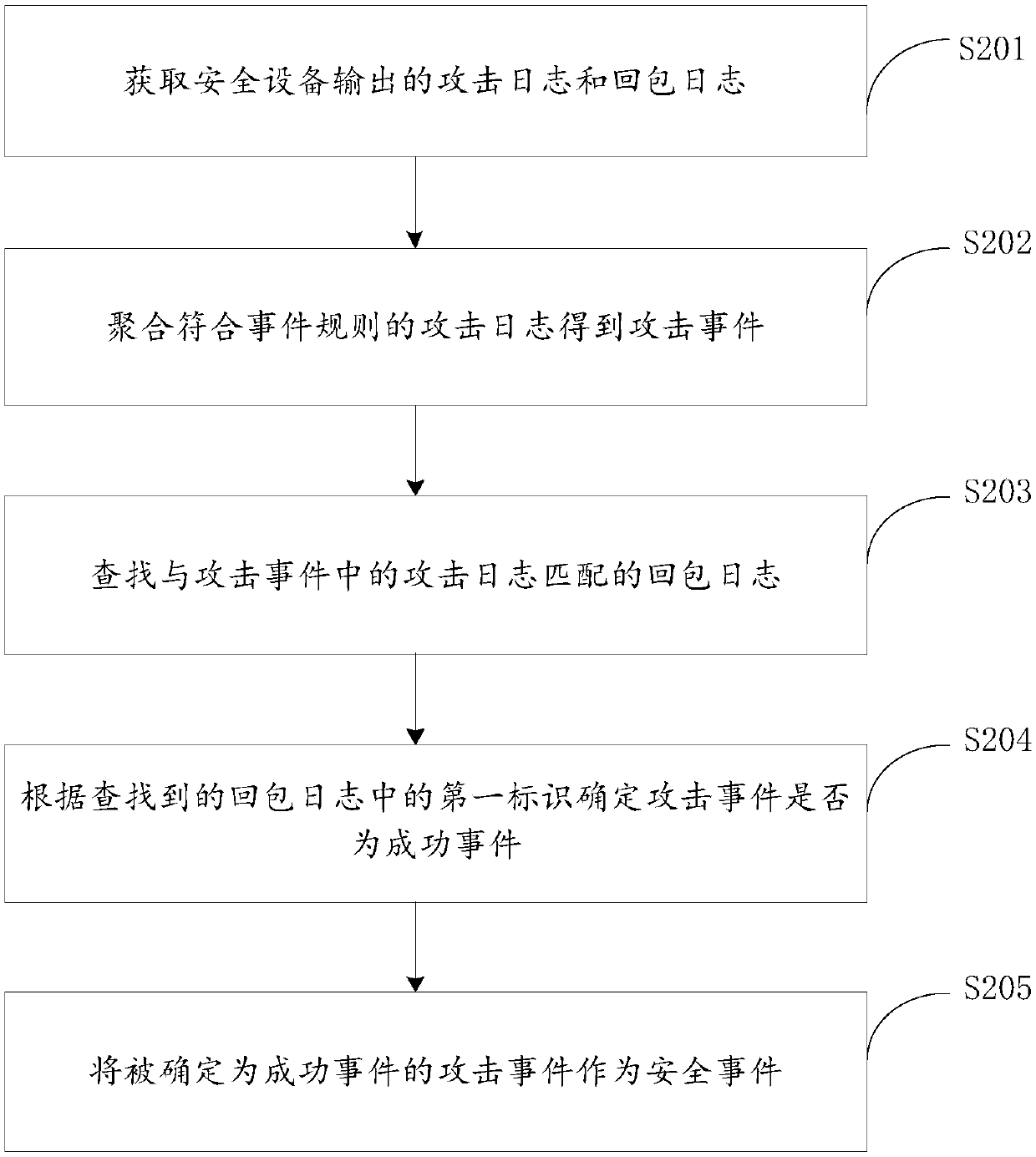
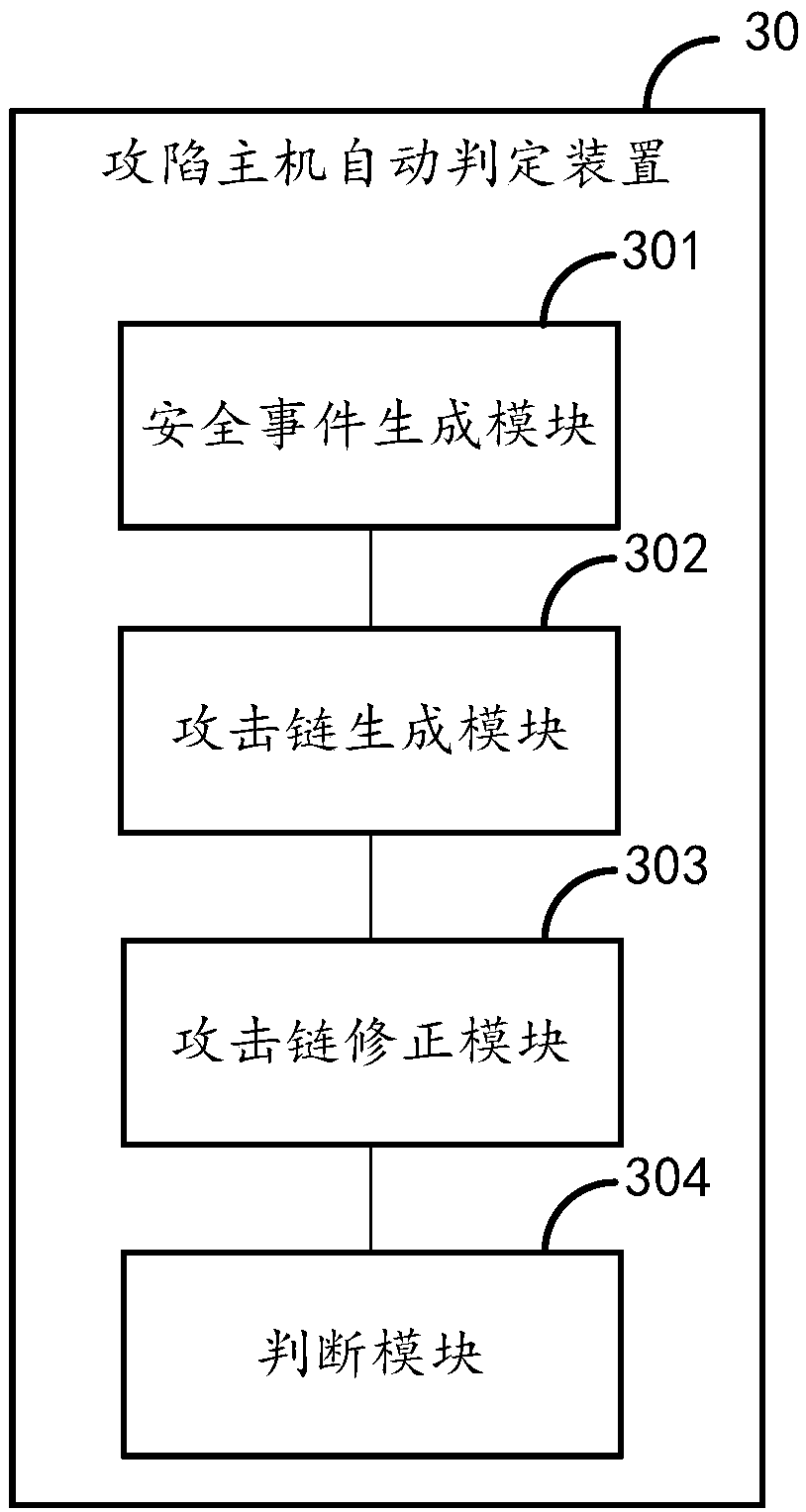
[0022] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention more clear, the technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the drawings in the embodiments of the present invention.
[0023] For the convenience of understanding, the nouns involved in the embodiments of the present invention are explained below:
[0024] Assets are network devices used in an organization's internal network, such as servers, network devices, personal computers, etc.
[0025] Host refers to network devices, including but not limited to the following types: servers, mobile terminals, notebooks, and gateways.
[0026] A zombie host refers to a computer device infected with a bot virus and controlled by a hacker program. It can launch a denial of service (DoS) attack or send spam at any time according to the hacker's command and control (C&C, command and control)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com