Method and system for monitoring service calls in a virtualized environment
A service calling and monitoring technology, applied in the field of computer security, can solve the problem that auxiliary modules are no longer trusted
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described below through specific embodiments and accompanying drawings.
[0044] This embodiment is an example of a cryptographic operation service call monitoring system in a cloud environment.
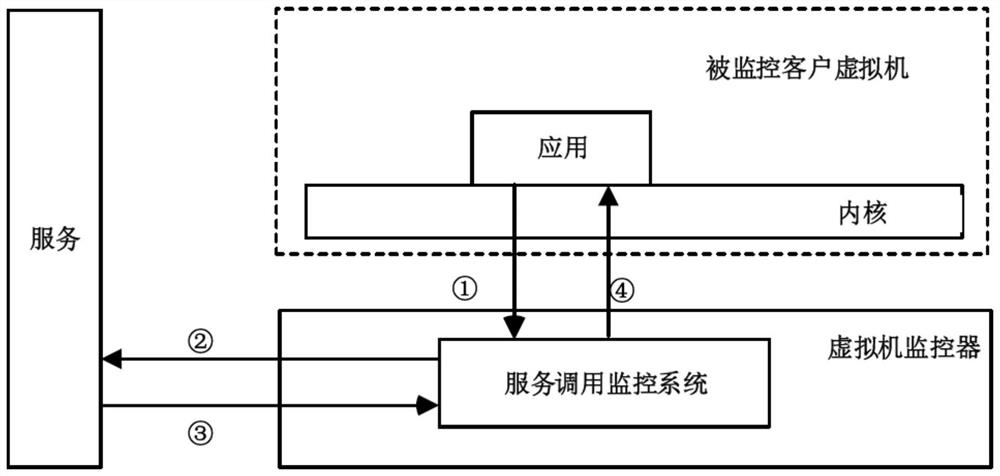
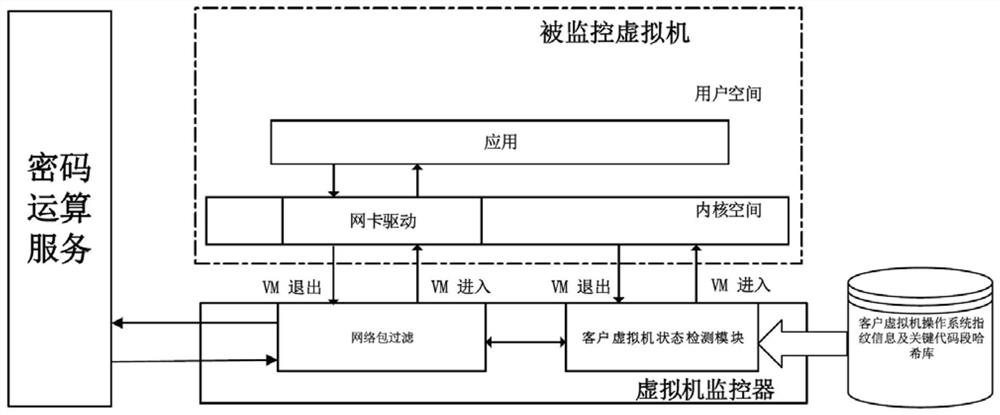
[0045] figure 2 It is a schematic diagram of using the method of the present invention to provide a cryptographic operation service invoking a monitoring service in a virtualized environment. The user subscribes to the key management service (KMS) provided by the cloud service provider, and the KMS service provides services through https. The KMS service is responsible for managing the user's key and providing cryptographic computing services.
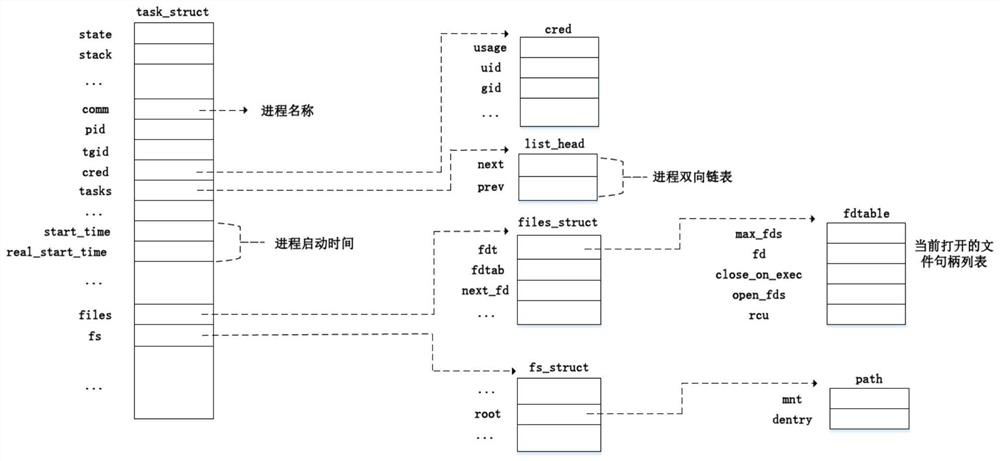
[0046] The service call monitoring system in this embodiment is implemented on the QEMU-KVM virtualization platform, and the host computer uses an Intel CPU chip. The detection part of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com