Circuit supporting multiple Hash algorithms
An algorithm and circuit technology, applied in the field of information security and cryptography, can solve the problems of high cost, reverse difficulty, poor versatility, etc., and achieve the effect of high clock frequency and high efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] It should be noted that the embodiments of the present invention and the features of the embodiments may be combined with each other under the condition of no conflict.
[0040] The present invention will be described in detail below with reference to the accompanying drawings and in conjunction with the embodiments.
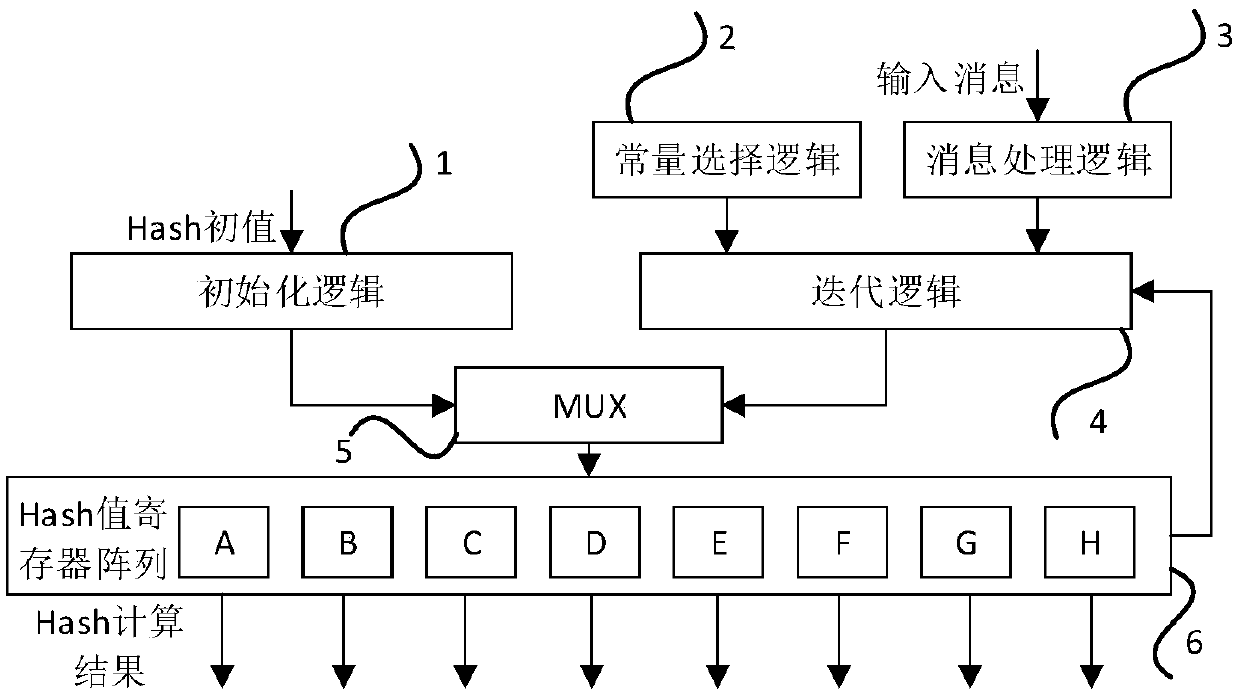
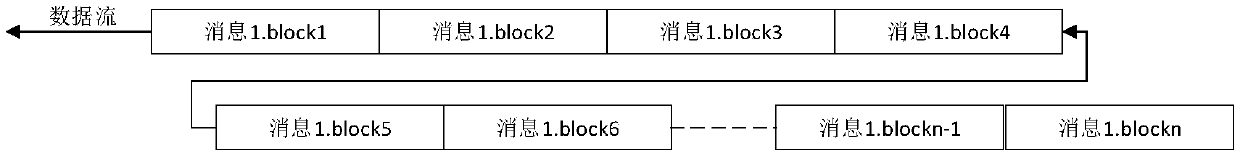
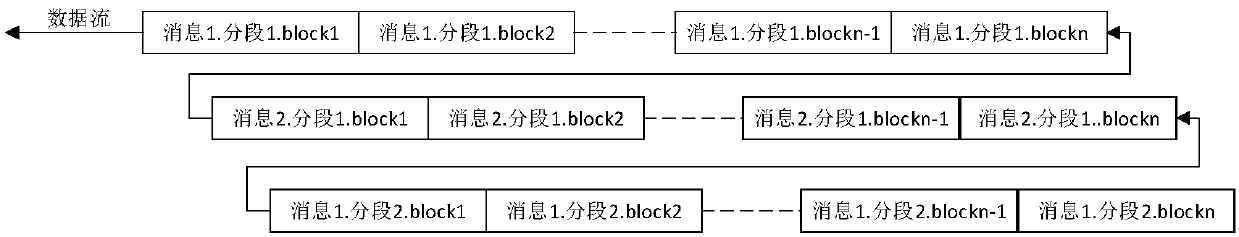
[0041] This embodiment is a circuit that supports multiple hash algorithms, including MD5, SHA0, SHA1, SHA224, SHA256, SHA384, SHA512, and SM3; this circuit supports continuous processing of a message, and also supports continuous processing of a message. Segmented processing, that is, another message can be inserted between two segments of a message for processing;
[0042] like figure 1 As shown, the circuit includes: initialization logic, constant selection logic, message processing logic, iteration logic, MUX and Hash value register array,
[0043] The initialization logic is used to complete the initialization of the Hash value register array, that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com