Privacy Preservation Method Based on Dynamic Location Association
A privacy protection and dynamic location technology, applied in the field of privacy protection, can solve problems such as user privacy leakage, user reputation rough evaluation, infringement of user security interests, etc., to achieve the effect of enhancing possibility and feasibility, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
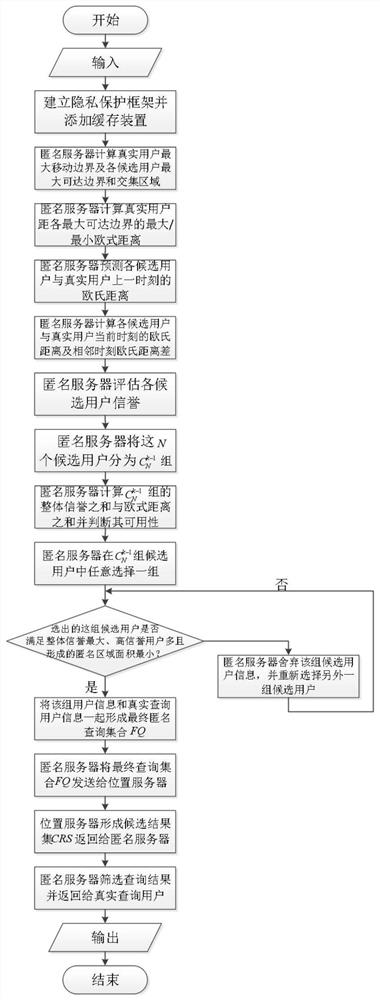
[0035] specific implementation plan
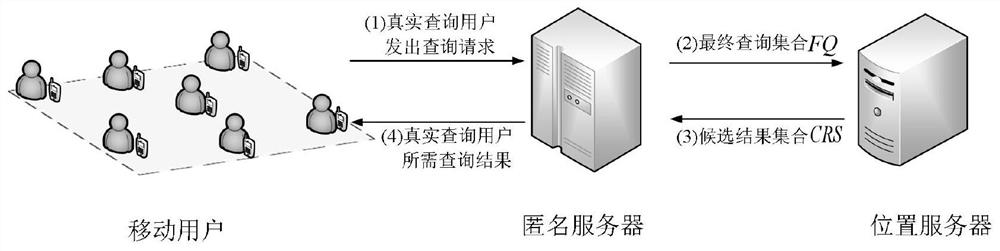
[0036] The present invention adopts figure 1 Centralized privacy protection based on anonymous server privacy protection architecture.
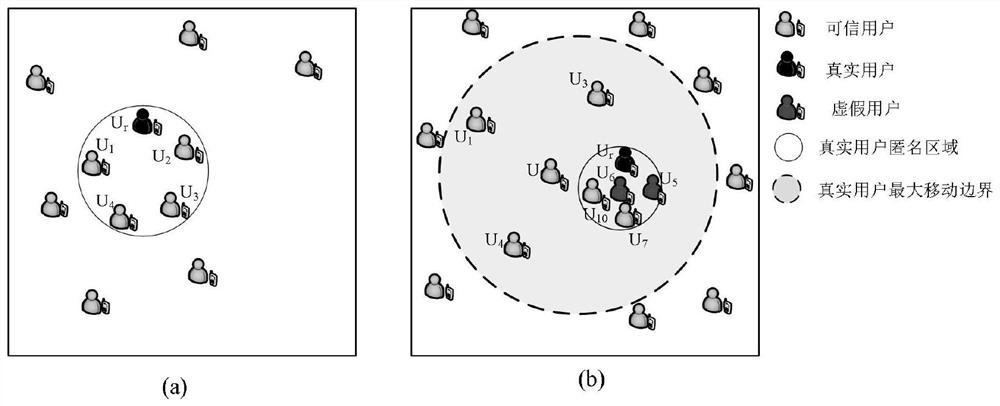
[0037] refer to figure 1 , based on the anonymous server privacy protection architecture, including mobile users, anonymous server and location server LBS-S. The mobile user is an ordinary mobile user in the mobile Internet, and has a mobile device with a cache device, which is used for anonymous server to query a certain When a specific user implements k-anonymous privacy protection, a k-anonymous area is formed. The anonymous server is mainly used in the query service to evaluate the reputation value of each candidate user, select the appropriate user to realize k-anonymity, finally send the k-anonymous query request, and filter the candidate query results to return to the real query user, that is, the anonymous server first chooses to satisfy the real Query the candidate users with user privacy p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com