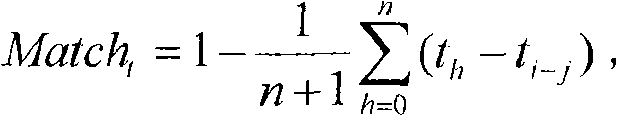Patents
Literature
121results about How to "Reduce credibility" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
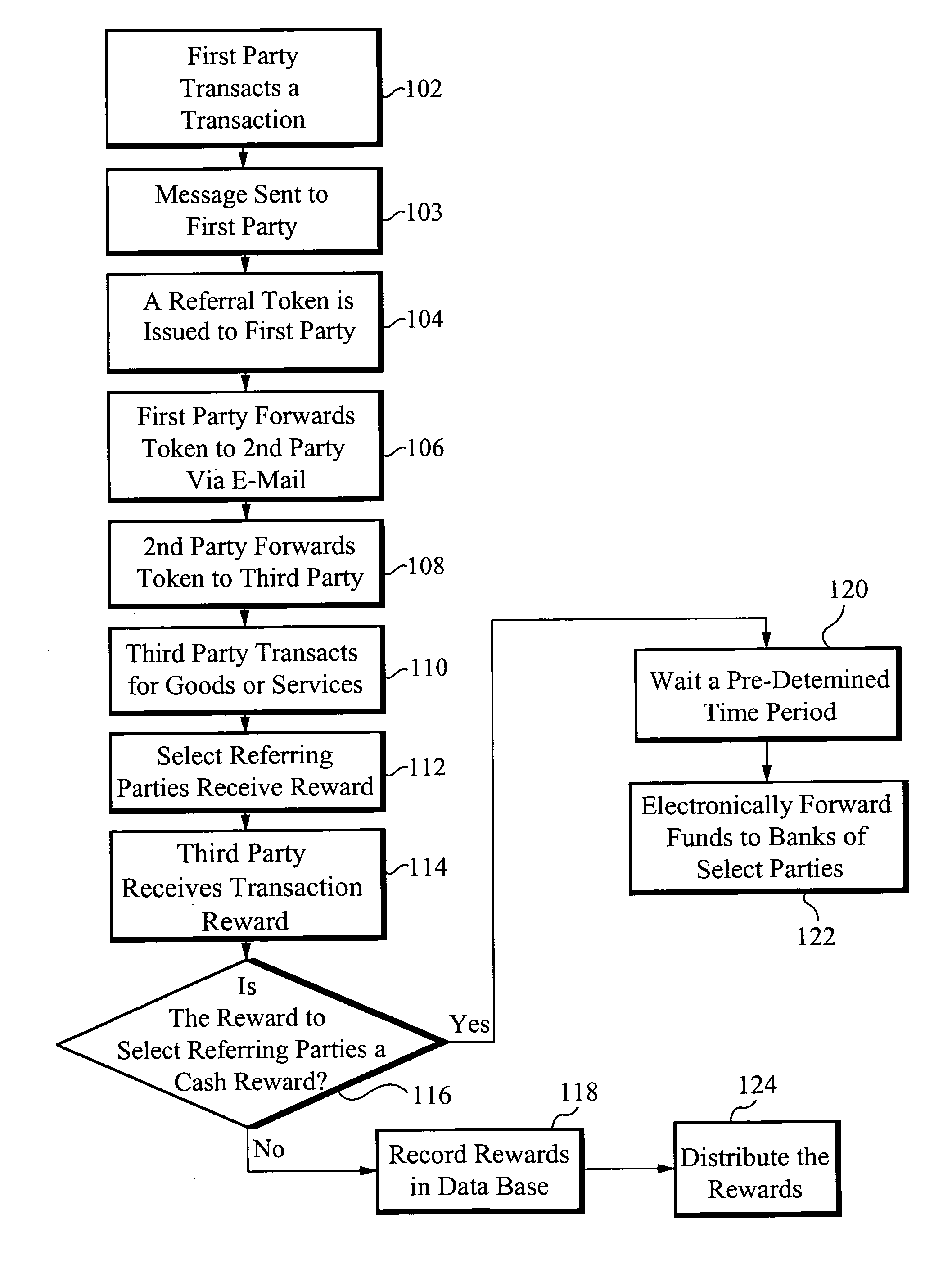
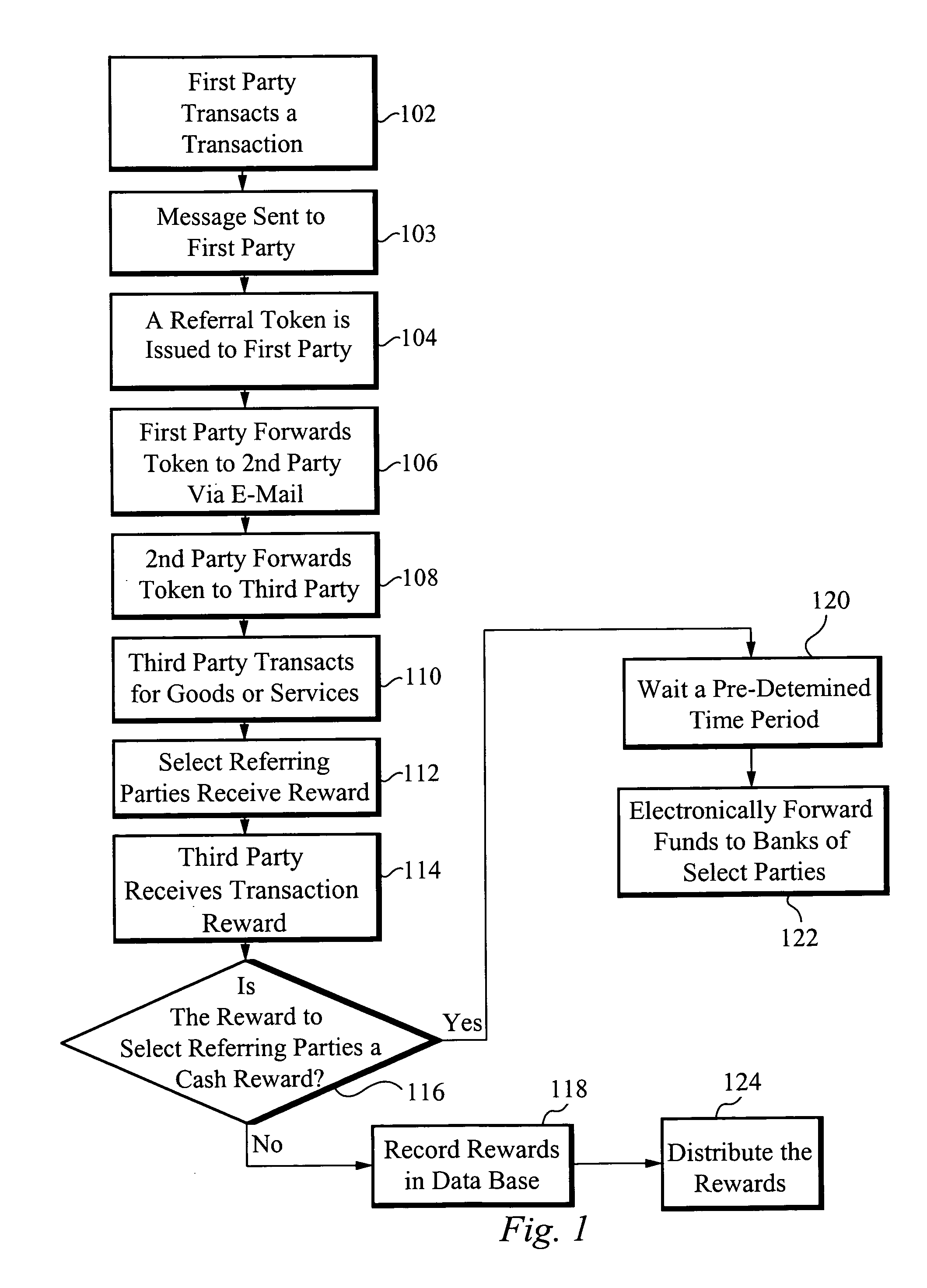
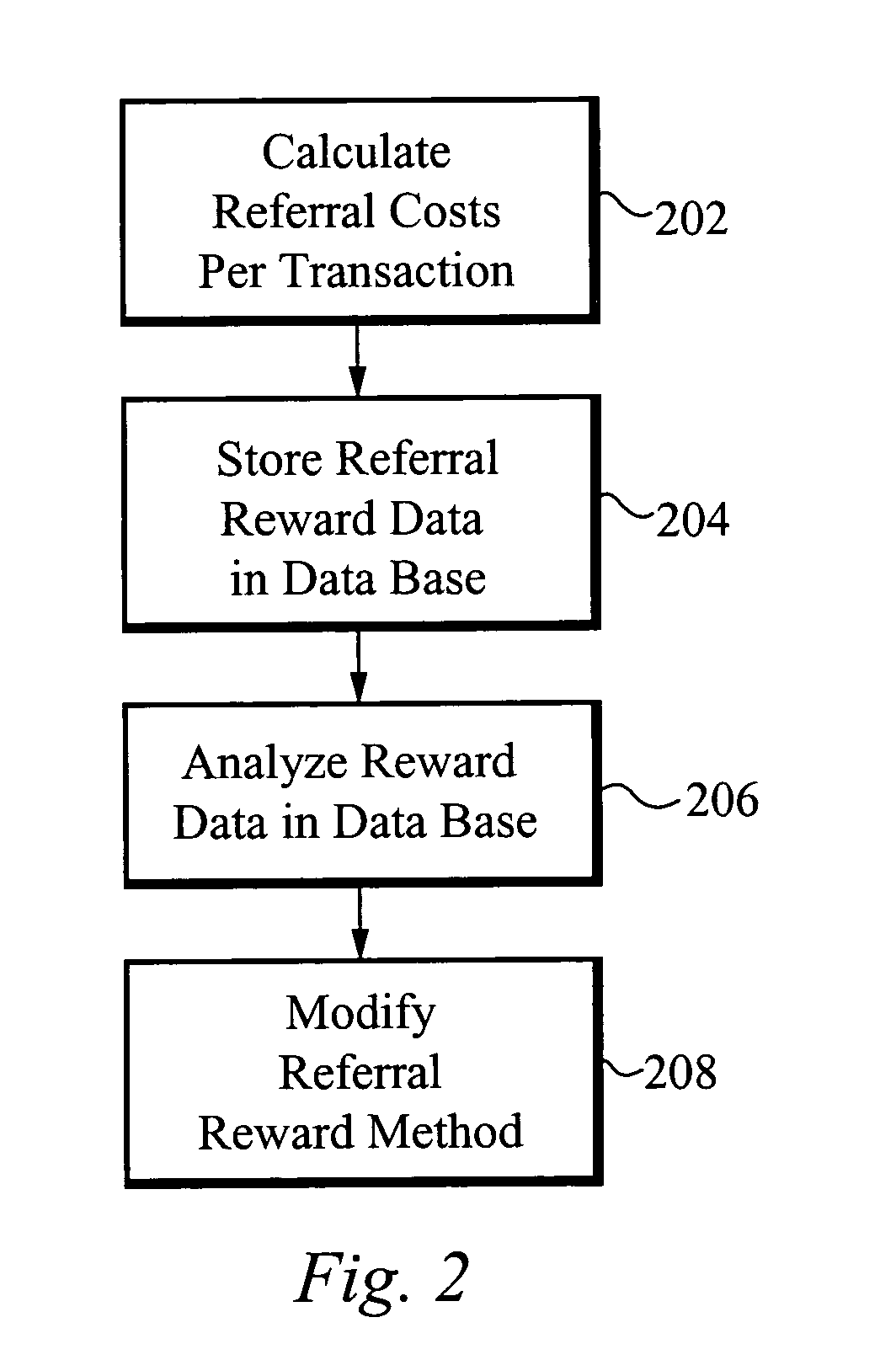
Methods of anti-spam marketing through personalized referrals and rewards
ActiveUS7774229B1Protect privacy and confidentialityConfidenceDiscounts/incentivesAdvertisementsDigital dataPersonalization
A marketing method comprising a Provider offering a potential reward to a first party in exchange for promotional assistance of forwarding a first e-mail message to a second party comprising a personalized referral for the marketable entity, a first set of data comprising a first serial number and a first URL link. A first Web site corresponding to the first URL link is created which provides information on the referenced marketable entity and an offer to transact. The first set of data in the first e-mail message is correlated to a first set of database data within a digital database controlled by the Provider. The first e-mail message is forwarded from the Provider to the first party. The first e-mail message is forwarded from the first party directly to the second party without giving any identifying information about the second party to the Provider.
Owner:STRIPE INC
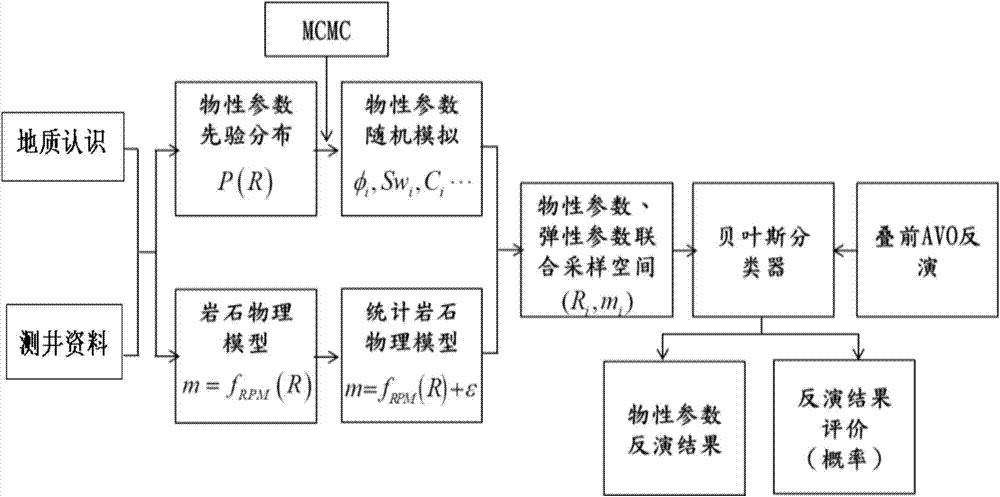
Carbonate rock physical parameter seismic inversion method
ActiveCN104516017AAchieve simultaneous inversionReduce credibilitySeismic signal processingSeismology for water-loggingS-waveMaximum a posteriori estimation
The invention provides a carbonate rock physical parameter seismic inversion method, which belongs to the field of petroleum geophysical exploration. The method comprises the following steps: (1) carrying out pre-stack AVO three-parameter inversion based on a pre-stack angle gather to obtain formation elasticity parameters M, wherein M includes P-wave velocity, S-wave velocity and density; (2) establishing a statistical rock physical model based on logging data; (3) randomly simulating physical conditions of a reservoir based on the rock physical model obtained from step (2) to obtain a random simulation result; and (4) carrying out Bayes classified simulation on the random simulation result obtained from step (3) to obtain a posterior probability distribution, and taking the M obtained from step (1) as the input of inversion to find a R with the maximum posteriori probability distribution, wherein R is the final inversion result.
Owner:CHINA PETROLEUM & CHEM CORP +1
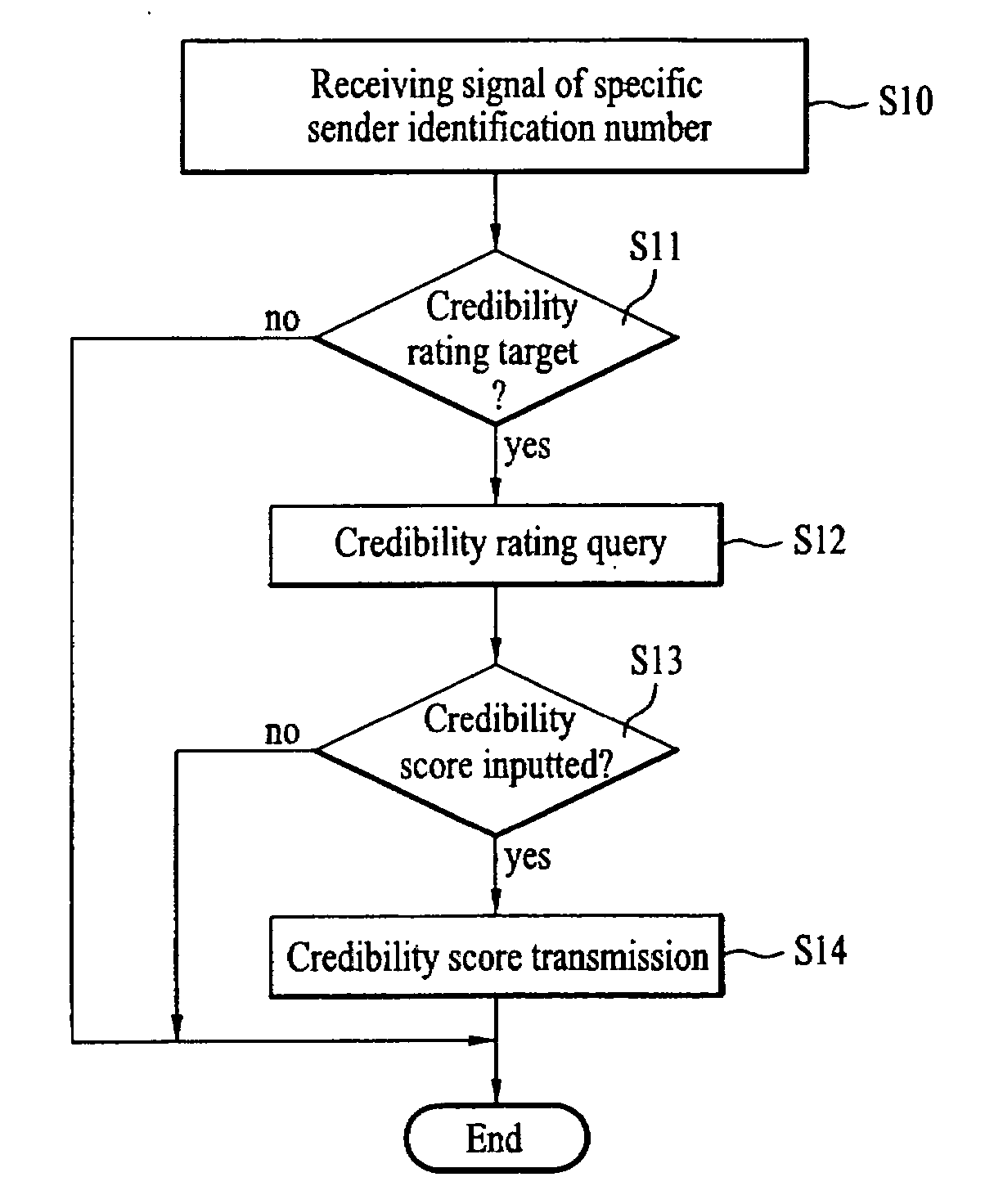
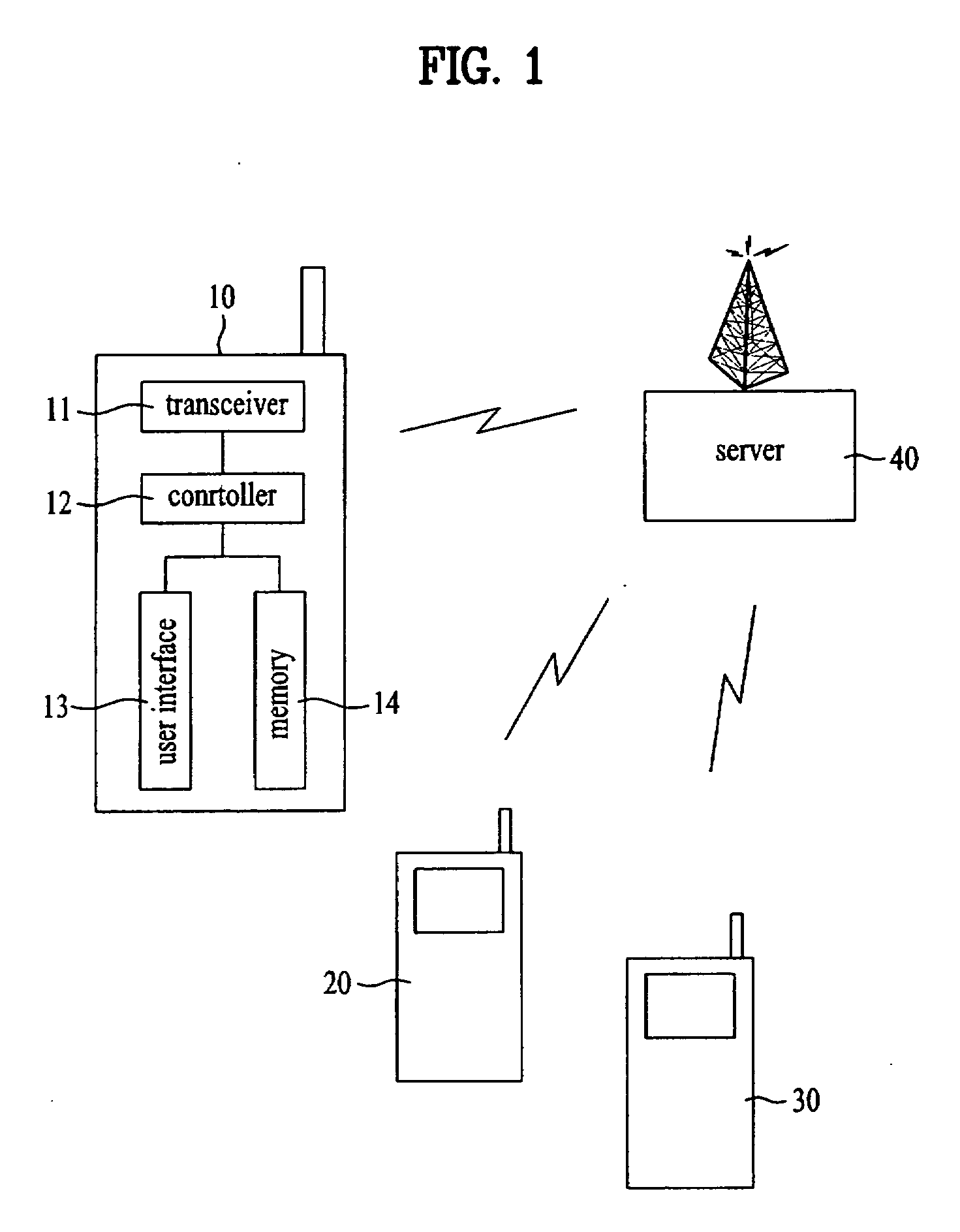
Communication terminal and reception blocking method thereof
InactiveUS20070019235A1Eliminate the problemReduce credibilityAutomatic call-answering/message-recording/conversation-recordingCommmunication supplementary servicesTelecommunications
A communication terminal and reception blocking method thereof are disclosed, by which a signal of a sender having poor credibility can be blocked in advance, by which a plurality of recipients are able to rate a credibility of a specific sender to block a signal of the specific sender and by which information for the rating can be shared. The present invention includes the steps of setting a level of a reception blocking for a signal transmitted from a specific sender identification number, receiving credibility rating information for the specific sender identification number, and if a credibility rating of the specific sender identification number based on the credibility rating information belongs to a range of the set level, deciding the reception blocking for the signal transmitted from the specific sender identification number.
Owner:LG ELECTRONICS INC
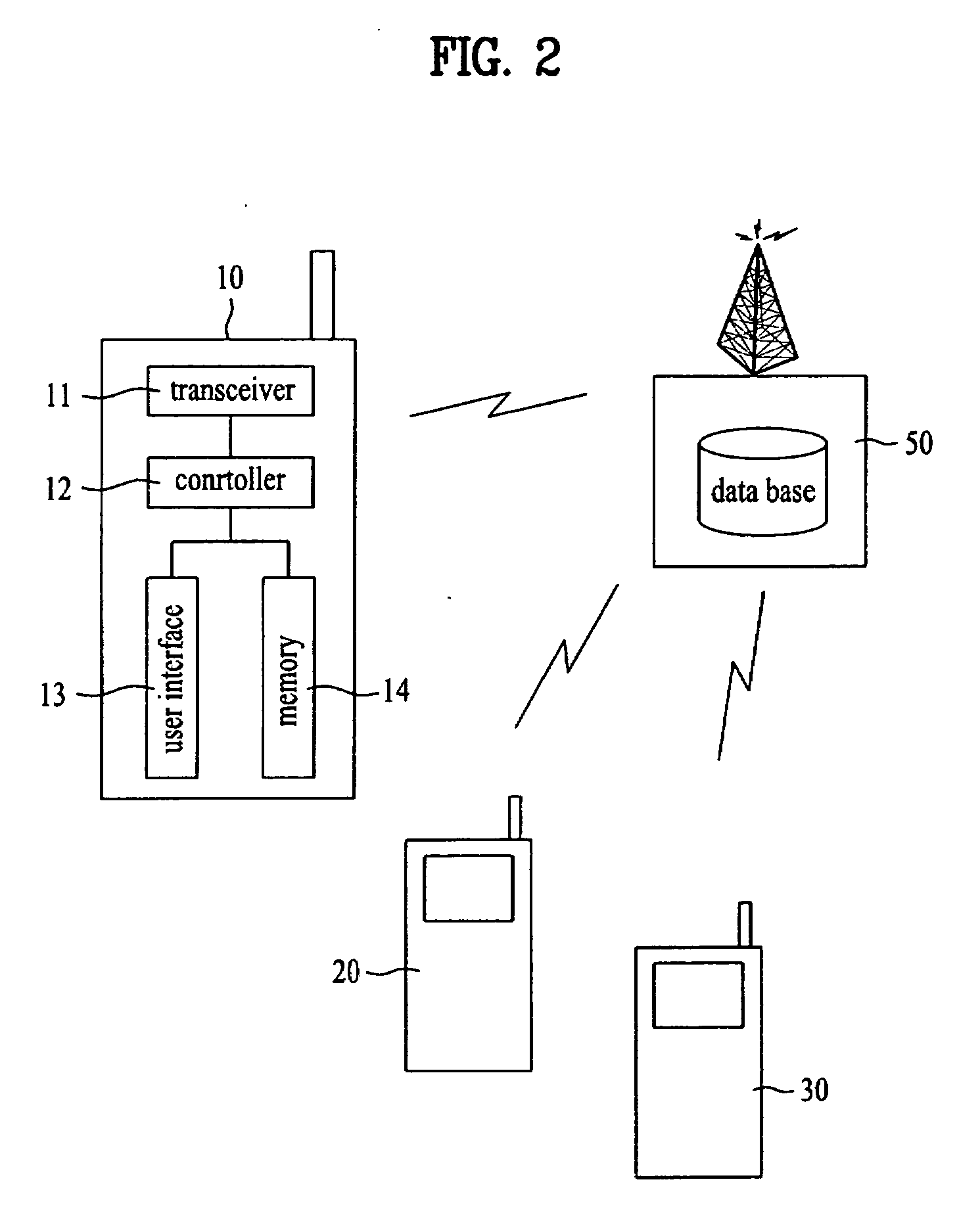
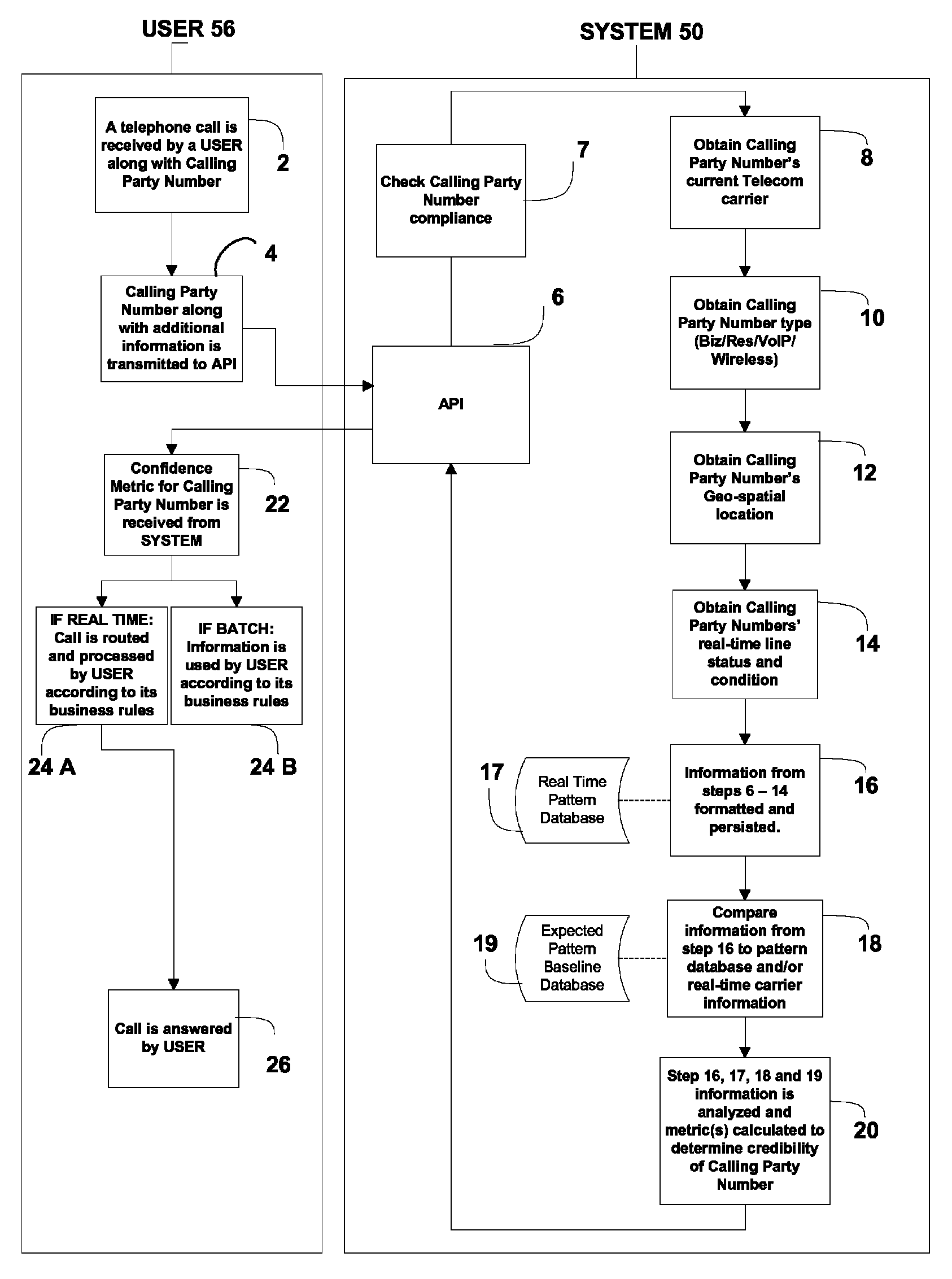
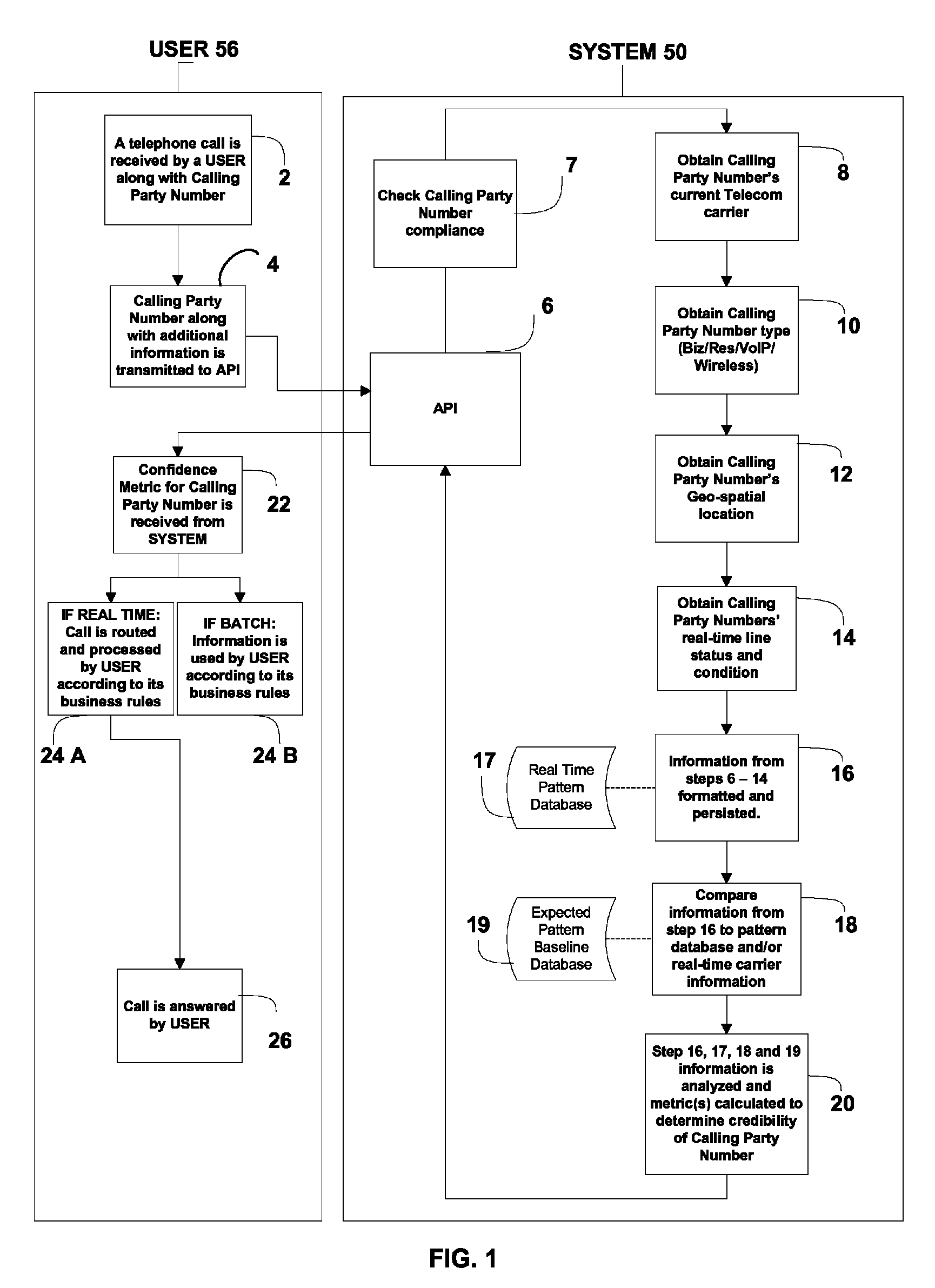
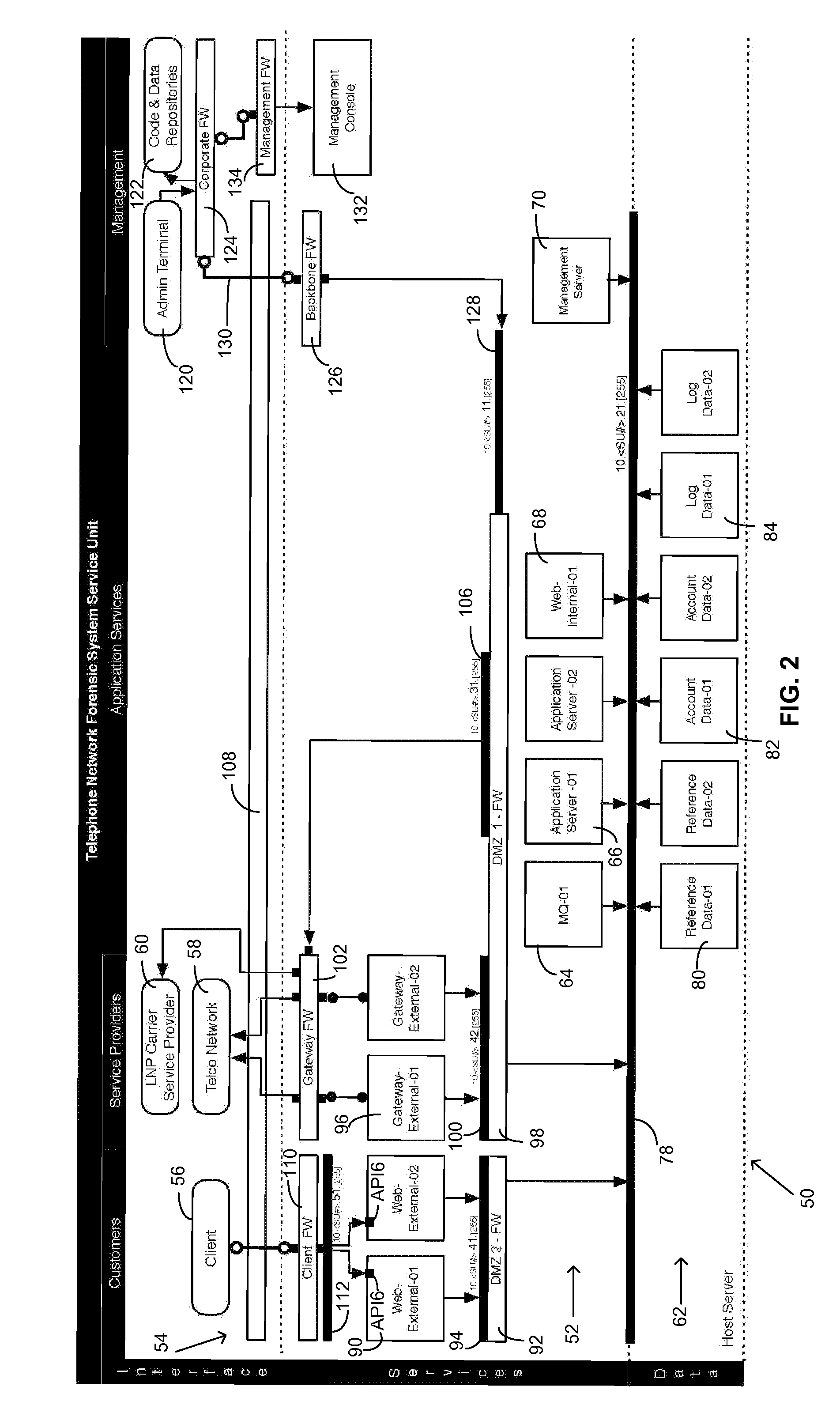
Method of and system for discovering and reporting trustworthiness and credibility of calling party number information
ActiveUS8238532B1Reduce credibilityImprove trustCoin/check-freed systemsTelephone networkNetwork data
A method of and system for discovering and reporting the trustworthiness and credibility of calling party number information, such as Automatic Number Identification (ANI) or Calling Number Identification (Caller ID) information, or for inbound telephone calls. The disclosed method entails the use of real time telephone network status and signaling, network data, locally stored data, and predictive analytics. Practice of the disclosed method is neither detectable by nor intrusive to the calling party, and the method can be implemented into existing enterprise, telecommunications, and information service infrastructures.
Owner:TRUSTID
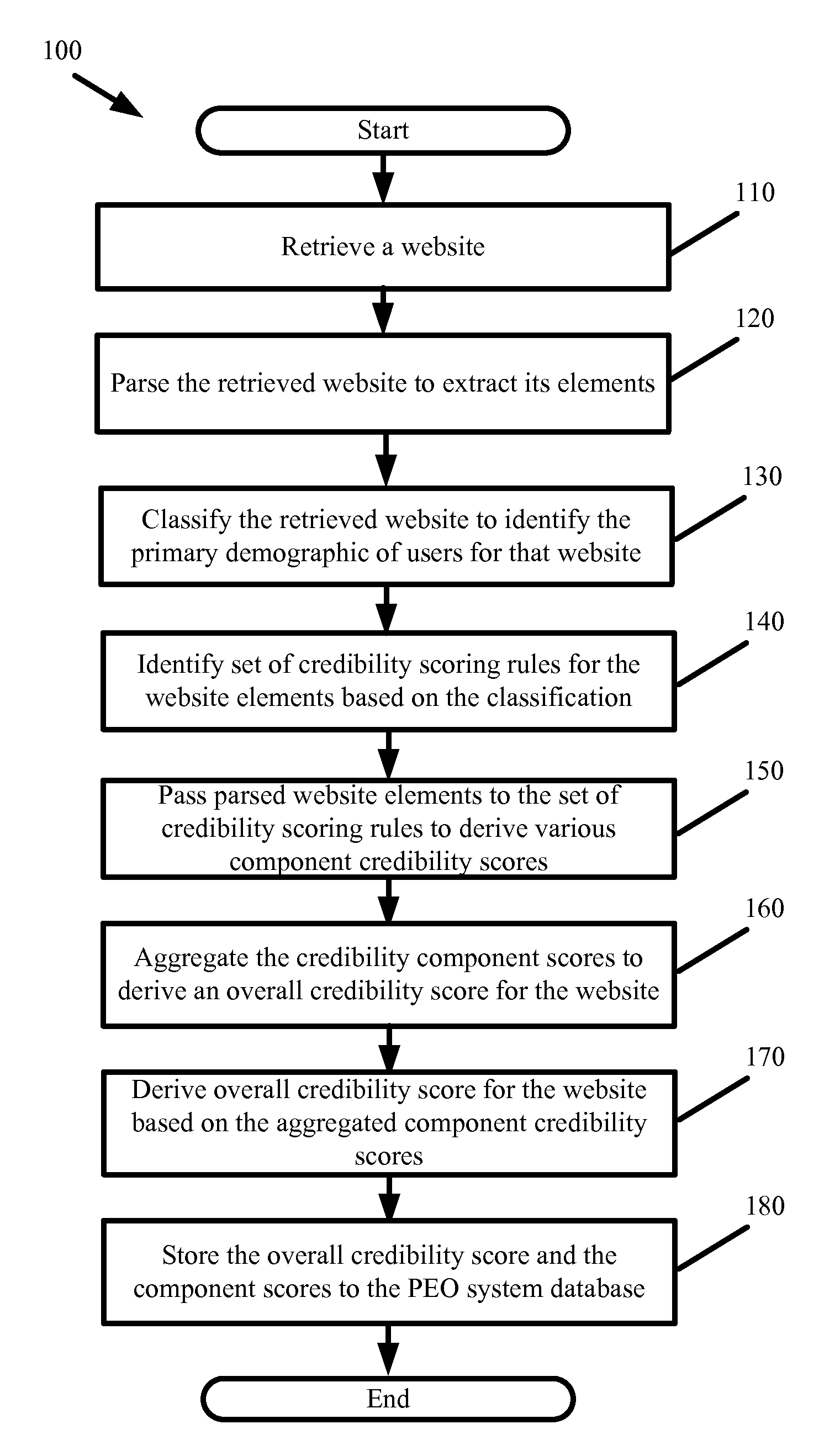
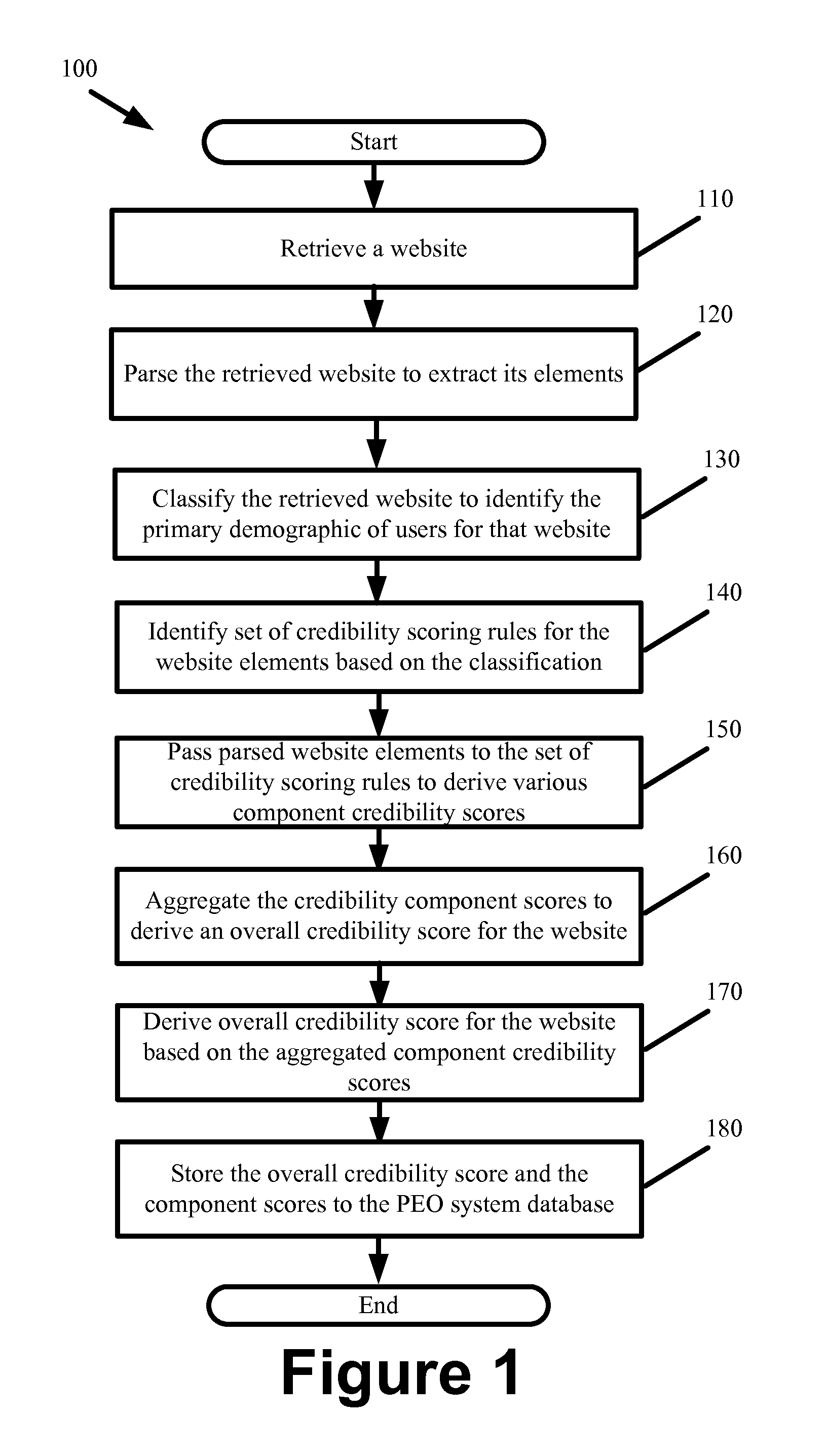
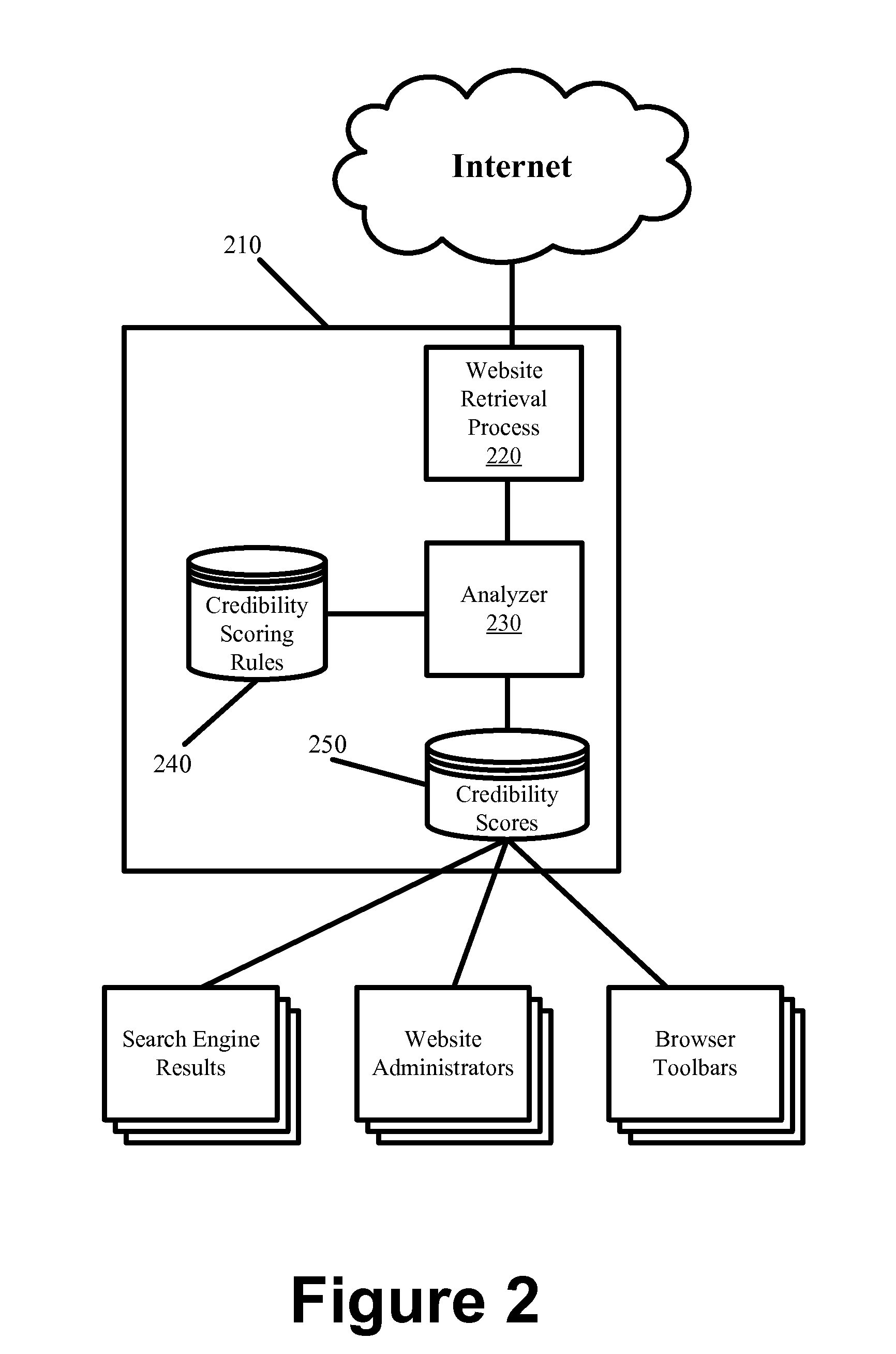
People Engine Optimization
ActiveUS20120310937A1Improve website credibilityEnjoyable web browsing experienceWeb data indexingDigital data processing detailsCrowdsData mining
Some embodiments promote website credibility and the optimization of websites for people by automatedly quantifying various elements of a website into component credibility scores. In some embodiments, a set of encoded credibility scoring rules are used to compute each of the component credibility scores, wherein the credibility scoring rules are derived based on factors that have been identified by a grouping of people that preferably represent a primary demographic of users that consume the content of a particular classified type of website. In some such embodiments, the credibility scoring rules are derived from commonality that is identified from a sample set of known credible and / or non-credible websites of a particular classification. Once the credibility scoring rules are defined, the system applies the rules to other websites having the same classification as those from which the rules are derived to automatically generate credibility scores for the other websites.
Owner:DUN & BRADSTREET EMERGING BUSINESSES
Integrated diagnosis method of gas path fault of aeroengine
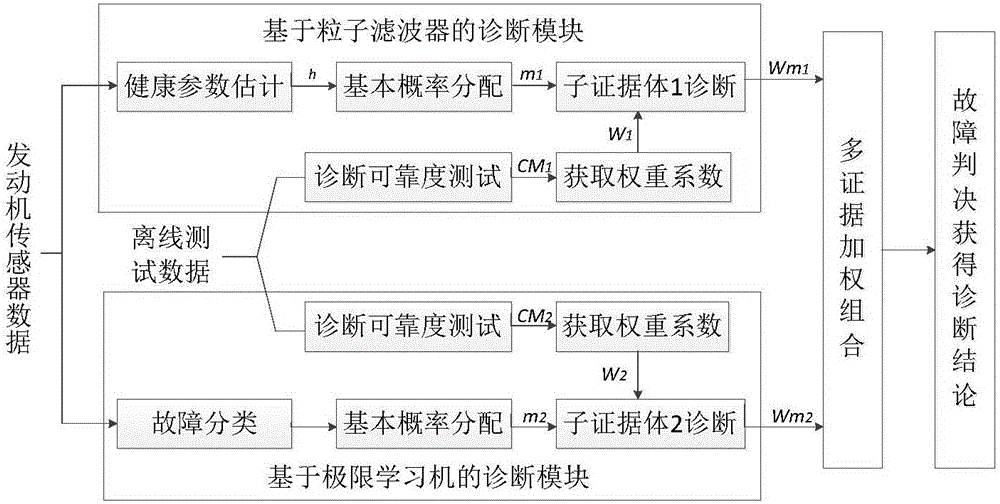
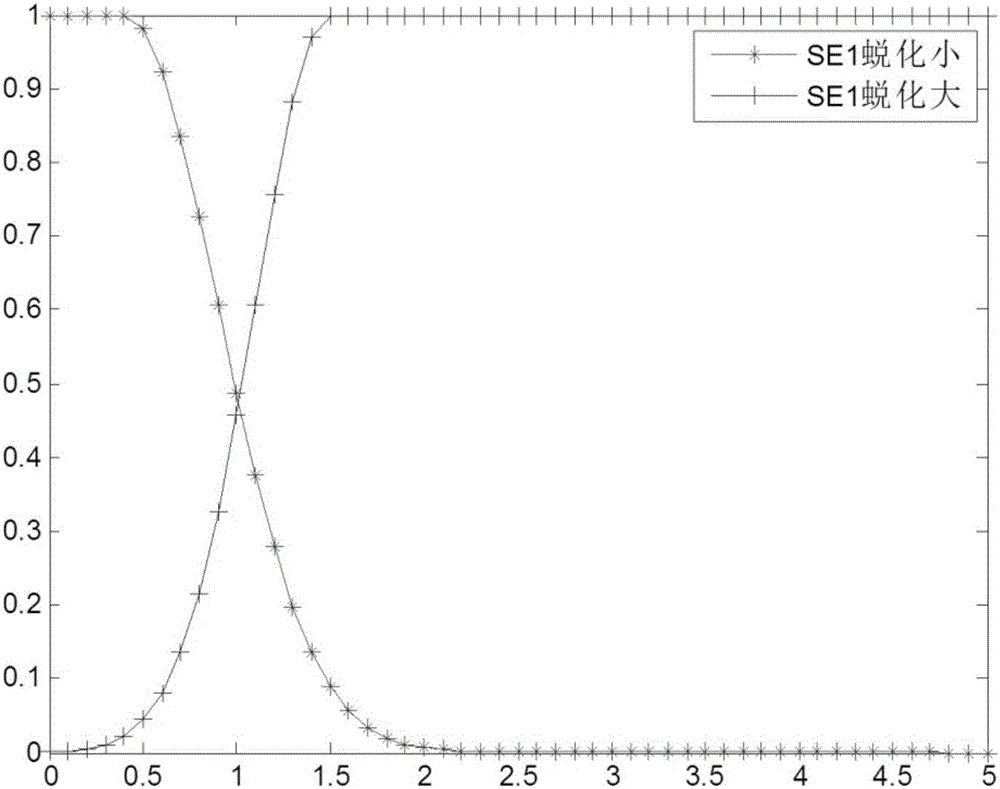
InactiveCN105911975AReduce conflictHigh precisionElectric testing/monitoringAviationWeight coefficient
The invention relates to an integrated diagnosis method of a gas path fault of an aeroengine, wherein the method is based on an adaptive weighted D-S evidence theory. With the method, problems that the precision is low because of a single fault diagnosis method and the evidence conflict exists during the fusion process of multiple methods can be solved. A non-linear local diagnosis module based on a particle filter and a non-linear local diagnosis module based on an extreme learning machine are constructed respectively; and fusion of local diagnosis results is carried out by using an adaptive weighted D-S evidence theory. A multi-method integrated diagnosis structure for an engine fault; diagnosis reliability degrees of all fault modes by a local diagnosis systems based on a particle filter and an extreme learning machine are obtained in an off-line mode by using a confusion matrix; and on the basis of the reliability degrees, different weight coefficients are assigned for an evidence body. Therefore, the evidence conflict is reduced effectively and the precision of an integrated diagnosis of a gas path component fault of an engine is improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
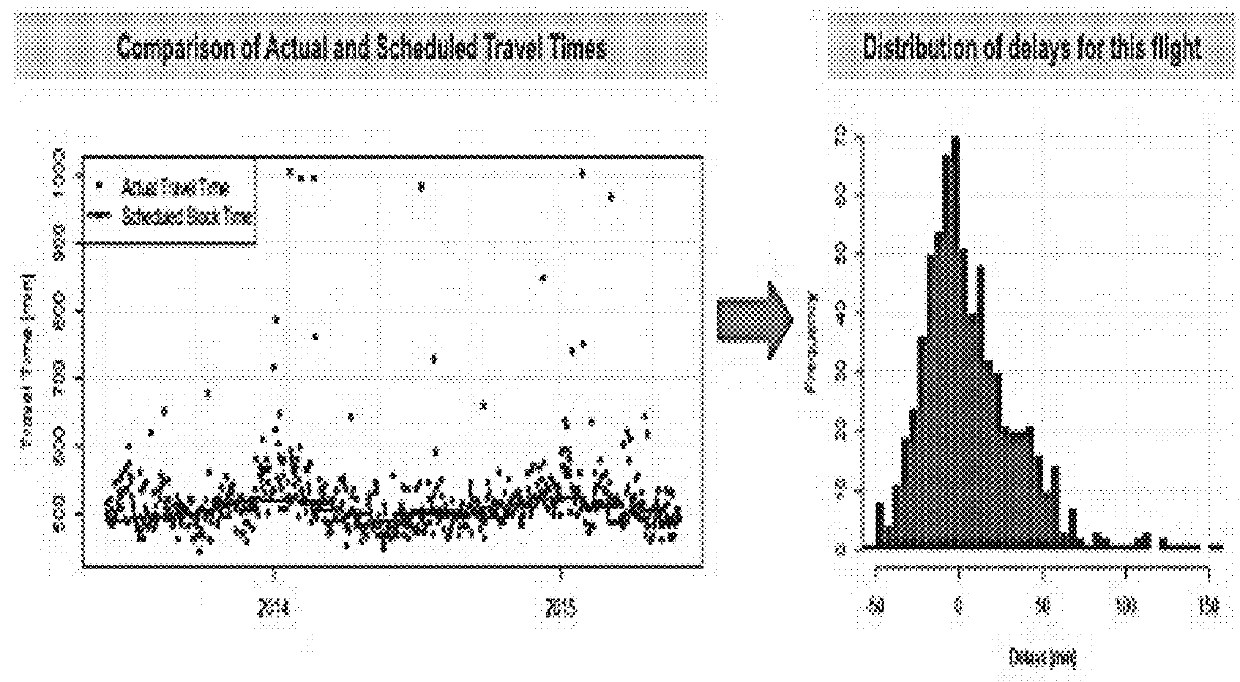
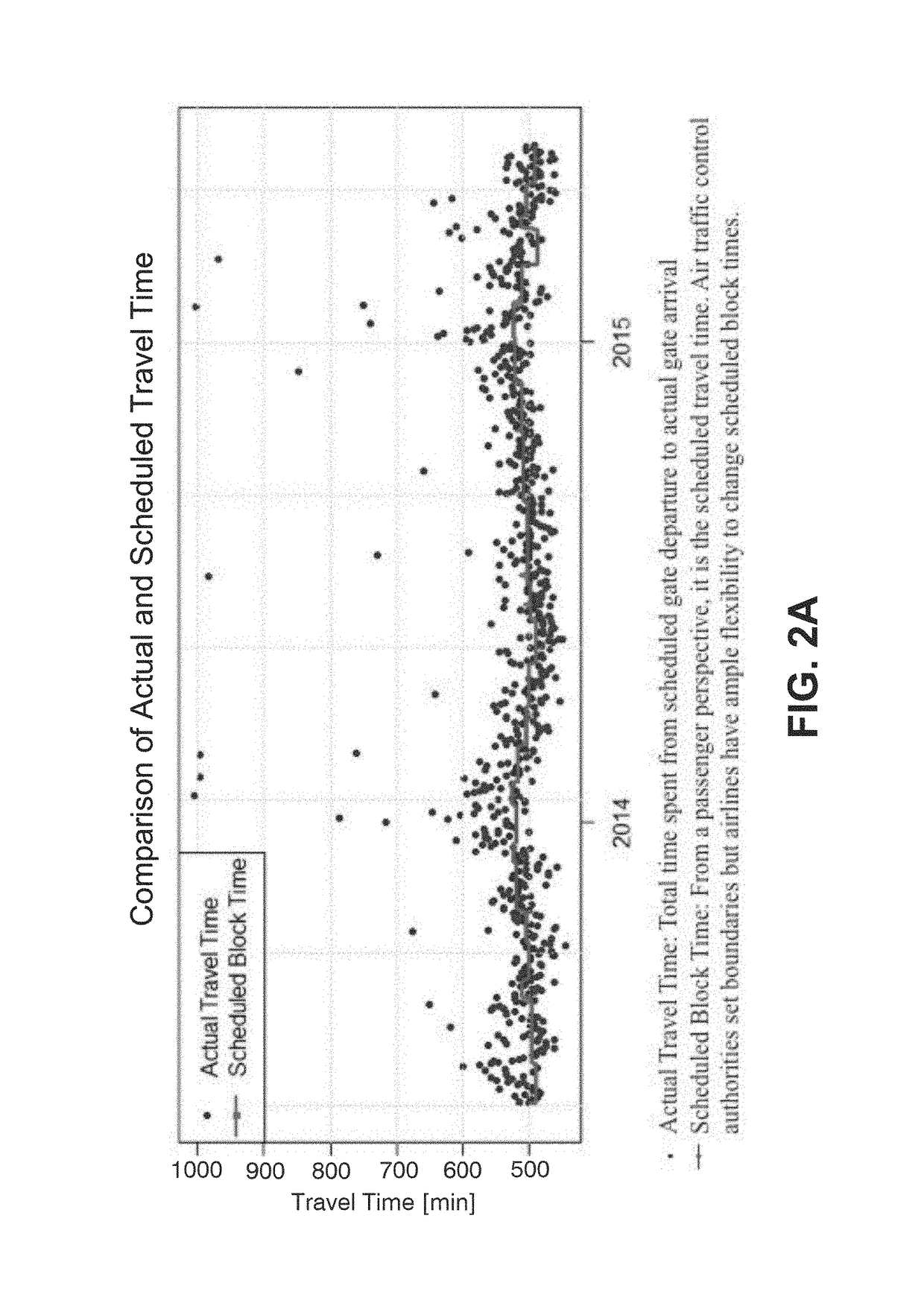
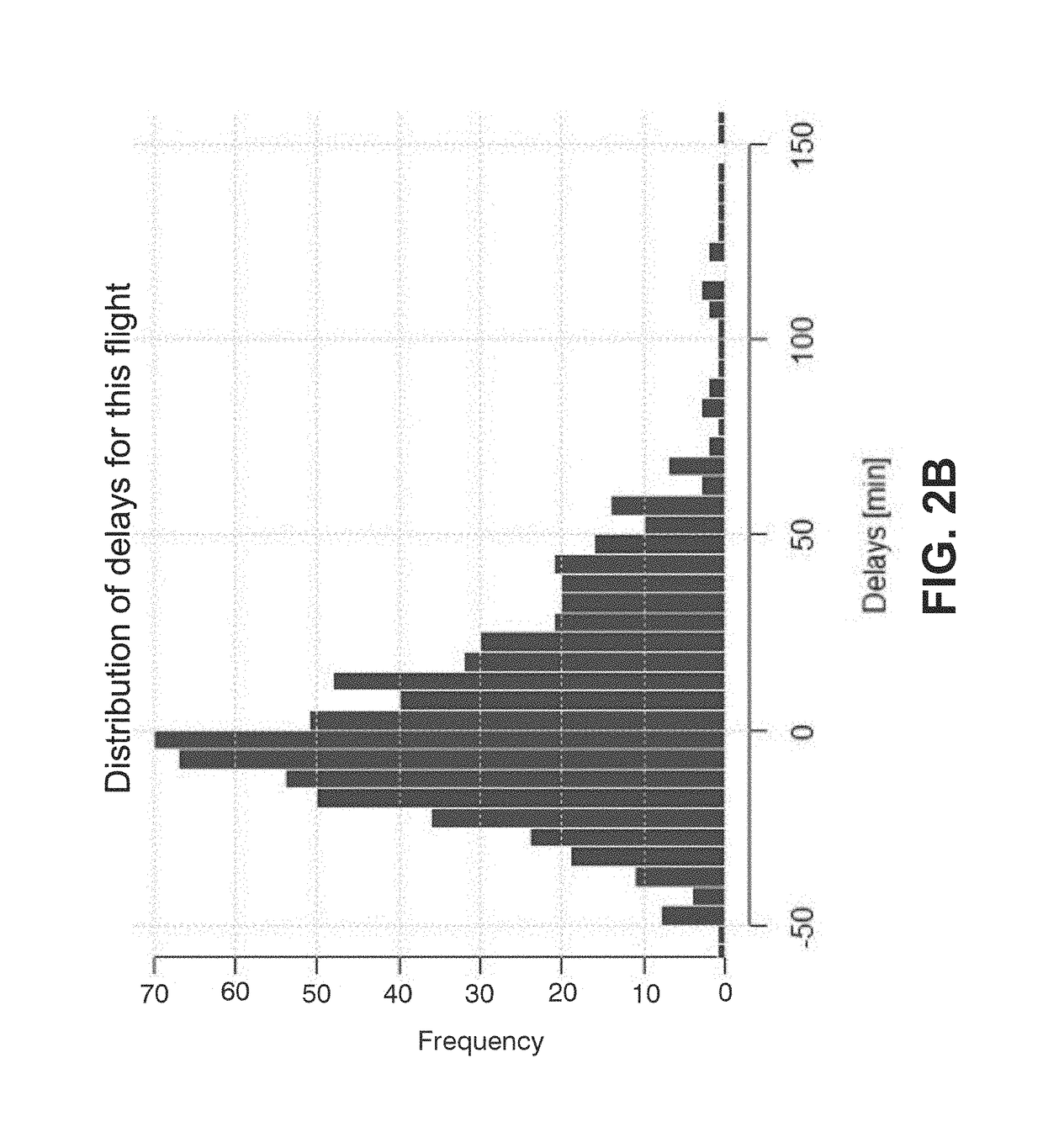
Flight trajectory prediction system and flight trajectory-borne automated delay risk transfer system and corresponding method thereof
ActiveUS20180181144A1Easy to operateImprove sustainabilityAutonomous decision making processFinanceRisk sharingRisk exposure
A method and automated flight trajectory prediction and flight trajectory-borne automated delay risk-transfer system related to airspace risks for risk sharing of a variable number of risk-exposed units by pooling resources of the risk-exposed units and by providing the risk-transfer system as a self-sufficient operatable risk-transfer system based on the pooled resources for the risk-exposed units by a resource-pooling system associated with the risk-transfer system. The risk-exposed units are connected to the risk-transfer system by a plurality of payment-transfer devices configured to receive and store payments from the risk-exposed units for the pooling of their risks and resources, and an automated transfer of risk exposure associated with the risk-exposed units is provided by the risk-transfer system.
Owner:SWISS REINSURANCE CO LTD
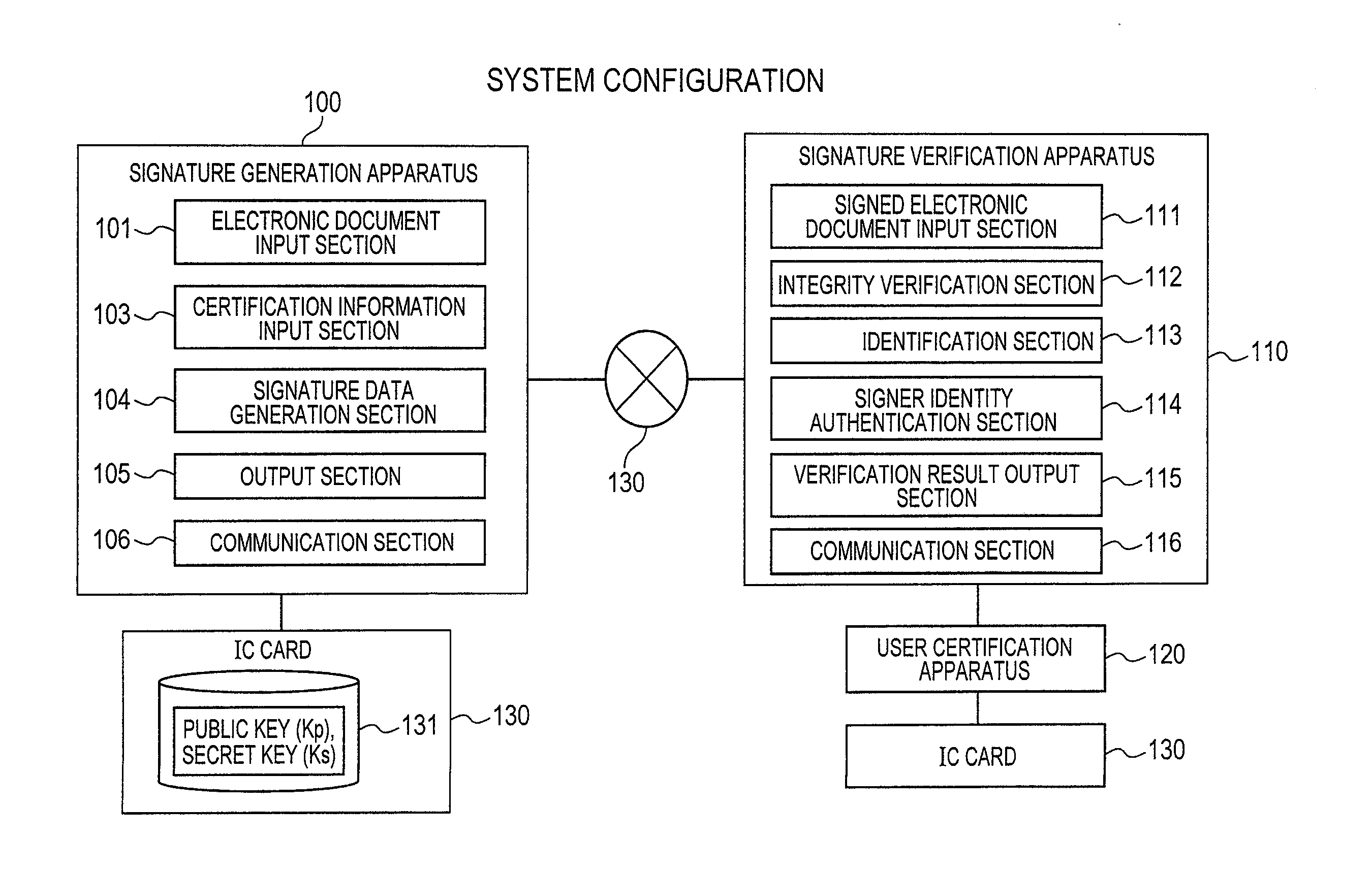
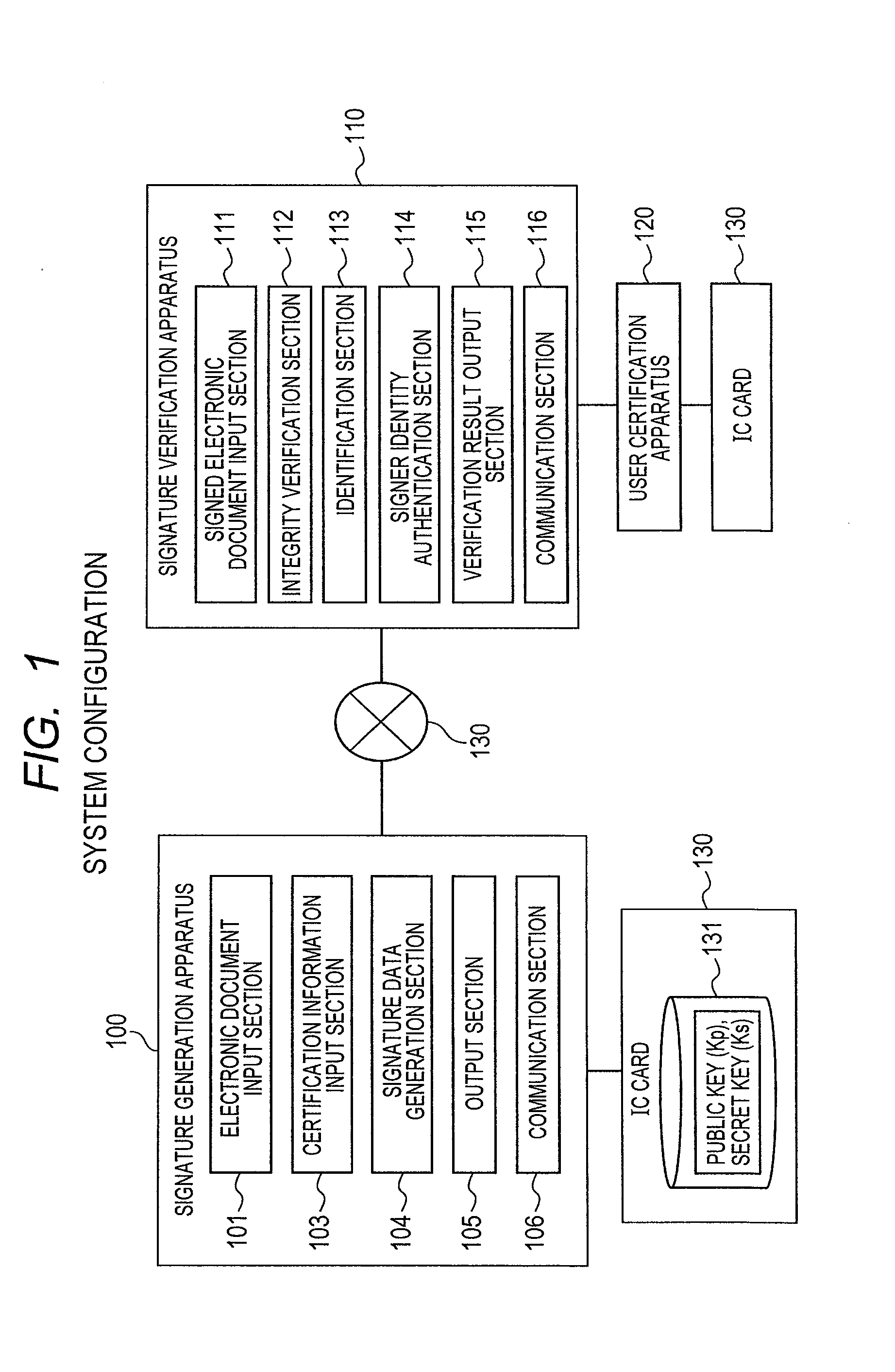
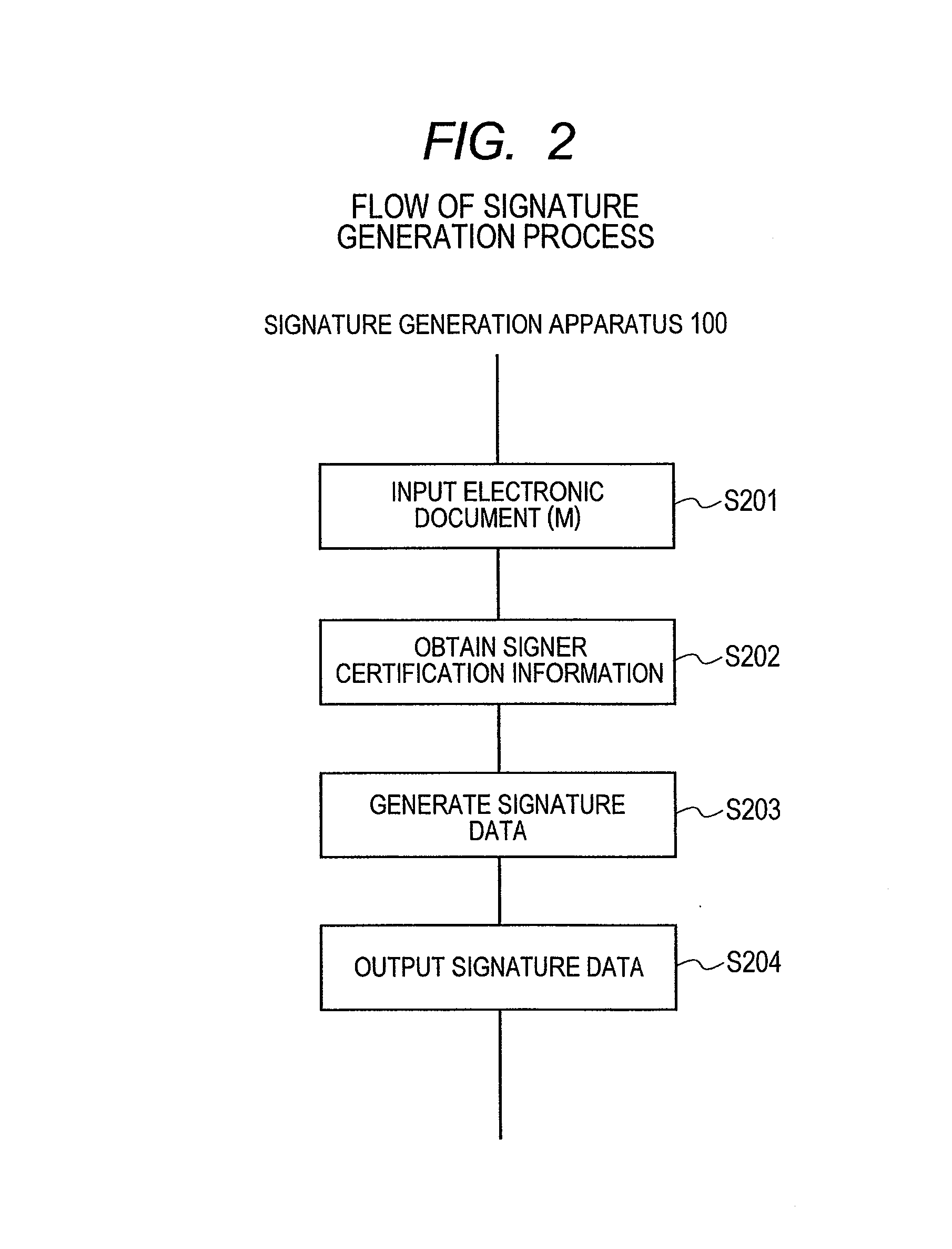
Signature Generation and Verification System and Signature Verification Apparatus
ActiveUS20140019766A1High operating costsMakes cost highUser identity/authority verificationDigital data protectionData validationElectronic document
A signature generation and verification system including a signature generation apparatus and a signature verification apparatus is provided. Based on signer certification information possessed by a signer, the signature generation apparatus generates a digital signature and verification data corresponding to a given electronic document and outputs the set of the digital signature and the verification data as signature data. Upon receipt of the electronic document and the signature data, the signature verification apparatus verifies the digital signature using the verification data to verify the integrity of the electronic document. As needed, the signature verification apparatus performs user identification ex-post facto by authenticating that the signer certification information from which the verification data was generated belongs to a legitimate user without knowledge of the signer certification information.
Owner:HITACHI LTD
Internet-of-Vehicles trust management method based on block chain
ActiveCN111447177ASecurityInformation judgment is accurateDatabase distribution/replicationDigital data protectionBlockchainData security
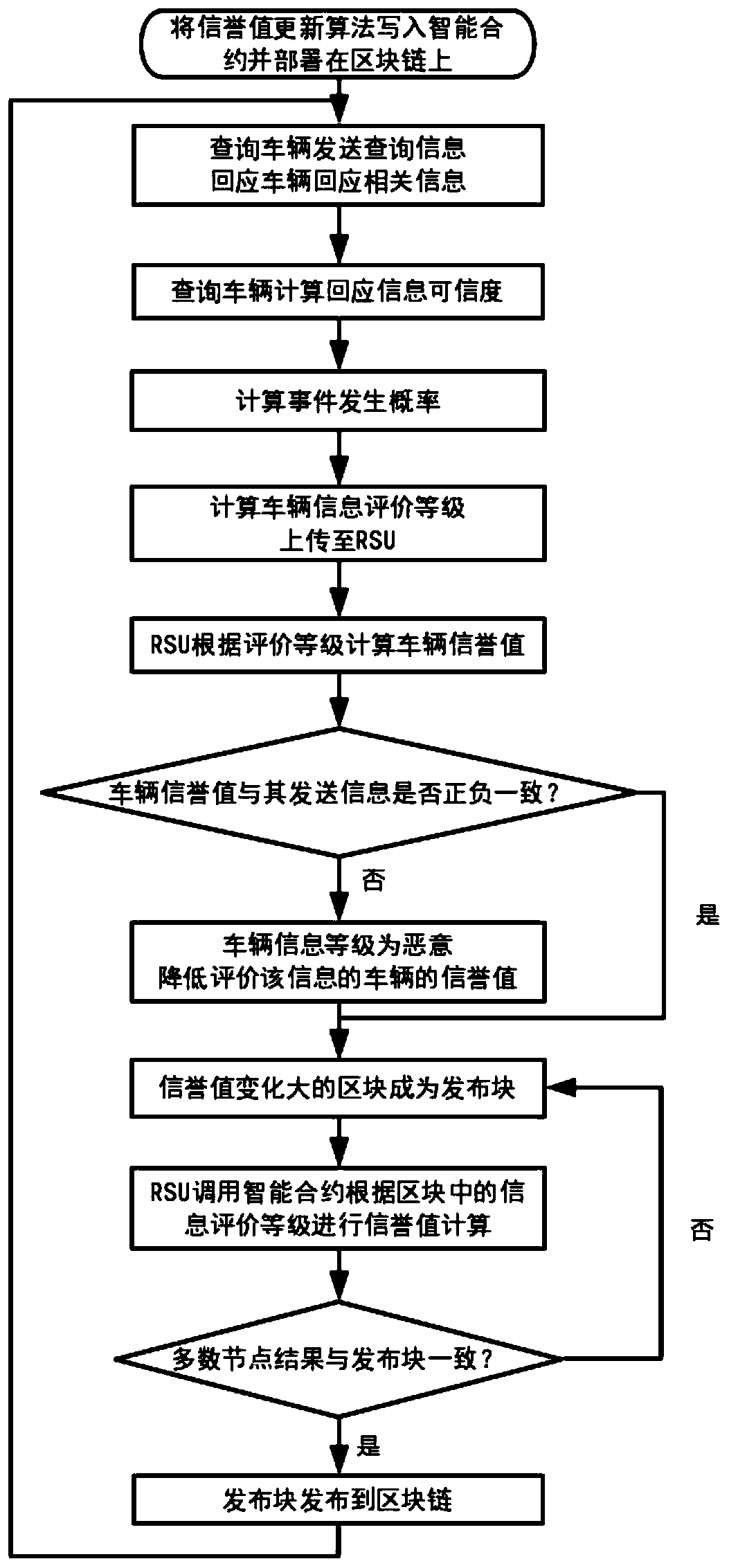
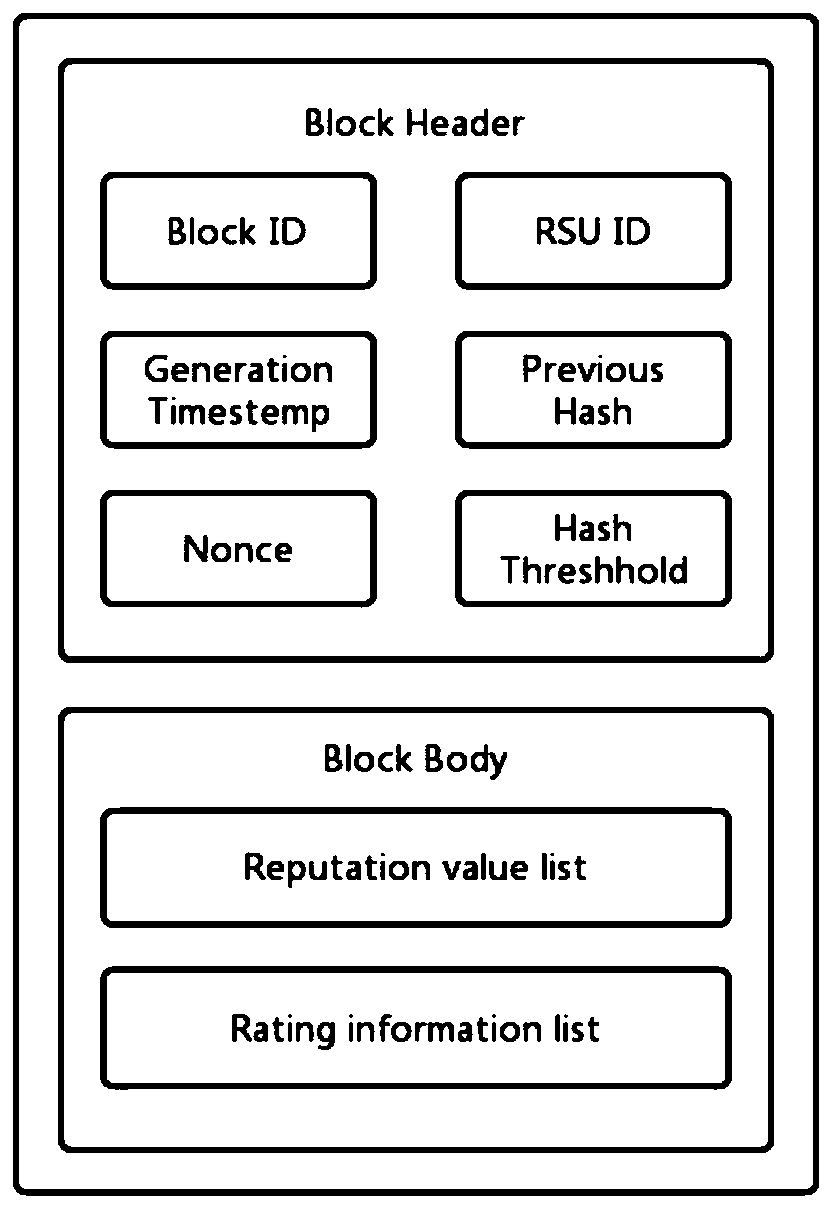
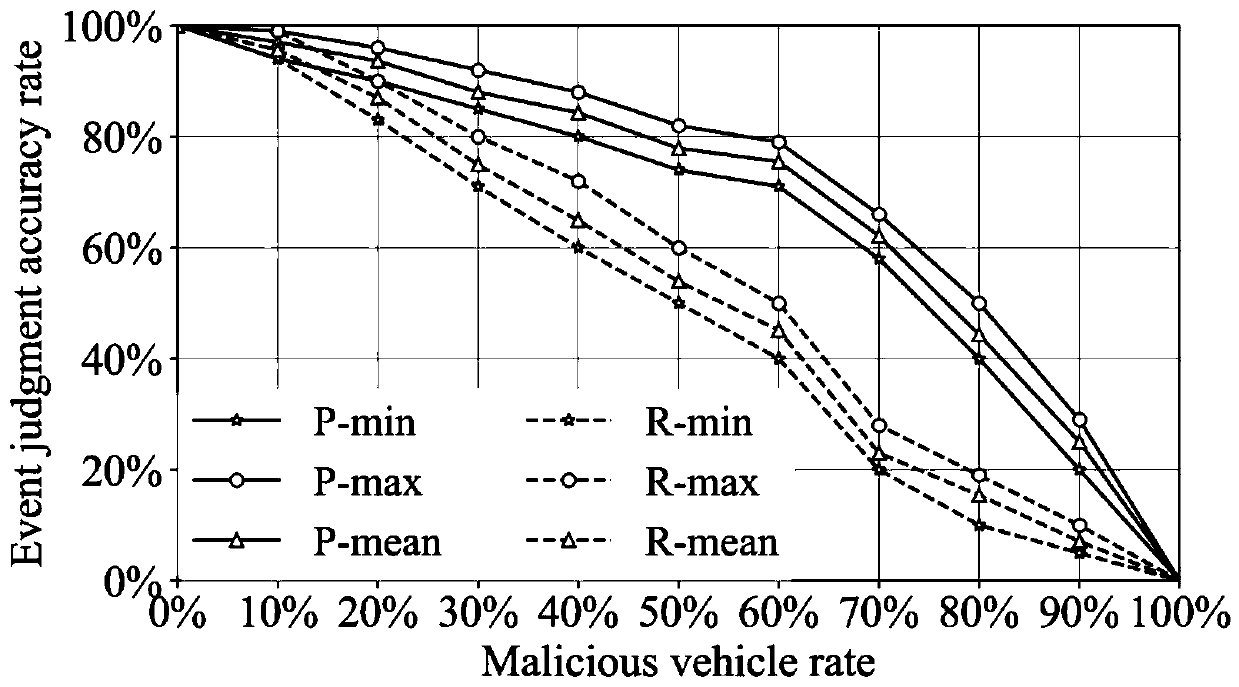
The invention discloses an Internet-of-Vehicles trust management method based on a block chain, and the method comprises the steps: firstly calculating the credibility of received vehicle informationrelated to an event, judging the occurrence probability of each event through the credibility of the vehicle information, generating a rating for transmitted information, and uploading the rating of the vehicle information to nearby RSUs; enabling the RSU to call a reputation value updating method in an intelligent contract deployed on a block chain to calculate a vehicle reputation value, whereinthe calculated vehicle reputation value and the collected rating information are all packaged into a block; through a consensus mechanism combining PoW and PoS, ensuring RSUs with larger change of vehicle reputation values to serve as miner nodes to publish blocks; and enabling other RSUs to re-use the reputation value updating method of the smart contract to re-calculate the rating in the release block, and if the calculation results of most nodes are consistent with the data in the release block, releasing the release block to the block chain to realize Internet-of-Vehicles trust management. According to the invention, the data security is ensured, and the accuracy of event judgment in the Internet of Vehicles is improved.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Flash memory error correction method and device
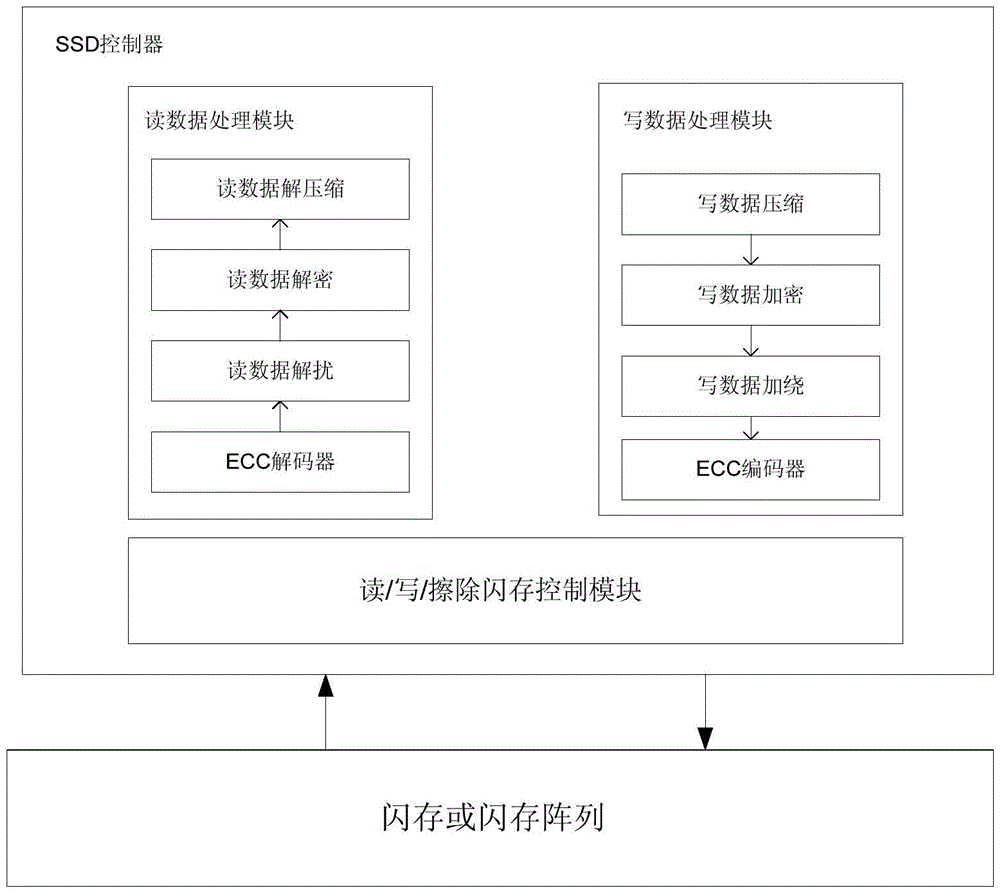
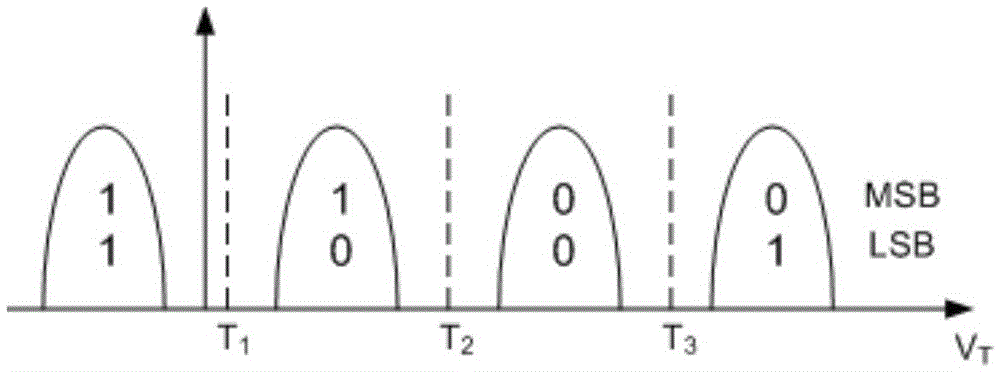
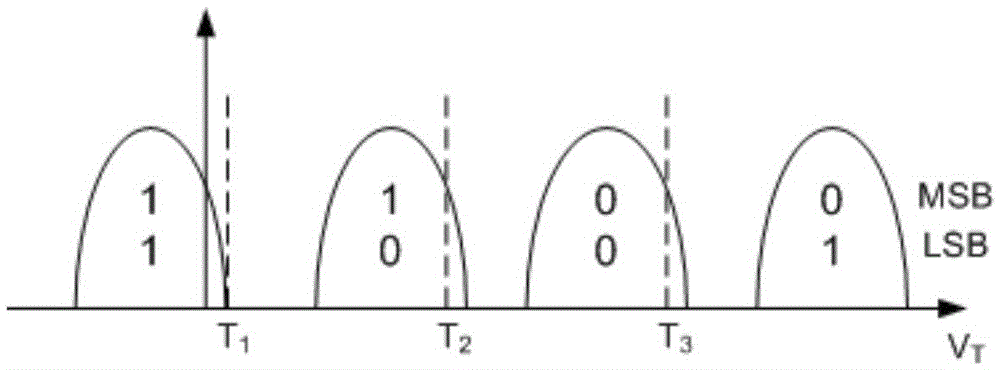
ActiveCN106816179AReduce credibilityIncrease success rateError detection/correctionError correction/detection using LDPC codesSolid-state driveError correcting
The invention provides a flash memory error correction method and device. The method comprises the steps of determining a first data bit in data obtained by reading a flash memory page by a (n+1)th voltage reading threshold value and data obtained by reading the flash memory page by a mth voltage reading threshold value, wherein the first data bit is a data bit which has different corresponding data in the same data bit in the data obtained by reading the flash memory page by the (n+1)th voltage reading threshold value and the data obtained by reading the flash memory page by the mth voltage reading threshold value, and further, the credibility of the first data bit in the data obtained by reading the flash memory page by the (n+1)th voltage reading threshold value; performing error correcting decoding on data obtained by reading the flash memory page by the (n+1)th voltage reading threshold value according to the credibility of the first data bit after regulation. The data obtained by reading the same flash memory page twice is used in a combined way; the credibility of the data bit corresponding to the data with different data bits is reduced, so that the error correcting decoding success rate is effectively improved; the performance of an SSD (solid state drive) storage system can be greatly improved.
Owner:HUAWEI TECH CO LTD
Transient power disturbance identification method based on S conversion and improved SVM algorithm
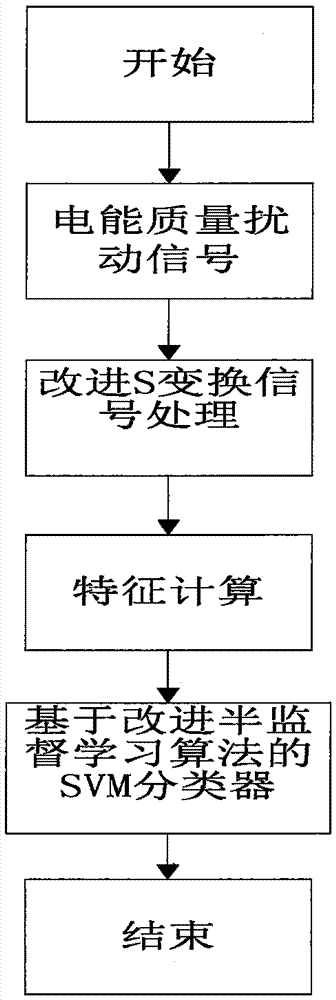
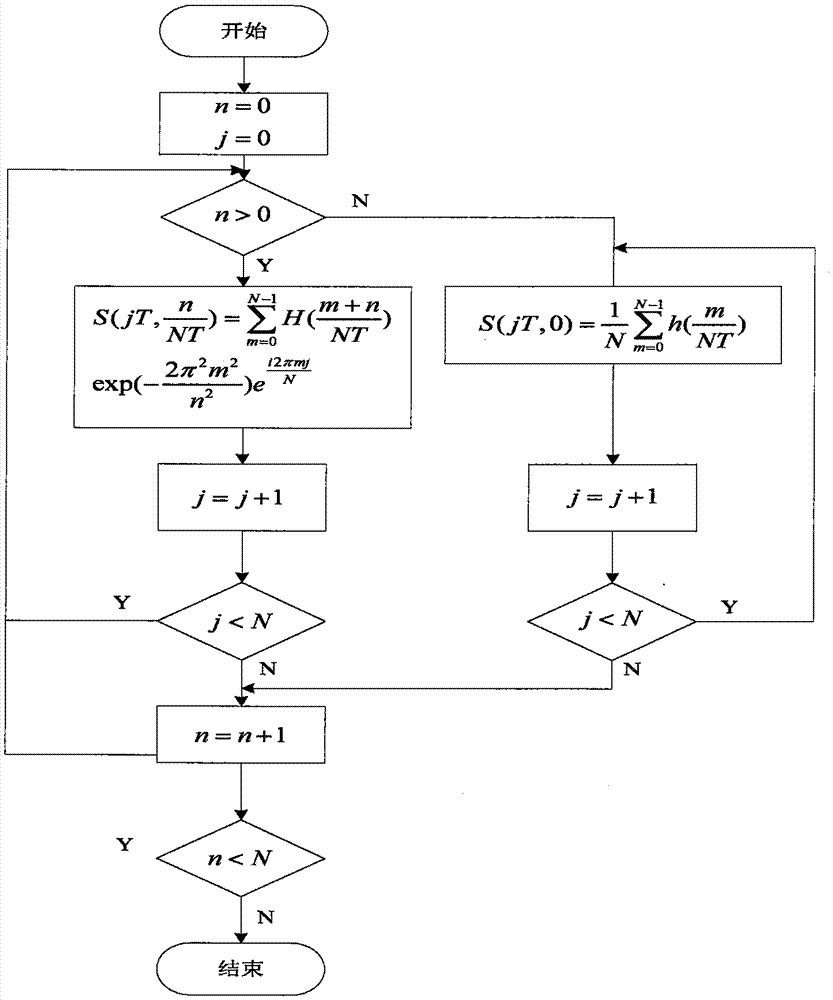
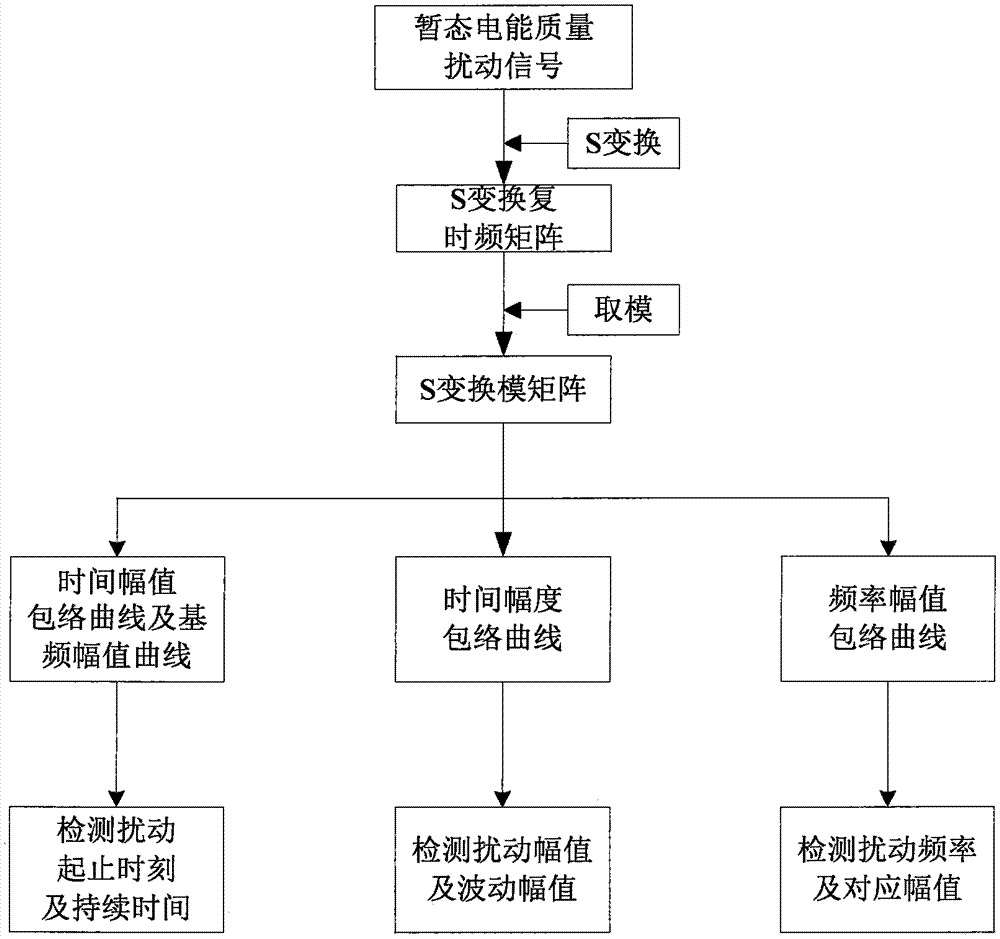
InactiveCN105447502AGuaranteed recognition accuracyImprove recognition accuracyCharacter and pattern recognitionTransient statePower quality
The invention discloses a transient power disturbance identification method based on S conversion and an improved SVM algorithm. The method comprises the following steps: (1), carrying out processing on a disturbance signal based on improved S conversion; (2), extracting a disturbance signal characteristic; and (3) designing an SVM classifier based on a semi-supervised learning algorithm to classify samples. Compared with the previous power quality disturbance classification method, the provided method has beneficial effects: on the premise that the identification accuracy of the SVM algorithm is guaranteed, the improved semi-supervised learning algorithm is introduced into the sample with low reliability in the SVM algorithm, so that the identification accuracy of the disturbance signal can be improved; and advantages of good scientific and reasonable performances, high adaptability, and great promotional value and the like are realized.
Owner:STATE GRID CORP OF CHINA +3
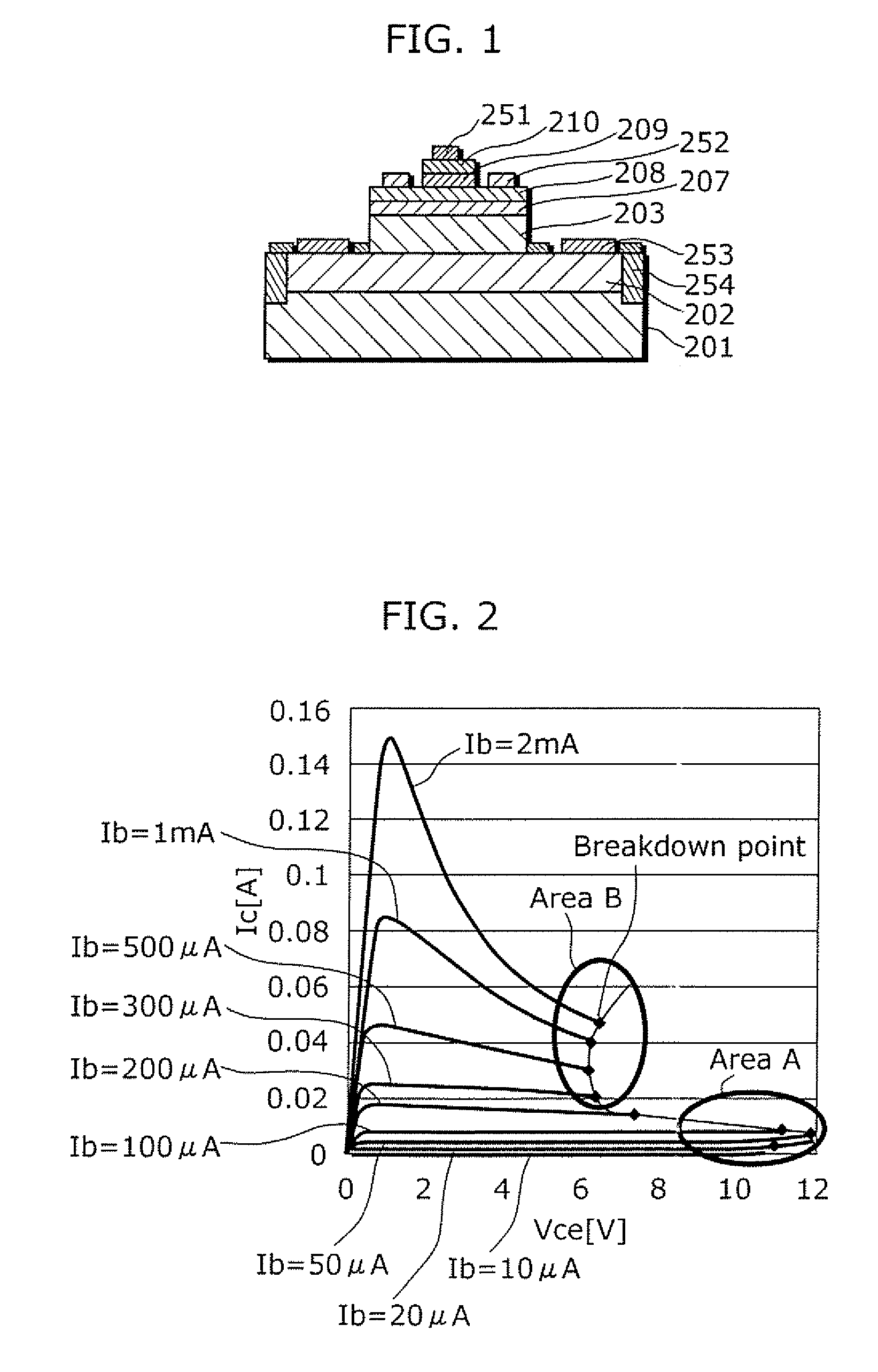
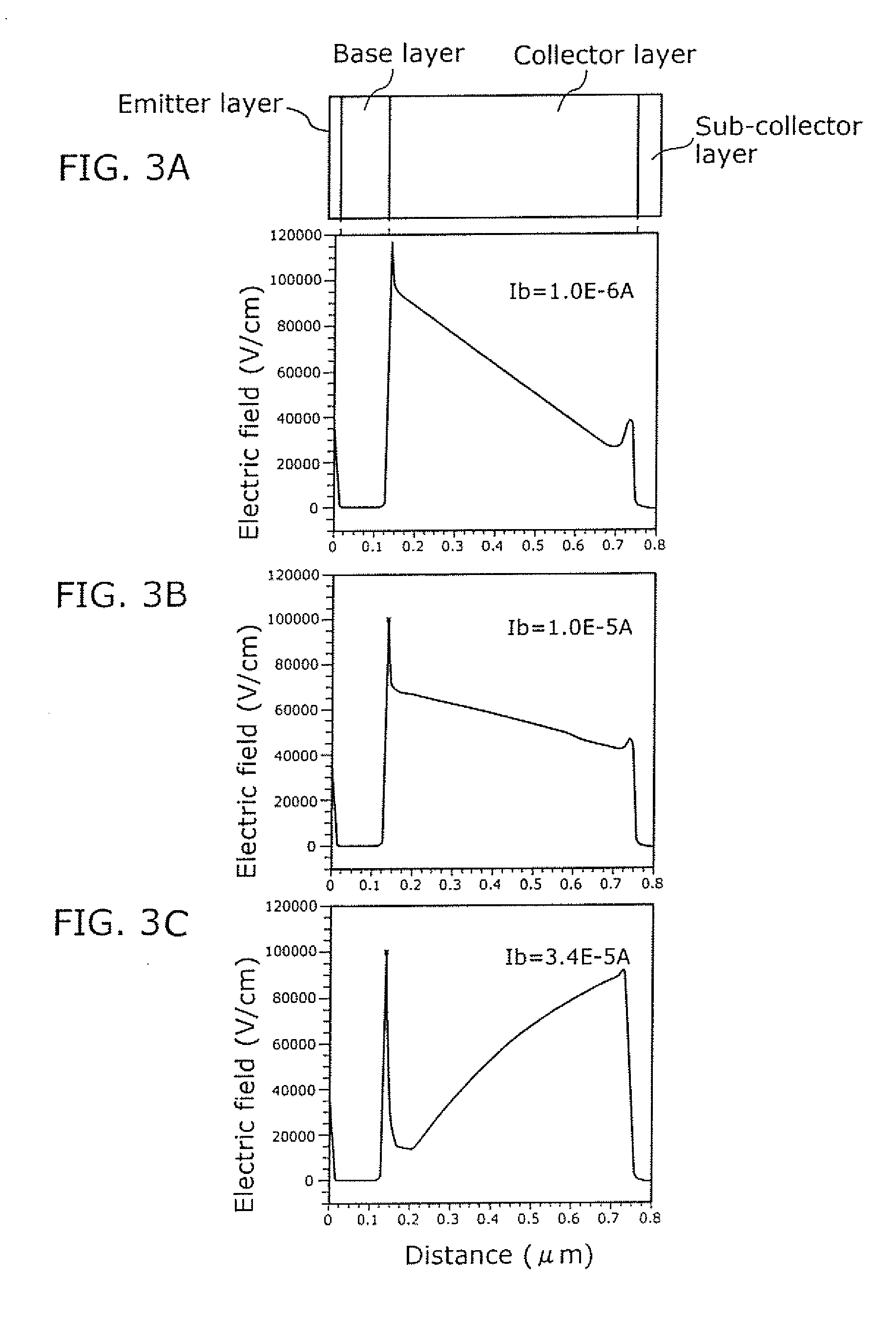
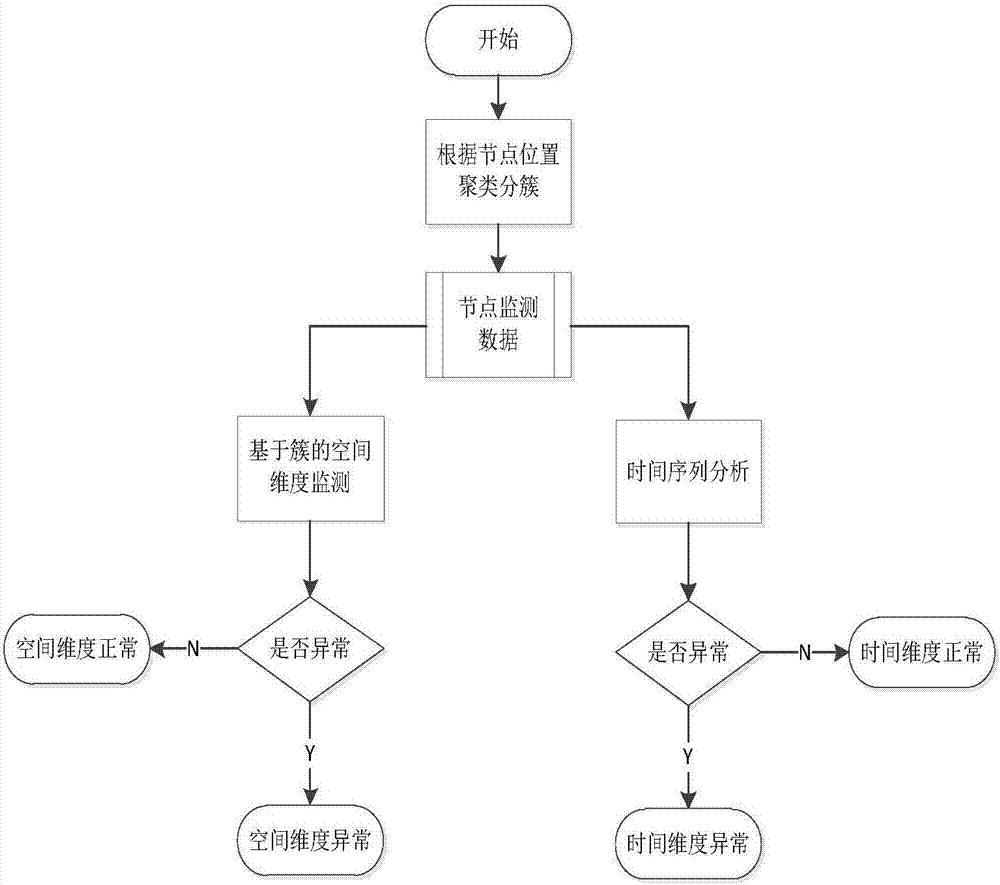
Heterojunction bipolar transistor and manufacturing method thereof
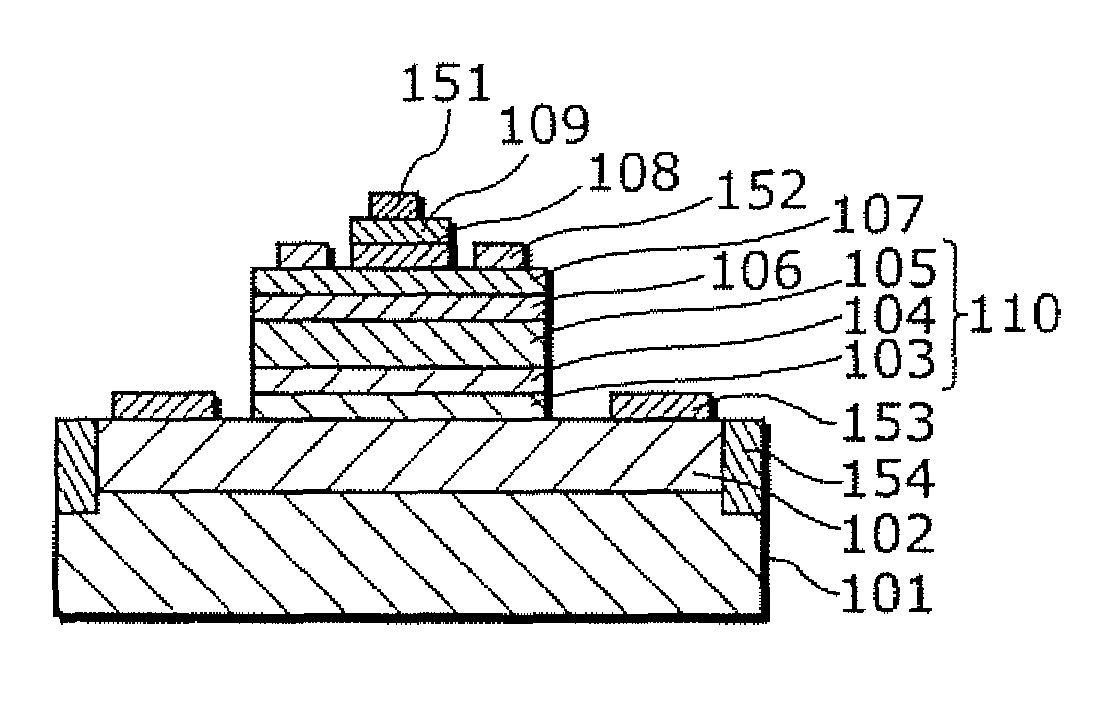
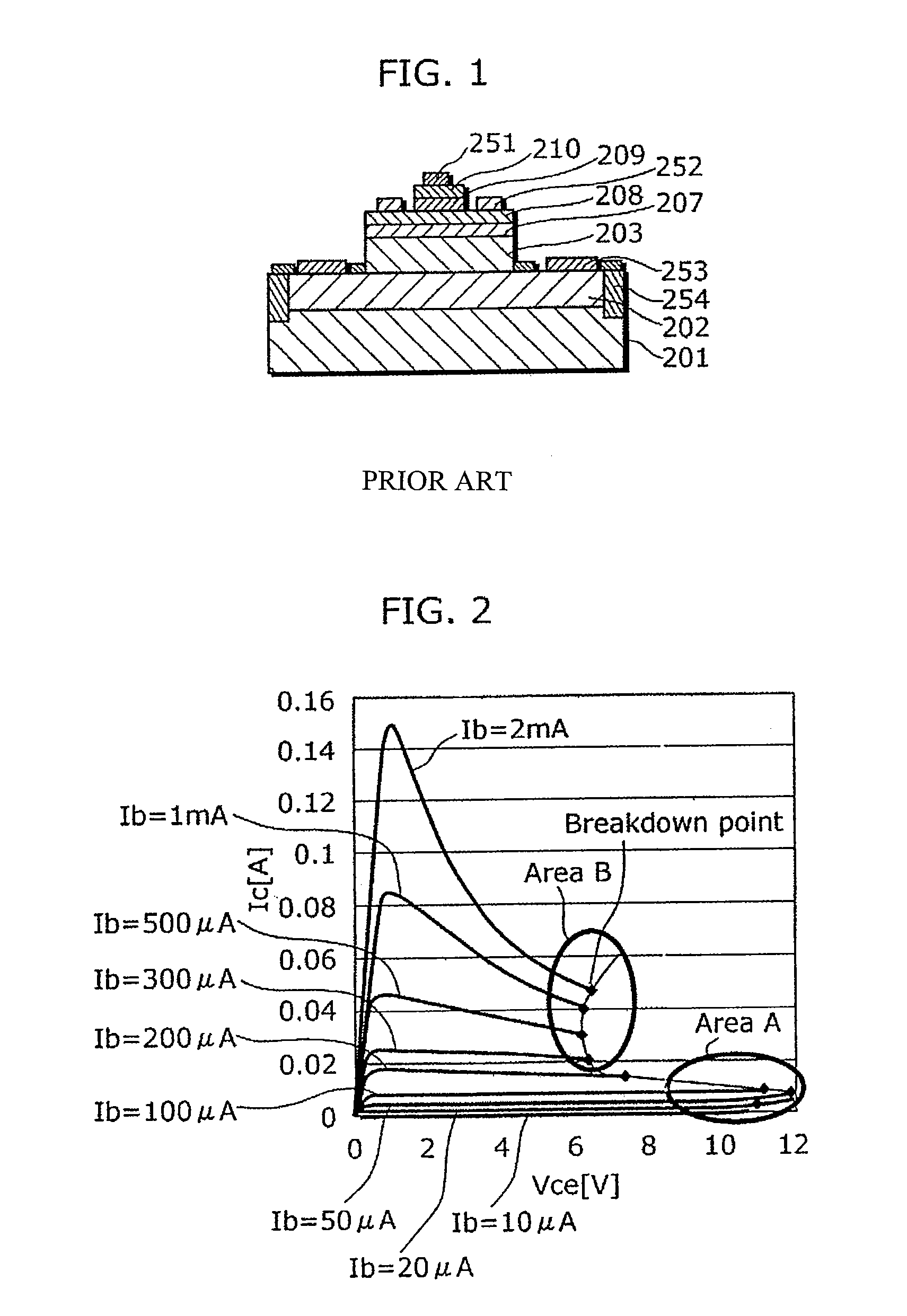
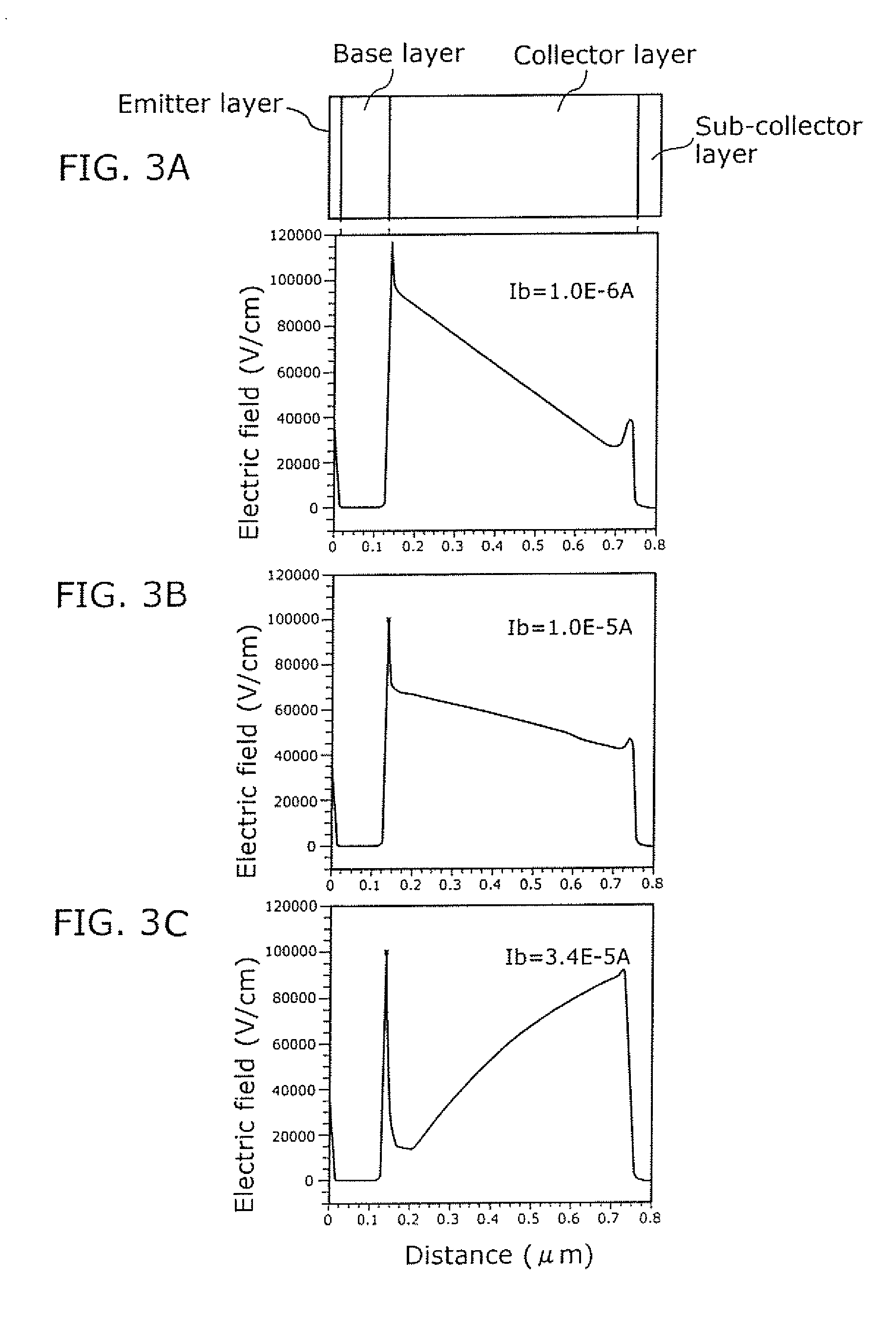
ActiveUS7728357B2Improve the level ofGood reproducibilitySemiconductor devicesOptoelectronicsImpurity
The object of the present invention is to provide a heterojunction bipolar transistor with high breakdown tolerance which can be manufactured at a high reproducibility and a high yield, the heterojunction bipolar transistor includes: a sub-collector layer; a collector layer formed on the sub-collector layer; a base layer formed on the collector layer; and an emitter layer, which is formed on the base layer and is made of a semiconductor that has a larger bandgap than a semiconductor of the base layer, in which the collector layer includes: a first collector layer formed on the sub-collector layer; a second collector layer formed on the first collector layer; and a third collector layer formed between the second collector layer and the base layer, a semiconductor of the first collector layer differs from semiconductors of the third collector layer and the second collector layer, and an impurity concentration of the second collector layer is lower than an impurity concentration of the sub-collector layer and higher than an impurity concentration of the third collector layer.
Owner:PANASONIC SEMICON SOLUTIONS CO LTD
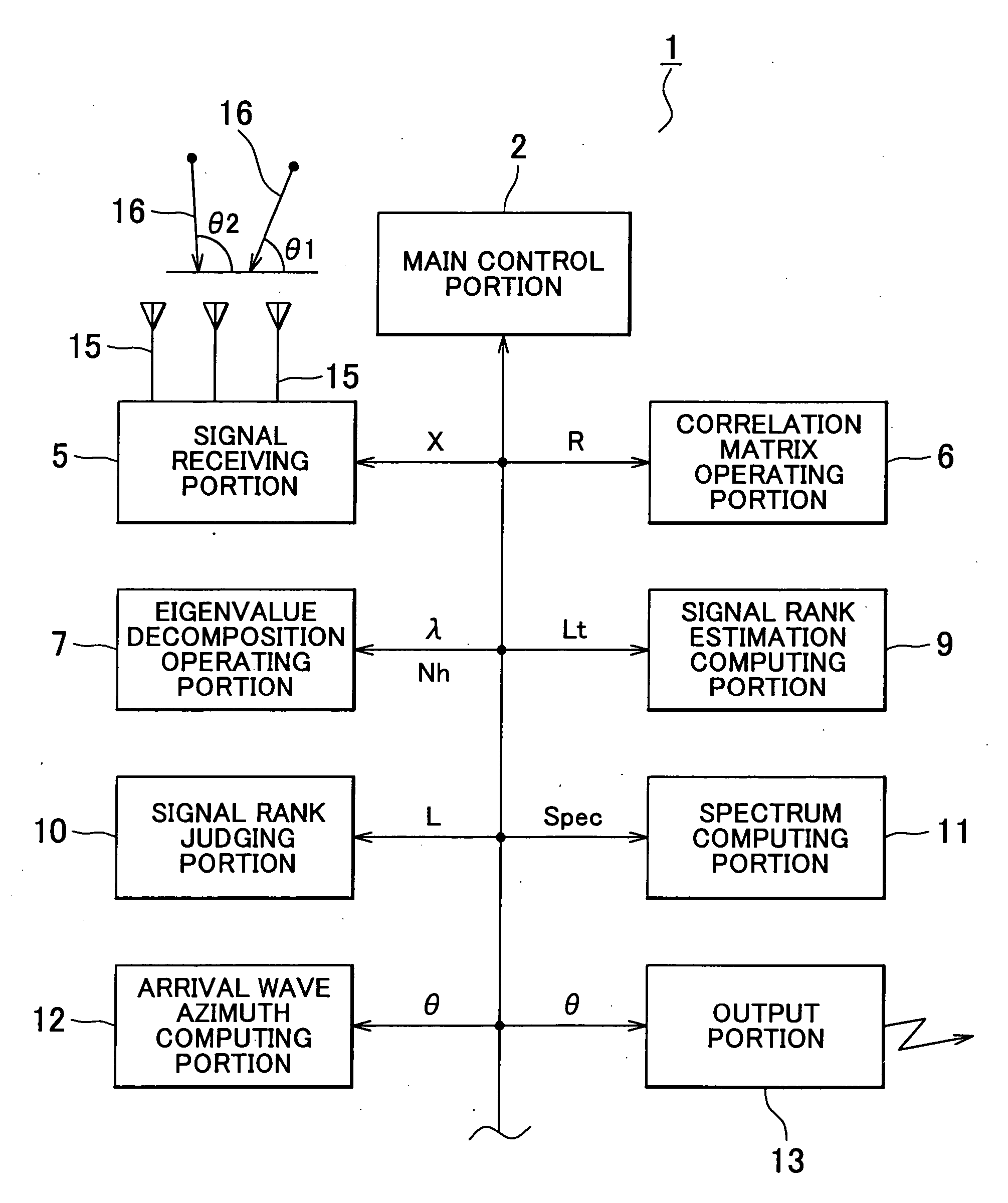
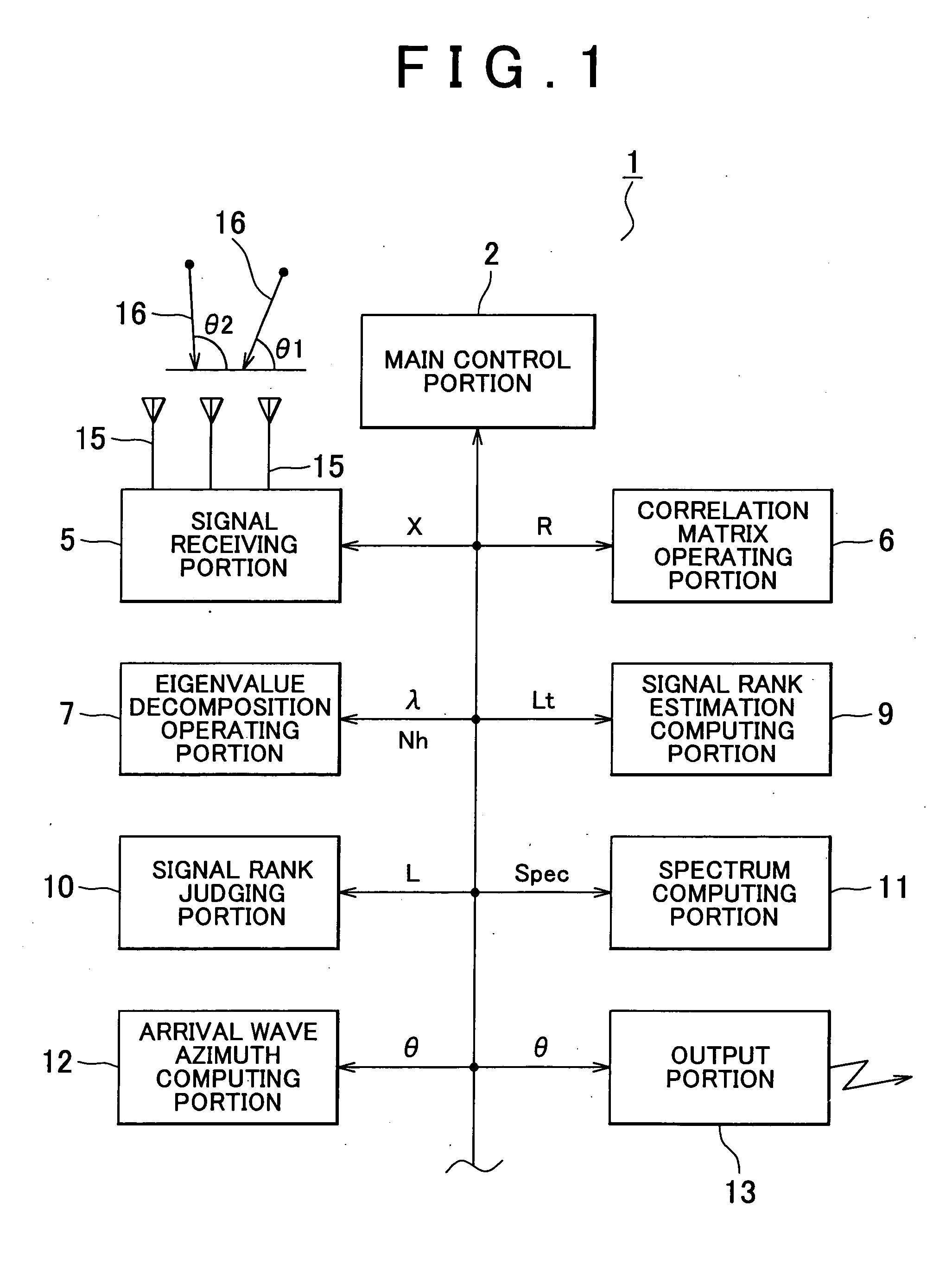
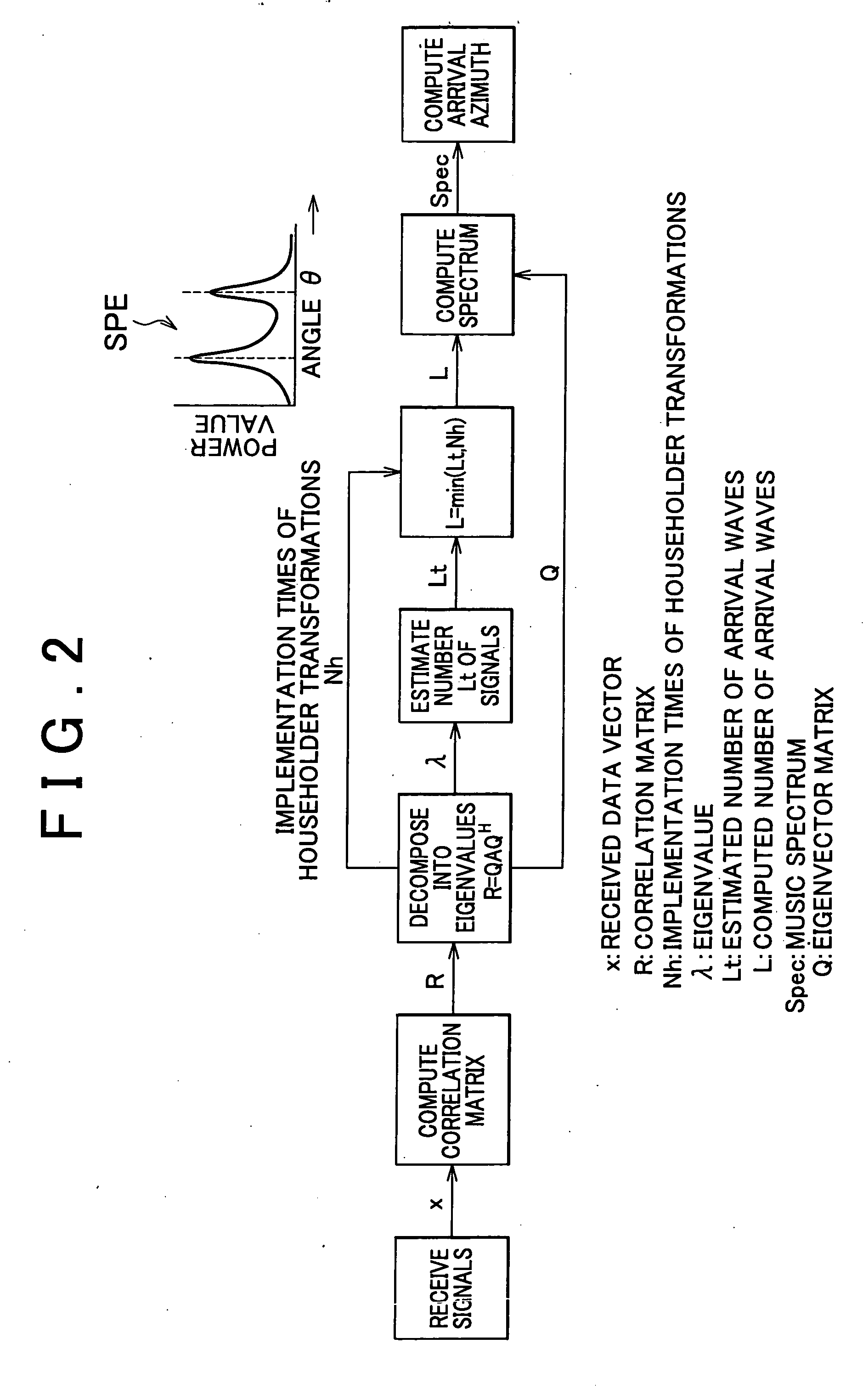
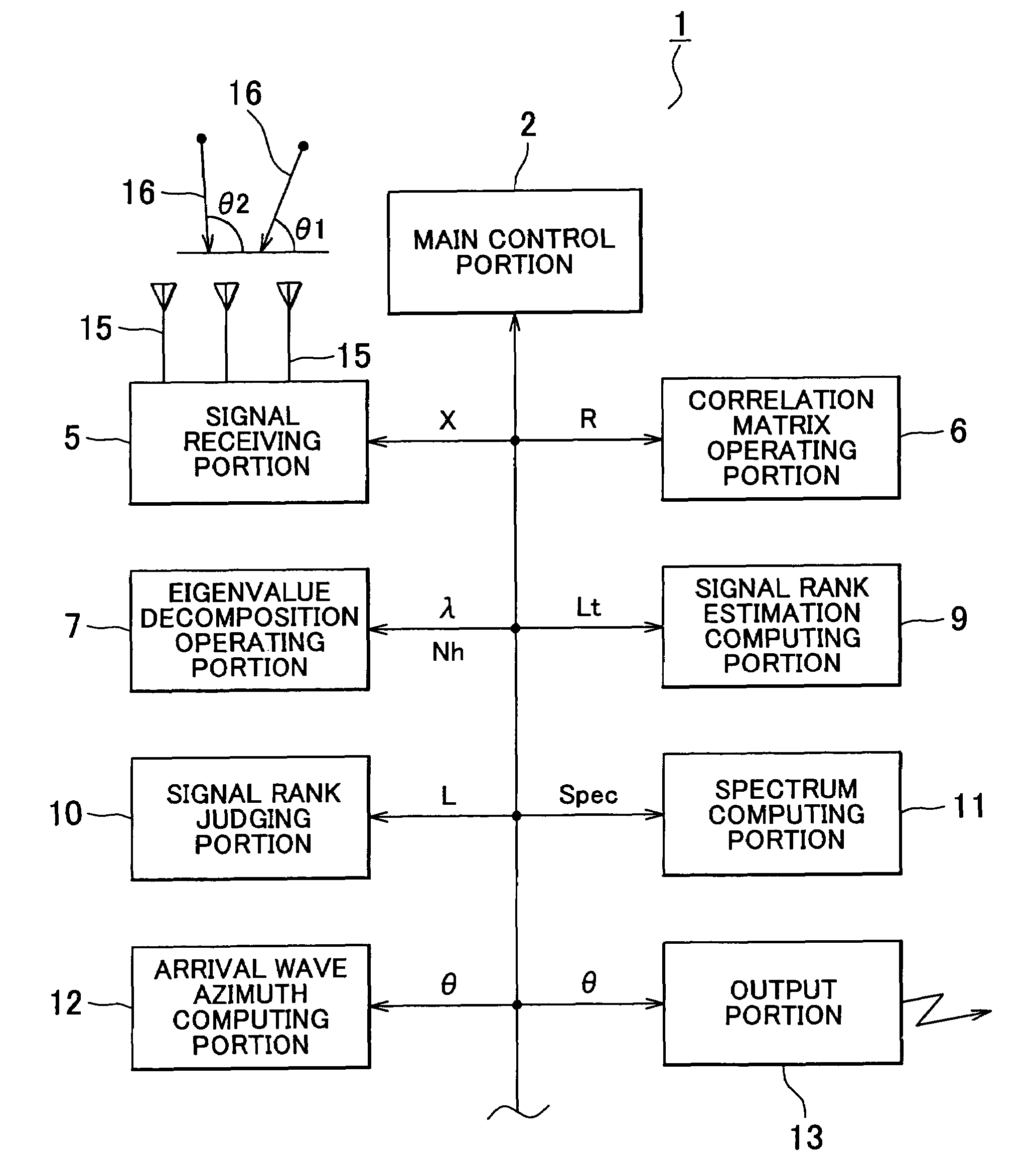
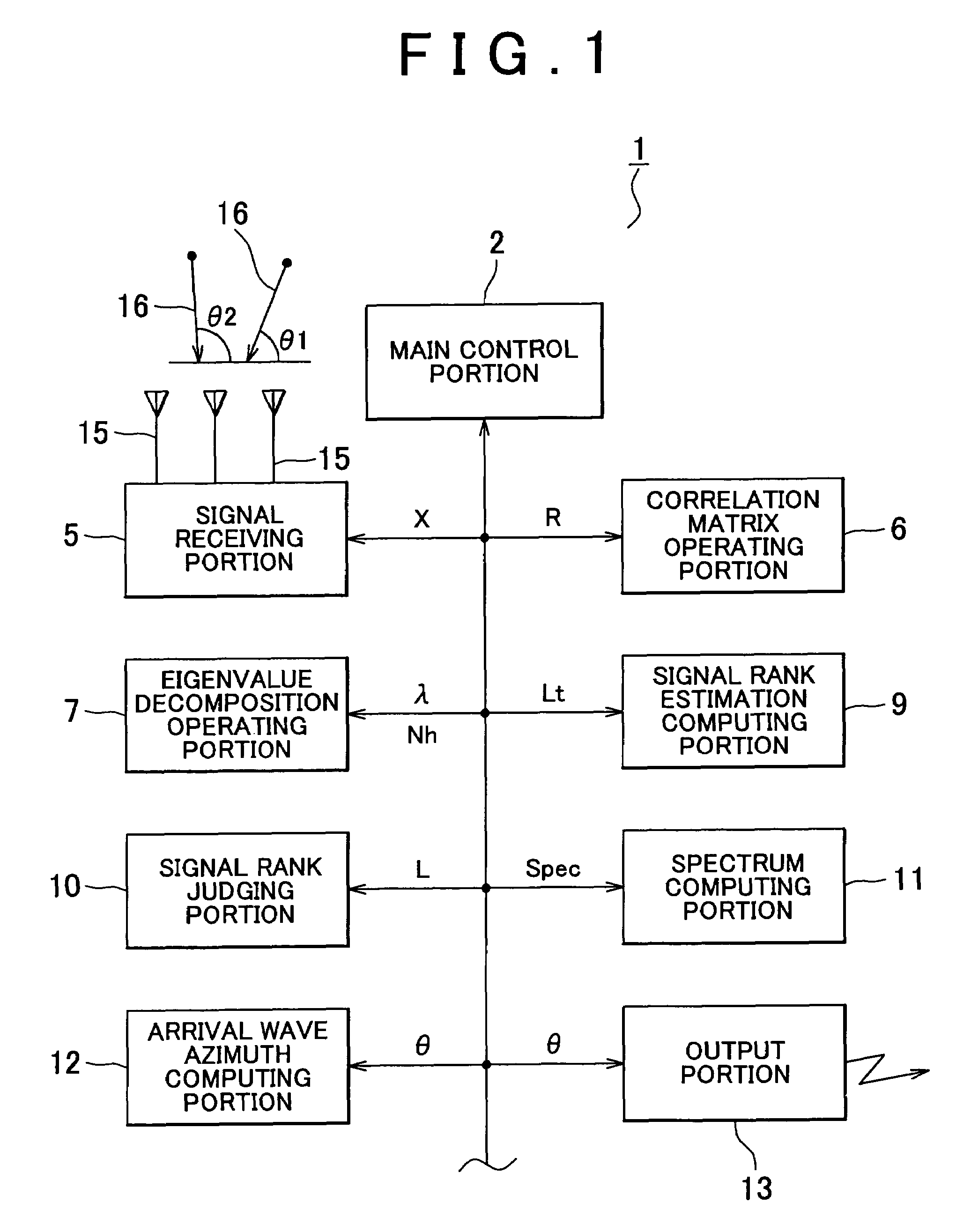
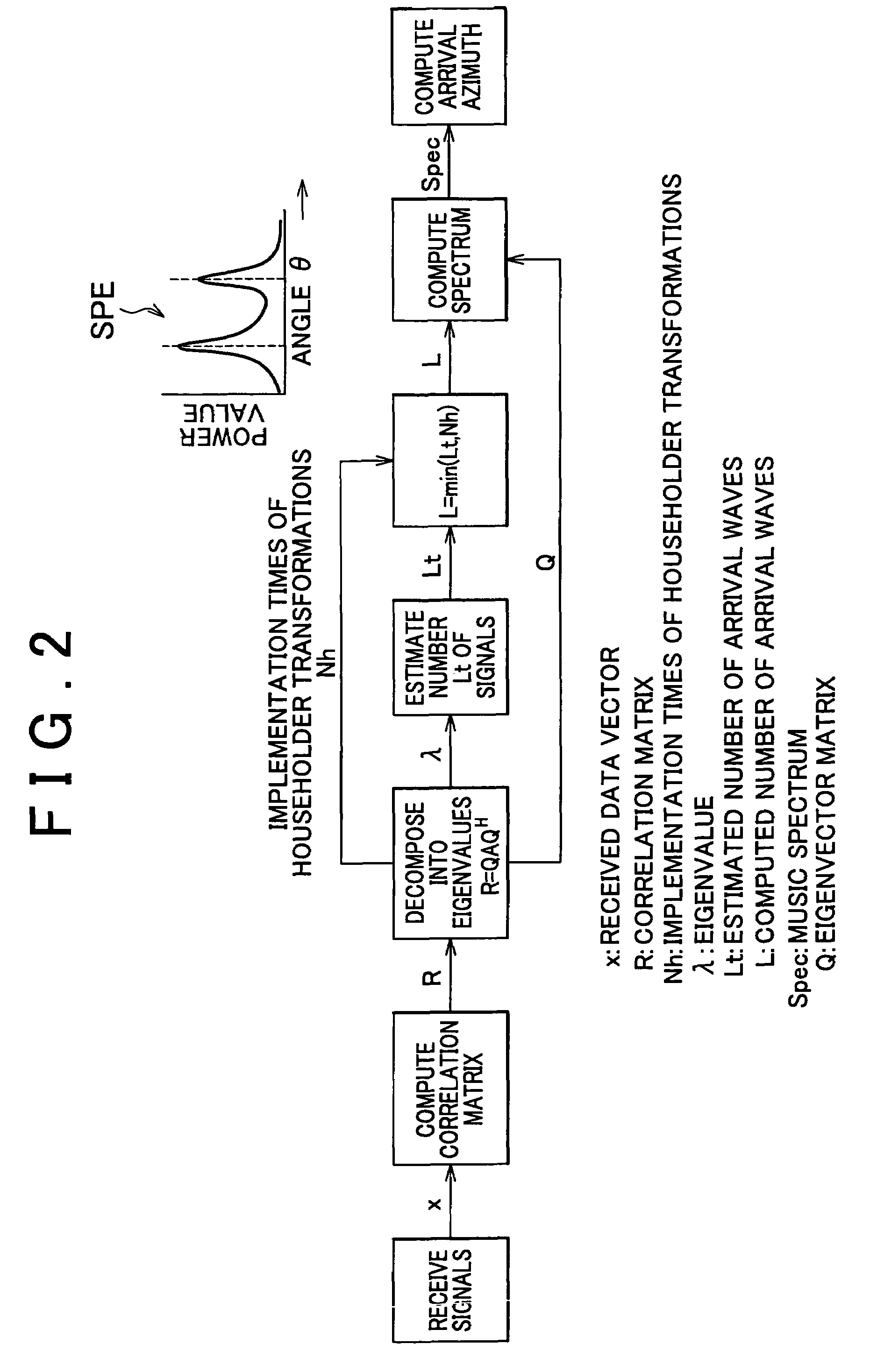
Apparatus for estimating direction of arrival wave
ActiveUS20060224655A1Operation efficiency can be improvedReduce credibilityMulti-channel direction-finding systems using radio wavesComputation using non-contact making devicesFeature vectorComputer science
Apparatus has means for computing correlation matrix of arrival wave, means for producing a matrix for obtaining eigenvalues and a matrix for obtaining eigenvectors, means for computing column norms on the matrix which is a subject for Householder transformation, means for judging whether a maximum value of the column norms is the same as or lower than a predetermined threshold, means for repeating Householder transformation on the matrix only if the maximum value of the column norms is judged not to be the same or not to be lower, means for breaking Householder transformation if the maximum value is the same as or lower, means for further implementing Householder transformation and for obtaining the eigenvectors and the eigenvalues of the correlation matrix, and means for judging the number of the arrival waves from the implementation times of Householder transformation.
Owner:DENSO IT LAB +1
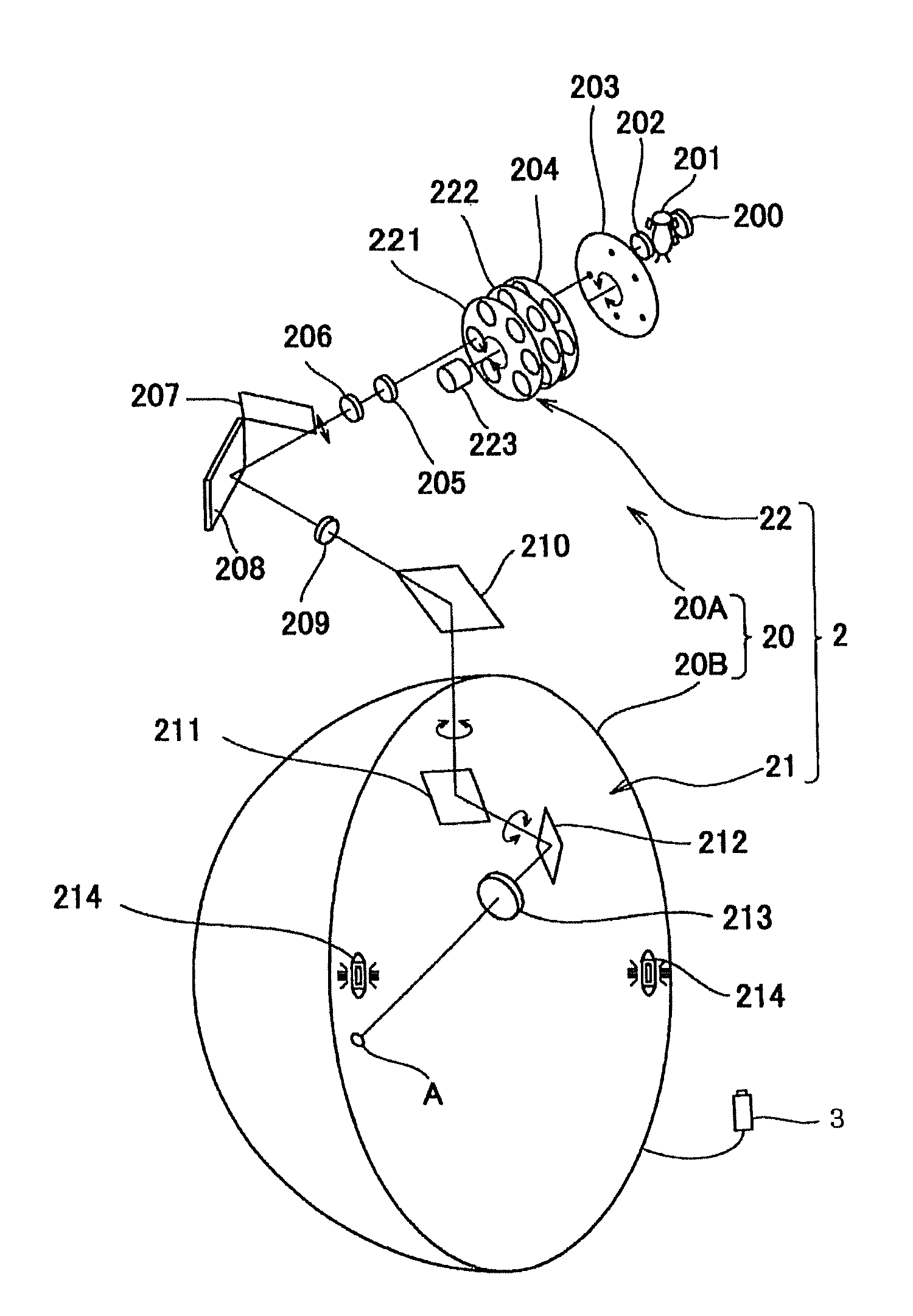
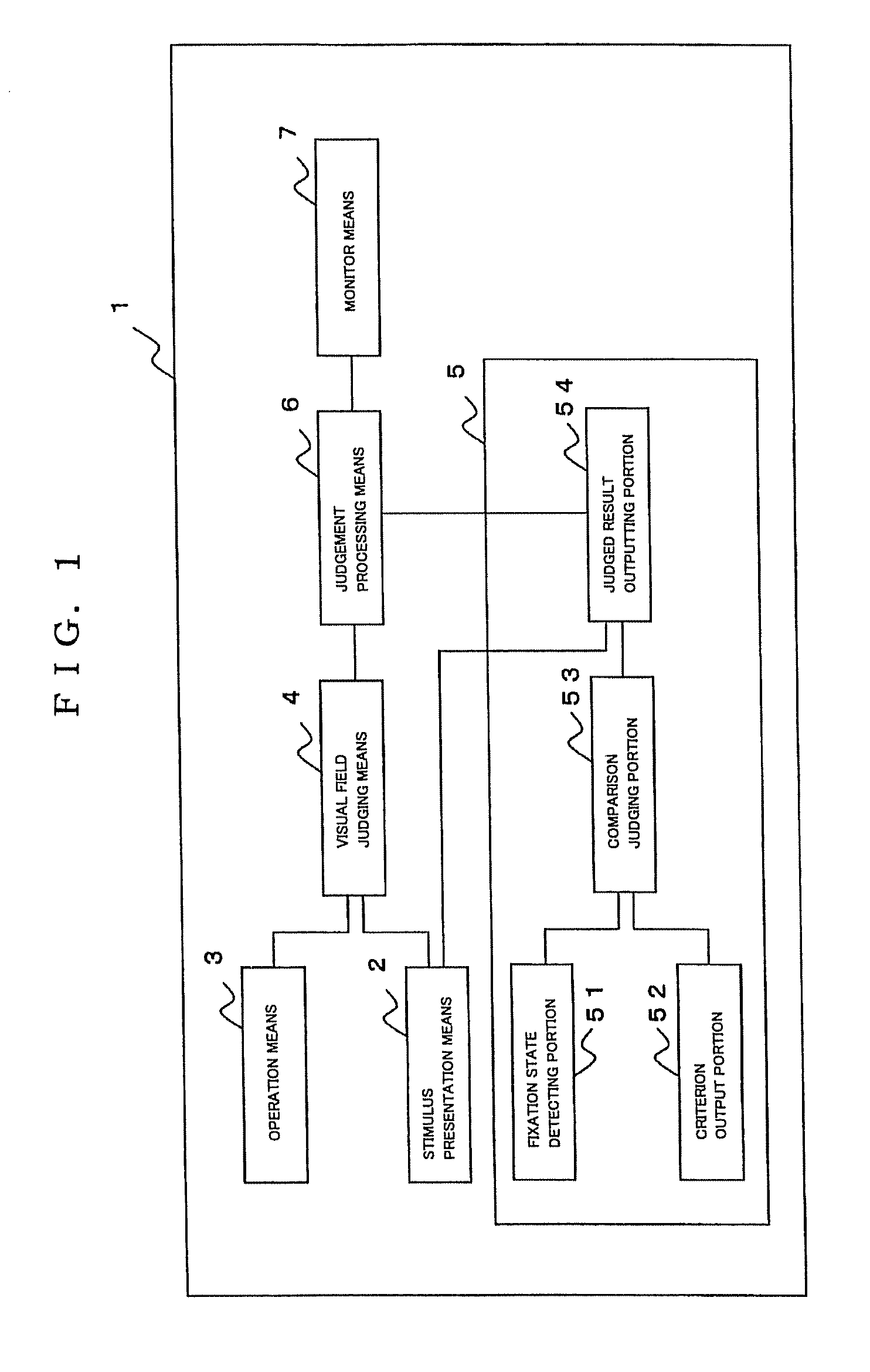
Perimeter
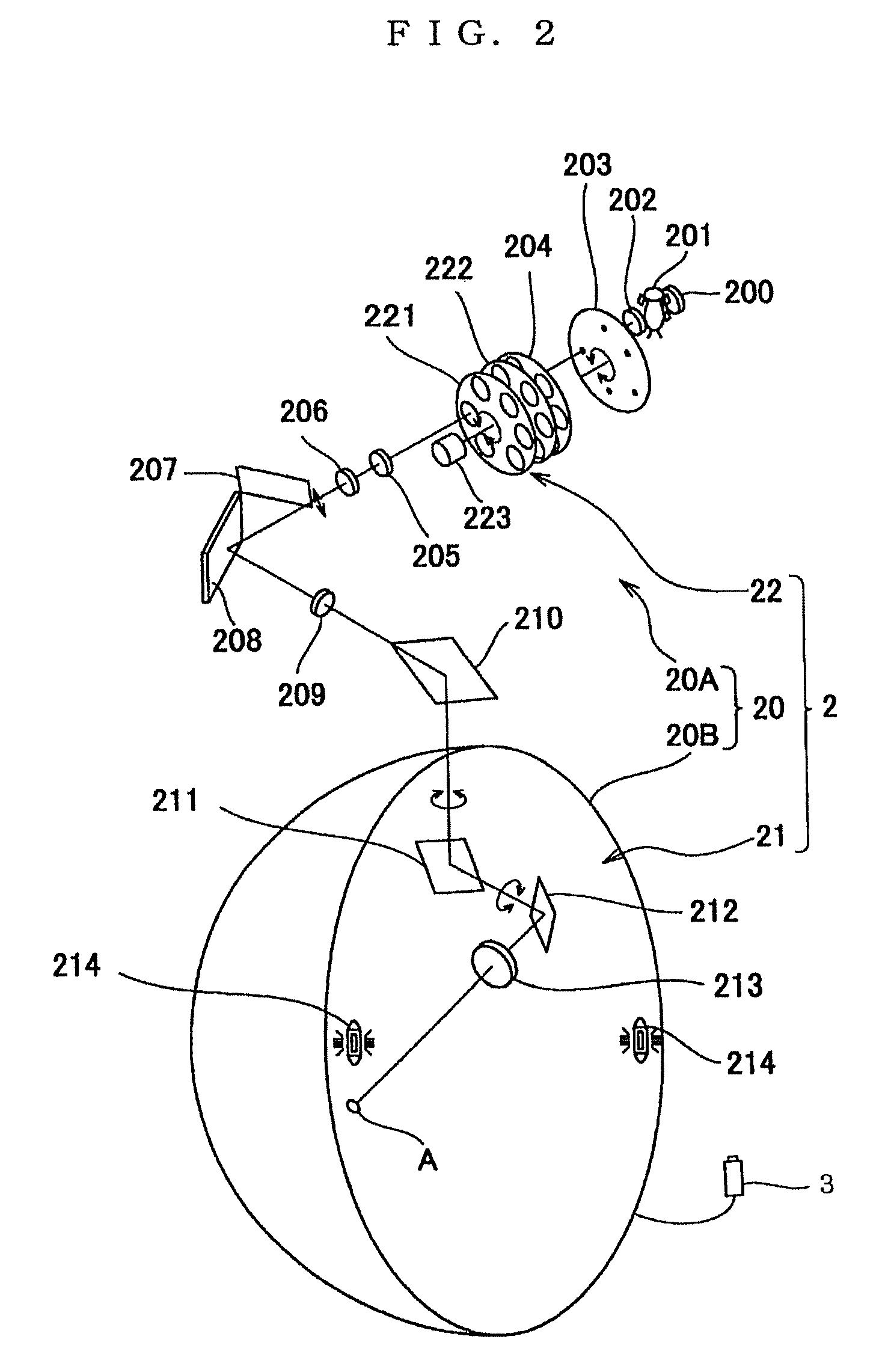
InactiveUS20100002192A1Increase credibilityReduce credibilityEye diagnosticsTest efficiencyTested time
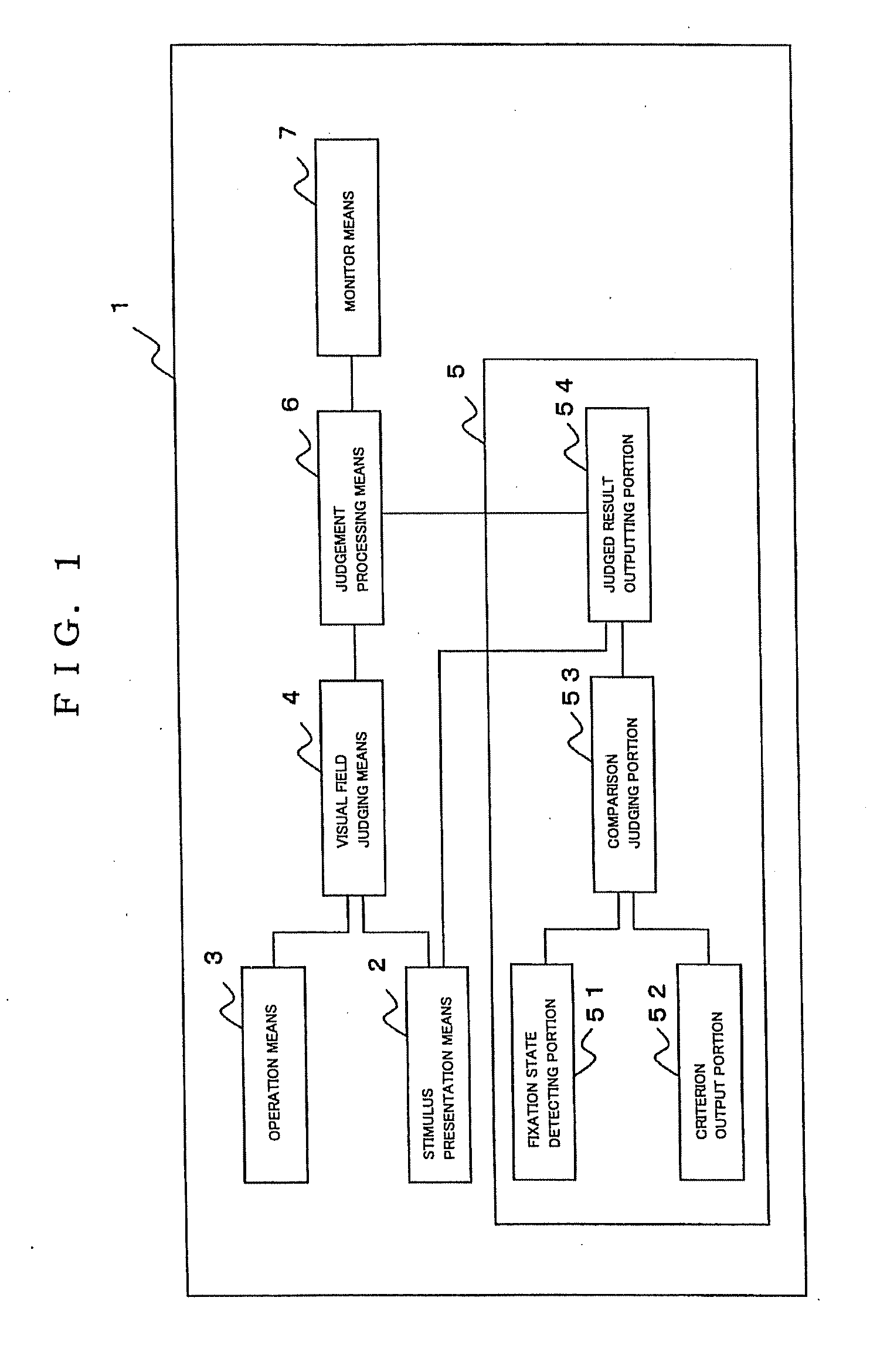
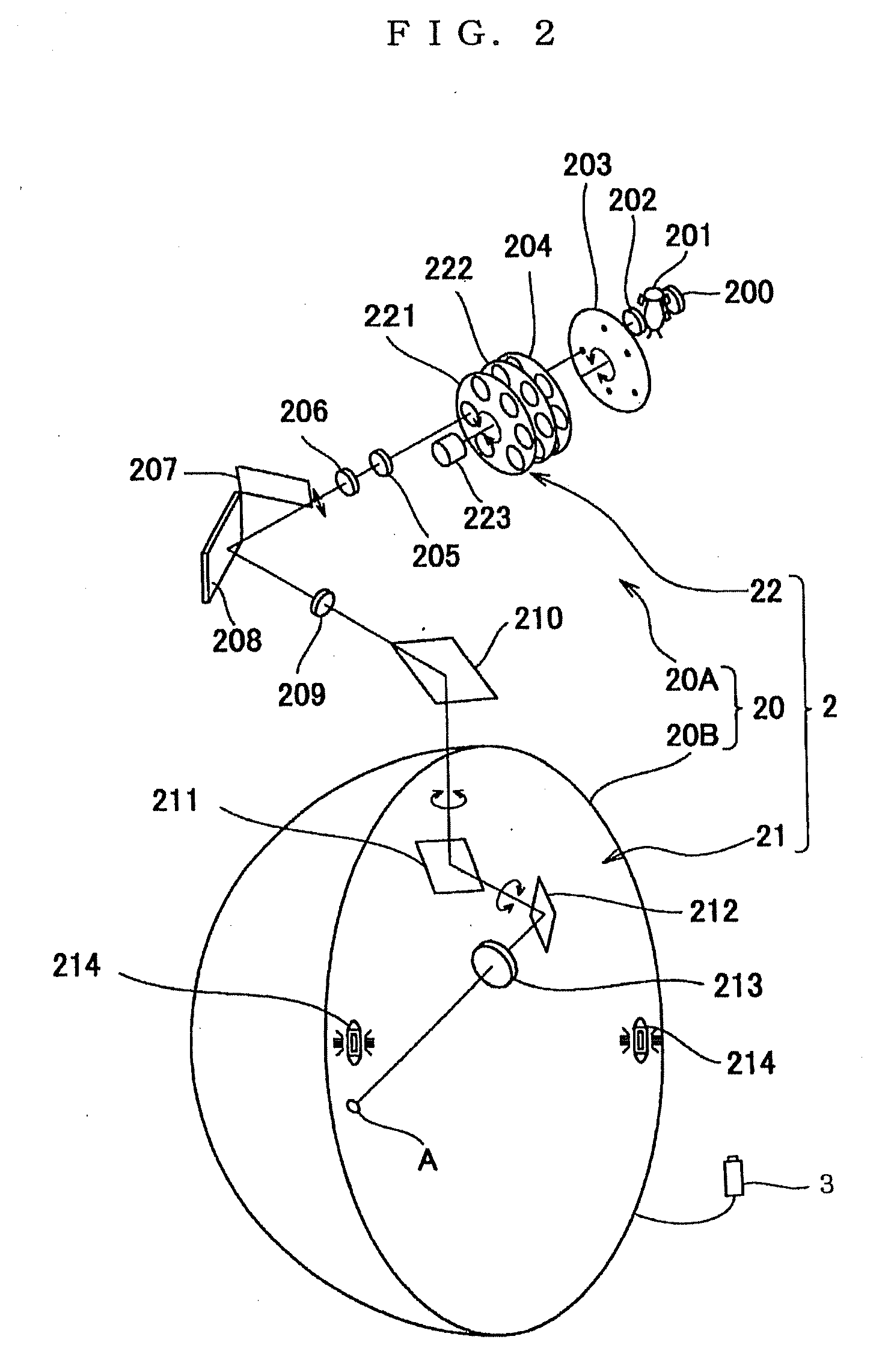
A perimeter has fixation state judging means for individually judging a fixation state of an examinee in connection with each presented stimulus, and the fixation state judging means individually judges the fixation state whenever the stimulus is presented. Even if defective fixation is judged, retest is conducted on only a point where the stimulus was presented, which was judged to be defective fixation. Then, examiner's burden and examinee's burden can be lightened, the test time can be made shorter and test efficiency can be improved in comparison with a case where the whole test is retried from the first as a conventional way.
Owner:KOWA CO LTD
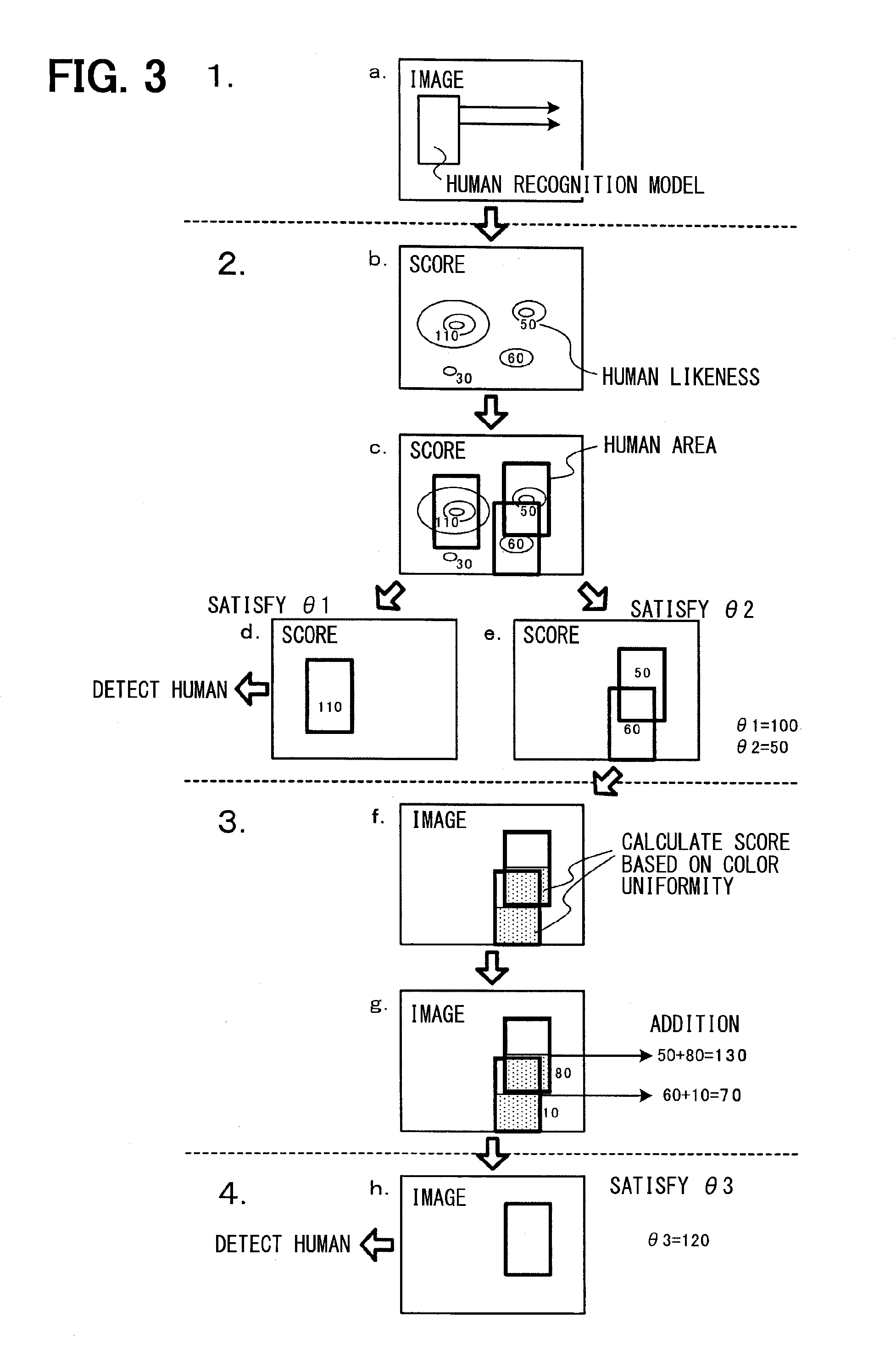
Human detection apparatus
ActiveUS20150117773A1Improve recognition rateReduce credibilityScene recognitionBiometric pattern recognitionPattern recognitionHuman body
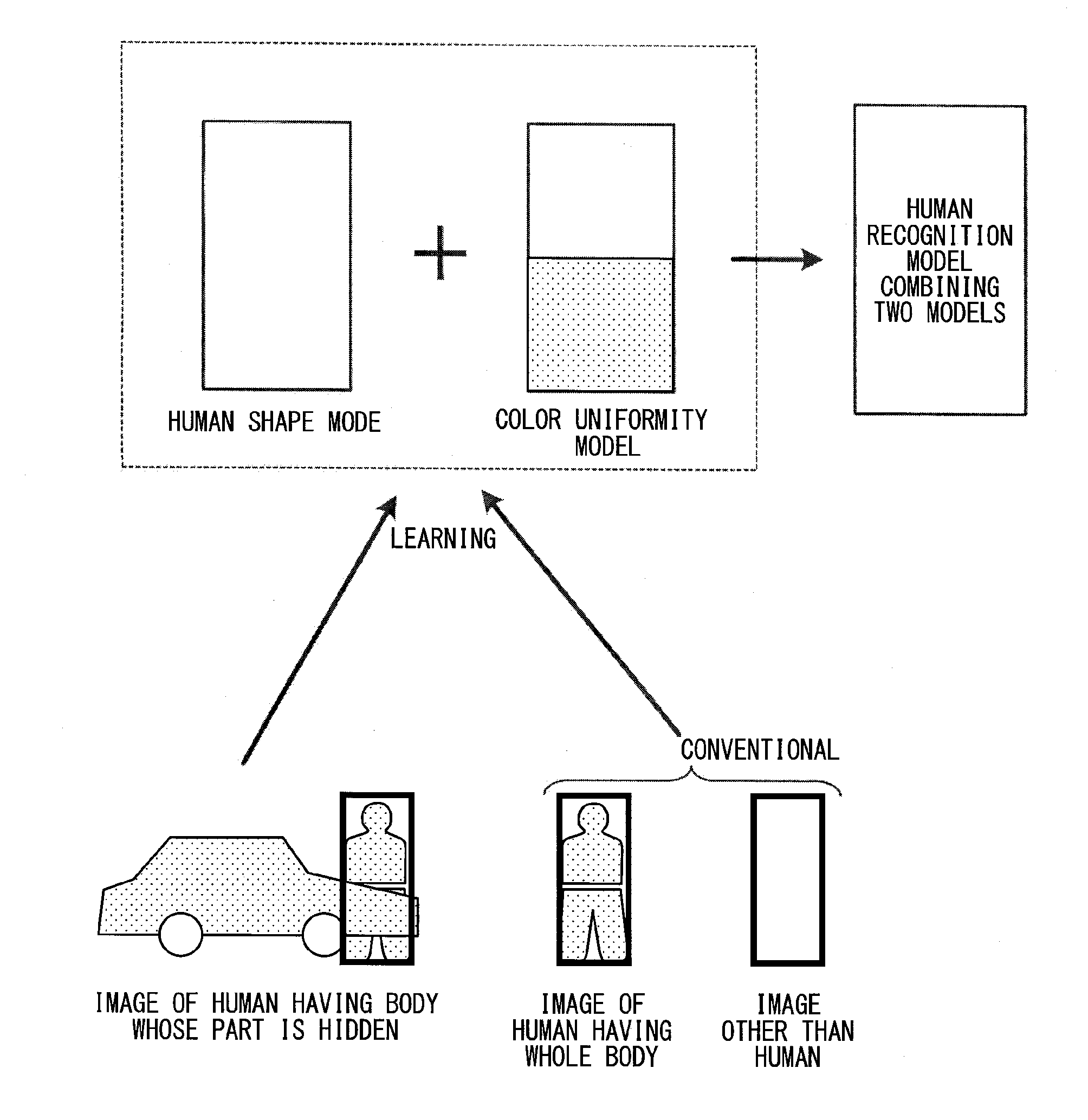
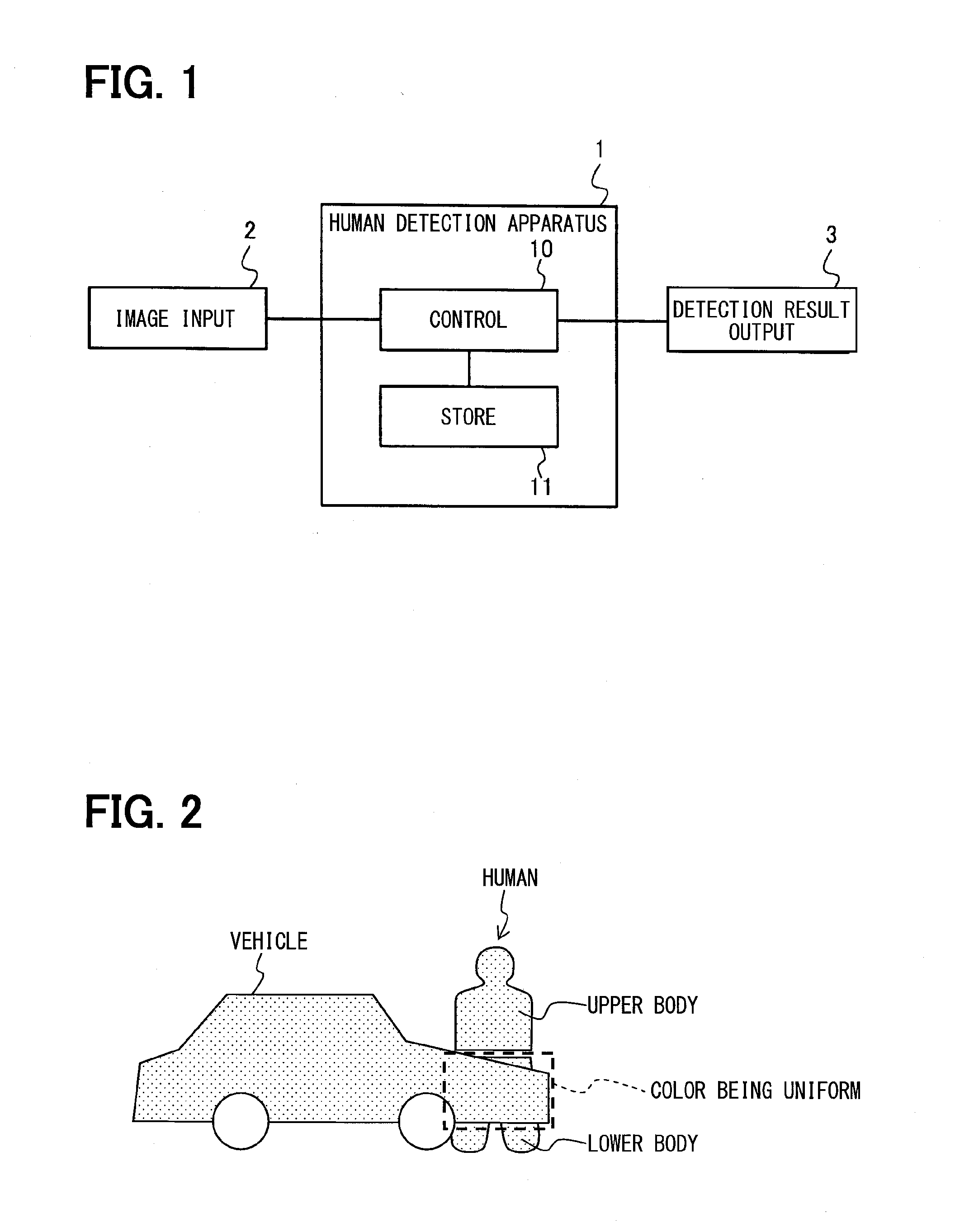
The knowledge that “the color of a vehicle body or guard rail is uniform” applies to the detection of a human, improving the detection performance of the human of which a part of the body is hidden. That is, it is determined whether or not a human candidate area specified based on the ordinary human recognition model has a specific part, e.g., an area corresponding to a lower body, exhibiting the high degree of color uniformity. When affirmed, the human candidate area is understood to be “a human of which a part of the body is hidden by a hood or a trunk” and recognized as a human, same as in the case where the body is not hidden.
Owner:DENSO CORP
Constructing method of incentive mechanism based on recommended node credibility computation
InactiveCN101626388APrevent common cheatingPrevent problems such as simple calculation of trust valueData switching networksComputer networkCalculation methods
Owner:NANJING UNIV OF POSTS & TELECOMM
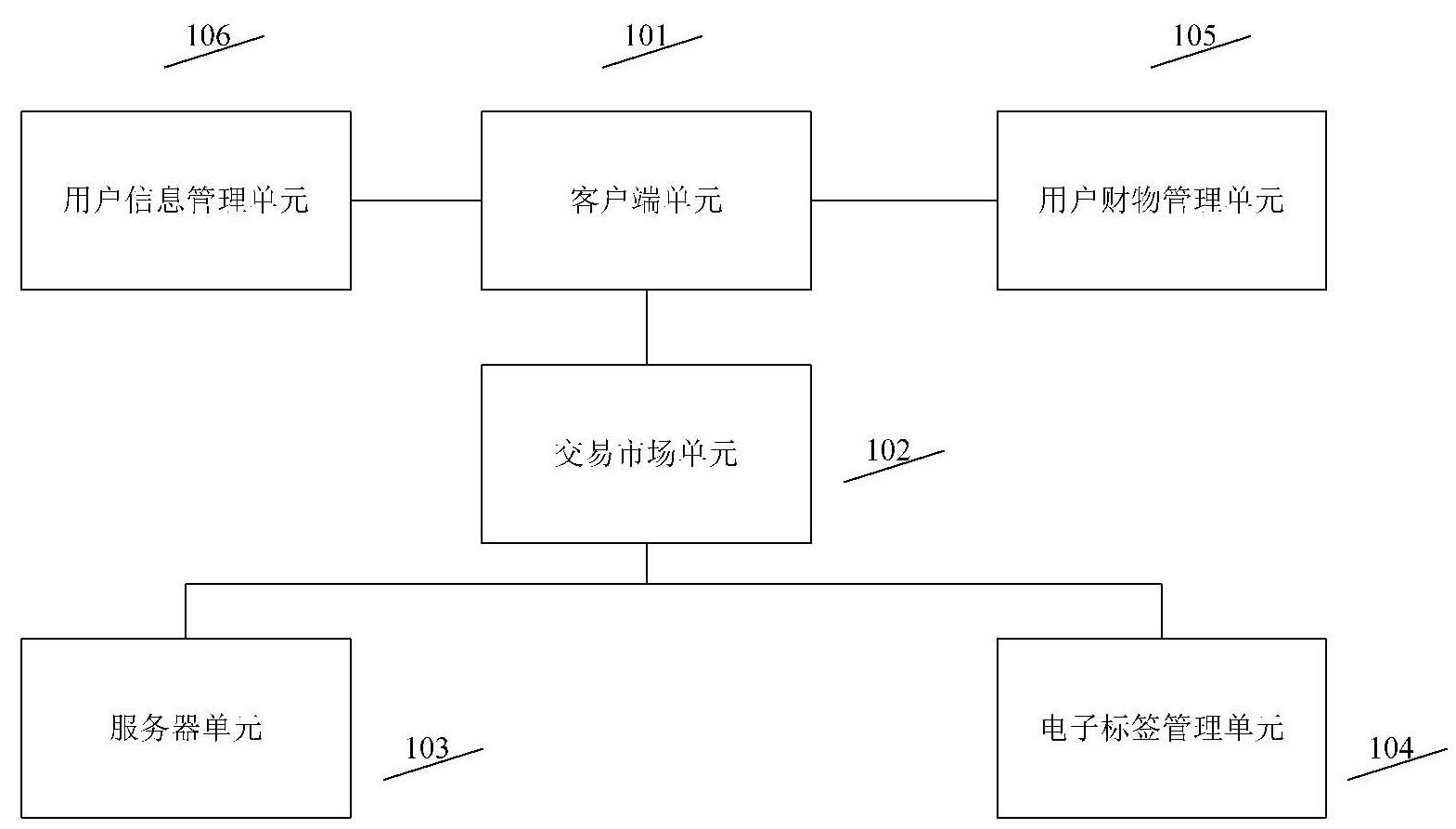
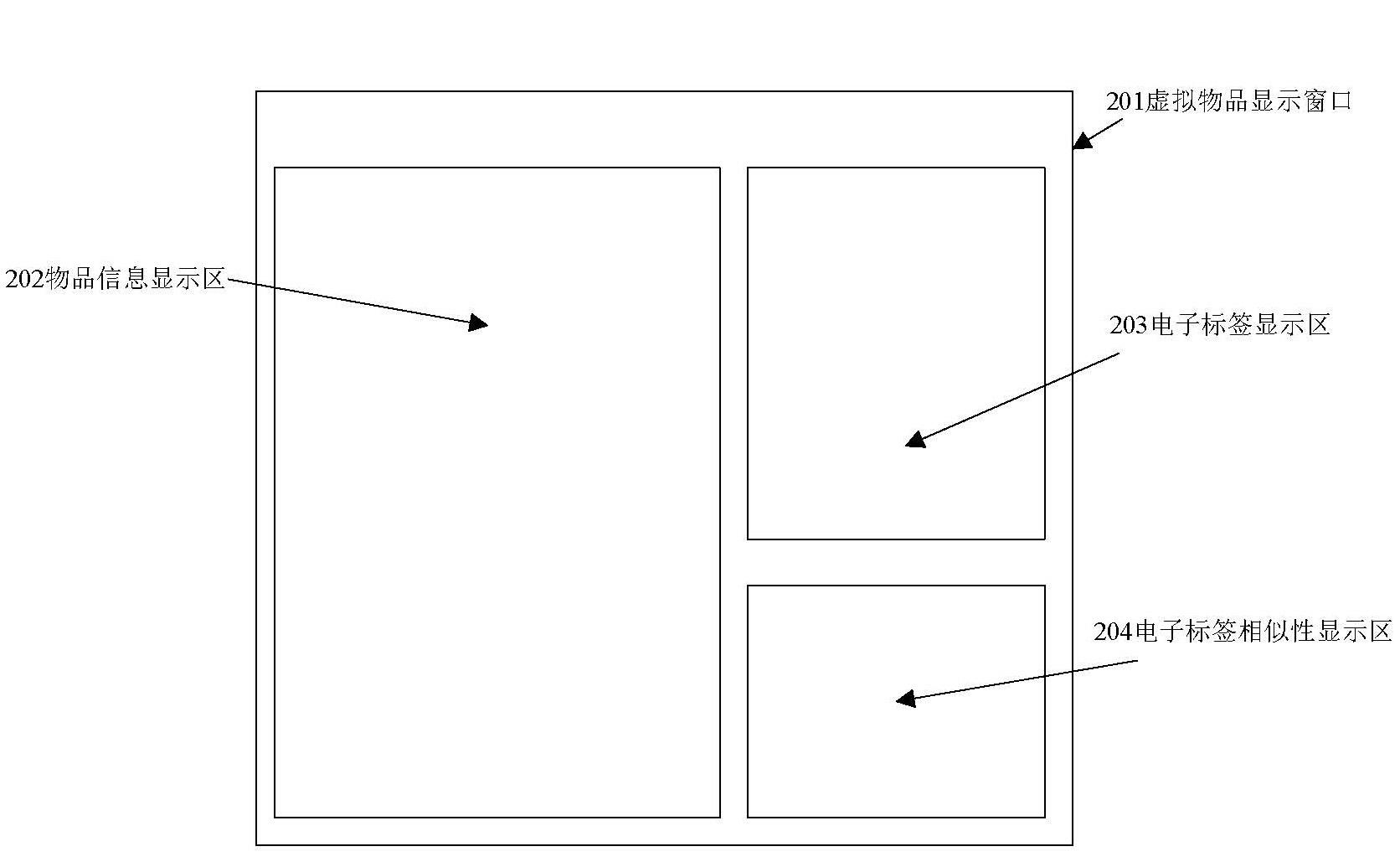
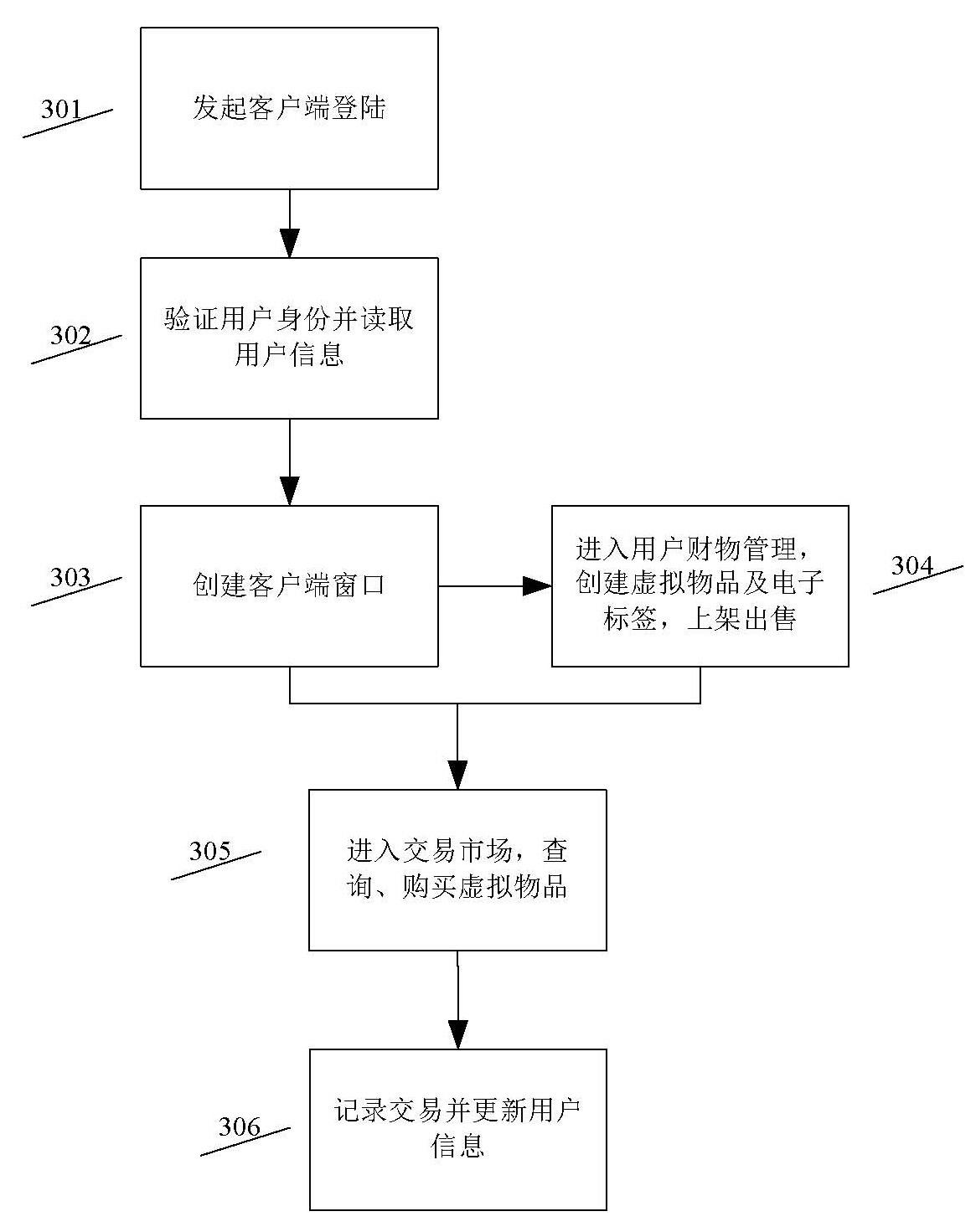
Virtual item trading method and system using electronic tags
The invention discloses a virtual item trading method and system using electronic tags, relates to the field of Internet e-commerce and communication and particularly relates to a virtual item trading method and system using electronic tags. The method and system provided by the invention can be used for overcoming the defects existing in virtual item trading technologies under the existing technical conditions. The virtual item trading system comprises a client unit, a user information management unit, a user property management unit, a trading market unit, an electronic tag management unit and a server unit; and a direct trading way is established for the supply and requisitioning parties of virtual items, so that the individually-accumulated valuable data of Internet users can be circulated, thereby satisfying the needs of other users. According to the invention, the enthusiasm of the Internet users for spreading resources possessed by the Internet users is improved by using a market trading mechanism, therefore, one the one hand, the wealth of networks is accumulated for resource suppliers, and on the other hand, the demands of the users on network resources are satisfied. Under the existing technical conditions, valuable network resources are spread less and mutually copied and duplicated much, especially the contents of virtual items are lack of transparency, and such defects reduce the credibility of resources in the process of network resource circulation. By using the method and system disclosed by the invention, one the one hand, the variety of network resource circulation is expanded, meanwhile, electronic tags are created for all circulated virtual items, a value judgment basis of virtual items is provided for buyers, and the reliability of virtual item trading is increased by using a technical means.
Owner:深圳市财富万方信息技术有限公司
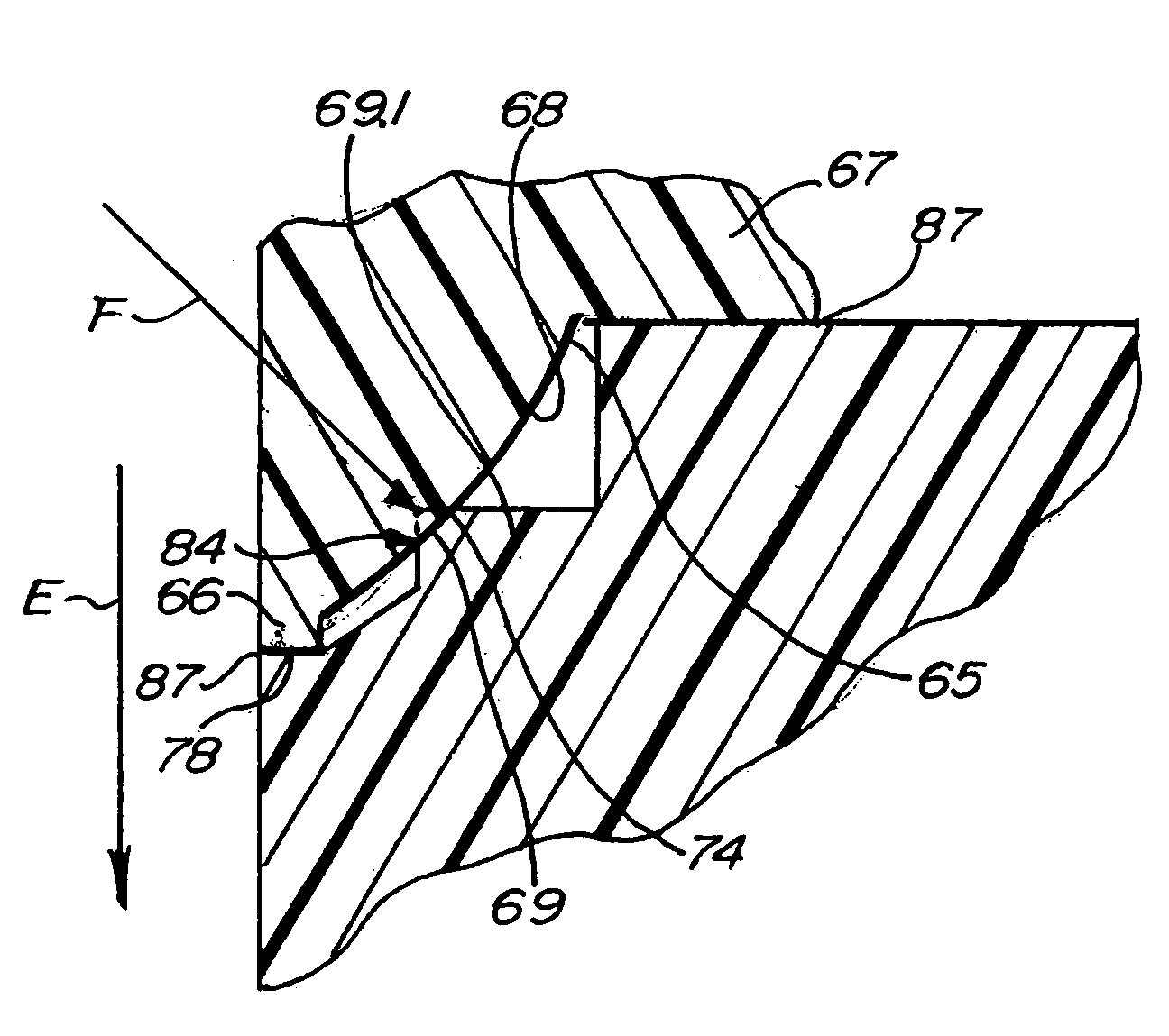
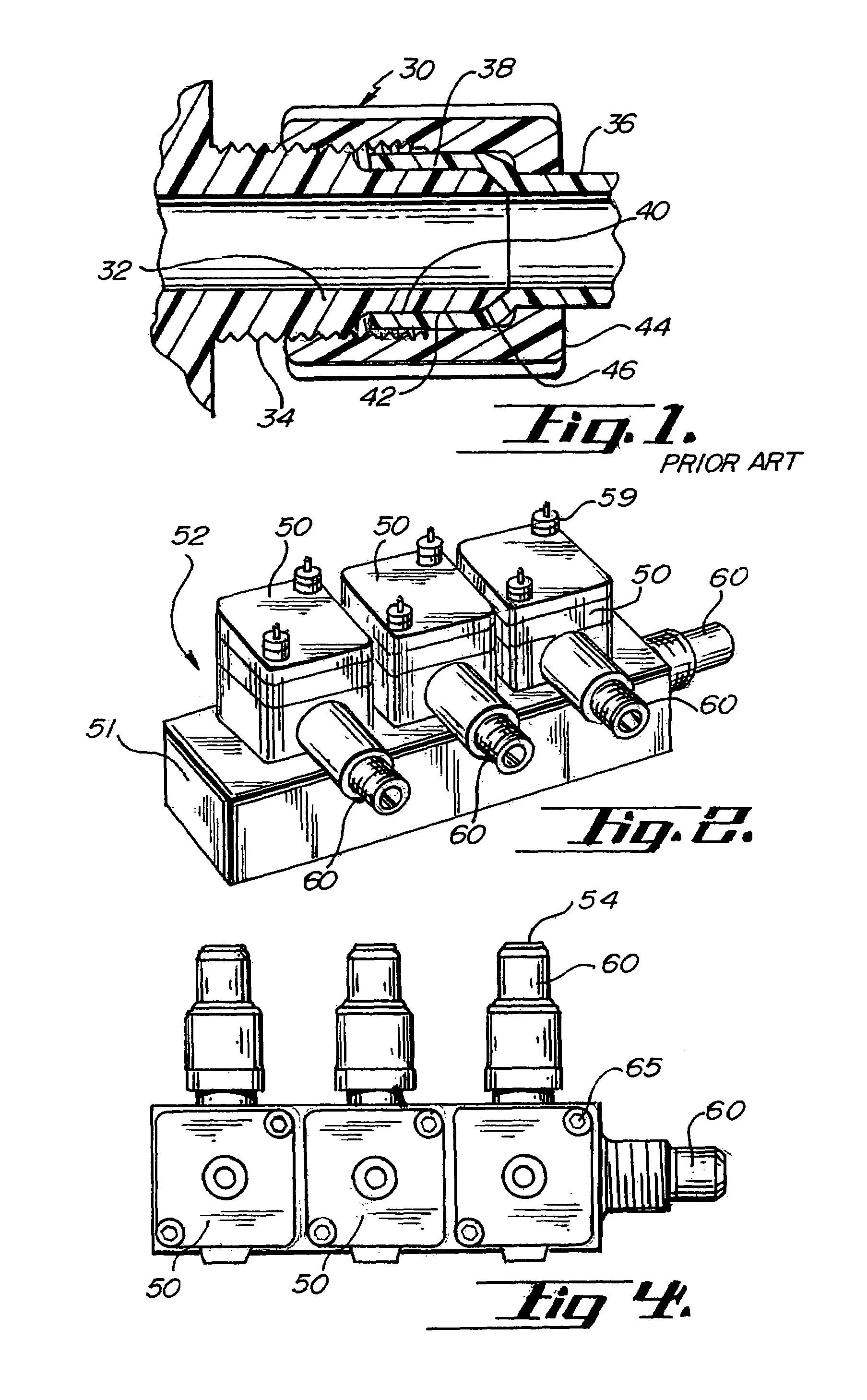
Component to component sealing method
InactiveUS7036204B2Easy to manufactureReduce credibilityJoints with sealing surfacesPipe elementsEngineeringMechanical engineering
A method for sealingly coupling a first component and a second component. The method includes forming a polymer male portion attached to the first component. The male portion has a first axis and a first bore extending therethrough. The male portion has a first stop surface, a second stop surface and an annular sealing portion intermediate the first stop surface and the second stop surface. The method also includes forming a polymer female portion attached to the second component. The female portion has a second axis and a second bore extending therethrough. The female portion has a third stop surface, a fourth stop surface and an annular ring intermediate the third stop surface and the fourth stop surface. The male portion is urged towards the female portion so that at least one of the first stop surface is adjacent the third stop surface or the second stop surface is adjacent the fourth stop surface. The annular ring is subjected to a compressive force in an oblique direction with respect to at least one of the first axis and the second axis by contact with the annular sealing portion.
Owner:ENTEGRIS INC
Apparatus for estimating direction of arrival wave
ActiveUS7372404B2Reduce credibilityEasy to operateMulti-channel direction-finding systems using radio wavesComputation using non-contact making devicesFeature vectorEigenvalues and eigenvectors
Apparatus and method are disclosed for estimating direction of an arrival wave, such as radio or acoustic waves. A correlation matrix of an arrival wave is computed, and matrices for obtaining eigenvalues and eigenvectors are produced. Column norms of the matrix, which is subject to a Householder transformation, are computed. Whether a maximum value of the column norms is the same as or lower than a predetermined threshold is judged. A Householder transformation of the matrix is performed only if the maximum value of the column norms is determined to be greater than or equal to the threshold, and not when the maximum value of the column norms is less than the threshold. The eigenvectors and the eigenvalues of the correlation matrix are obtained by further implementing the Householder transformation. The number of arrival waves is judged from the number of times the Householder transformation is performed.
Owner:DENSO IT LAB +1
Parallel stage separation free flight wind tunnel testing device with mass center located on interface
ActiveCN107782526ASolve the problem of not being able to installUnplug the solutionAerodynamic testingEngineeringModel set
A parallel stage separation free flight wind tunnel testing device with the mass center located on the interface comprises a first model, a second model, a pull pin frame, pins, a first fixing nail, asecond fixing nail, a first spring, a second spring, a first pull pin and a second pull pin. The first pull pin, the second pull pin and the pull pin frame are installed together through the two pins, the first fixing nail and the second fixing nail penetrate through respective springs and are inserted into the first model and the second model, and the pull pins installed just are inserted into the models from the model tails and are just inserted into a round hole formed by a semi-circular groove of the first fixing nail and a round hole formed by a semi-circular groove of the second fixingnail to lock the whole model set. It is ensured that the first model and the second model can be fast and effectively separated without interference, the problem that a parallel stage separation freeflight wind tunnel test with the mass center located on the interface cannot be realized is solved mainly, and the defect that two stages cannot release the freedom degree at the same time due to theprevious model fixing mode is overcome.
Owner:CHINA ACAD OF AEROSPACE AERODYNAMICS
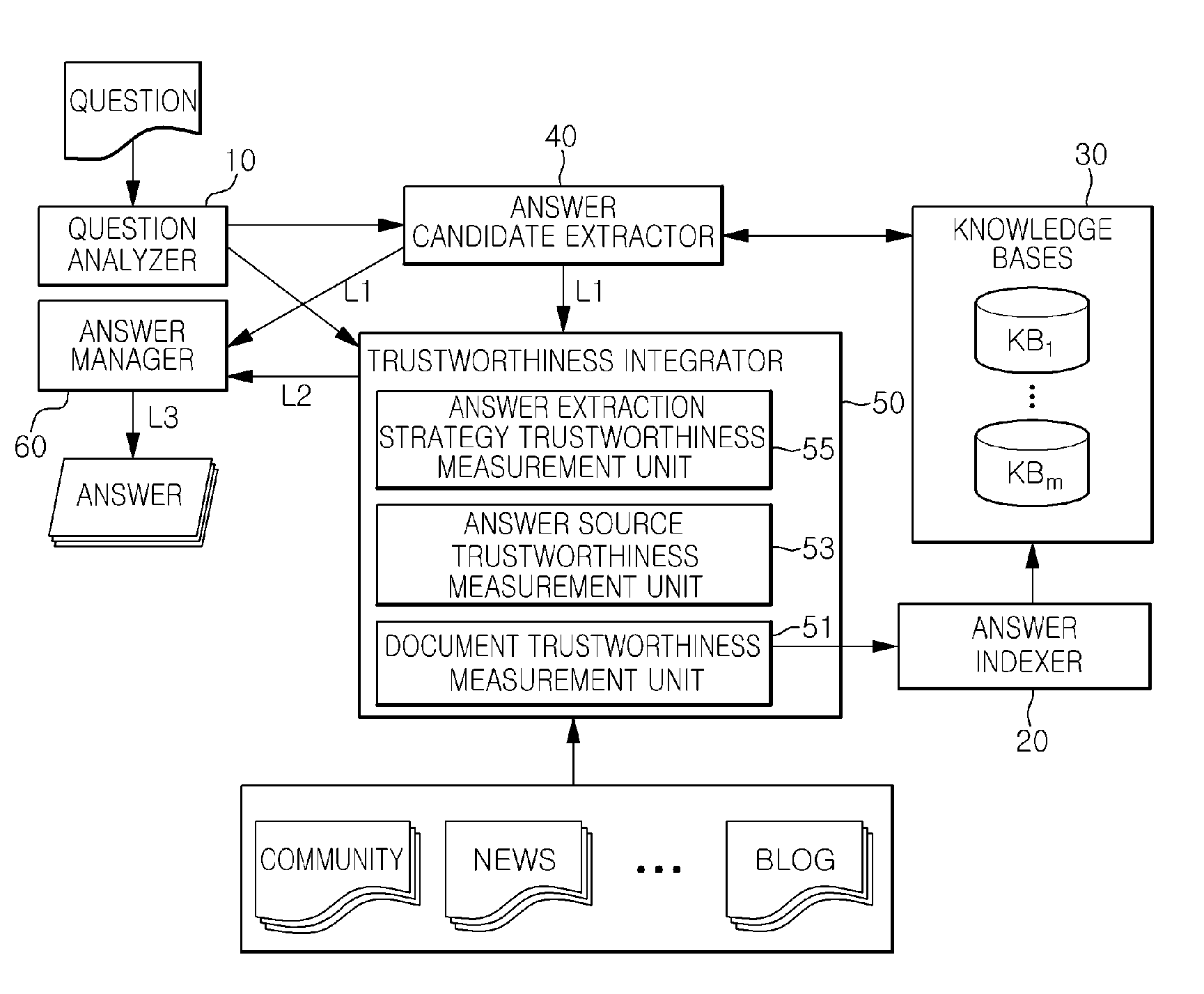
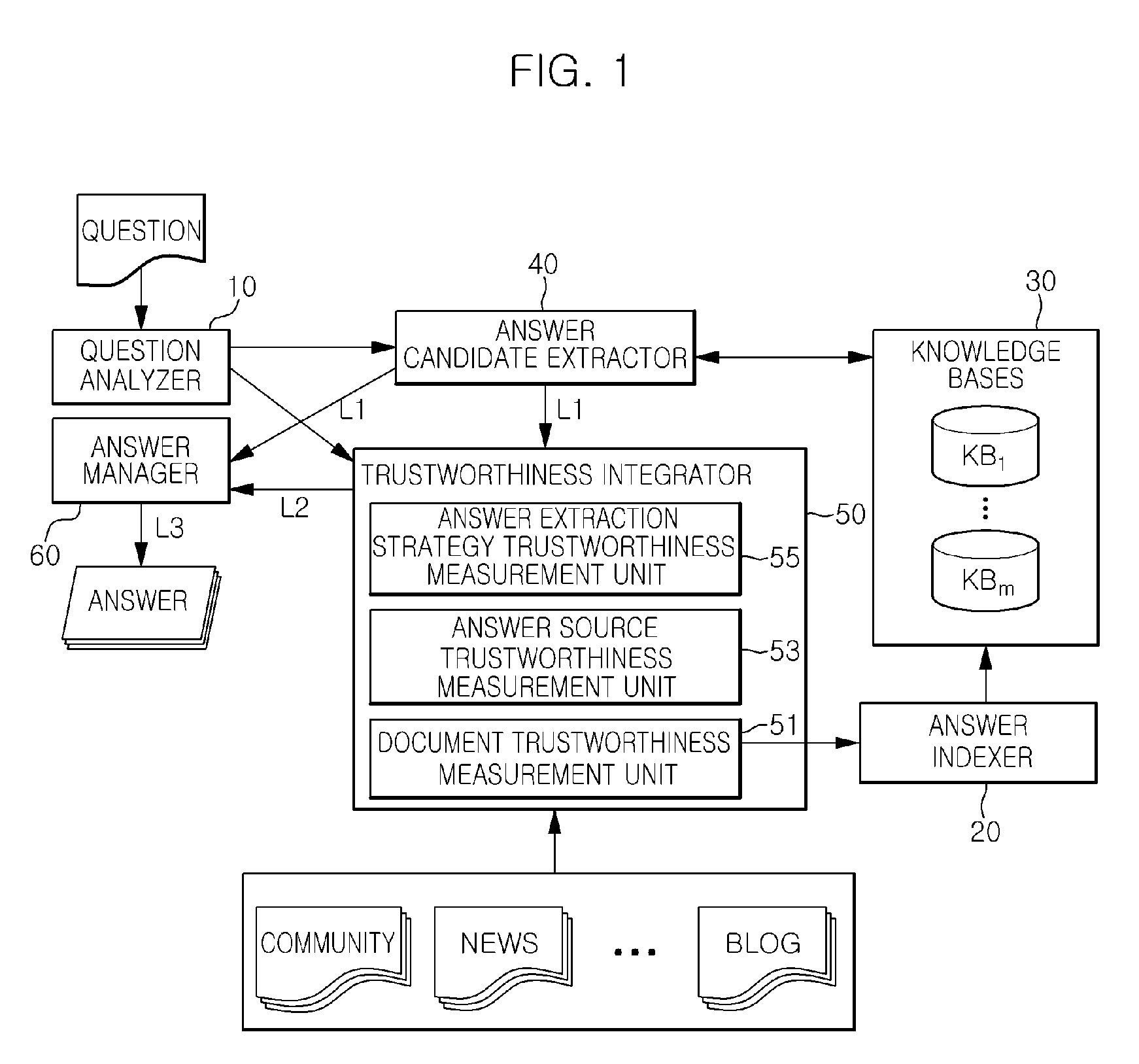
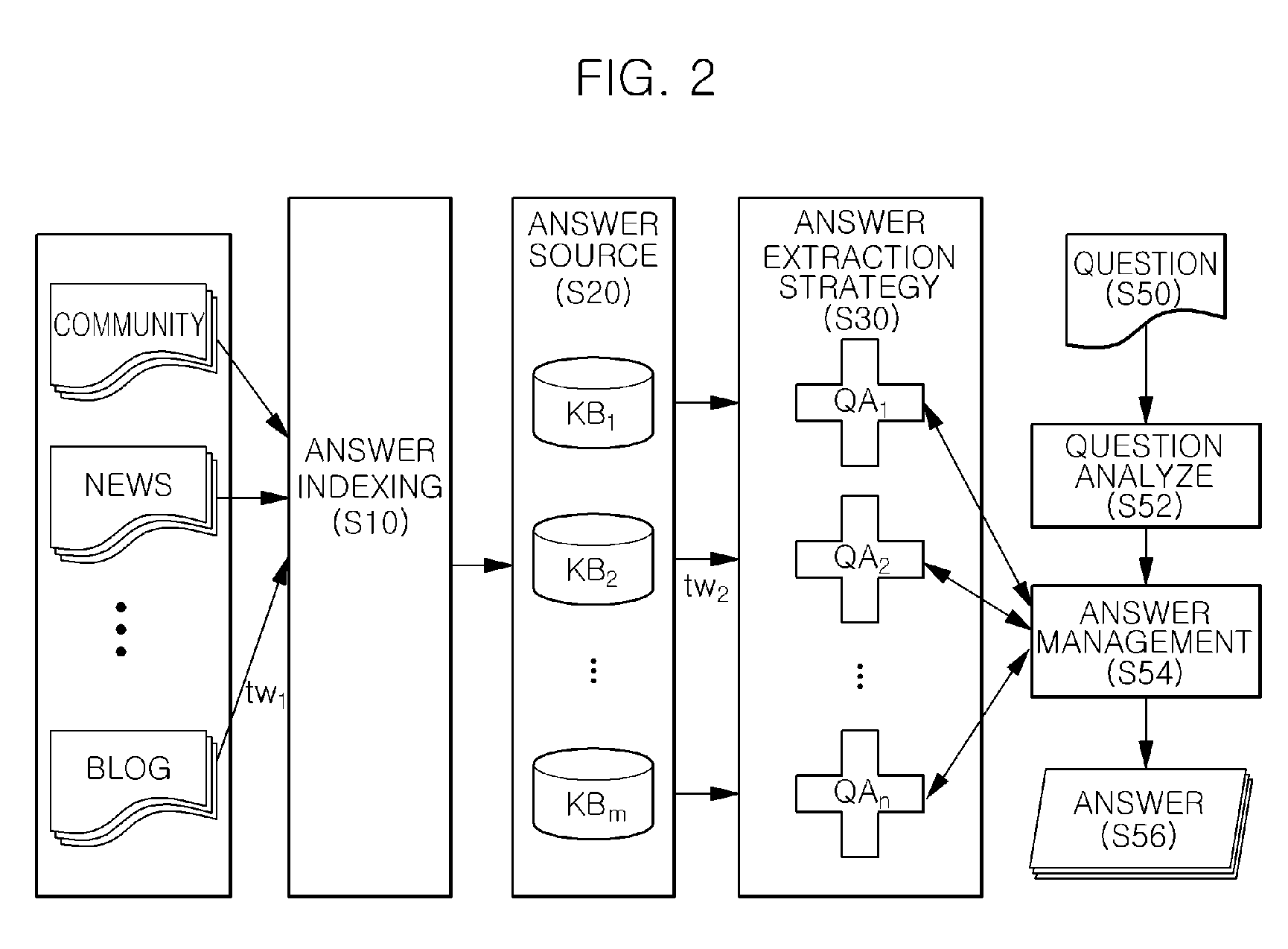
Apparatus for question answering based on answer trustworthiness and method thereof
InactiveUS8380713B2Reduce in quantityReduce credibilityDigital data information retrievalDigital data processing detailsIntegratorDocument preparation
Provides is an apparatus for question answering based on answer trustworthiness including: an answer indexer that indexes documents of which document trustworthiness satisfying a threshold value among documents included in a document collection and stores it in a knowledge Bases; an answer candidate extractor that extracts answer candidate documents for a user's question from the knowledge Bases; an answer source trustworthiness measurement unit; an answer extraction strategy trustworthiness measurement unit; and a trustworthiness integrator that generates an answer candidate trustworthiness list by ranking the answer candidate documents on the basis of the document trustworthiness, the source trustworthiness, and the extraction strategy trustworthiness of the answer candidate documents.
Owner:ELECTRONICS & TELECOMM RES INST
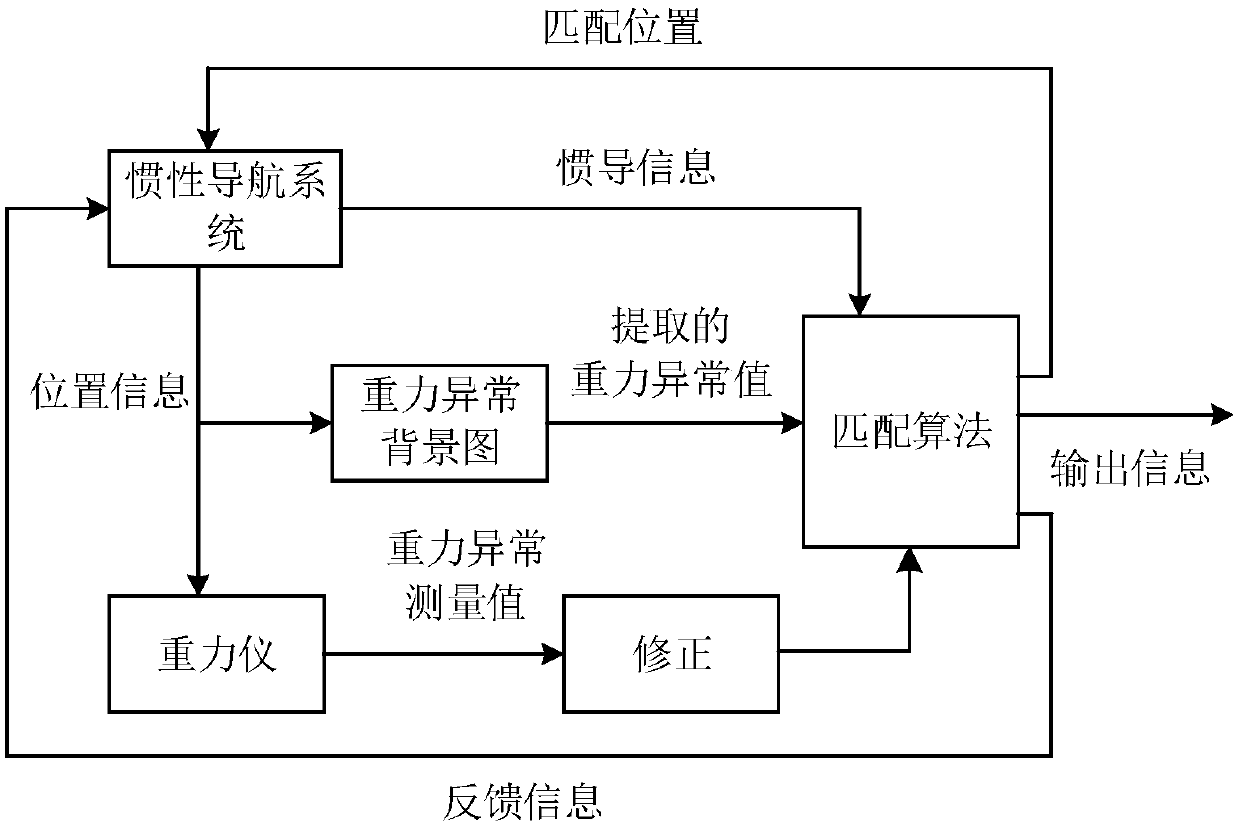
Gravity matching method based on self-adaptive robust untracked Kalman filtering
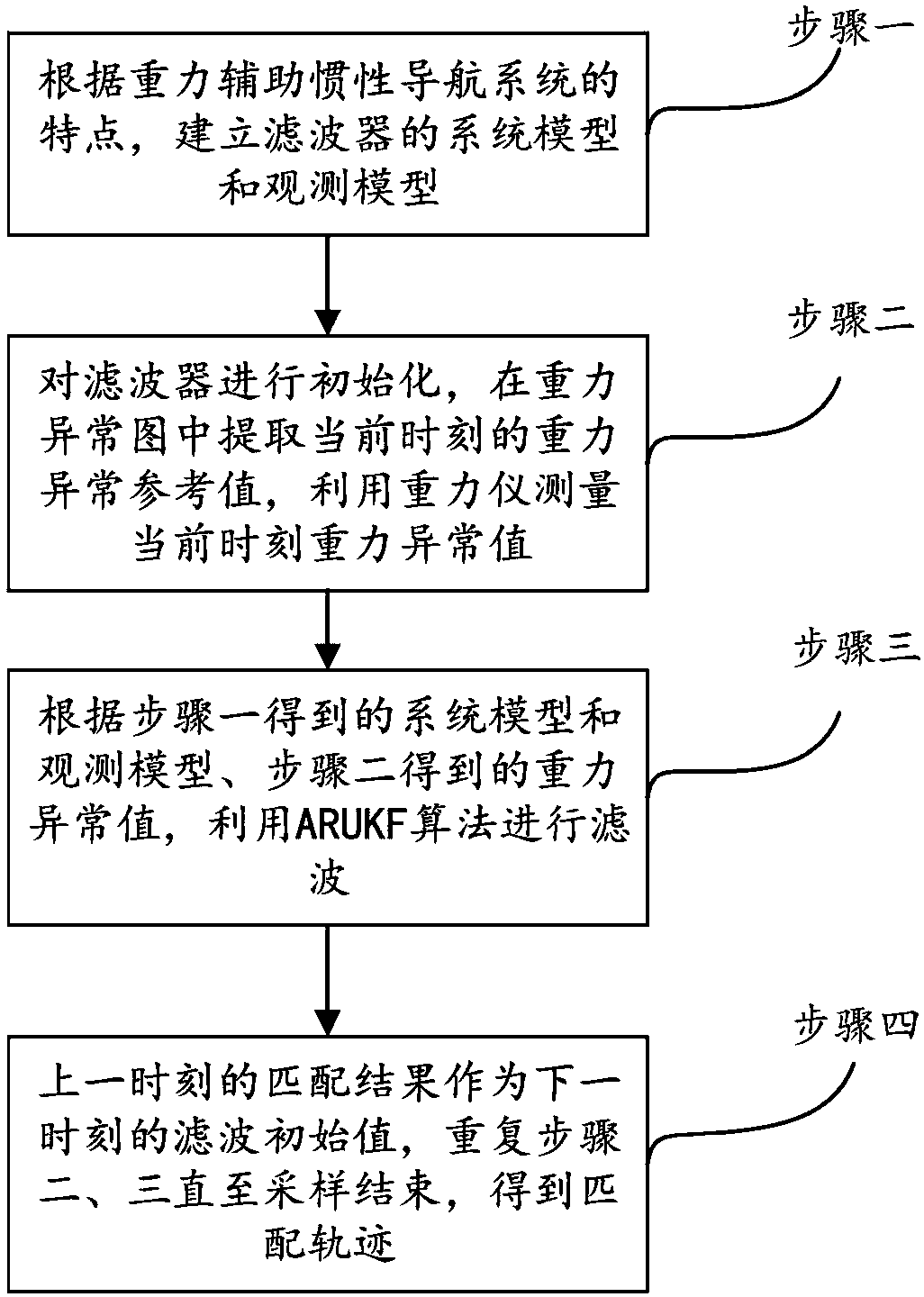
InactiveCN108444479AImprove real-time performanceReduce credibilityNavigational calculation instrumentsNavigation by speed/acceleration measurementsGravity anomalyNavigation system
The invention discloses a gravity matching method based on robust self-adaptive untracked Kalman filtering. The method comprises the following process of building a system state equation and observation equation of a gravity assistance inertial navigation system filter on the basis of a single-point matching algorithm of the recurrence filtering; performing subtraction on the gravity abnormal reference value extracted from the current moment gravity abnormal pattern and the gravity abnormal practical measuring value to obtain the gravity abnormal difference value; on the basis of the improvedARUKF algorithm, performing filtering on the gravity abnormal difference by using the system state equation and the observation equation of the gravity assistance inertial navigation system filter soas to obtain the position and the variance of a submersible vehicle at the next moment; calculating the submersible vehicle position at each filtering sampling moment in the mode by using the positionand the variance of the submersible vehicle at the next moment; finally obtaining a complete matching track. The matching error can be effectively reduced; the navigation positioning precision of thegravity assistance inertial navigation system is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Metallogenic prediction method and system based on fuzzy logic and machine learning
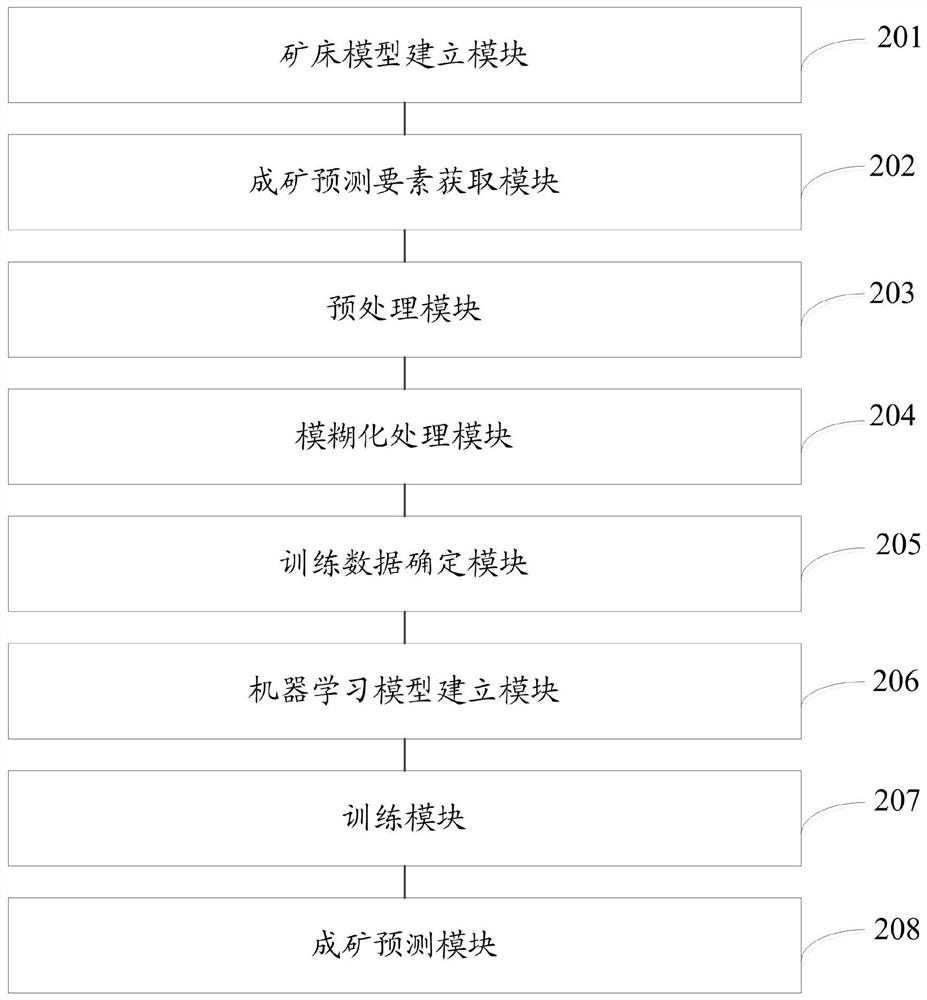
ActiveCN111859811AImprove accuracyFully excavatedDesign optimisation/simulationFuzzy logic based systemsMetallogenyEngineering
The invention relates to a metallogenic prediction method based on fuzzy logic and machine learning. The method comprises the following steps: establishing an ore deposit model, wherein the ore deposit model comprises mineralization geological elements, a mineralization process and a mineralization effect; obtaining mineralization prediction elements related to mineralization based on the ore deposit model; preprocessing the mineralization prediction elements; fuzzy processing is carried out on the preprocessed metallogenic prediction elements; determining training data based on the mineralization prediction elements after fuzzy processing; establishing a machine learning model; training the machine learning model based on the training data to obtain a trained machine learning model; and performing metallogenic prediction based on the trained machine learning model. According to the method provided by the invention, the prediction accuracy can be improved.
Owner:INST OF MINERAL RESOURCES CHINESE ACAD OF GEOLOGICAL SCI
Leveraging Transaction data for Entity Verification and Credibility
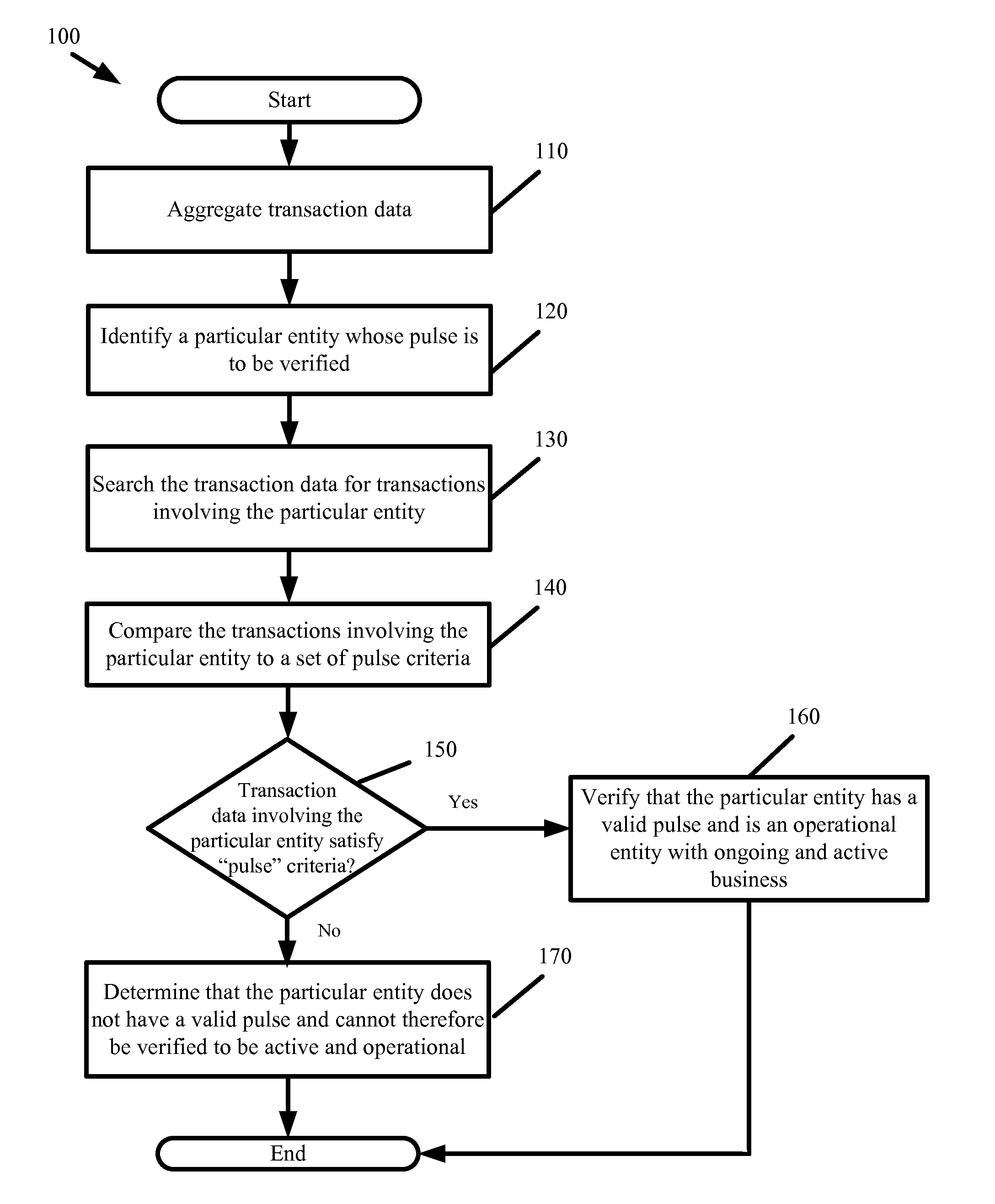
InactiveUS20150154717A1Improve credibilityShorten the timeComplete banking machinesFinanceTime frameData science
Some embodiments provide an accurate and real-time account of an entity's verification status and credibility from transaction data. Some embodiments verify the entity's operational status by aggregating transaction data involving the entity and by determining if the transaction data satisfies some threshold number of transactions within a given time frame. If the threshold is satisfied, the entity is verified to be active and operational and have a “pulse”. The pulse can be used to scrub directories or marketing lists. Some embodiments derive the entity's credibility by monitoring for increases or decreases in the transaction data, wherein increases or decreases can be identified from changes in the transaction volume, changes in average transaction price, and / or changes in price of a good or service from one monitored interval to another. Some embodiments derive entity credibility by comparing those changes to changes in one or more competitors' transaction data.
Owner:DUN & BRADSTREET EMERGING BUSINESSES
Heterojunction bipolar transistor and manufacturing method thereof
The object of the present invention is to provide a heterojunction bipolar transistor with high breakdown tolerance which can be manufactured at a high reproducibility and a high yield, the heterojunction bipolar transistor includes: a sub-collector layer; a collector layer formed on the sub-collector layer; a base layer formed on the collector layer; and an emitter layer, which is formed on the base layer and is made of a semiconductor that has a larger bandgap than a semiconductor of the base layer, in which the collector layer includes: a first collector layer formed on the sub-collector layer; a second collector layer formed on the first collector layer; and a third collector layer formed between the second collector layer and the base layer, a semiconductor of the first collector layer differs from semiconductors of the third collector layer and the second collector layer, and an impurity concentration of the second collector layer is lower than an impurity concentration of the sub-collector layer and higher than an impurity concentration of the third collector layer.
Owner:PANASONIC SEMICON SOLUTIONS CO LTD
Designing method for detecting sensor network abnormal data based on space-time correlation
InactiveCN107205244AMaintain network securityMaintain securityNetwork topologiesSecurity arrangementSpacetimeLine sensor
The present invention relates to the field of information communication, and discloses a design method for sensor network abnormal data detection based on spatio-temporal correlation, which includes space dimension detection and time dimension detection, and can realize the detection and classification of abnormal data in wireless sensor networks. and classification results, can respond to events in the network in a timely manner, and at the same time, for malicious nodes that affect the observation results of the base station by sending malicious data, thereby reducing the reliability of the network, by reducing their reputation in the network, the data will not Forwarding from malicious nodes, if the reputation of the node is low to a certain extent, the node will be blacklisted and its data will no longer be received, so as to achieve the purpose of shielding such malicious nodes and maintaining network security.
Owner:HARBIN INST OF TECH AT WEIHAI
Block chain consensus mechanism based on credibility model
ActiveCN113313378AReduce the probability of doing evilCircumstances against briberyFinanceResourcesBlockchainWeighted average method
The invention discloses a block chain consensus mechanism based on a credibility model, and the mechanism comprises the steps: employing a weighted average method to calculate the credibility of nodes, taking the credibility of other nodes voted by a certain node as a weight, calculating the final vote number for each node participating in voting, carrying out the sorting of the final scores of all nodes from high to low, taking the scores in front of preset values as candidates for packaging nodes, after the voting process and the packaging process are successfully finished, rewarding the nodes participating in packaging and successful in packaging and the nodes voting for the nodes, punishing the nodes failed in packaging, the nodes disable in packaging and the nodes voting for the nodes, and combining the rewarding and punishing of the node credibility to update the credibility value. According to the invention, during election, voting is carried out by taking the credibility value as a weight, and the packaging nodes are randomly selected, so that the condition of direct selection is prevented; and a reward and punishment mechanism is introduced, so that the probability of malicious node discovering can be effectively reduced.
Owner:BEIHANG UNIV
Crystal micro-texture orientation obtaining device and obtaining method
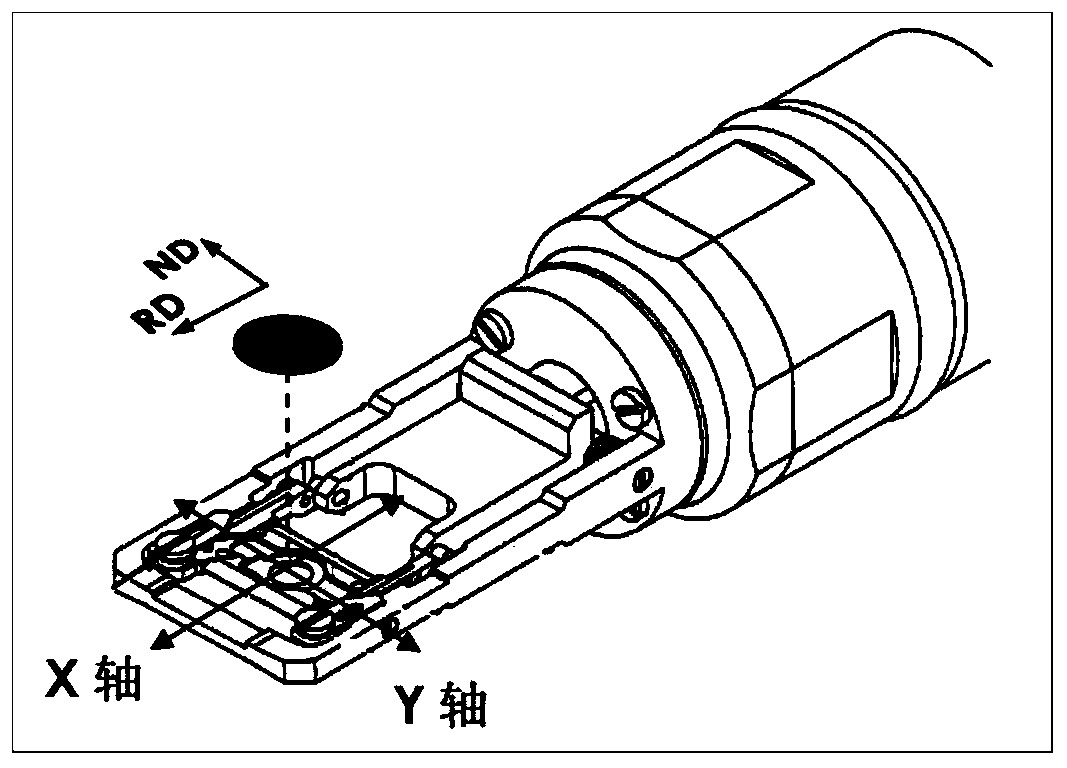
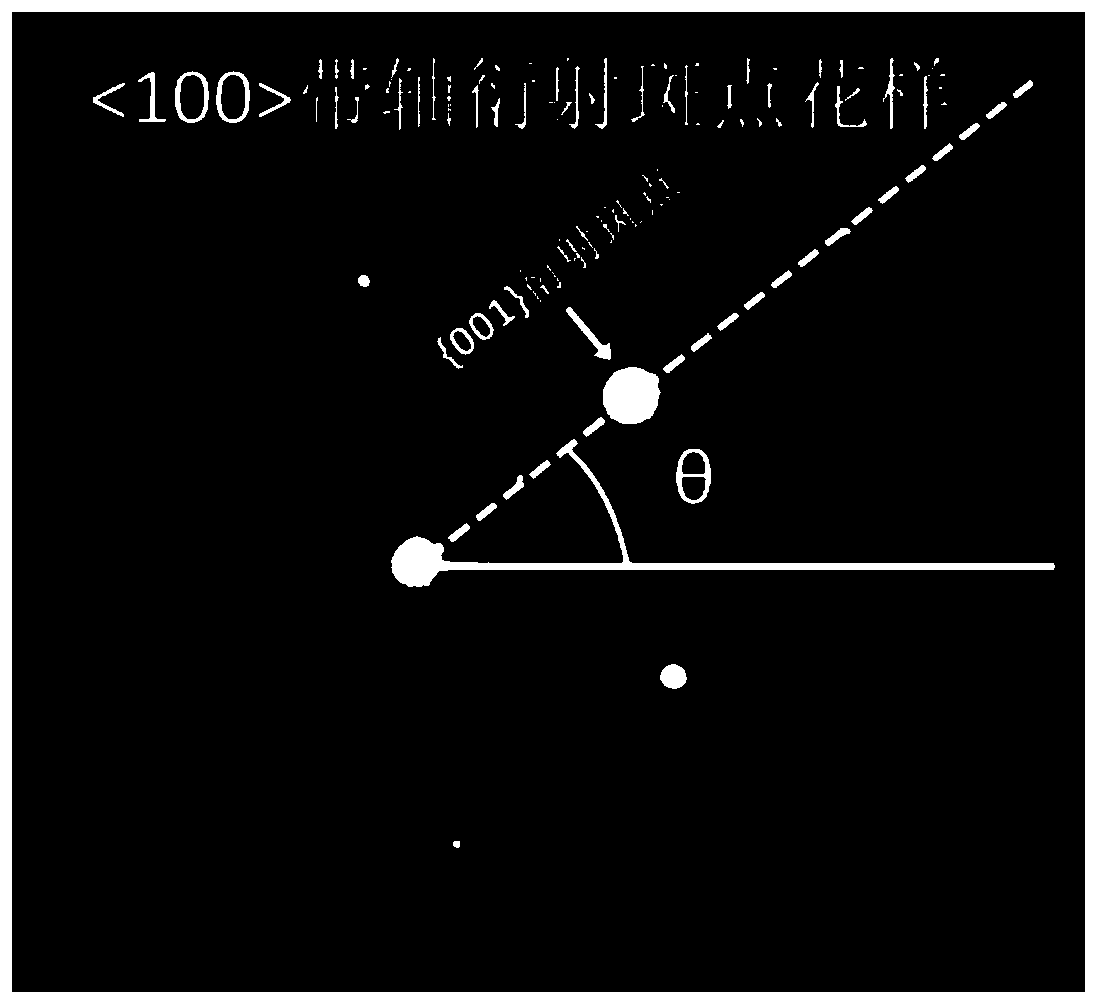
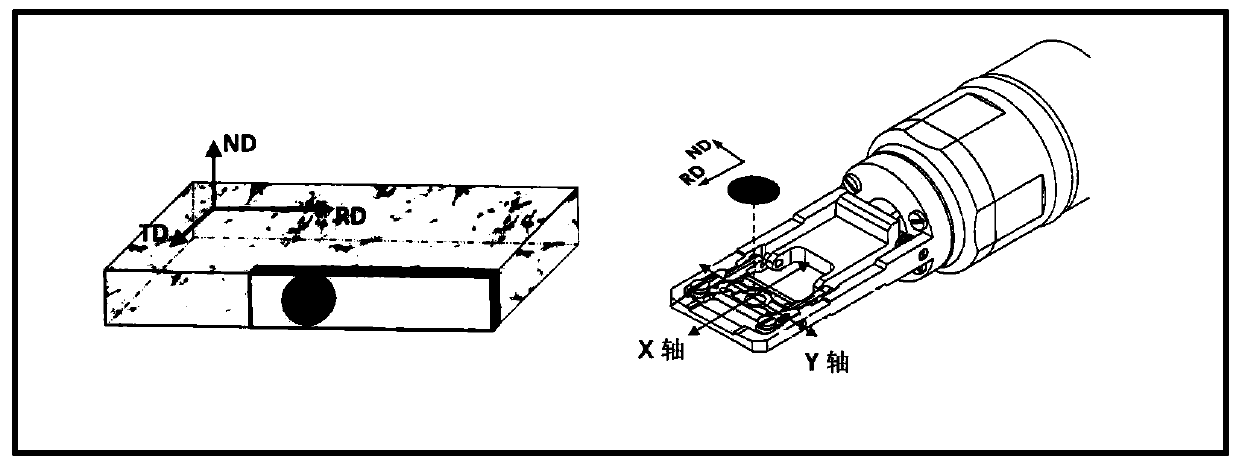
ActiveCN110361404AOvercoming the problem of low calibration rateOvercoming the problem of difficult determination of orientationMaterial analysis using wave/particle radiationScanning electron microscopeMicro texture
The invention provides a crystal micro-texture orientation obtaining device and obtaining method based on a transmission electron microscope (TEM), and aims at the technical shortcomings that the traditional micro-texture test technique (SEM-EBSD) is unable to measure the micro-texture of a large plastic deformation sample or a nanocrystal-scale sample. The obtaining device is composed of sample cutting equipment, sample clamping equipment, image acquisition equipment, angle acquisition equipment and a computer. The obtaining method can finally calculate the micro-texture Euler angle (phi1, phi, phi2) of the measured region. The beneficial technical effects are that the invention the micro-texture of the measured region can be obtained and the problems of limited spatial resolution of thetraditional scanning electron microscope backscattering diffraction technique and low calibration rate of the large strain amount sample of any large plastic deformation sample and nano-scale sample can be overcome.
Owner:HEFEI UNIV OF TECH
Automated, reactive flight-delay risk-transfer system and method thereof
ActiveUS20190005585A1Stable structureSmooth transferAutonomous decision making processFinanceResource poolPayment
There is provided an automated, reactive flight delay risk-transfer system and method related to airspace risks for risk sharing of a variable number of risk-exposed units by pooling resources of the units and by providing a self-sufficient risk-transfer system based on the pooled resources by a resource-pooling system associated with the risk-transfer system, where an automated transfer of risk exposure associated with the units is provided by an automated flight delay insurance system including a capturing means to receive transmitted air data parameters of aircraft ground-based flight controllers. A trigger module dynamically triggers filtered flight time parameters via a data flow pathway of the controllers by means of a predefined time-delay threshold value, where in case of triggering of an excess of the value, operational parameters of the triggered flight including delay parameters and identification are captured and losses associated with the delay are covered by a parametric payment transfer.
Owner:SWISS REINSURANCE CO LTD
Perimeter
A perimeter has fixation state judging means for individually judging a fixation state of an examinee in connection with each presented stimulus, and the fixation state judging means individually judges the fixation state whenever the stimulus is presented. Even if defective fixation is judged, retest is conducted on only a point where the stimulus was presented, which was judged to be defective fixation. Then, examiner's burden and examinee's burden can be lightened, the test time can be made shorter and test efficiency can be improved in comparison with a case where the whole test is retried from the first as a conventional way.
Owner:KOWA CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com