A packet encryption and decryption method and device
A technology of encryption, decryption and configuration methods, which is applied in the field of information security and can solve problems such as poor security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
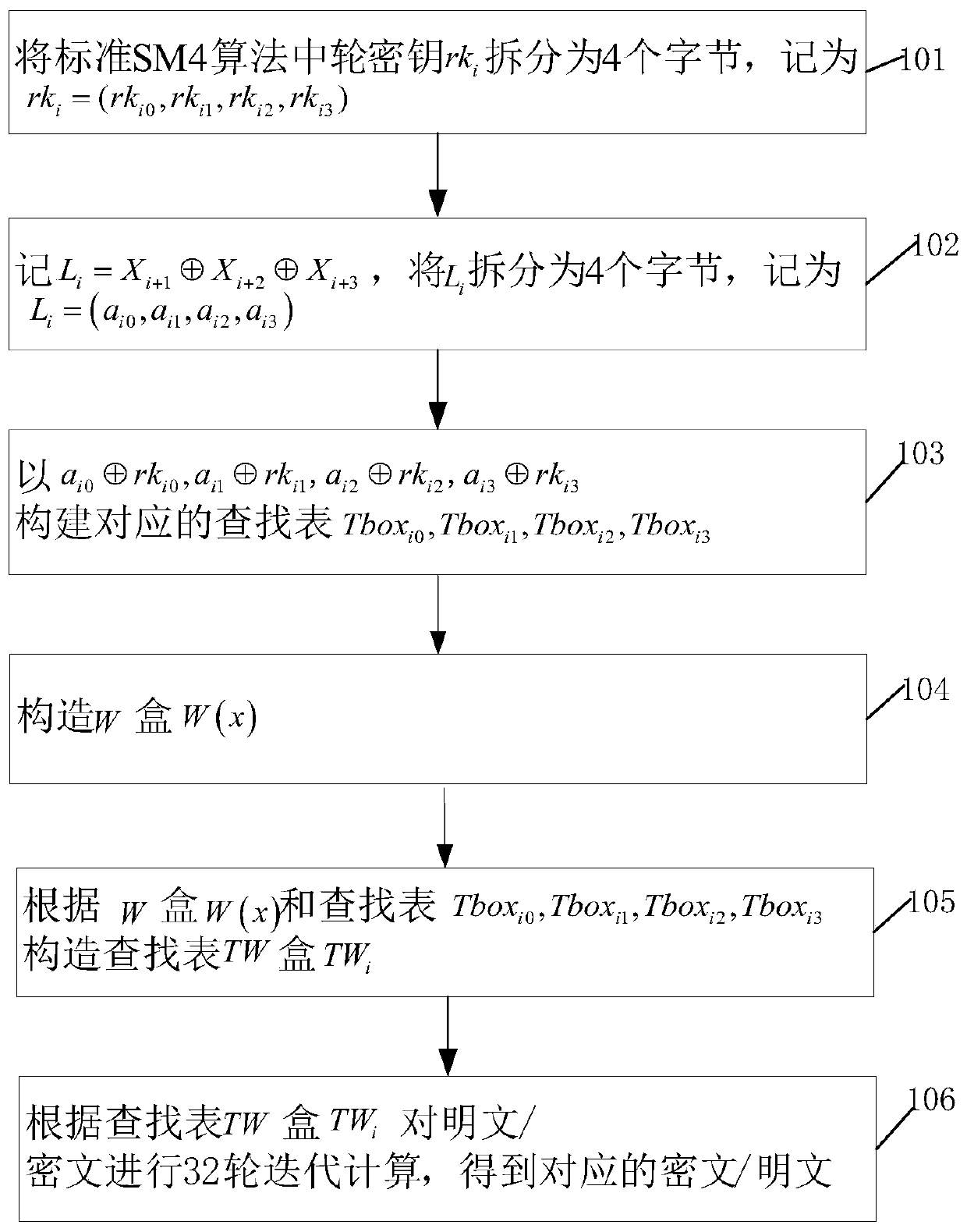
[0057] Such as figure 1 As shown, the embodiment of the present invention provides a packet encryption and decryption method, including:
[0058] Step 101, the round key rk in the standard SM4 algorithm i Split into 4 bytes, recorded as rk i =(rk i0 ,rk i1 ,rk i2 ,rk i3 ).
[0059] In this embodiment, the standard SM4 algorithm has a total of 32 round keys, that is, in step 101, i represents the number of iterative calculation rounds, i is an integer, and i satisfies 0≤i≤31.
[0060] Step 102, remember Will L i Split into 4 bytes, denoted as L i =(a i0 ,a i1 ,a i2 ,a i3 ).
[0061] In this embodiment, in step 102 Exclusive OR; X i+1 is the i+1 round ciphertext; X i+2 is the i+2 round ciphertext; X i+3 is the i+3 round ciphertext.
[0062] Step 103, with Build the corresponding lookup table Tbox i0 ,Tbox i1 ,Tbox i2 ,Tbox i3 .
[0063] In this embodiment, Tbox in step 103 ij for Corresponding lookup table; j is an integer, and j satisfies 0≤j≤3. ...
Embodiment 2
[0077] Such as image 3 As shown, the embodiment of the present invention provides a packet encryption and decryption method, including:
[0078] Step 301 to step 305, build lookup table Tbox i0 ,Tbox i1 ,Tbox i2 ,Tbox i3 and W box W(x), and according to W box W(x) and lookup table Tbox i0 ,Tbox i1 ,Tbox i2 ,Tbox i3 Construct lookup table TW box TW i . The process is related to figure 1 Steps 101 to 105 shown are similar and will not be repeated here.
[0079] Step 306, each round of operation randomly generates four 8-bit random numbers Z i0 ,Z i1 ,Z i2 ,Z i3 .
[0080] In this embodiment, in order to improve the security of encryption and decryption operations, in 32 rounds of iterative operations, each round randomly generates a set of random numbers Z through step 306 i0 ,Z i1 ,Z i2 ,Z i3 . Preferably, in order to ensure that all Z in 32 rounds of iterative operations ij (0≤j≤3) are different, can generate 32*4 byte random numbers at one time, take 4 b...
Embodiment 3
[0092] Such as Figure 5 As shown, the embodiment of the present invention provides a packet encryption method, including:
[0093] Step 501, remember Will M t Split into 4 bytes, denoted as M t =(b t0 ,b t1 ,b t2 ,b t3 ).
[0094] In this embodiment, t in step 501 is an integer, and t satisfies 0≤t≤31, Y 0 ,Y 1 ,Y 2 ,Y 3 4 32bit words split for plaintext; Y t+1 is the t+1th round ciphertext; Y t+2 is the t+2 round ciphertext; Y t+3 It is the ciphertext of the t+3th round.
[0095] Step 502, respectively with b t0 ,b t1 ,b t2 ,b t3 To TW cassette TW i Perform table lookup operation to get B t0 ,B t1 ,B t2 ,B t3 .
[0096] In this embodiment, in step 502, TW box TW i is generated, with figure 1 Steps 101 to 105 shown are similar and will not be repeated here.
[0097] Step 503, according to C and D, set B t0 ,B t1 ,B t2 ,B t3 Convert to U t .
[0098] In this embodiment, the acquisition process of C and D is the same as figure 2 The steps 107...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com