Cache penetration method and a terminal
A cache and terminal technology, applied in special data processing applications, instruments, electrical and digital data processing, etc., can solve problems such as failure, poor user experience, waste of resources, etc., to avoid meaningless operations, improve user experience, and increase resources. The effect of utilization and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
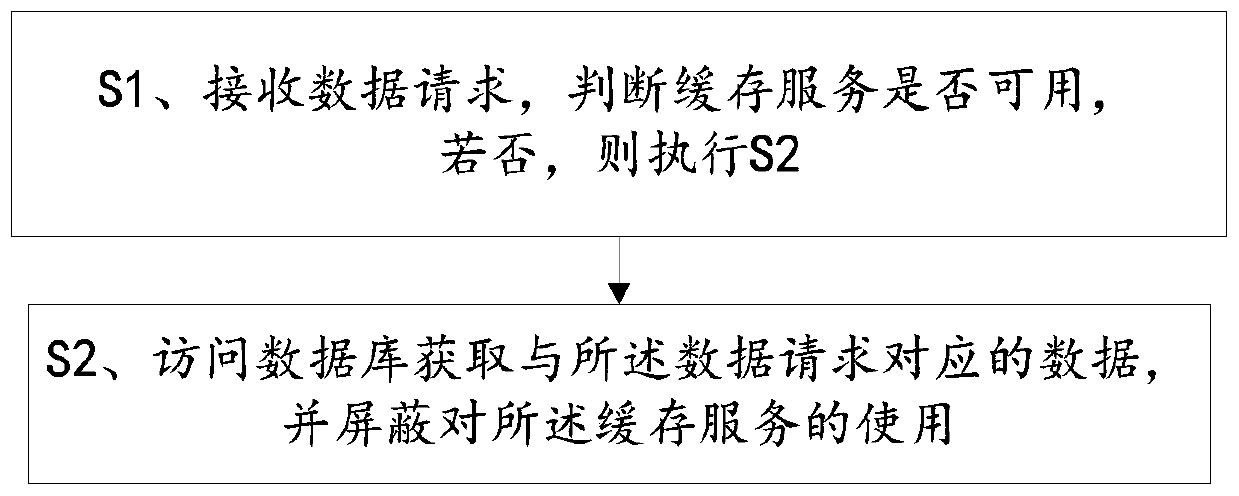
[0057] A cache penetration method, including steps:
[0058] S1. Receive the data request, judge whether the cache service is available, if not, execute S2;
[0059] Among them, the cache server is dynamically monitored through an independent asynchronous thread, and an indication of whether the cache service is available is set according to the monitoring result;
[0060] Specifically, regularly query the cache server, access the data of the preset field on the cache server, and judge whether the cache server can normally return the data of the preset field, if so, then access the cache server successfully, and the preset The number of failures is set to 0, and the identifier of the cache service is set to be available;
[0061] If not, when waiting for timeout or abnormality of the cache server, etc. cannot return the preset field data normally, the access to the cache server fails, and the preset number of failures is increased by 1, and the continuous query cache is judge...
Embodiment 2
[0072] Apply the method described in Embodiment 1 to the scenario of user login:
[0073] The server saves the token required for user login in the cache service and database;
[0074] S1. Receive the token request, judge whether the cache service is available, if not, execute S2;
[0075] When verifying the token, first query whether there is a corresponding token in the cache service, and if not, access the database;
[0076] Among them, the cache server is dynamically monitored through an independent asynchronous thread, and an indication of whether the cache service is available is set according to the monitoring result;
[0077] Specifically, regularly query the cache server, access the data of the preset field key on the cache server, and judge whether the cache server can normally return the data of the preset field key, if so, then access the cache server successfully, and send The preset number of failures is set to 0, and the identifier of the cache service is set ...
Embodiment 3
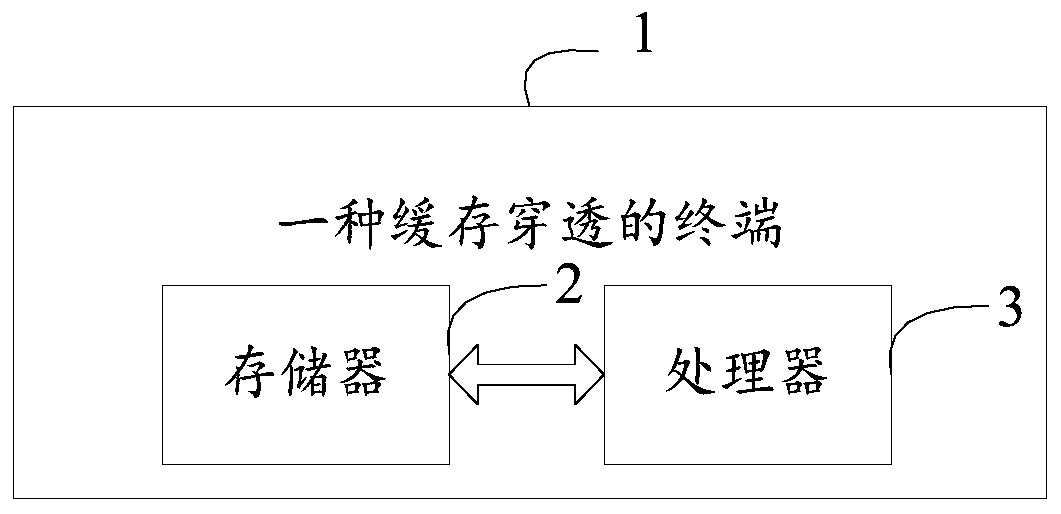
[0086] Please refer to figure 2 , a cache penetration terminal 1, comprising a memory 2, a processor 3, and a computer program stored in the memory 2 and operable on the processor 3, the processor 3 implements the computer program when executing the computer program Steps in Example 1.
[0087] To sum up, the cache penetration method and terminal provided by the present invention dynamically monitor the cache server, and set whether the cache service is available or not according to the monitoring results. The identifier of whether the cache service is available determines whether the cache service is available. If not, access the database to obtain the data corresponding to the data request, and block the use of the cache service. That is, if the cache service is found to be unavailable, the database After the corresponding data is obtained, the obtained data will not be loaded into the cache service again; dynamic monitoring is realized by periodically querying the cache s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com