Memory leakage risk detection method, terminal and computer readable storage medium
A memory leak and risk detection technology, applied in the field of smart terminals, can solve problems such as memory leaks that cannot be completely avoided
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
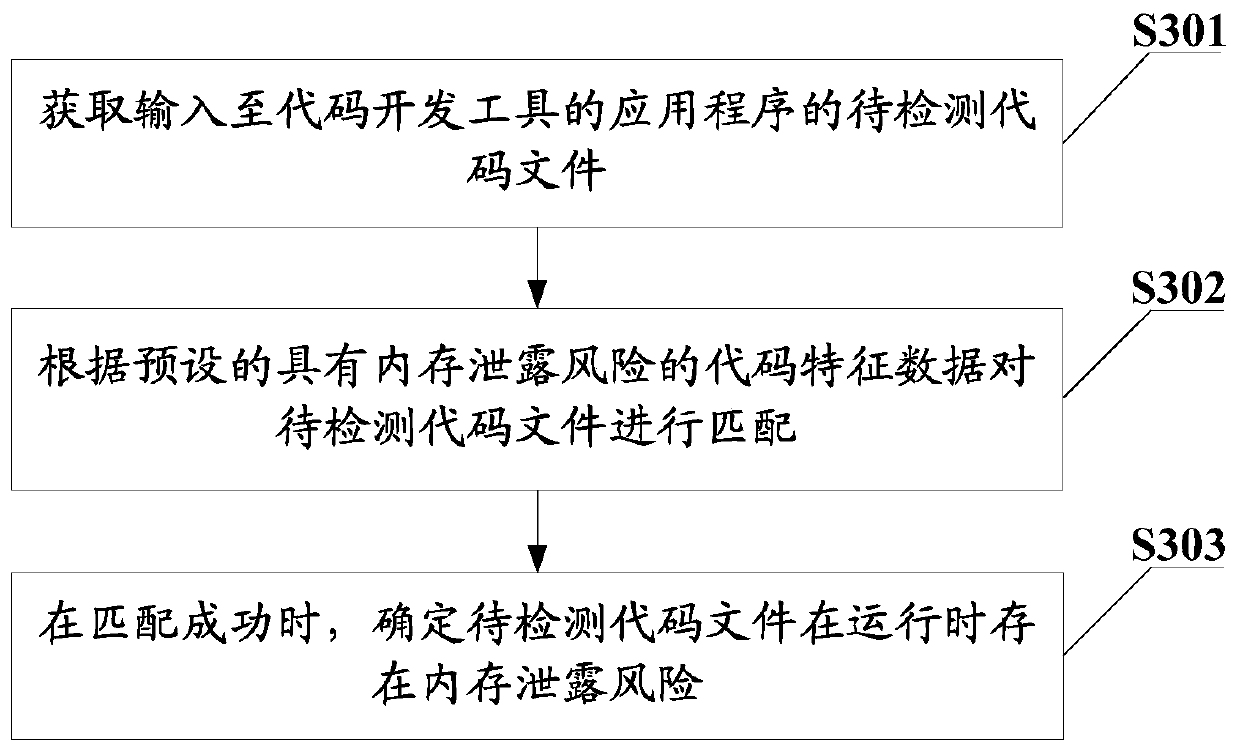
[0069] In order to solve the defect in the prior art that hidden dangers can only be checked when a memory leak error occurs in the code running phase, and the memory leak problem cannot be completely avoided during online operation, this embodiment provides a memory leak risk detection method. Such as image 3 Shown is the basic flow chart of the memory leak risk detection method provided in this embodiment. The memory leak risk detection method specifically includes the following steps:
[0070] S301. Obtain a code file to be tested input to the application program of the code development tool.
[0071] The code development tool in this embodiment is also a programming language development tool. The development tool here may be a code editor for generating human-readable program text, that is, source code, or a code compiler for converting The source code is converted into machine language, which can be directly run by the computer's central processing unit, that is, the co...
no. 2 example
[0092] In order to better understand the present invention, this embodiment uses a specific example to illustrate the memory leak risk detection method, Figure 4 It is a detailed flow chart of the memory leak risk detection method provided in the second embodiment of the present invention. The memory leak risk detection method includes:
[0093] S401. In the code editing stage, from all the code files of the application program input to the code editor, intercept corresponding code file fragments according to the type of the executed task.
[0094] S402. Use the intercepted code file segment as the code file to be detected.
[0095] In this embodiment, only specific code fragments are intercepted from all code files in the editor as the code files to be detected, so that code fragments with high memory leak potential can be intercepted in a targeted manner for detection, and no memory leaks are detected. Detecting leaked hidden codes can effectively improve detection efficie...
no. 3 example
[0107] In order to better understand the present invention, this embodiment uses another specific example to illustrate the memory leak risk detection method, Figure 5 It is a detailed flow chart of the memory leak risk detection method provided in the third embodiment of the present invention. The memory leak risk detection method includes:
[0108] S501. Obtain a code file to be tested input to the application program of the code development tool.
[0109] S502. Match the to-be-detected code file according to the preset code characteristic data with memory leak risk.
[0110] The development tool here may be a code editor or a code compiler, that is, in this embodiment, any one of the two, or both, may be used to perform the matching detection of the code feature data. Wherein, the code feature data may include at least one of the following: keywords, built-in classes of the software development kit SDK.
[0111] S503. When the code feature data is not matched from the co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com