A method for relieving flooding attacks of hidden interest packets in a named data network
A named data network and flooding attack technology, which is applied in the field of mitigating hidden interest packet flooding attacks in named data networks, can solve problems such as inability to accurately distinguish attackers, low-speed attack sensitivity, and legitimate user request damage, etc., to achieve Effect of Avoiding Data Access Requests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be described in further detail below in conjunction with the accompanying drawings.
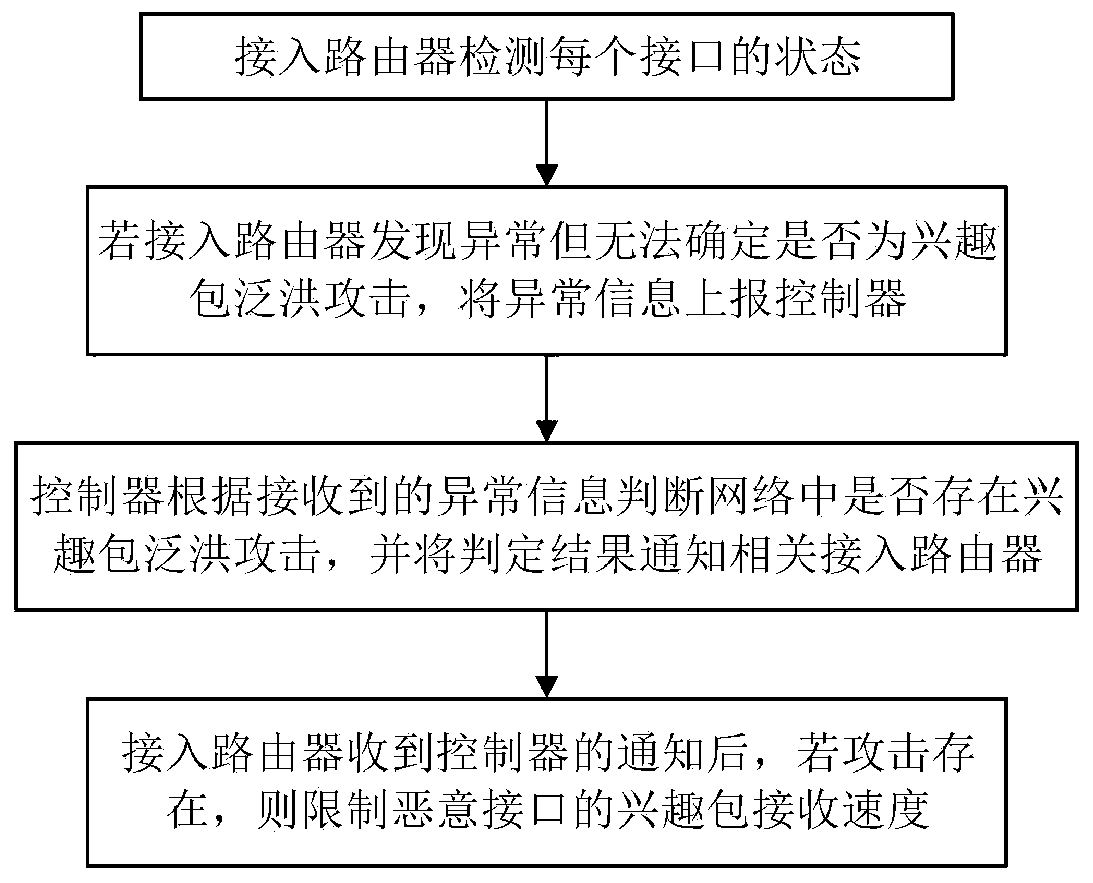
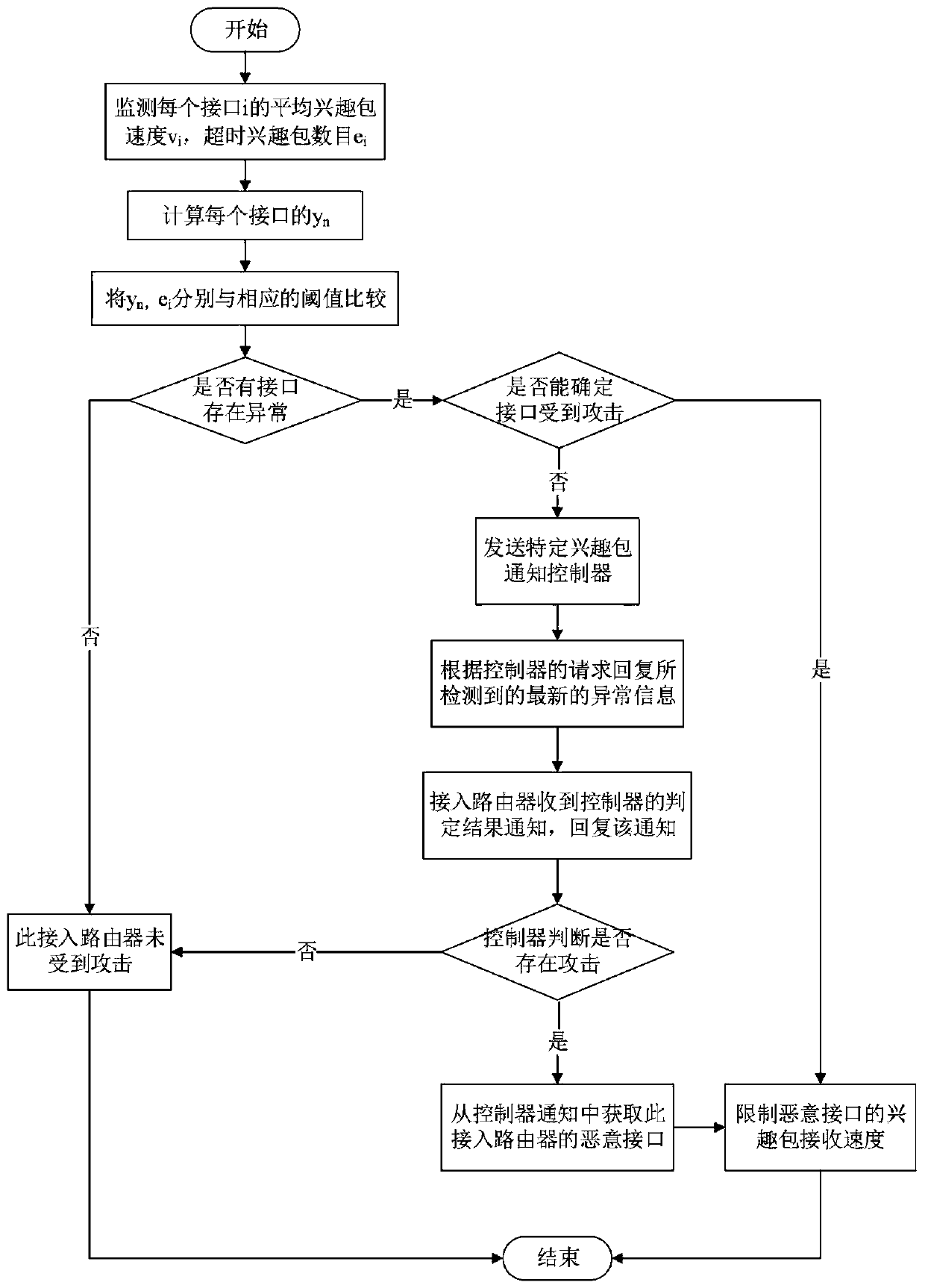
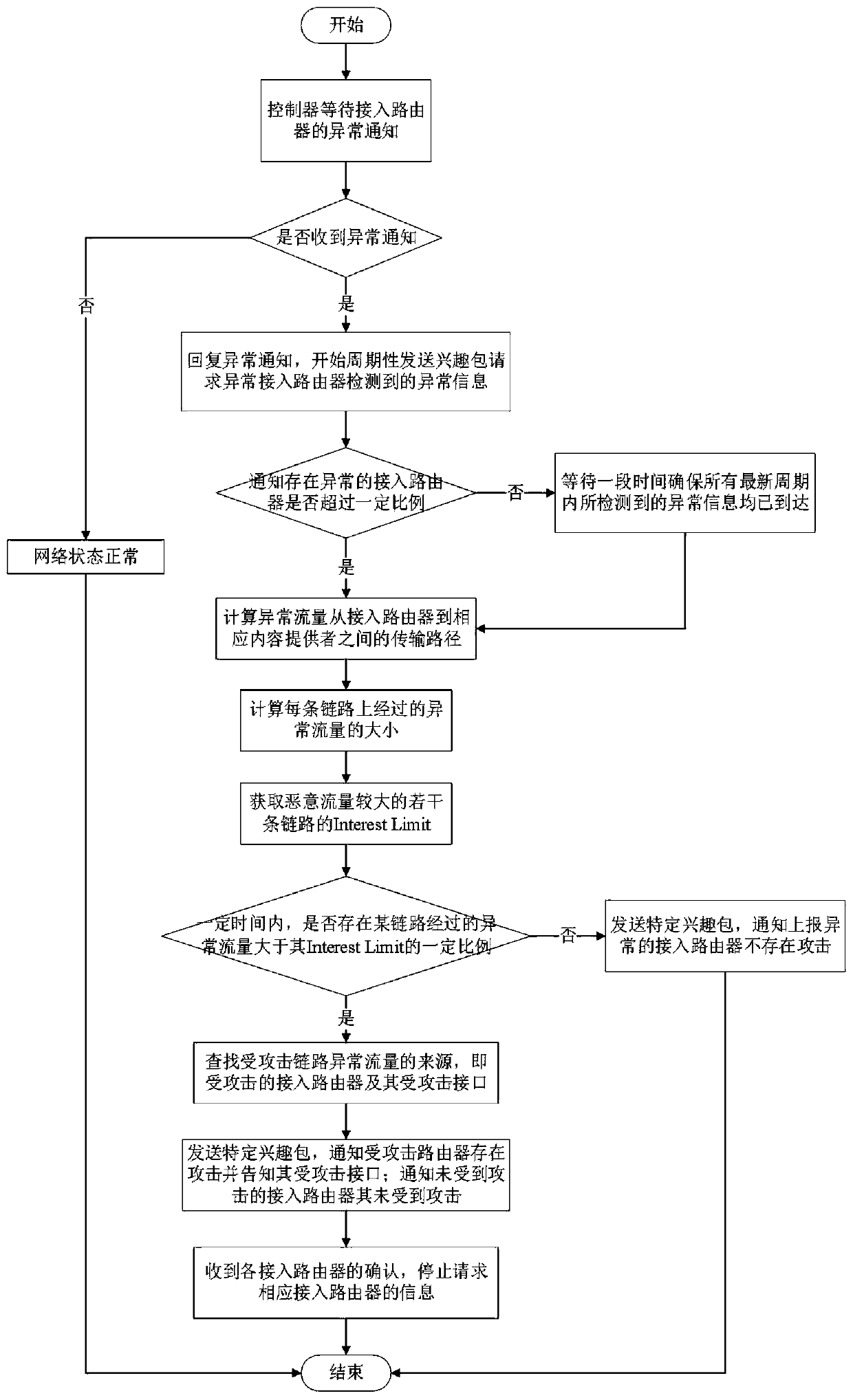
[0031] In the present invention, the controller monitors the network from the perspective of the entire network to timely detect concealed interest packet flooding attacks and effectively locate attackers, and then take targeted defense measures. The so-called covert interest packet flooding attack means that the attacker sends malicious interest packets at a low speed at the beginning of the attack, but then gradually increases the attack speed, so that the relevant state data of the router changes gradually and is not easy to detect. Routers that are directly connected to users or attackers are called access routers, and other routers are called intermediate routers.
[0032] NDN routers are responsible for continuously monitoring their status. When anomalies are detected, such as the interest packet satisfaction rate is too low, the distribution of receiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com