A Web attack detection method based on collaborative training
A technology of attack detection and collaborative training, which is applied in the field of Web intrusion detection and network security, and can solve the problems of high training cost, low accuracy rate, and large number of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
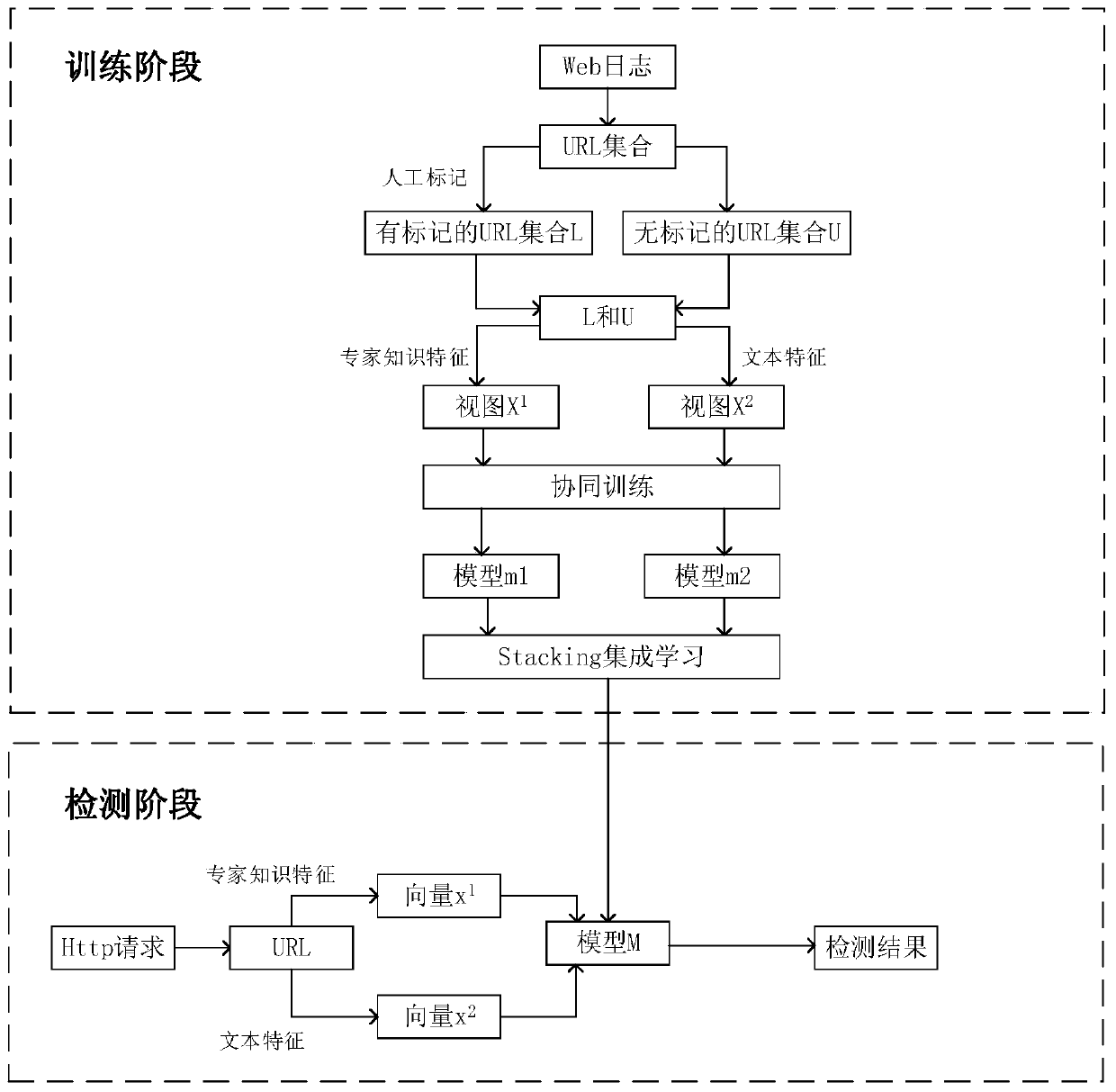
[0042]实施例:一种基于协同训练的Web攻击检测方法,该方法的流程如图1所示,该实施例具体实施步骤如下:
[0043]1处理Web日志,构建数据集
[0044]1.1从Web日志中提取URL
[0045]先从Web服务器中收集Web日志,再从中提取出URL,并对其进行解码,构成集合S;例如,Web日志中的一条记录 202.107.201.11--[18 / Aug / 2018:16:15:46+0800]″GET″ / html / main / col38 / column_38_1.html?id=361 HTTP / 1.0″200 472″-″″-″,经过处理后变为 / html / main / col38 / column_38_1.html?id=361;
[0046]1.2人工标记部分URL
[0047]人工标记部分URL:随机从S中抽取|L|个样本,人工对样本进行标记,标签的集合为{-1, +1},-1代表是正常的URL,+1代表带有攻击的URL,标记样本构成集合L,未标记样本构成集合U,保证S=L+U,L<
[0048]2利用专家知识特征和文本特征,获得两个独立的视图
[0049]2.1用专家知识特征构建视图
[0050]特征空间={路径长度,路径深度,参数长度,参数个数,参数名最大长度,参数名平均长度,参数值最大长度,参数值平均长度,参数值中字母占有的比例,参数之中数字占有的比例,参数值中特殊字符占有的比例,攻击关键字的个数},共计12个特征,其中特殊字符有"”、"eval”等,可以通过查询攻击特征库来得到,用特征空间将URL向量化,S转化为视图X1,最后需要对 X1进行归一化处理,公式为其中Xmax、Xmin分别是原始X1的最大值和最小值;
[0051]2.2用文本特征构建视图
[0052]首先利用N-gram对URL进行分词,URL的特征空间是所有字符的组合,若S中有c种不同的字符,则URL向量的维度d=cn,其中n为N-gram中N的取值,之后用TF-IDF来计算URL的特征值,对于样本x第i个的特征值xi公式由以下的公式得出:xi=TFi×IDFi,其中ni、ntotal、nS、分别表示第i个特征在URL中出现的数量、URL分词后的总数、S的大小、有第i个特征的URL数量,通过上述方法将S 转化为视图X2;
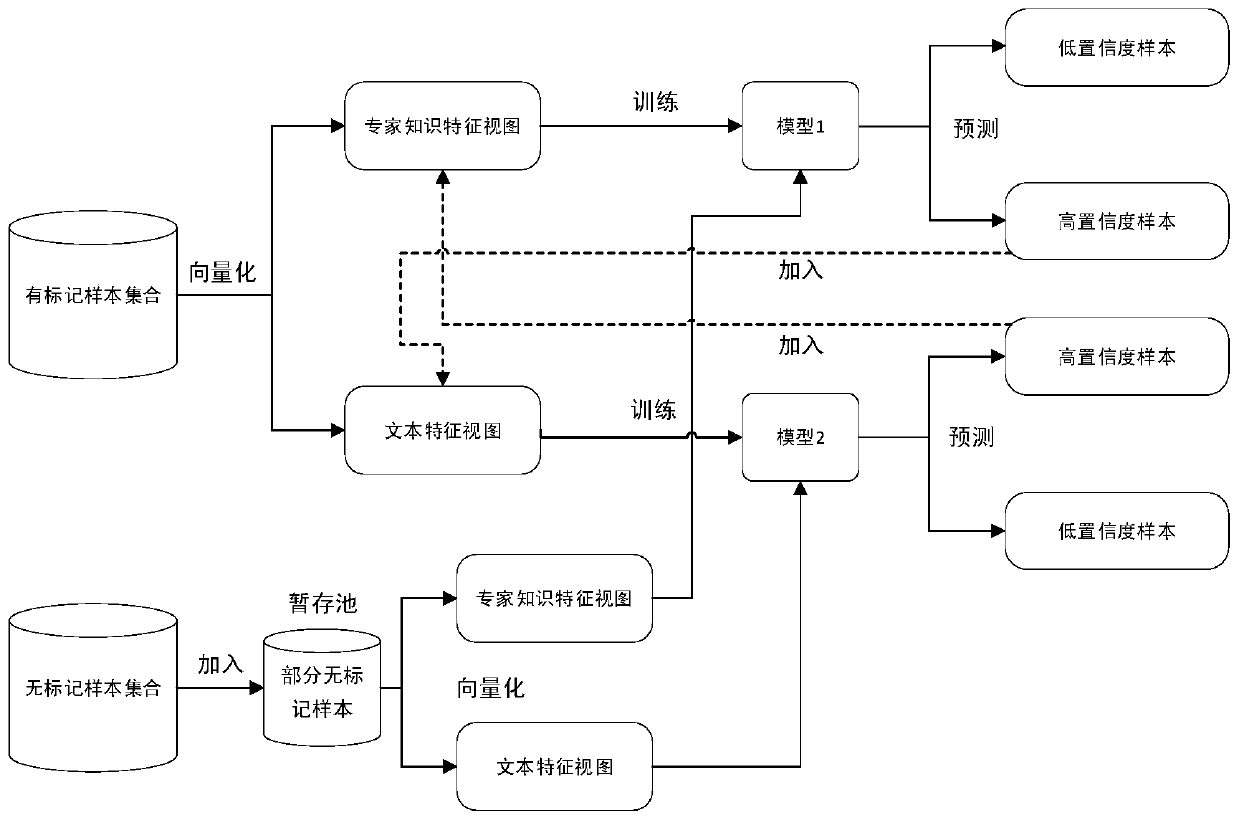
[0053]3利用两个独立的视图进行协同训练,获得两个分类器
[0054]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com