An information interaction method and a cross-scene tracking method of a monitoring terminal
A monitoring terminal and information interaction technology, which is applied in the field of data interaction, can solve the problems of information delay and packet loss, and cannot guarantee that information will not be maliciously tampered with, so as to reduce the difficulty of sharing and reduce the effect of information delay and packet loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
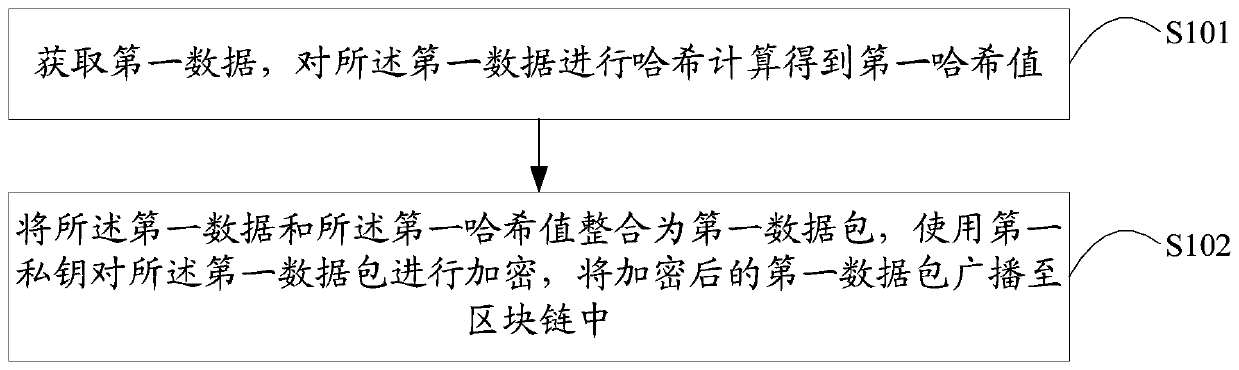
[0036] The following describes a monitoring terminal information interaction method provided by Embodiment 1 of the present application. Please refer to the attached figure 1 The information interaction method of the monitoring terminal in Embodiment 1 of the present application includes:
[0037] Step S101. Obtain first data, and perform hash calculation on the first data to obtain a first hash value;
[0038] The network topology of the traditional monitoring equipment of the Internet of Things is a centralized network topology. There is no direct information exchange between monitoring equipment. The monitoring equipment must transfer information through the upper network center, which is prone to information delay and packet loss. Monitoring The access between terminals is extremely difficult, which hinders the sharing of interconnection and intercommunication information between monitoring terminals, reduces resource utilization, and because information needs to penetrate...
Embodiment 2
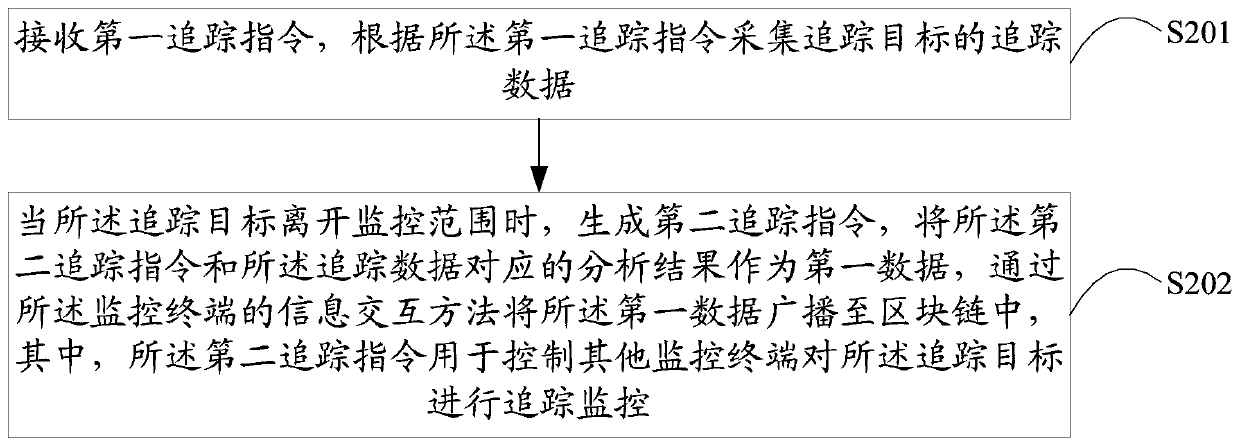
[0059] A cross-scene tracking method provided in Embodiment 2 of the present application is described below, please refer to the attached figure 2 The cross-scene tracking method in Embodiment 2 of the present application is based on the monitoring terminal information interaction method described in Embodiment 1, and the cross-scene tracking method includes:
[0060] Step S201, receiving a first tracking instruction, and collecting tracking data of a tracking target according to the first tracking instruction;
[0061] The Internet of Things network topology of traditional monitoring equipment is a centralized network topology, with large information delays, and it is difficult to quickly coordinate various monitoring equipment to track the same target across scenarios.
[0062] When each monitoring device uses the decentralized network topology of the blockchain network for information interaction, each monitoring device can quickly perform information interaction and colla...
Embodiment 3
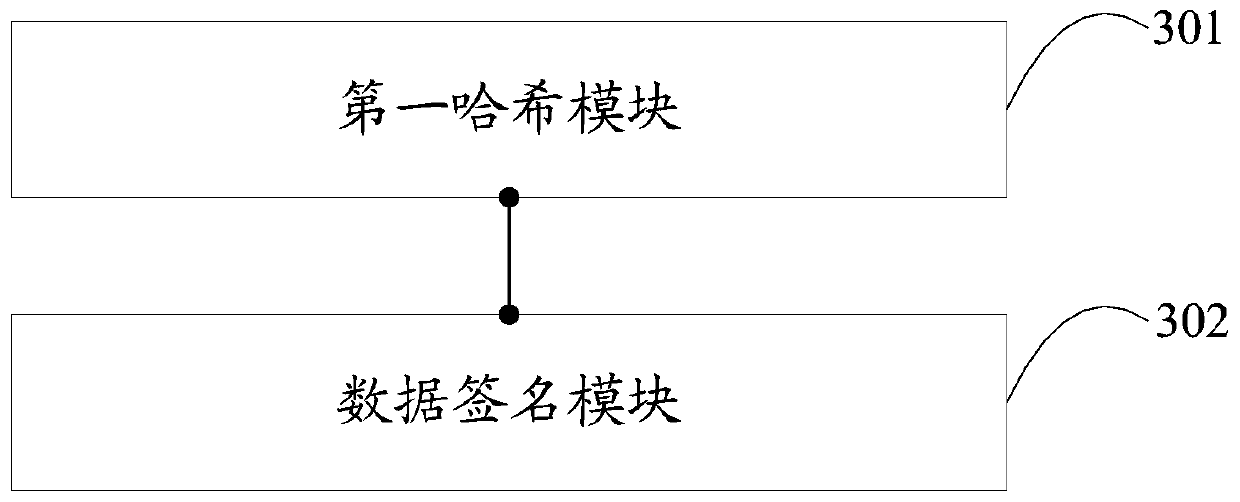
[0075] Embodiment 3 of the present application provides an information exchange device for a monitoring terminal. For the convenience of description, only the parts related to the present application are shown, such as image 3 As shown, the information interaction device of the monitoring terminal includes,
[0076] The first hash module 301 is configured to acquire first data, and perform hash calculation on the first data to obtain a first hash value;
[0077] A data signature module 302, configured to integrate the first data and the first hash value into a first data packet, use a first private key to encrypt the first data packet, and encrypt the encrypted first data The package is broadcast to the blockchain.
[0078] Further, the device also includes:
[0079] A data verification module, configured to receive an encrypted second data packet broadcast to the block chain, and use a second public key to decrypt the encrypted second data packet to obtain a decrypted seco...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com